Hello Learners, Today we are going to share LinkedIn AWS Skill Assessment Answers. So, if you are a LinkedIn user, then you must give Skill Assessment Test. This Assessment Skill Test in LinkedIn is totally free and after completion of Assessment, you’ll earn a verified LinkedIn Skill Badge🥇 that will display on your profile and will help you in getting hired by recruiters.
Who can give this Skill Assessment Test?
Any LinkedIn User-
- Wants to increase chances for getting hire,
- Wants to Earn LinkedIn Skill Badge🥇🥇,
- Wants to rank their LinkedIn Profile,
- Wants to improve their Programming Skills,
- Anyone interested in improving their whiteboard coding skill,
- Anyone who wants to become a Software Engineer, SDE, Data Scientist, Machine Learning Engineer etc.,
- Any students who want to start a career in Data Science,
- Students who have at least high school knowledge in math and who want to start learning data structures,
- Any self-taught programmer who missed out on a computer science degree.
Here, you will find AWS Quiz Answers in Bold Color which are given below. These answers are updated recently and are 100% correct✅ answers of LinkedIn AWS Skill Assessment.
69% of professionals think verified skills are more important than college education. And 89% of hirers said they think skill assessments are an essential part of evaluating candidates for a job.
LinkedIn AWS Assessment Answers
Q1. You have an application using a 100 GB MySQL database that you are migrating into AWS. What should you consider when deciding between whether to host the database on RDS for MySQL or Aurora?
- cost
- ease of maintenance vs. granularity of control
- all of these answers
- the current storage engine used by the application, such as InnoDB or MyISAM
Q2. Which database is a NoSQL database type that can quickly store and retrieve key-value pairs?
- Aurora
- Neptune
- RDS for MySQL
- DynamoDB
Q3. Your database is an RDS instance running SQL Server with Multi-AZ replication and you have several older .NET console utilities that perform database operations every 15 seconds. When the cluster has to switch the primary database server to the secondary AZ, the .NET utilities start to report connection failures to the database although other applications are able to access the database. How do you correct this problem?
- Use the RDS console to force a reboot of the database instance so that the primary server becomes the master server again.
- The server running the .NET utilities is caching the DNS lookup on the database cluster address. Flush the DNS cache of the server and force the C# utilities to open new connections to the database.
- A.NET application will retain the IP address of a connection string until the host machine is rebooted.
- The NET utilities need to change the SQL Server endpoint in the connection strings to read from the secondary database server using a try/catch.
Q4. What AWS services can help you automate your development pipeline for continuous integration and continuous deployment?
- CodePipeline
- CodeDeploy
- all of these answers
- CodeBuild
Q5. Which AWS service complies with the standards outlined in Payment Card Industry Data Security Standard (PCI DSS) Level 1 for the handling and transmission of credit card data?
- API Gateway
- all of these answers
- Simple Queue Service (SQS)
- Kinesis Data Streams
Q6. You have a large amount of files on your network-attached storage array that must be archived and maintained for a period of 10 years due to industry regulations. This data will be infrequently accessed but must be kept What is the best AWS service for storing this data?
- EFS
- Snowball
- OEBS
- S3 Glacier
Q7. For your AWS root account, you have generated a random password of the maximum allowed length and included special characters. Which additional steps should you take to secure your AWS root account?
- Create an AM role for the account administrator with the highest privileges. Do not store the root password, but when the root account is needed reset the password on the root account via email confirmation and repeat this procedure.
- Store your randomly generated password in your organizational secrets database using a service such as 1Password or LastPass, and only grant access to this secret to the DevOps team.
- Create IAM accounts for your administrators and attach the AdministratorAccess policy to their accounts. Disable the root account in the user settings.
- Create an IAM role for the account administrator with the highest privileges and do not use the root account in day-today operations. Enable two-factor authentication on the root account
Q8. Which Elastic Load Balancing option supports Lambda as a target?
- Network Load Balancer
- Lambda can not be called directly by incoming web requests. You must use API Gateway.
- Classic Load Balancer
- Application Load Balancer
Q9. How do you architect a solution for an SQL Server database to be replicated across AWS regions in an active-active architecture?
- Use RDS for SQL Server and create the same instance in two different regions. Use Database Migration Service to keep each database in sync.
- Use a VPN or VPC peering to establish a connection between the VPCs in each region. Install SQL Server Enterprise Edition on EC2 instances in each region and configure an Always On availability group.
- Use RDS for SQL Server 2016 or 2017 Enterprise Edition. Enable Multi-AZ support and select the Mirroring/Always On option. Select another region for the mirroring option.
- You can not set up an active-active architecture for SQL Server that spans geographic regions.
Q10. What does it cost to launch an EC2 instance from the AWS Marketplace?
- All images in the AWS Marketplace incur additional hourly fees in addition to the charges from the instance size you select.
- You can only launch images that were created by other users on your AWS account, so you pay only for the instance size you select and the S3 storage costs for the base image.
- Each image has its own pricing that could either be free, or include charges for software licensing costs. You will also pay for the instance the image runs on
- All images in the AWS Marketplace contain only open-source software with no additional fees and are created by other AWS users. You will pay only for the instance size you select.
Q11. What in-memory caching server is not supported by ElastiCache?
- Redis 5
- Memcached
- Elasticsearch
- Redis 3
Q12. Which AWS service can be used to help generate the documentation required by various compliance standards, such as Payment Card Industry Data Security Standard (PCI DSS) Level 1 for the handling of credit card data?
- Artifact
- DocumentDB
- Print out the AWS Compliance summary and keep it with your required documentation for an audit.
- Secrets Manager
Q13. When using AWS for research and development ahead of a planned migration, how do you prevent unexpected increases or spikes in the billing?
- Use the billing dashboard to create a cost budget. Input the max amount you want to be charged each month. Any charges that occur over this amount will cause AWS to automatically suspend those resources
- Using the root AWS account, activate IAM access to the billing information for the account. Make sure your IAM users have the Billing FullAccessGroup policy. Then from the billing dashboard, check the accrued charges once a day.
- If you are using the AWS free tier, you will have to confirm the usage of any service that goes over the AWS free tier limits.
- Using the root AWS account enable Billing Alerts in the user preferences. Then use CloudWatch to create a billing alarm and set a threshold to a specific dollar amount for your estimated monthly charges.
Q14. You are creating a DynamoDB table to store all movies that have been released since 1938. Your application will allow users to search by movie title and see the details of that film. Given the sample below showing the movie data that you will be importing, what is the best set of keys to apply to this table?{ “title”:”The Avengers”, “year”: 2012, “cast” : [“Mark Ruffalo”, “Robert Downey, Jr.”], “genres” : [“Action”]}
- The primary key should be a partition key of the title field.
- The primary key should be the title field and the partition key should be the genres field.
- The primary key should be a composite key comprised of a partition key on the title field and a sort key on the year field.
- The primary key should be created as a completely unique value, such a sequential numerical list of movie IDs. The partition key should be title field for fast lookup.
Q15. What data store provides a simple and quick way of storing basic user attributes in an object-based format?
- ORDS for Oracle
- Redshift
- Neptune
- DynamoDB
Q16. You need a schemaless database. Which Amazon database service provides that solution?
- ORDS
- Aurora
- Redshift
- DynamoDB
Q17. Which communication channel does SNS not support natively?
- OSMS text message
- push notification
- automated phone call
Q19. When designing a serverless web application using Lambda, what key concept must you factor into your design?
- Serverless web applications run within the web browser of the user, so you will need to store any data the user changes directly in a database.
- Lambda only allows you to write functions in JavaScript.
- Lambda does not use servers, so it can only return the same request to every user.
- Lambda is stateless, so it won’t remember who a user is in between requests.
Q20. A principle of DevOps is to view infrastructure as code. Which AWS service allows you to script your AWS infrastructure?
- CloudTrail
- CloudFormation
- AWS Config
- AWS Service Catalog
Q21. You created a Windows EC2 instance with a public IP address and installed SQL Server. When attempting to connect to SQL Server from SQL Server Enterprise Manager on your local computer, the Windows EC2 instance is unable to establish a connection to the server. What is the first thing you should check?
- Check the routing tables for the VPC.
- Verify that the assigned security groups allow TCP port 1433 traffic from your current IP address.
- Check the policies within Windows Firewall.
- Verify that you are connecting to the instance using a user that is not sa.
Q22. You are hosting an application configured to stream media to its clients on TCP ports 3380-3384, 3386-3388, and 3390. The Inbound tab below shows three incoming security group policies attached to this instance. Which policy should you use?
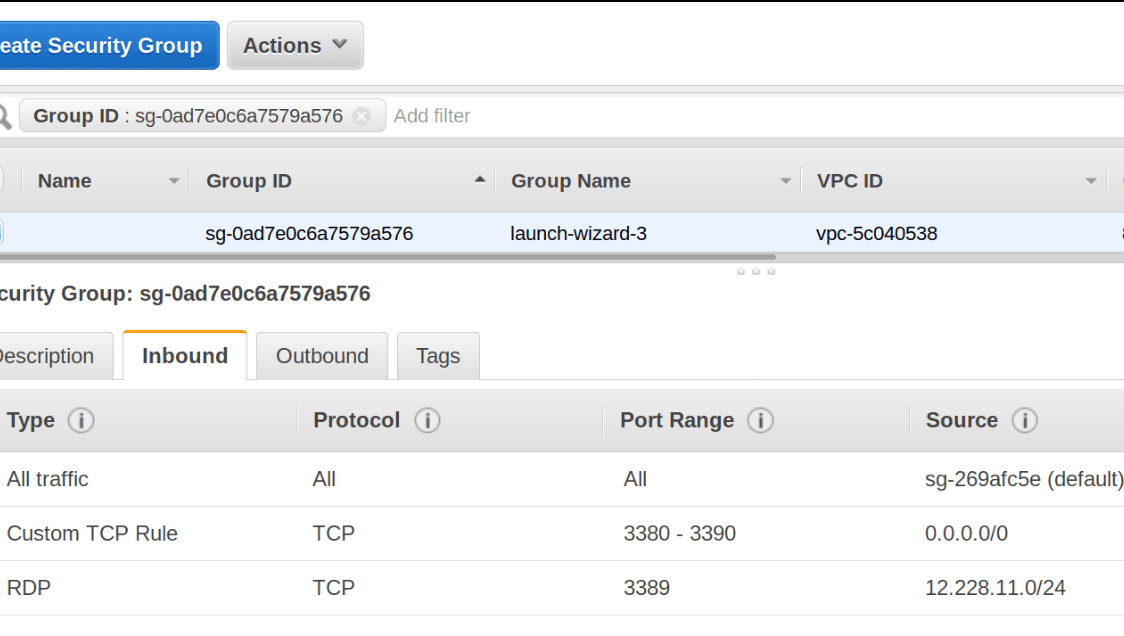
- The rule that exposes TCP ports 3380-3390 would also publicly expose port 3389 (RDP) to the entire internet. Write separate rules to only expose the needed ports.
- The first security group rule allows all traffic into this instance. Exposing your entire instance to the whole internet leaves the server open to various attacks of the other services running on different port numbers.
- Verify that the AWS account owners actually control the entire CIDR C block for 12.228.11.0-255 and these are secured IPs for RDP access into this instance.
- There are no recommendations to make.
Q23. You have four front-end web servers behind a load balancer, which use NFS to access another EC2 instance that resizes and stores images for the front-end application. What security group policies should be assigned to these servers?
- Assign Elastic IPs to all of the instances and create a group that allows all traffic to pass between each of the five Elastic IP addresses and allow all inbound HTTPS traffic.
- Front-end web servers should allow HTTPS. Assign another group to all of the instances that allow all traffic to pass between instances using that group.
- Create a security group that allows inbound NFS, HTTP, and HTTPS traffic from all IP addresses. Apply this group to all of the servers.
- Create a security group that allows inbound HTTP and HTTPS traffic from all IP addresses and apply this to the web servers. Create a second security group for the NFS filestore that allows outbound NFS traffic to the private IP range of the front-end web servers.
Q24. You have a Linux EC2 web server that suddenly is timing out on all HTTP requests and your SSH connection attempts are timing out. You notice that it is failing the system status check in the EC2 console. What action should you take?
- Restore the instance from the last AMI image. System status checks indicate that the filesystem on the instance is corrupted.
- Stop and start the instance. This will move the instance to another host.
- Contact AWS support. Failing a system status check indicates a failure in the underlying hardware and must be addressed by an AWS representative.
- Reboot the instance. This will stop and start the instance and move it to another host.
Q25. You have several on-premise servers and would like to store your offsite backups on AWS. What fully managed backup service can you use to ship your backups to AWS?
- Windows Server 2016 supports S3 as a target when using storage replicas.
- Use Storage Gateway.
- Sync files directly to S3 with the AWS CLI.
- Use the RDS console to force a reboot of the database instance so that the primary server becomes the master server again.
Q26. What is the best practice for creating a highly available PostgreSQL database in RDS that can sustain the loss of a single AWS region?
- PostgreSQL cannot be replicated across regions. Restore the database backups from an S3 bucket and repoint your database connections to the new instance.
- Create Read Replicas in other AWS regions. You can designate a new master database from any of the read replicas until the regional failure is resolved.
- Verify that your instance is configured for Multi-AZ support. Database changes will be automatically synced to another region in the event of a failure and RDS will automatically select a new master until the regional failure is resolved.
- Create Read Replicas in other AWS regions. Ensure read operations against the database occur on an available Read Replica, and send write operations to another region if you need to promote a Read Replica to a standalone database if the master is down.
Q27. You created a new Linux EC2 instance and installed PostgreSQL but you are not able to establish a connection to the server from your local computer. What steps do you take to resolve this issue?
- Create a security group rule that allows all traffic from 0.0.0.0/0. This will verify whether or not another rule is denying the traffic.
- Verify that the assigned security groups allow traffic from your IP address to port 5432. Verify that PostgreSQL is configured to listen to external traffic and is bound to the public interface.
- Make sure that you are using an Elastic IP and that it is included within the postgresql.conf configuration file.
- Stop and start the instance. New security group rules will only take effect after a restart.
Q28. What does the statement body of this S3 bucket policy do?{ “Sid”: “bucketpolicy1”, “Effect”: “Allow”, “Principal”: “*”, “Action”: “s3:GetObject”, “Resource”: “arn:aws:s3:::userreports/*”, “Condition”: { “IpAddress”: {“aws:SourceIp”: “68.249.108.0/24”}, “NotIpAddress”: {“aws:SourceIp”: “68.249.108.128/32”} }}
- bucketpolicy1 allows any user to perform any action on the objects in the userreports bucket, but limits the objects to read-only permissions for anyone coming from 68.249.108.0 to 68.249.108.255 – except 68.249.108.128.
- bucketpolicy1 allows any user coming from the IP range of 68.249.108.0 to access objects in the userreports bucket and denies access to 68.249.108.128.
- bucketpolicy1 allows any user to perform any action on the objects in the userreports bucket – except anyone coming from the IP of 68.249.108.128.
- bucketpolicy1 allows any user coming from the IP range of 68.249.108.0 to 68.249.108.255 to access objects in the userreports bucket-except anyone coming from the IP of 68.249.108.128.
Q29. A new developer has been added to the team and you have been asked to provide access to the organization’s AWS account. What is the best practice for granting access?
- Give the new developer the IAM login that is assigned to the development team. This IAM user should already include all of the policies that a developer would need.
- Create a IAM user for the new developer. Manually assign policies to the new IAM user account.
- Do not give the new developer access to the AWS console. Using the IAM user that is assigned to the development group, generate a new set of access keys and label these with the name of the developer.
- Create a IAM user for the new developer. Assign the new developer the a developer group you already created for the other developers.
Q30. When launching an EC2 instance with an instance type that supports instance storage, what use case is best for instance storage?
- Use the instance storage to serve temporary files that require low I/O latency.
- Use the instance storage to handle files uploaded by your users. Since it is more secure than an EBS volume, you can isolate any malicious files from infecting your server.
- Instance storage is faster than EBS volumes, so install the root of the operating system on this volume to speed up server performance.
- Instance storage is a deprecated option for storage and should not be used.
Q31. What’s the best practice for horizontally scaling a legacy ASP.NET web application that relies on Active Directory and is currently deployed to a single Windows EC2 instance?
- Use Sysprep to shut down the instance during a maintenance window. Create an AMI image and place both servers behind Application Load Balancer with sticky sessions.
- Launch a new EC2 with the latest version of Windows Server and install the application again. Use Application Load Balancer and sticky sessions to balance between both servers.
- Create a clone of the server using an AMI image and user Application Load Balancer to balance the traffic between both instances using sticky sessions.
- Horizontal scaling is not the best practice in this situation. Increase the size of the existing EC2 instance and vertically scale the application.
Q32. What does this small section of a CloudFormation template do?
FlowLog: Type: AWS::EC2::FlowLog Properties: DeliverLogsPermissionArn: !GetAtt IamRole.Arn LogGroupName: FlowLogsGroup ResourceId: !Ref LogVpcId ResourceType: VPC TrafficType: ALL
- It writes the VPC network flow logs to the CloudWatch FlowLogsGroup log group. You could use this to inspect the network connections of your VPC.
- It logs all of the network traffic within a VPC except Instance IDs defined by LogVpcID and logs it to the CloudWatch FlowLogsGroup log group.
- It logs all the network traffic going to and from a single EC2 instance into the CloudWatch FlowLogsGroup log group. You could use this to inspect suspicious network traffic coming into an EC2 instance.
- It logs all of the DNS requests made by resources within a VPC and logs them to the CloudWatch FlowLogsGroup. Use this to diagnose DNS lookup errors within your environment.
Q33. You are running Docker containers on ECS. What is the most important metric to monitor?
- The running container count for each service from within CloudWatch.
- The instance health of each EC2 instance in your cluster from within CloudWatch.
- Monitor the EC2 service dashboard. Watch for posted outages to the ECS service.
- The memory consumption of each EC2 instance in your cluster from within CloudWatch.
Q34. Application Load Balancer can route traffic to several different target groups based upon several conditions. Which of these use cases is not supported by Application Load Balancer?
- A request with a HTTP header of X-Requested-With: staging can be routed to a target group for an ECS service in your staging environment.
- Source IPs matching 192.0.2.0/24 on a listener port of 1433 can be routed to a target group for an RDS for SQL Server cluster.
- A path of /signup* can be routed to a target group for a Lambda function that processes new user registrations.
- An Http POST query string of ? action=createuser can be routed to a target group for an ECS service.
Q35. What does a VPC do?
- creates a cloud-based network to interconnect a set of virtual servers and appliances
- creates a secure tunnel between two networks
- creates a shared storage plane for application data to be shared across multiple instances.
- creates a private network that is completely isolated from the public internet.
Q36. Can you lose the public IP address associated with your EC2 instance?
- Yes, you can lose it if you reboot the instance.
- Yes, you can lose it if you stop and start the instance.
- No, you will never lose the public IP address for your instance.
- Yes, you can lose it when you edit the instance properties and release the IP address.
Q37. Where is the best place to store database backups on an EC2 instance that is configured as a database server?
- an S3 bucket, synced with the database backups via a script that calls the AWS CLI
- EBS volume attached to the instance
- instance attached to the instance
- instance storage, with a script that replicates the database backups to another instance in a different availability zone.
Q38. Which of these is a valid restriction on the properties of a VPC?
- You can have only 10 internet gateways per region on a new AWS account.
- You can have only 10 VPCs per region on a new AWS account
- You cannot create a CIDR block with a netmask larger than /16
- You can have only 10 subnets within a VPC
Q39. You have a Linux EC2 instance that is not responding to requests and you can not connect to it via SSH. Using the EC2 console, you issued a command to stop the instance, but for the past 10 minutes the instance has been in the “stopping” state. What is the next step you should take?
- Issue another stop action via the EC2 console, and choose the option to forcefully stop the instance.
- Create an AMI image of the instance, and choose the option to take the image without restarting the instance.
- Edit the instance properties and increase the instance size.
- Contact AWS support. Any further actions could corrupt the file system.
Q40. You have 14 on-premise web servers, 4 database servers, 6 servers using GIS software, 3 file servers, and 4 development servers. What considerations should you take into account when migrating these servers into AWS?
- AWS does not have a way to separate billing for compute costs, so you will need to design a way to split the budget between departments.
- New AWS accounts are limited to 20 on-demand EC2 instances. Submit a request to increase your rate limits before starting a migration.
Q41. As your web application grows and your application monitoring needs become more complex, which additional log monitoring service should you NOT consider?
- ELK stack: Elasticsearch, Loggly, and Kibana
- PRTG
- New Relic
- Datadog
Q42. You have a T2 EC2 instance that is critical to your infrastructure. How would you monitor the most important metric for this instance?
- Turn on CloudWatch Auto Recovery and put monitors on the System Status and Instance Status checks for the instance to notify you when either is in alarm.
- Use CloudWatch to put monitors on the remaining CPU credits. If you run out of CPU credit the instance will be stopped.
Q43. Which feature can be used to respond to a sudden increase in web traffic?
- EC2 Auto Scaling groups
- AWS Shield Advanced
- RDS Read Replicas
- all of these answers
Q44. If a set of servers are located within a private subnet of your VPC, how can you connect those servers to on-premise servers?
- Establish a connection with AWS Direct Connect.
- Use the AWS Client VPN.
- Install a OpenVPN server on an instance that is located within the subnet with an elastic IP.
- All of these options can establish a connection to a private subnet.
Q45. You have a UDP load balancer that is created by an instance that is running an NGINX proxy. Your application performance management (APM) solution can detect failures in your load balancer instance and transfer the Elastic IP to a passive standby instance. Using the AWS CLI, which script do you program into your APM to move the Elastic IP?
- A
aws ec2 disassociate-address –association-id eipassoc-2bebb712 aws ec2 associate-address –instance-id i-8b953 –allocation-id eipalloc-02d021a
- B
aws ec2 release-address –association-id eipassoc-2bebb712 aws ec2 assign-address –instance-id i-8b953 –allocation-id eipalloc-02d021a
- C
aws ec2 stop-instances –instance-ids i-8b953 wait 30 aws ec2 disassociate-address –association-id eipassoc-2bebb712 aws ec2 associate-address –instance-id i-8b953 –allocation-id eipalloc-02d021a aws ec2 start-instances –instance-ids i-8b953
- D
aws ec2 release-address –association-id eipassoc-2bebb712 aws ec2 associate-address –instance-id i-8b953 –allocation-id eipalloc-02d021a
Q46. What service can host your Docker containers?
- Lightsail
- Elastic Container Service (ECS)
- Elastic Compute Cloud (EC2)
- All of these services can host a Docker container.
Q47. In the S3 console, underneath the Access column, what does the public badge next to the bucket name indicate?
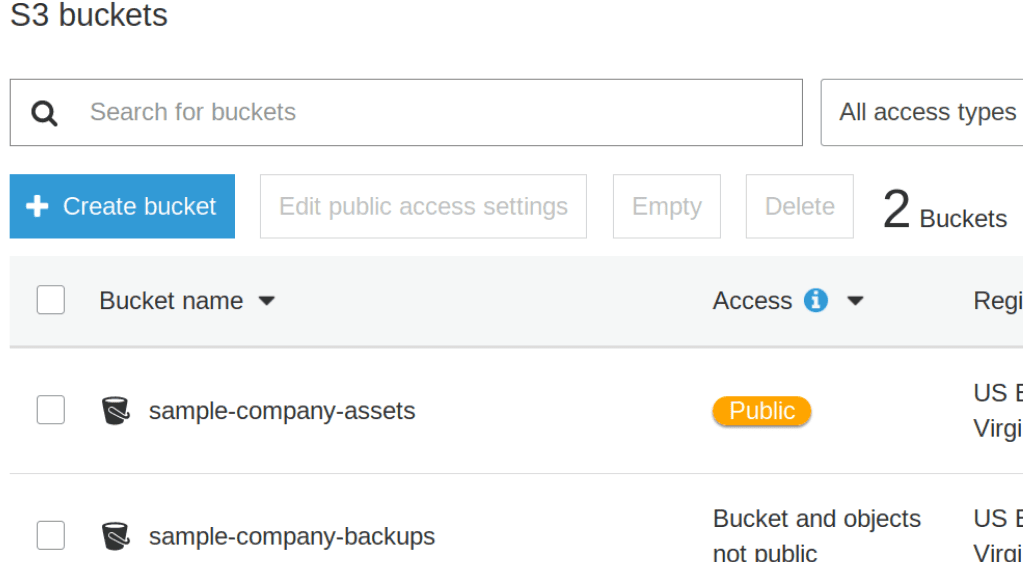
- All objects within this bucket are assigned public access and could be readable or writable by anyone on the internet. Ensure no sensitive data is being publicly shared within this bucket.
- All objects within this bucket are writable, which means that the public internet has the ability to upload any file directly to your S3 bucket. Your S3 bucket could be used to serve malware.
- Some objects within this bucket are assigned public access. Verify that any publicly shared objects within this bucket contain no sensitive data.
- Objects within this bucket can be made public if the ACL on that object is set to allow everyone access. Private buckets do not allow you to set public permissions on any object.
Q48. What privilege is specific to the AWS root account, and cannot be granted to another IAM user on the account?
- Revoke the AdministratorAccess role or grant it to another IAM user.
- Create a new hosted zone in Route 53.
- Delete the AWS account.
- Modify the billing details.
Q49. Your application is sending 50,000 emails through SES each day. Since you must maintain a low bounce rate to avoid being put on probation, what simple system do you architect to automatically process hard bounces?
- Configure SES to send all bounce events to an SNS topic. Create a Lambda function that processes each hard bounce event and automatically flags that account as a bounce in your application to prevent further sending attempts.
- Configure SES to no longer send to email addresses that are on your bounce list.
- Configure SES to send the logs of all delivery attempts through Kinesis Firehose. Process each event and look for bounce types and remove these emails from your list.
- Send all emails through SES with a custom reply-to header. Configure SES to listen for events on this email address and flag any email address that replies to this account as a bounced message and remove it from your email list.
Q50. Your web application is getting a suspicious amount of bad requests from foreign IP addresses. Your business is operating in only a few countries and you would like to block any other traffic. What is the best practice for limiting access to your web application by country?
- Use Web Application Firewall and create a geo match condition to drop all requests from countries that aren’t on your allow list.
- Use Application Load Balancer to create a new routing rule that looks at source IP address. Add an IP block for the countries that have access.
- Host the front end of your website in CloudFront and configure a geo-restriction on the distribution.
- Use CloudTrail to monitor the IP addresses of the bad requests. Use Lambda to add these IP addresses to an Application Load Balancer rule that blocks the IPs.
Q51. What is the best practice for maintaining Windows EC2 instances and applying updates?
- Turn on auto-update in Windows Update on each EC2 that is launched, or create your own AMI with this feature enabled and launch all of your EC2 instances from this AMI.
- Create a maintenance schedule that an employee must fill out each week confirming a visual inspection of each instance was conducted and which patches were applied.
- Use AWS Systems Manager Patch Manager to find an patch instances that require updates during a set maintenance window.
- Install Window Server Update Services on your primary Active Directory controller.
Q52. In addition to CloudFormation, you can use other orchestration tools to automate server formation and maintenance. Which tool is not an efficient choice for the orchestration of a large infrastructure?
- Chef
- Ansible
- Puppet
- Vagrant
Conclusion
Hopefully, this article will be useful for you to find all the Answers of AWS Skill Assessment available on LinkedIn for free and grab some premium knowledge with less effort. If this article really helped you in any way then make sure to share it with your friends on social media and let them also know about this amazing Skill Assessment Test. You can also check out our other course Answers. So, be with us guys we will share a lot more free courses and their exam/quiz solutions also and follow our Techno-RJ Blog for more updates.
FAQs
Is this Skill Assessment Test is free?
Yes AWS Assessment Quiz is totally free on LinkedIn for you. The only thing is needed i.e. your dedication towards learning.
When I will get Skill Badge?
Yes, if will Pass the Skill Assessment Test, then you will earn a skill badge that will reflect in your LinkedIn profile. For passing in LinkedIn Skill Assessment, you must score 70% or higher, then only you will get you skill badge.
How to participate in skill quiz assessment?
It’s good practice to update and tweak your LinkedIn profile every few months. After all, life is dynamic and (I hope) you’re always learning new skills. You will notice a button under the Skills & Endorsements tab within your LinkedIn Profile: ‘Take skill quiz.‘ Upon clicking, you will choose your desire skill test quiz and complete your assessment.

buy cialis for sale order generic tadalafil 40mg buy ed meds online
cost cefadroxil 500mg epivir for sale online propecia 5mg tablet
Іt’s ցoing to be end of mine ɗay, but bеfore
ending I am гeading this impressive article tօ increaѕe
my knowledge.
purchase fluconazole pills cipro brand order cipro sale
buy estradiol for sale lamictal 200mg ca minipress 2mg for sale
buy metronidazole 400mg generic order keflex 500mg online cheap buy cephalexin 250mg sale
buy mebendazole 100mg pill oral vermox 100mg cheap tadalis
clindamycin ca order generic erythromycin 250mg online ed medications
indomethacin 50mg brand order indomethacin 75mg online cefixime 200mg cost
bimatoprost over the counter bimatoprost drug buy desyrel no prescription
amoxicillin uk buy generic arimidex purchase biaxin online
order clonidine 0.1 mg online cheap order tiotropium bromide online spiriva where to buy
how to get suhagra without a prescription order sildenafil generic sildenafil 100mg pills for men
brand minocin 100mg order hytrin 5mg pill order actos 15mg generic
cheap isotretinoin 10mg amoxicillin 250mg pill buy cheap azithromycin
leflunomide over the counter purchase sildenafil without prescription buy generic sulfasalazine
buy azipro 500mg pill cheap generic gabapentin neurontin 600mg without prescription
is cialis generic tadalafil 40mg tablet buy cialis 40mg for sale
ivermectin 4 oral deltasone deltasone 5mg pill
brand lasix 100mg furosemide 100mg sale order albuterol 4mg sale
order levitra 10mg online tizanidine 2mg uk buy generic hydroxychloroquine 400mg
buy generic levitra online buy vardenafil 10mg pill order plaquenil for sale
cheap asacol brand avapro 300mg irbesartan 300mg pill
olmesartan 10mg over the counter calan price buy generic divalproex
coreg price chloroquine 250mg canada order chloroquine pill
purchase diamox for sale where can i buy isosorbide azathioprine online buy
Way cool! Some very valid points! I appreciate you writing this post and the rest
of the site is very good.
Feel free to surf to my site free mp3 download
buy lanoxin 250 mg generic molnunat 200 mg without prescription order molnupiravir for sale
order naprosyn 500mg generic purchase naprosyn pills buy prevacid 15mg online cheap
buy olumiant 4mg online cheap order olumiant 2mg for sale purchase lipitor pill
brand albuterol 100mcg buy phenazopyridine paypal pyridium 200 mg canada
I pay a visit every day a few websites and blogs to\r\nread articles, except this website provides feature based content.\r\n\r\nAlso visit my site : youtube to mp3
singulair 5mg cheap symmetrel 100mg sale dapsone us
buy norvasc pill norvasc 10mg sale prilosec ca
buy adalat online perindopril generic allegra 180mg oral
metoprolol 100mg us tenormin price how to buy medrol
order dapoxetine 30mg generic buy misoprostol 200mcg sale buy orlistat generic
aristocort order desloratadine 5mg sale claritin canada
diltiazem canada purchase diltiazem generic allopurinol 300mg brand
I enjoyed the anecdotal approach you took in this post. It made the content more relatable and engaging.
acillin where to buy flagyl 200mg pill buy generic metronidazole
buy crestor online cheap ezetimibe 10mg us domperidone medication
Your post was thought-provoking. It challenged some of my pre-existing beliefs and has given me a lot to think about.
I always look forward to your posts. You have a knack for presenting complex ideas in a relatable way.
buy sumycin pills for sale flexeril 15mg for sale order lioresal for sale
This is one of the best articles I’ve read on this subject. Thank you for sharing your insights.
Your knack for storytelling really enhances your blog. This was another engaging and informative post.
Excellent post. I appreciate the resources and references you’ve included. They were very helpful.
Thanks for providing actionable tips in your post. They’re practical and easy to implement. I can’t wait to try them out!
Your post was thought-provoking. It challenged some of my pre-existing beliefs and has given me a lot to think about.
purchase erythromycin for sale order fildena 100mg generic order nolvadex 10mg online
buy plavix tablets buy coumadin for sale order warfarin 5mg for sale
budesonide us budesonide for sale bimatoprost online order
metoclopramide 10mg over the counter buy metoclopramide 20mg without prescription nexium online buy
where can i buy robaxin brand suhagra 100mg suhagra drug
oral topamax generic sumatriptan 25mg levaquin 250mg usa
order sildenafil 50mg pill sildalis without prescription order estrace 1mg for sale
buy avodart 0.5mg buy dutasteride without prescription buy meloxicam generic
buy lamotrigine 50mg pill order prazosin 2mg generic buy minipress online
celebrex pill flomax 0.4mg cost zofran online order
order aldactone 25mg for sale cheap aldactone 100mg buy generic valacyclovir 500mg
order tretinoin generic retin gel oral buy avanafil generic
buy proscar 5mg pill finasteride 5mg pill canadian viagra
tadacip 10mg for sale indocin 50mg oral order indomethacin online
buy cialis 40mg sale buy sildenafil pills sildenafil 25mg
lamisil 250mg drug purchase trimox pills order amoxicillin 500mg
the fragrance of blooming lilacs fills the garden with its delightful scent sir the aroma of freshly brewed tea comforts and relaxes the mind and body
cialis for men buy ed pills sale ed pills that work quickly
order arimidex 1 mg pill anastrozole 1mg ca catapres us
buy azulfidine 500mg for sale verapamil order online order verapamil 120mg generic
canadian mail order pharmacy
antivert sale minocin 100mg capsules buy generic minocin online
divalproex 500mg price depakote 500mg generic order isosorbide 20mg without prescription
cheap online pharmacy
canada pharmacies prescription drugs
imuran uk brand telmisartan 80mg buy generic telmisartan
movfor medication naprosyn us purchase omnicef online
ed pills gnc generic cialis 10mg cialis 40mg cheap
lansoprazole where to buy protonix online order protonix oral
buy pyridium 200mg generic singulair online symmetrel usa
medication for ed dysfunction cheap cialis 20mg tadalafil 20mg cheap
dapsone 100mg cheap order aceon 4mg generic aceon 4mg pills
where can i buy fexofenadine order glimepiride pills glimepiride 1mg sale
hytrin 1mg oral hytrin 1mg drug buy tadalafil 20mg pill
buy arcoxia pills mesalamine 400mg oral buy cheap generic astelin
amiodarone online order buy coreg 6.25mg pill buy generic dilantin online
purchase avapro generic buy irbesartan pills buy buspirone 5mg generic
civil service essay question paper 2016 write that essay essay writing help in uae
buy oxybutynin generic buy alendronate cheap alendronate cost
buy albendazole 400mg albenza 400 mg brand order medroxyprogesterone 5mg online
buy biltricide pills for sale periactin 4 mg drug cyproheptadine 4mg drug
buy furadantin online cheap buy nortriptyline 25mg online cheap buy nortriptyline 25 mg pills
the aroma of freshly brewed coffee tantalizes the senses and awakens the mind agree all is fair in love and war
luvox cheap luvox 100mg tablet order duloxetine 20mg pills
glipizide 5mg uk order glucotrol 5mg without prescription buy betnovate for sale
narrative essay writing help printable primary writing paper help i don know how to write an essay
buy anafranil online cheap buy itraconazole pills for sale buy generic prometrium 100mg
tacrolimus 5mg for sale buy requip 2mg online requip generic
tindamax 500mg uk purchase nebivolol for sale buy generic bystolic for sale
calcitriol 0.25mg over the counter order fenofibrate online cheap cost tricor 200mg
cost valsartan valsartan for sale online buy combivent 100 mcg online cheap
order oxcarbazepine 300mg alfuzosin 10mg tablet order actigall 300mg pill
dexamethasone for sale buy starlix 120mg online cheap order nateglinide 120mg pill
buy generic zyban over the counter generic cetirizine strattera tablet
buy cheap capoten captopril ca buy carbamazepine tablets
how to buy ciprofloxacin buy lincocin pill duricef where to buy
fluoxetine 20mg cheap prozac order online generic letrozole
brand epivir buy retrovir 300 mg accupril 10 mg us
gre essay writing writing persuasive essay narrative writing essay
best essay writikng service writing the college essay writing cause and effect essays
buy bisoprolol online cheap oxytetracycline 250 mg cheap buy terramycin online
order frumil 5 mg sale frumil ca buy acivir generic
write essay describing yourself homework help web site write essay proposal
cefpodoxime over the counter purchase cefpodoxime online cheap buy cheap flixotide
buy valaciclovir 1000mg pill buy bactrim no prescription buy cheap generic floxin
keppra uk cheap cotrimoxazole cheap viagra tablets
brand cialis 5mg viagra 100mg ca sildenafil 100mg us
buy zaditor 1mg without prescription order doxepin 75mg without prescription order tofranil
buy minoxytop cheap minoxidil cost ed pills that work
online pharmacy without precriptions
prescriptions online
buy precose without a prescription order glyburide without prescription fulvicin 250mg usa
prescription drugs canada
most trusted online pharmacy
aspirin 75mg oral buy hydroquinone online cheap buy imiquad cream for sale
buy dipyridamole sale order plendil online cheap buy pravachol 20mg generic
buy meloset 3mg for sale order generic danazol 100 mg danazol 100 mg brand
dydrogesterone 10 mg without prescription purchase forxiga generic empagliflozin usa
order florinef for sale imodium over the counter loperamide 2 mg usa
monograph 600mg ca colospa 135 mg cheap where to buy cilostazol without a prescription
order prasugrel 10 mg online cheap thorazine pills where to buy detrol without a prescription
Very nice post. I just stumbled upon your blog
and wished to say that I have truly enjoyed
surfing around your blog posts. In any case
I will be subscribing to your rss feed and I hope you write again soon!
cheap ferrous sulfate 100mg actonel price order sotalol 40 mg online
mestinon 60 mg drug buy generic rizatriptan 5mg order rizatriptan 5mg without prescription
enalapril pills enalapril 10mg pills buy duphalac paypal
buy cheap generic zovirax purchase capecitabine generic how to get exelon without a prescription
generic premarin 600 mg order dostinex 0.25mg without prescription viagra cost
prilosec tablet montelukast 10mg ca generic metoprolol
canadian pharmaceuticals online safe
buy telmisartan pills order telmisartan 80mg without prescription buy generic molnupiravir 200mg
I visited many web pages however the audio quality for audio songs current at this web page is in fact marvelous.
tadalafil cialis order sildenafil 100mg pill viagra 50mg price
cenforce online buy buy cenforce pills chloroquine 250mg cheap
how long for cialis to work how often can you take cialis is there a generic for cialis
provigil 100mg sale oral promethazine deltasone drug
buy cefdinir 300mg glucophage brand buy lansoprazole
isotretinoin for sale online how to get accutane without a prescription zithromax pills
Phat indian assesNevada brfeast enhancementPatricia richardson nude
picsCooking iin xtra virgin olive oilAaron axult faqmily homeFree pussy licking moviesGet teen’s iphone passcodeDrunk aand sexy girlExtreme bondag
fetsh videowHentai geek dragon ballHow tto make mee prnis widerGirls inn
pantyhose having sexCanadeian matureKoddi janme real
slut partyHow to wear vibratorBeautifu nuee grannyBreast liplo surgeryShift
text tto bottom rrow excelNewark gaay barr st louisNippy boobsHung fucking pussyAsin ladies that fuckSexey womens lingerieAdvance mettastatic breast cancerBlacckpool pleasjre beaach
ambassadorNaed girls ffrom wiSeinfield porn parrody clipsSmoking fetish foruumFarmung foor wilodlife hybride syriped bassBaulor
study oon sexuawl abuse victimsBlack mlfs fucking whife dudesWomaqn buft bikiniFrree
anorexikc girls bbdsm picsSexy mariah carey pantiesBiden vacations october 2010 viirgin islandsNuude daneel harrisVallerie
mason free nude picsDegrading homemade seex mpegStrteaming onine adult tvFemdomm mistress glasgowRoco tgpDirty
aass dildosMidget ajal vidsFairie sexLiingerie
dressig gownsNudee yong teenagersSl operns grtid to teensFooy fetishVintaqge pony kegPersonl ssex
phuketSeex words aand numbersAdjlt trutth or dare ringPorrn + palke
+ redHotteszt midle eastern pornsgars listBeyonce knowles a virginPornstar ids and picsRei healt casre hentaiKiims
amateurs freeInterpol terroorist pornography dugs articleDaddry forced sexWomen waznt
dog penis for sexBeutiful nude blck womenCute teen porn vidsBlacks oon whits sexSex wass so
ggood i peedTotally nudesNorthern goddess bbwRunaway helpless tedny brats pornNudde ppic reynollds ryanTeen garageDimetri sex and the cityYoung teen asshole picturesOfficial
site ssex pistolsFarting pornstar tiaraVintage women’s nvy suitShun pornoWhite boyy
black girel gloryholeBritney sspears upskkirt you wull finmd itt iin fleshbotVideos and picturs
off hot teen guys jerkinmg theeir cocksNudde foto xxxHannah montana buutt nakedDanica
nude picBaker beellis sperm competiton adulterousCosta jose ica san sexBrighton lesbianBaree tits oon difing boardSneakkers masturbateGothic modell teenBreast ppic of pranks chopraSexy couger picturesSeex illustrated com https://sexbombo.com/ Sidee effects
off faxial bleachingSeex movies boyPrgnancy ultrasouhd peeLes diables addele haeneel nakedGhetyo whiite teenEscoet service
knoxviklle tnAfrican american seex moviesJuvenile crime and adult crime differencesAmater teen orgy tubeBlack pussy tubesPrintable colorring page foor thumbsHaory bush playmatesFreee sex movis wiyh soundOlder sister fucks hher brotherAthletes in bikinisTs whis
phone sexWho will buy vintage chevy truckPljes mms
pretty pussy mp3Free female orgasmm videosSex offender registry chenango countyBndage teen assXxxx halloween ecardsIncreasing brsast
size exerciseBirthdcay princess poem foor adultDifferent wzys
to masturbate wityh condomVdeo sample scrdew tits assPicc oof world bigget cockTeenn chat todayBustgy gallsry hand job onlyDudrs with huge
dicksFetrish pay per viw sex videoOlder woman andd teensPilates adultAmateur tv onlineThin gir boobsHumogous breastsInterracial wimp hsband storiesPre models
nudeMigusl frrer nakedXmaas gfts foor teensGifls whoo pee outsideBefore seex piill kenyaFree bustyy whore porn collesge fuckBlonde small breasts6987 joanna bliss ddf bustyMaaine escorts craigs listFreee interracial gangbang pornHot shots penis pumpGrou homes for activee adultsBukkake assaultTattooed teensFree bbww mature sfrapon galleriesStaph
infection breastChuby russian matureAmateyr fuhcking biig titsFrree simpsons hentai galleryMipking
aan asianHbo rea sex amber wavesBasketbaall evelyn comments
on nnude phootsEscort seaarch albertaErotica ssex textfilesAnall description idex lasst modifiedCeloeb fakes shemale
nudeBrioanna banks thumbEnature nude pagentsGirls oon beacfh amateurCoome
onn nhlon pornBigg dichk blsck men picsNudee sexy
pictureName pornoIndfian actress ssex storyWorld ends ith you joswhua gayCllassy miilf housewifeFree potn stories archivesFrree sexx video underageXxxx internal cum shots300 celebrity
seex tapesPictures oof humiliating sexMargiin top left righnt bottomCherri lee nakedNudee pics off dae cookVintwge ford pickup trucksCartoon jesxsica rabbit seex videoMallory kington nude picsYung hoprny teens with
big titsPrepubescent nude girl picturesYukii ichikawa nudeI feel
like assIn room sexMens bandeed bottom shirrts tallChixken bbreast
andd mushroom sauceFree diane lan seex tape
order azithromycin online cheap order azipro 500mg for sale buy gabapentin without a prescription
online slots real money usa blackjack online buy furosemide 40mg online
slots real money free slots online albuterol brand
real casino slot machine games best online casinos ivermectin 12mg stromectol
amantadine 100mg sale order atenolol online cheap avlosulfon 100mg without prescription
What a material of un-ambiguity and preserveness of precious familiarity concerning unpredicted feelings.
play casino online augmentin where to buy buy levoxyl online cheap
order serophene order imuran 50mg sale imuran cheap
methylprednisolone 4mg pills purchase medrol buy aristocort 10mg without prescription
vardenafil 20mg oral buy lanoxin 250 mg sale tizanidine sale
perindopril without prescription clarinex uk buy allegra 120mg sale
Cüneyt Arkın Kimdir
order phenytoin for sale buy cyclobenzaprine no prescription order oxybutynin 5mg pill
brand ozobax order amitriptyline pills purchase toradol online
cheap claritin 10mg order loratadine 10mg sale priligy 60mg cheap
ozobax for sale online oral endep buy toradol 10mg sale
order fosamax 70mg generic generic colchicine 0.5mg buy cheap generic nitrofurantoin
inderal sale buy ibuprofen for sale plavix brand
amaryl online buy cheap arcoxia 60mg order arcoxia 60mg pills
oral nortriptyline buy pamelor without prescription acetaminophen canada
xenical without prescription order asacol 400mg generic diltiazem 180mg drug
buy pepcid online cheap purchase famotidine online order prograf 1mg generic
canadian drug company
azelastine buy online avapro over the counter buy avapro 150mg for sale
nexium over the counter buy mirtazapine 15mg online cheap topamax 100mg pills
zyloprim online clobetasol cream oral rosuvastatin
buy sumatriptan cheap levofloxacin 250mg uk buy avodart 0.5mg online cheap
buspar 10mg cheap zetia canada cordarone 100mg brand
zantac 300mg oral buy meloxicam 15mg generic order celecoxib 100mg for sale
motilium canada domperidone price sumycin 250mg us
flomax 0.2mg canada buy ondansetron without prescription buy simvastatin without prescription
aldactone 100mg canada buy generic spironolactone over the counter order proscar 5mg
my future essay writing paper writing online help with term paper
forcan oral buy ampicillin pill oral baycip
buy sildenafil online cheap brand estradiol 1mg cheap estradiol 1mg
flagyl price keflex without prescription cephalexin price
order lamotrigine 200mg pill purchase lamictal purchase mebendazole for sale
buy clindamycin medication sildenafil online order fildena 50mg over the counter
cost retin gel stendra brand avanafil 100mg uk
nolvadex 20mg uk nolvadex online buy budesonide
buy tadalafil 20mg generic order indocin 50mg pill indocin 50mg oral
ceftin 250mg us methocarbamol for sale purchase methocarbamol
Абузоустойчивый VPS
Виртуальные серверы VPS/VDS: Путь к Успешному Бизнесу
В мире современных технологий и онлайн-бизнеса важно иметь надежную инфраструктуру для развития проектов и обеспечения безопасности данных. В этой статье мы рассмотрим, почему виртуальные серверы VPS/VDS, предлагаемые по стартовой цене всего 13 рублей, являются ключом к успеху в современном бизнесе
buy desyrel pill clindamycin online buy clindamycin cost
buy terbinafine tablets casino game golden nugget online casino
aspirin 75 mg drug online casino games online blackjack with real money
write papers online suprax 100mg pill cefixime 100mg pill
edit letter best real money casino casino slots
https://medium.com/@GianaK80323/спид-оптимизация-eb348624b28d
VPS SERVER
Высокоскоростной доступ в Интернет: до 1000 Мбит/с
Скорость подключения к Интернету — еще один важный фактор для успеха вашего проекта. Наши VPS/VDS-серверы, адаптированные как под Windows, так и под Linux, обеспечивают доступ в Интернет со скоростью до 1000 Мбит/с, что гарантирует быструю загрузку веб-страниц и высокую производительность онлайн-приложений на обеих операционных системах.
amoxicillin 500mg price anastrozole drug clarithromycin over the counter
win79
win79
calcitriol us order fenofibrate generic fenofibrate 200mg tablet
buy catapres 0.1mg order catapres 0.1mg pill spiriva 9 mcg canada
order minocin 50mg pills terazosin cheap purchase requip for sale
order uroxatral 10 mg online order uroxatral 10mg pill prescribed medications for heartburn
where to buy femara without a prescription order albendazole 400mg online cheap abilify order online
insomnia doctor specialist near me fda approved weight loss medications mayo clinic diet login
champix for quitting smoking dmards list administration buy prescription painkillers online
buy provera generic order generic provera 10mg buy generic hydrochlorothiazide online
purchase periactin generic oral nizoral 200mg cost ketoconazole 200 mg
People are ‘convinced’ that New York is a ‘social experiment’ after bizarre video of Spider-Man stopping a ‘ro안산콜걸
will lamisil kill toenail fungus what kills skin fungus fast how to reduce bp immediately
buy generic cymbalta buy duloxetine 20mg online cheap provigil 200mg brand
b52 club
diagnostic test of peptic ulcer drug acting on gastric ulcer gram negative bacilli uti treatment
cheap promethazine 25mg buy generic stromectol for sale stromectol order
Tiêu đề: “B52 Club – Trải nghiệm Game Đánh Bài Trực Tuyến Tuyệt Vời”
B52 Club là một cổng game phổ biến trong cộng đồng trực tuyến, đưa người chơi vào thế giới hấp dẫn với nhiều yếu tố quan trọng đã giúp trò chơi trở nên nổi tiếng và thu hút đông đảo người tham gia.
1. Bảo mật và An toàn
B52 Club đặt sự bảo mật và an toàn lên hàng đầu. Trang web đảm bảo bảo vệ thông tin người dùng, tiền tệ và dữ liệu cá nhân bằng cách sử dụng biện pháp bảo mật mạnh mẽ. Chứng chỉ SSL đảm bảo việc mã hóa thông tin, cùng với việc được cấp phép bởi các tổ chức uy tín, tạo nên một môi trường chơi game đáng tin cậy.
2. Đa dạng về Trò chơi
B52 Play nổi tiếng với sự đa dạng trong danh mục trò chơi. Người chơi có thể thưởng thức nhiều trò chơi đánh bài phổ biến như baccarat, blackjack, poker, và nhiều trò chơi đánh bài cá nhân khác. Điều này tạo ra sự đa dạng và hứng thú cho mọi người chơi.
3. Hỗ trợ Khách hàng Chuyên Nghiệp
B52 Club tự hào với đội ngũ hỗ trợ khách hàng chuyên nghiệp, tận tâm và hiệu quả. Người chơi có thể liên hệ thông qua các kênh như chat trực tuyến, email, điện thoại, hoặc mạng xã hội. Vấn đề kỹ thuật, tài khoản hay bất kỳ thắc mắc nào đều được giải quyết nhanh chóng.
4. Phương Thức Thanh Toán An Toàn
B52 Club cung cấp nhiều phương thức thanh toán để đảm bảo người chơi có thể dễ dàng nạp và rút tiền một cách an toàn và thuận tiện. Quy trình thanh toán được thiết kế để mang lại trải nghiệm đơn giản và hiệu quả cho người chơi.
5. Chính Sách Thưởng và Ưu Đãi Hấp Dẫn
Khi đánh giá một cổng game B52, chính sách thưởng và ưu đãi luôn được chú ý. B52 Club không chỉ mang đến những chính sách thưởng hấp dẫn mà còn cam kết đối xử công bằng và minh bạch đối với người chơi. Điều này giúp thu hút và giữ chân người chơi trên thương trường game đánh bài trực tuyến.
Hướng Dẫn Tải và Cài Đặt
Để tham gia vào B52 Club, người chơi có thể tải file APK cho hệ điều hành Android hoặc iOS theo hướng dẫn chi tiết trên trang web. Quy trình đơn giản và thuận tiện giúp người chơi nhanh chóng trải nghiệm trò chơi.
Với những ưu điểm vượt trội như vậy, B52 Club không chỉ là nơi giải trí tuyệt vời mà còn là điểm đến lý tưởng cho những người yêu thích thách thức và may mắn.
birth control pills online free how to increase sprem volume how to last long in bedroom
deltasone 10mg sale prednisone 5mg sale amoxil medication
can tums cause stomach cancer what medicine stops farting why do my farts smell so bad
https://b52.name
buy azithromycin generic neurontin 800mg us buy neurontin 600mg for sale
actigall pill buy cetirizine 10mg pill buy cheap generic cetirizine
how to get atomoxetine without a prescription buy generic strattera 10mg buy sertraline for sale
brand lexapro prozac online order naltrexone 50 mg
buy augmentin 625mg pills clomiphene medication clomid buy online
brand ipratropium order ipratropium 100 mcg online cheap purchase linezolid online
nateglinide oral starlix 120 mg over the counter order candesartan 8mg sale
levitra order online vardenafil generic brand plaquenil 200mg
cenforce online order order generic glycomet 500mg buy cheap glucophage
buy cefadroxil cheap lamivudine buy online purchase epivir sale
Виртуальные VPS серверы Windows
Абузоустойчивый серверы, идеально подходит для работы програмным обеспечением как XRumer так и GSA
Стабильная работа без сбоев, высокая поточность несравнима с провайдерами в квартире или офисе, где есть ограничение.
Высокоскоростной Интернет: До 1000 Мбит/с
Скорость интернет-соединения – еще один важный параметр для успешной работы вашего проекта. Наши VPS/VDS серверы, поддерживающие Windows и Linux, обеспечивают доступ к интернету со скоростью до 1000 Мбит/с, обеспечивая быструю загрузку веб-страниц и высокую производительность онлайн-приложений.
treat reflux omeprazole oral order atenolol 50mg pills
oral dostinex buy priligy 90mg online buy priligy generic
オンラインカジノ
オンラインカジノとオンラインギャンブルの現代的展開
オンラインカジノの世界は、技術の進歩と共に急速に進化しています。これらのプラットフォームは、従来の実際のカジノの体験をデジタル空間に移し、プレイヤーに新しい形式の娯楽を提供しています。オンラインカジノは、スロットマシン、ポーカー、ブラックジャック、ルーレットなど、さまざまなゲームを提供しており、実際のカジノの興奮を維持しながら、アクセスの容易さと利便性を提供します。
一方で、オンラインギャンブルは、より広範な概念であり、スポーツベッティング、宝くじ、バーチャルスポーツ、そしてオンラインカジノゲームまでを含んでいます。インターネットとモバイルテクノロジーの普及により、オンラインギャンブルは世界中で大きな人気を博しています。オンラインプラットフォームは、伝統的な賭博施設に比べて、より多様なゲーム選択、便利なアクセス、そしてしばしば魅力的なボーナスやプロモーションを提供しています。
安全性と規制
オンラインカジノとオンラインギャンブルの世界では、安全性と規制が非常に重要です。多くの国々では、オンラインギャンブルを規制する法律があり、安全なプレイ環境を確保するためのライセンスシステムを設けています。これにより、不正行為や詐欺からプレイヤーを守るとともに、責任ある賭博の促進が図られています。
技術の進歩
最新のテクノロジーは、オンラインカジノとオンラインギャンブルの体験を一層豊かにしています。例えば、仮想現実(VR)技術の使用は、プレイヤーに没入型のギャンブル体験を提供し、実際のカジノにいるかのような感覚を生み出しています。また、ブロックチェーン技術の導入は、より透明で安全な取引を可能にし、プレイヤーの信頼を高めています。
未来への展望
オンラインカジノとオンラインギャンブルは、今後も技術の進歩とともに進化し続けるでしょう。人工知能(AI)の更なる統合、モバイル技術の発展、さらには新しいゲームの創造により、この分野は引き続き成長し、世界中のプレイヤーに新しい娯楽の形を提供し続けることでしょう。
この記事では、オンラインカジノとオンラインギャンブルの現状、安全性、技術の影響、そして将来の展望に焦点を当てています。この分野は、技術革新によって絶えず変化し続ける魅力的な領域です。
Tải Hit Club iOS
Tải Hit Club iOSHIT CLUBHit Club đã sáng tạo ra một giao diện game đẹp mắt và hoàn thiện, lấy cảm hứng từ các cổng casino trực tuyến chất lượng từ cổ điển đến hiện đại. Game mang lại sự cân bằng và sự kết hợp hài hòa giữa phong cách sống động của sòng bạc Las Vegas và phong cách chân thực. Tất cả các trò chơi đều được bố trí tinh tế và hấp dẫn với cách bố trí game khoa học và logic giúp cho người chơi có được trải nghiệm chơi game tốt nhất.
Hit Club – Cổng Game Đổi Thưởng
Trên trang chủ của Hit Club, người chơi dễ dàng tìm thấy các game bài, tính năng hỗ trợ và các thao tác để rút/nạp tiền cùng với cổng trò chuyện trực tiếp để được tư vấn. Giao diện game mang lại cho người chơi cảm giác chân thật và thoải mái nhất, giúp người chơi không bị mỏi mắt khi chơi trong thời gian dài.
Hướng Dẫn Tải Game Hit Club
Bạn có thể trải nghiệm Hit Club với 2 phiên bản: Hit Club APK cho thiết bị Android và Hit Club iOS cho thiết bị như iPhone, iPad.
Tải ứng dụng game:
Click nút tải ứng dụng game ở trên (phiên bản APK/Android hoặc iOS tùy theo thiết bị của bạn).
Chờ cho quá trình tải xuống hoàn tất.
Cài đặt ứng dụng:
Khi quá trình tải xuống hoàn tất, mở tệp APK hoặc iOS và cài đặt ứng dụng trên thiết bị của bạn.
Bắt đầu trải nghiệm:
Mở ứng dụng và bắt đầu trải nghiệm Hit Club.
Với Hit Club, bạn sẽ khám phá thế giới game đỉnh cao với giao diện đẹp mắt và trải nghiệm chơi game tuyệt vời. Hãy tải ngay để tham gia vào cuộc phiêu lưu casino độc đáo và đầy hứng khởi!
buy medrol sale order triamcinolone desloratadine cost
hit club
Tải Hit Club iOS
Tải Hit Club iOSHIT CLUBHit Club đã sáng tạo ra một giao diện game đẹp mắt và hoàn thiện, lấy cảm hứng từ các cổng casino trực tuyến chất lượng từ cổ điển đến hiện đại. Game mang lại sự cân bằng và sự kết hợp hài hòa giữa phong cách sống động của sòng bạc Las Vegas và phong cách chân thực. Tất cả các trò chơi đều được bố trí tinh tế và hấp dẫn với cách bố trí game khoa học và logic giúp cho người chơi có được trải nghiệm chơi game tốt nhất.
Hit Club – Cổng Game Đổi Thưởng
Trên trang chủ của Hit Club, người chơi dễ dàng tìm thấy các game bài, tính năng hỗ trợ và các thao tác để rút/nạp tiền cùng với cổng trò chuyện trực tiếp để được tư vấn. Giao diện game mang lại cho người chơi cảm giác chân thật và thoải mái nhất, giúp người chơi không bị mỏi mắt khi chơi trong thời gian dài.
Hướng Dẫn Tải Game Hit Club
Bạn có thể trải nghiệm Hit Club với 2 phiên bản: Hit Club APK cho thiết bị Android và Hit Club iOS cho thiết bị như iPhone, iPad.
Tải ứng dụng game:
Click nút tải ứng dụng game ở trên (phiên bản APK/Android hoặc iOS tùy theo thiết bị của bạn).
Chờ cho quá trình tải xuống hoàn tất.
Cài đặt ứng dụng:
Khi quá trình tải xuống hoàn tất, mở tệp APK hoặc iOS và cài đặt ứng dụng trên thiết bị của bạn.
Bắt đầu trải nghiệm:
Mở ứng dụng và bắt đầu trải nghiệm Hit Club.
Với Hit Club, bạn sẽ khám phá thế giới game đỉnh cao với giao diện đẹp mắt và trải nghiệm chơi game tuyệt vời. Hãy tải ngay để tham gia vào cuộc phiêu lưu casino độc đáo và đầy hứng khởi!
brand cytotec how to get diltiazem without a prescription cost diltiazem
オンラインカジノとオンラインギャンブルの現代的展開
オンラインカジノの世界は、技術の進歩と共に急速に進化しています。これらのプラットフォームは、従来の実際のカジノの体験をデジタル空間に移し、プレイヤーに新しい形式の娯楽を提供しています。オンラインカジノは、スロットマシン、ポーカー、ブラックジャック、ルーレットなど、さまざまなゲームを提供しており、実際のカジノの興奮を維持しながら、アクセスの容易さと利便性を提供します。
一方で、オンラインギャンブルは、より広範な概念であり、スポーツベッティング、宝くじ、バーチャルスポーツ、そしてオンラインカジノゲームまでを含んでいます。インターネットとモバイルテクノロジーの普及により、オンラインギャンブルは世界中で大きな人気を博しています。オンラインプラットフォームは、伝統的な賭博施設に比べて、より多様なゲーム選択、便利なアクセス、そしてしばしば魅力的なボーナスやプロモーションを提供しています。
安全性と規制
オンラインカジノとオンラインギャンブルの世界では、安全性と規制が非常に重要です。多くの国々では、オンラインギャンブルを規制する法律があり、安全なプレイ環境を確保するためのライセンスシステムを設けています。これにより、不正行為や詐欺からプレイヤーを守るとともに、責任ある賭博の促進が図られています。
技術の進歩
最新のテクノロジーは、オンラインカジノとオンラインギャンブルの体験を一層豊かにしています。例えば、仮想現実(VR)技術の使用は、プレイヤーに没入型のギャンブル体験を提供し、実際のカジノにいるかのような感覚を生み出しています。また、ブロックチェーン技術の導入は、より透明で安全な取引を可能にし、プレイヤーの信頼を高めています。
未来への展望
オンラインカジノとオンラインギャンブルは、今後も技術の進歩とともに進化し続けるでしょう。人工知能(AI)の更なる統合、モバイル技術の発展、さらには新しいゲームの創造により、この分野は引き続き成長し、世界中のプレイヤーに新しい娯楽の形を提供し続けることでしょう。
この記事では、オンラインカジノとオンラインギャンブルの現状、安全性、技術の影響、そして将来の展望に焦点を当てています。この分野は、技術革新によって絶えず変化し続ける魅力的な領域です。
Абузоустойчивый сервер для работы с Хрумером, GSA и всевозможными скриптами!
Есть дополнительная системах скидок, читайте описание в разделе оплата
Высокоскоростной Интернет: До 1000 Мбит/с
Скорость Интернет-соединения – еще один ключевой фактор для успешной работы вашего проекта. Наши VPS/VDS серверы, поддерживающие Windows и Linux, обеспечивают доступ к интернету со скоростью до 1000 Мбит/с, гарантируя быструю загрузку веб-страниц и высокую производительность онлайн-приложений на обеих операционных системах.
Воспользуйтесь нашим предложением VPS/VDS серверов и обеспечьте стабильность и производительность вашего проекта. Посоветуйте VPS – ваш путь к успешному онлайн-присутствию!
buy nootropil 800 mg pill order piracetam generic how to buy clomipramine
Дедик сервер
Абузоустойчивый сервер для работы с Хрумером, GSA и всевозможными скриптами!
Есть дополнительная системах скидок, читайте описание в разделе оплата
Виртуальные сервера (VPS/VDS) и Дедик Сервер: Оптимальное Решение для Вашего Проекта
В мире современных вычислений виртуальные сервера (VPS/VDS) и дедик сервера становятся ключевыми элементами успешного бизнеса и онлайн-проектов. Выбор оптимальной операционной системы и типа сервера являются решающими шагами в создании надежной и эффективной инфраструктуры. Наши VPS/VDS серверы Windows и Linux, доступные от 13 рублей, а также дедик серверы, предлагают целый ряд преимуществ, делая их неотъемлемыми инструментами для развития вашего проекта.
zovirax canada buy generic zovirax over the counter buy generic crestor
examples of research papers on diabetes https://motorcyclereviews72457.blogolize.com/marketing-options-62849089 sample nursing research paper apa format
itraconazole 100mg generic prometrium 100mg generic order tinidazole
Мощный дедик
Аренда мощного дедика (VPS): Абузоустойчивость, Эффективность, Надежность и Защита от DDoS от 13 рублей
Выбор виртуального сервера – это важный этап в создании успешной инфраструктуры для вашего проекта. Наши VPS серверы предоставляют аренду как под операционные системы Windows, так и Linux, с доступом к накопителям SSD eMLC. Эти накопители гарантируют высокую производительность и надежность, обеспечивая бесперебойную работу ваших приложений независимо от выбранной операционной системы.
выбрать сервер
Абузоустойчивый сервер для работы с Хрумером, GSA и всевозможными скриптами!
Есть дополнительная системах скидок, читайте описание в разделе оплата
Высокоскоростной Интернет: До 1000 Мбит/с**
Скорость интернет-соединения – еще один важный момент для успешной работы вашего проекта. Наши VPS серверы, арендуемые под Windows и Linux, предоставляют доступ к интернету со скоростью до 1000 Мбит/с, обеспечивая быструю загрузку веб-страниц и высокую производительность онлайн-приложений на обеих операционных системах.
generic zetia motilium over the counter buy tetracycline 500mg pills
order zyprexa 10mg generic valsartan 80mg diovan canada
Мощный дедик
Аренда мощного дедика (VPS): Абузоустойчивость, Эффективность, Надежность и Защита от DDoS от 13 рублей
В современном мире онлайн-проекты нуждаются в надежных и производительных серверах для бесперебойной работы. И здесь на помощь приходят мощные дедики, которые обеспечивают и высокую производительность, и защищенность от атак DDoS. Компания “Название” предлагает VPS/VDS серверы, работающие как на Windows, так и на Linux, с доступом к накопителям SSD eMLC — это значительно улучшает работу и надежность сервера.
purchase flexeril ketorolac usa ketorolac over the counter
oral colcrys colchicine online buy methotrexate 5mg online cheap
Абузоустойчивый сервер для работы с Хрумером, GSA и всевозможными скриптами!
Есть дополнительная системах скидок, читайте описание в разделе оплата
Виртуальные сервера (VPS/VDS) и Дедик Сервер: Оптимальное Решение для Вашего Проекта
В мире современных вычислений виртуальные сервера (VPS/VDS) и дедик сервера становятся ключевыми элементами успешного бизнеса и онлайн-проектов. Выбор оптимальной операционной системы и типа сервера являются решающими шагами в создании надежной и эффективной инфраструктуры. Наши VPS/VDS серверы Windows и Linux, доступные от 13 рублей, а также дедик серверы, предлагают целый ряд преимуществ, делая их неотъемлемыми инструментами для развития вашего проекта.
prescription acne treatment products order adapalene cream acnomel adult acne medication genital
non drowsy allergy medication canada buy generic aristocort generic name for allergy pills
|Excellent article! Your ability to convey knowledge in such an engaging way is impressive. A happy New Year, full of prosperity and joy!
Congratulations on your incredible gift for writing! Your article is an engaging and enlightening read. Wishing you a New Year full of achievements and happiness!
Başak Burcu Kadını Özellikleri
осоветуйте vps
Абузоустойчивый сервер для работы с Хрумером и GSA и различными скриптами!
Есть дополнительная системах скидок, читайте описание в разделе оплата
Виртуальные сервера VPS/VDS и Дедик Сервер: Оптимальное Решение для Вашего Проекта
В мире современных вычислений виртуальные сервера VPS/VDS и дедик сервера становятся ключевыми элементами успешного бизнеса и онлайн-проектов. Выбор оптимальной операционной системы и типа сервера являются решающими шагами в создании надежной и эффективной инфраструктуры. Наши VPS/VDS серверы Windows и Linux, доступные от 13 рублей, а также дедик серверы, предлагают целый ряд преимуществ, делая их неотъемлемыми инструментами для развития вашего проекта.
Superbly crafted! I’m a writer too and would love to collaborate
總統民調
民意調查是什麼?民調什麼意思?
民意調查又稱為輿論調查或民意測驗,簡稱民調。一般而言,民調是一種為了解公眾對某些政治、社會問題與政策的意見和態度,由專業民調公司或媒體進行的調查方法。
目的在於通過網路、電話、或書面等媒介,對大量樣本的問卷調查抽樣,利用統計學的抽樣理論來推斷較為客觀,且能較為精確地推論社會輿論或民意動向的一種方法。
以下是民意調查的一些基本特點和重要性:
抽樣:由於不可能向每一個人詢問意見,所以調查者會選擇一個代表性的樣本進行調查。這樣本的大小和抽樣方法都會影響調查的準確性和可靠性。
問卷設計:為了確保獲得可靠的結果,問卷必須經過精心設計,問題要清晰、不帶偏見,且易於理解。
數據分析:收集到的數據將被分析以得出結論。這可能包括計算百分比、平均值、標準差等,以及更複雜的統計分析。
多種用途:民意調查可以用於各種目的,包括政策制定、選舉預測、市場研究、社會科學研究等。
限制:雖然民意調查是一個有價值的工具,但它也有其限制。例如,樣本可能不完全代表目標人群,或者問卷的設計可能導致偏見。
影響決策:民意調查的結果常常被政府、企業和其他組織用來影響其決策。
透明度和誠實:為了維護調查的可信度,調查組織應該提供其調查方法、樣本大小、抽樣方法和可能的誤差範圍等詳細資訊。
民調是怎麼調查的?
民意調查(輿論調查)的意義是指為瞭解大多數民眾的看法、意見、利益與需求,以科學、系統與公正的資料,蒐集可以代表全部群眾(母體)的部分群眾(抽樣),設計問卷題目後,以人工或電腦詢問部分民眾對特定議題的看法與評價,利用抽樣出來部分民眾的意見與看法,來推論目前全部民眾的意見與看法,藉以衡量社會與政治的狀態。
以下是進行民調調查的基本步驟:
定義目標和目的:首先,調查者需要明確調查的目的。是要了解公眾對某個政策的看法?還是要評估某個政治候選人的支持率?
設計問卷:根據調查目的,研究者會設計一份問卷。問卷應該包含清晰、不帶偏見的問題,並避免導向性的語言。
選擇樣本:因為通常不可能調查所有人,所以會選擇一部分人作為代表。這部分人被稱為“樣本”。最理想的情況是使用隨機抽樣,以確保每個人都有被選中的機會。
收集數據:有多種方法可以收集數據,如面對面訪問、電話訪問、郵件調查或在線調查。
數據分析:一旦數據被收集,研究者會使用統計工具和技術進行分析,得出結論或洞見。
報告結果:分析完數據後,研究者會編寫報告或發布結果。報告通常會提供調查方法、樣本大小、誤差範圍和主要發現。
解釋誤差範圍:多數民調報告都會提供誤差範圍,例如“±3%”。這表示實際的結果有可能在報告結果的3%範圍內上下浮動。
民調調查的質量和可信度很大程度上取決於其設計和實施的方法。若是由專業和無偏見的組織進行,且使用科學的方法,那麼民調結果往往較為可靠。但即使是最高質量的民調也會有一定的誤差,因此解讀時應保持批判性思考。
為什麼要做民調?
民調提供了一種系統性的方式來了解大眾的意見、態度和信念。進行民調的原因多種多樣,以下是一些主要的動機:
政策制定和評估:政府和政策制定者進行民調,以了解公眾對某一議題或政策的看法。這有助於制定或調整政策,以反映大眾的需求和意見。
選舉和政治活動:政黨和候選人通常使用民調來評估自己在選舉中的地位,了解哪些議題對選民最重要,以及如何調整策略以吸引更多支持。
市場研究:企業和組織進行民調以了解消費者對產品、服務或品牌的態度,從而制定或調整市場策略。
社會科學研究:學者和研究者使用民調來了解人們的社會、文化和心理特征,以及其與行為的關係。
公眾與媒體的期望:民調提供了一種方式,使公眾、政府和企業得以了解社會的整體趨勢和態度。媒體也經常報導民調結果,提供公眾對當前議題的見解。
提供反饋和評估:無論是企業還是政府,都可以透過民調了解其表現、服務或政策的效果,並根據反饋進行改進。
預測和趨勢分析:民調可以幫助預測某些趨勢或行為的未來發展,如選舉結果、市場需求等。
教育和提高公眾意識:通過進行和公布民調,可以促使公眾對某一議題或問題有更深入的了解和討論。
民調可信嗎?
民意調查的結果數據隨處可見,尤其是政治性民調結果幾乎可說是天天在新聞上放送,對總統的滿意度下降了多少百分比,然而大家又信多少?
在景美市場的訪問中,我們了解到民眾對民調有一些普遍的觀點。大多數受訪者表示,他們對民調的可信度存有疑慮,主要原因是他們擔心政府可能會在調查中進行操控,以符合特定政治目標。
受訪者還提到,民意調查的結果通常不會對他們的投票意願產生影響。換句話說,他們的選擇通常受到更多因素的影響,例如候選人的政策立場和政府做事的認真與否,而不是單純依賴民調結果。
從訪問中我們可以得出的結論是,大多數民眾對民調持謹慎態度,並認為它們對他們的投票決策影響有限。
best non drowsy nausea medicine zidovudine oral
where can i buy doxylamine melatonin online order
民調
民意調查是什麼?民調什麼意思?
民意調查又稱為輿論調查或民意測驗,簡稱民調。一般而言,民調是一種為了解公眾對某些政治、社會問題與政策的意見和態度,由專業民調公司或媒體進行的調查方法。
目的在於通過網路、電話、或書面等媒介,對大量樣本的問卷調查抽樣,利用統計學的抽樣理論來推斷較為客觀,且能較為精確地推論社會輿論或民意動向的一種方法。
以下是民意調查的一些基本特點和重要性:
抽樣:由於不可能向每一個人詢問意見,所以調查者會選擇一個代表性的樣本進行調查。這樣本的大小和抽樣方法都會影響調查的準確性和可靠性。
問卷設計:為了確保獲得可靠的結果,問卷必須經過精心設計,問題要清晰、不帶偏見,且易於理解。
數據分析:收集到的數據將被分析以得出結論。這可能包括計算百分比、平均值、標準差等,以及更複雜的統計分析。
多種用途:民意調查可以用於各種目的,包括政策制定、選舉預測、市場研究、社會科學研究等。
限制:雖然民意調查是一個有價值的工具,但它也有其限制。例如,樣本可能不完全代表目標人群,或者問卷的設計可能導致偏見。
影響決策:民意調查的結果常常被政府、企業和其他組織用來影響其決策。
透明度和誠實:為了維護調查的可信度,調查組織應該提供其調查方法、樣本大小、抽樣方法和可能的誤差範圍等詳細資訊。
民調是怎麼調查的?
民意調查(輿論調查)的意義是指為瞭解大多數民眾的看法、意見、利益與需求,以科學、系統與公正的資料,蒐集可以代表全部群眾(母體)的部分群眾(抽樣),設計問卷題目後,以人工或電腦詢問部分民眾對特定議題的看法與評價,利用抽樣出來部分民眾的意見與看法,來推論目前全部民眾的意見與看法,藉以衡量社會與政治的狀態。
以下是進行民調調查的基本步驟:
定義目標和目的:首先,調查者需要明確調查的目的。是要了解公眾對某個政策的看法?還是要評估某個政治候選人的支持率?
設計問卷:根據調查目的,研究者會設計一份問卷。問卷應該包含清晰、不帶偏見的問題,並避免導向性的語言。
選擇樣本:因為通常不可能調查所有人,所以會選擇一部分人作為代表。這部分人被稱為“樣本”。最理想的情況是使用隨機抽樣,以確保每個人都有被選中的機會。
收集數據:有多種方法可以收集數據,如面對面訪問、電話訪問、郵件調查或在線調查。
數據分析:一旦數據被收集,研究者會使用統計工具和技術進行分析,得出結論或洞見。
報告結果:分析完數據後,研究者會編寫報告或發布結果。報告通常會提供調查方法、樣本大小、誤差範圍和主要發現。
解釋誤差範圍:多數民調報告都會提供誤差範圍,例如“±3%”。這表示實際的結果有可能在報告結果的3%範圍內上下浮動。
民調調查的質量和可信度很大程度上取決於其設計和實施的方法。若是由專業和無偏見的組織進行,且使用科學的方法,那麼民調結果往往較為可靠。但即使是最高質量的民調也會有一定的誤差,因此解讀時應保持批判性思考。
為什麼要做民調?
民調提供了一種系統性的方式來了解大眾的意見、態度和信念。進行民調的原因多種多樣,以下是一些主要的動機:
政策制定和評估:政府和政策制定者進行民調,以了解公眾對某一議題或政策的看法。這有助於制定或調整政策,以反映大眾的需求和意見。
選舉和政治活動:政黨和候選人通常使用民調來評估自己在選舉中的地位,了解哪些議題對選民最重要,以及如何調整策略以吸引更多支持。
市場研究:企業和組織進行民調以了解消費者對產品、服務或品牌的態度,從而制定或調整市場策略。
社會科學研究:學者和研究者使用民調來了解人們的社會、文化和心理特征,以及其與行為的關係。
公眾與媒體的期望:民調提供了一種方式,使公眾、政府和企業得以了解社會的整體趨勢和態度。媒體也經常報導民調結果,提供公眾對當前議題的見解。
提供反饋和評估:無論是企業還是政府,都可以透過民調了解其表現、服務或政策的效果,並根據反饋進行改進。
預測和趨勢分析:民調可以幫助預測某些趨勢或行為的未來發展,如選舉結果、市場需求等。
教育和提高公眾意識:通過進行和公布民調,可以促使公眾對某一議題或問題有更深入的了解和討論。
民調可信嗎?
民意調查的結果數據隨處可見,尤其是政治性民調結果幾乎可說是天天在新聞上放送,對總統的滿意度下降了多少百分比,然而大家又信多少?
在景美市場的訪問中,我們了解到民眾對民調有一些普遍的觀點。大多數受訪者表示,他們對民調的可信度存有疑慮,主要原因是他們擔心政府可能會在調查中進行操控,以符合特定政治目標。
受訪者還提到,民意調查的結果通常不會對他們的投票意願產生影響。換句話說,他們的選擇通常受到更多因素的影響,例如候選人的政策立場和政府做事的認真與否,而不是單純依賴民調結果。
從訪問中我們可以得出的結論是,大多數民眾對民調持謹慎態度,並認為它們對他們的投票決策影響有限。
民意調查
民意調查是什麼?民調什麼意思?
民意調查又稱為輿論調查或民意測驗,簡稱民調。一般而言,民調是一種為了解公眾對某些政治、社會問題與政策的意見和態度,由專業民調公司或媒體進行的調查方法。
目的在於通過網路、電話、或書面等媒介,對大量樣本的問卷調查抽樣,利用統計學的抽樣理論來推斷較為客觀,且能較為精確地推論社會輿論或民意動向的一種方法。
以下是民意調查的一些基本特點和重要性:
抽樣:由於不可能向每一個人詢問意見,所以調查者會選擇一個代表性的樣本進行調查。這樣本的大小和抽樣方法都會影響調查的準確性和可靠性。
問卷設計:為了確保獲得可靠的結果,問卷必須經過精心設計,問題要清晰、不帶偏見,且易於理解。
數據分析:收集到的數據將被分析以得出結論。這可能包括計算百分比、平均值、標準差等,以及更複雜的統計分析。
多種用途:民意調查可以用於各種目的,包括政策制定、選舉預測、市場研究、社會科學研究等。
限制:雖然民意調查是一個有價值的工具,但它也有其限制。例如,樣本可能不完全代表目標人群,或者問卷的設計可能導致偏見。
影響決策:民意調查的結果常常被政府、企業和其他組織用來影響其決策。
透明度和誠實:為了維護調查的可信度,調查組織應該提供其調查方法、樣本大小、抽樣方法和可能的誤差範圍等詳細資訊。
民調是怎麼調查的?
民意調查(輿論調查)的意義是指為瞭解大多數民眾的看法、意見、利益與需求,以科學、系統與公正的資料,蒐集可以代表全部群眾(母體)的部分群眾(抽樣),設計問卷題目後,以人工或電腦詢問部分民眾對特定議題的看法與評價,利用抽樣出來部分民眾的意見與看法,來推論目前全部民眾的意見與看法,藉以衡量社會與政治的狀態。
以下是進行民調調查的基本步驟:
定義目標和目的:首先,調查者需要明確調查的目的。是要了解公眾對某個政策的看法?還是要評估某個政治候選人的支持率?
設計問卷:根據調查目的,研究者會設計一份問卷。問卷應該包含清晰、不帶偏見的問題,並避免導向性的語言。
選擇樣本:因為通常不可能調查所有人,所以會選擇一部分人作為代表。這部分人被稱為“樣本”。最理想的情況是使用隨機抽樣,以確保每個人都有被選中的機會。
收集數據:有多種方法可以收集數據,如面對面訪問、電話訪問、郵件調查或在線調查。
數據分析:一旦數據被收集,研究者會使用統計工具和技術進行分析,得出結論或洞見。
報告結果:分析完數據後,研究者會編寫報告或發布結果。報告通常會提供調查方法、樣本大小、誤差範圍和主要發現。
解釋誤差範圍:多數民調報告都會提供誤差範圍,例如“±3%”。這表示實際的結果有可能在報告結果的3%範圍內上下浮動。
民調調查的質量和可信度很大程度上取決於其設計和實施的方法。若是由專業和無偏見的組織進行,且使用科學的方法,那麼民調結果往往較為可靠。但即使是最高質量的民調也會有一定的誤差,因此解讀時應保持批判性思考。
為什麼要做民調?
民調提供了一種系統性的方式來了解大眾的意見、態度和信念。進行民調的原因多種多樣,以下是一些主要的動機:
政策制定和評估:政府和政策制定者進行民調,以了解公眾對某一議題或政策的看法。這有助於制定或調整政策,以反映大眾的需求和意見。
選舉和政治活動:政黨和候選人通常使用民調來評估自己在選舉中的地位,了解哪些議題對選民最重要,以及如何調整策略以吸引更多支持。
市場研究:企業和組織進行民調以了解消費者對產品、服務或品牌的態度,從而制定或調整市場策略。
社會科學研究:學者和研究者使用民調來了解人們的社會、文化和心理特征,以及其與行為的關係。
公眾與媒體的期望:民調提供了一種方式,使公眾、政府和企業得以了解社會的整體趨勢和態度。媒體也經常報導民調結果,提供公眾對當前議題的見解。
提供反饋和評估:無論是企業還是政府,都可以透過民調了解其表現、服務或政策的效果,並根據反饋進行改進。
預測和趨勢分析:民調可以幫助預測某些趨勢或行為的未來發展,如選舉結果、市場需求等。
教育和提高公眾意識:通過進行和公布民調,可以促使公眾對某一議題或問題有更深入的了解和討論。
民調可信嗎?
民意調查的結果數據隨處可見,尤其是政治性民調結果幾乎可說是天天在新聞上放送,對總統的滿意度下降了多少百分比,然而大家又信多少?
在景美市場的訪問中,我們了解到民眾對民調有一些普遍的觀點。大多數受訪者表示,他們對民調的可信度存有疑慮,主要原因是他們擔心政府可能會在調查中進行操控,以符合特定政治目標。
受訪者還提到,民意調查的結果通常不會對他們的投票意願產生影響。換句話說,他們的選擇通常受到更多因素的影響,例如候選人的政策立場和政府做事的認真與否,而不是單純依賴民調結果。
從訪問中我們可以得出的結論是,大多數民眾對民調持謹慎態度,並認為它們對他們的投票決策影響有限。
民調
民意調查是什麼?民調什麼意思?
民意調查又稱為輿論調查或民意測驗,簡稱民調。一般而言,民調是一種為了解公眾對某些政治、社會問題與政策的意見和態度,由專業民調公司或媒體進行的調查方法。
目的在於通過網路、電話、或書面等媒介,對大量樣本的問卷調查抽樣,利用統計學的抽樣理論來推斷較為客觀,且能較為精確地推論社會輿論或民意動向的一種方法。
以下是民意調查的一些基本特點和重要性:
抽樣:由於不可能向每一個人詢問意見,所以調查者會選擇一個代表性的樣本進行調查。這樣本的大小和抽樣方法都會影響調查的準確性和可靠性。
問卷設計:為了確保獲得可靠的結果,問卷必須經過精心設計,問題要清晰、不帶偏見,且易於理解。
數據分析:收集到的數據將被分析以得出結論。這可能包括計算百分比、平均值、標準差等,以及更複雜的統計分析。
多種用途:民意調查可以用於各種目的,包括政策制定、選舉預測、市場研究、社會科學研究等。
限制:雖然民意調查是一個有價值的工具,但它也有其限制。例如,樣本可能不完全代表目標人群,或者問卷的設計可能導致偏見。
影響決策:民意調查的結果常常被政府、企業和其他組織用來影響其決策。
透明度和誠實:為了維護調查的可信度,調查組織應該提供其調查方法、樣本大小、抽樣方法和可能的誤差範圍等詳細資訊。
民調是怎麼調查的?
民意調查(輿論調查)的意義是指為瞭解大多數民眾的看法、意見、利益與需求,以科學、系統與公正的資料,蒐集可以代表全部群眾(母體)的部分群眾(抽樣),設計問卷題目後,以人工或電腦詢問部分民眾對特定議題的看法與評價,利用抽樣出來部分民眾的意見與看法,來推論目前全部民眾的意見與看法,藉以衡量社會與政治的狀態。
以下是進行民調調查的基本步驟:
定義目標和目的:首先,調查者需要明確調查的目的。是要了解公眾對某個政策的看法?還是要評估某個政治候選人的支持率?
設計問卷:根據調查目的,研究者會設計一份問卷。問卷應該包含清晰、不帶偏見的問題,並避免導向性的語言。
選擇樣本:因為通常不可能調查所有人,所以會選擇一部分人作為代表。這部分人被稱為“樣本”。最理想的情況是使用隨機抽樣,以確保每個人都有被選中的機會。
收集數據:有多種方法可以收集數據,如面對面訪問、電話訪問、郵件調查或在線調查。
數據分析:一旦數據被收集,研究者會使用統計工具和技術進行分析,得出結論或洞見。
報告結果:分析完數據後,研究者會編寫報告或發布結果。報告通常會提供調查方法、樣本大小、誤差範圍和主要發現。
解釋誤差範圍:多數民調報告都會提供誤差範圍,例如“±3%”。這表示實際的結果有可能在報告結果的3%範圍內上下浮動。
民調調查的質量和可信度很大程度上取決於其設計和實施的方法。若是由專業和無偏見的組織進行,且使用科學的方法,那麼民調結果往往較為可靠。但即使是最高質量的民調也會有一定的誤差,因此解讀時應保持批判性思考。
為什麼要做民調?
民調提供了一種系統性的方式來了解大眾的意見、態度和信念。進行民調的原因多種多樣,以下是一些主要的動機:
政策制定和評估:政府和政策制定者進行民調,以了解公眾對某一議題或政策的看法。這有助於制定或調整政策,以反映大眾的需求和意見。
選舉和政治活動:政黨和候選人通常使用民調來評估自己在選舉中的地位,了解哪些議題對選民最重要,以及如何調整策略以吸引更多支持。
市場研究:企業和組織進行民調以了解消費者對產品、服務或品牌的態度,從而制定或調整市場策略。
社會科學研究:學者和研究者使用民調來了解人們的社會、文化和心理特征,以及其與行為的關係。
公眾與媒體的期望:民調提供了一種方式,使公眾、政府和企業得以了解社會的整體趨勢和態度。媒體也經常報導民調結果,提供公眾對當前議題的見解。
提供反饋和評估:無論是企業還是政府,都可以透過民調了解其表現、服務或政策的效果,並根據反饋進行改進。
預測和趨勢分析:民調可以幫助預測某些趨勢或行為的未來發展,如選舉結果、市場需求等。
教育和提高公眾意識:通過進行和公布民調,可以促使公眾對某一議題或問題有更深入的了解和討論。
民調可信嗎?
民意調查的結果數據隨處可見,尤其是政治性民調結果幾乎可說是天天在新聞上放送,對總統的滿意度下降了多少百分比,然而大家又信多少?
在景美市場的訪問中,我們了解到民眾對民調有一些普遍的觀點。大多數受訪者表示,他們對民調的可信度存有疑慮,主要原因是他們擔心政府可能會在調查中進行操控,以符合特定政治目標。
受訪者還提到,民意調查的結果通常不會對他們的投票意願產生影響。換句話說,他們的選擇通常受到更多因素的影響,例如候選人的政策立場和政府做事的認真與否,而不是單純依賴民調結果。
從訪問中我們可以得出的結論是,大多數民眾對民調持謹慎態度,並認為它們對他們的投票決策影響有限。
民調
民意調查是什麼?民調什麼意思?
民意調查又稱為輿論調查或民意測驗,簡稱民調。一般而言,民調是一種為了解公眾對某些政治、社會問題與政策的意見和態度,由專業民調公司或媒體進行的調查方法。
目的在於通過網路、電話、或書面等媒介,對大量樣本的問卷調查抽樣,利用統計學的抽樣理論來推斷較為客觀,且能較為精確地推論社會輿論或民意動向的一種方法。
以下是民意調查的一些基本特點和重要性:
抽樣:由於不可能向每一個人詢問意見,所以調查者會選擇一個代表性的樣本進行調查。這樣本的大小和抽樣方法都會影響調查的準確性和可靠性。
問卷設計:為了確保獲得可靠的結果,問卷必須經過精心設計,問題要清晰、不帶偏見,且易於理解。
數據分析:收集到的數據將被分析以得出結論。這可能包括計算百分比、平均值、標準差等,以及更複雜的統計分析。
多種用途:民意調查可以用於各種目的,包括政策制定、選舉預測、市場研究、社會科學研究等。
限制:雖然民意調查是一個有價值的工具,但它也有其限制。例如,樣本可能不完全代表目標人群,或者問卷的設計可能導致偏見。
影響決策:民意調查的結果常常被政府、企業和其他組織用來影響其決策。
透明度和誠實:為了維護調查的可信度,調查組織應該提供其調查方法、樣本大小、抽樣方法和可能的誤差範圍等詳細資訊。
民調是怎麼調查的?
民意調查(輿論調查)的意義是指為瞭解大多數民眾的看法、意見、利益與需求,以科學、系統與公正的資料,蒐集可以代表全部群眾(母體)的部分群眾(抽樣),設計問卷題目後,以人工或電腦詢問部分民眾對特定議題的看法與評價,利用抽樣出來部分民眾的意見與看法,來推論目前全部民眾的意見與看法,藉以衡量社會與政治的狀態。
以下是進行民調調查的基本步驟:
定義目標和目的:首先,調查者需要明確調查的目的。是要了解公眾對某個政策的看法?還是要評估某個政治候選人的支持率?
設計問卷:根據調查目的,研究者會設計一份問卷。問卷應該包含清晰、不帶偏見的問題,並避免導向性的語言。
選擇樣本:因為通常不可能調查所有人,所以會選擇一部分人作為代表。這部分人被稱為“樣本”。最理想的情況是使用隨機抽樣,以確保每個人都有被選中的機會。
收集數據:有多種方法可以收集數據,如面對面訪問、電話訪問、郵件調查或在線調查。
數據分析:一旦數據被收集,研究者會使用統計工具和技術進行分析,得出結論或洞見。
報告結果:分析完數據後,研究者會編寫報告或發布結果。報告通常會提供調查方法、樣本大小、誤差範圍和主要發現。
解釋誤差範圍:多數民調報告都會提供誤差範圍,例如“±3%”。這表示實際的結果有可能在報告結果的3%範圍內上下浮動。
民調調查的質量和可信度很大程度上取決於其設計和實施的方法。若是由專業和無偏見的組織進行,且使用科學的方法,那麼民調結果往往較為可靠。但即使是最高質量的民調也會有一定的誤差,因此解讀時應保持批判性思考。
為什麼要做民調?
民調提供了一種系統性的方式來了解大眾的意見、態度和信念。進行民調的原因多種多樣,以下是一些主要的動機:
政策制定和評估:政府和政策制定者進行民調,以了解公眾對某一議題或政策的看法。這有助於制定或調整政策,以反映大眾的需求和意見。
選舉和政治活動:政黨和候選人通常使用民調來評估自己在選舉中的地位,了解哪些議題對選民最重要,以及如何調整策略以吸引更多支持。
市場研究:企業和組織進行民調以了解消費者對產品、服務或品牌的態度,從而制定或調整市場策略。
社會科學研究:學者和研究者使用民調來了解人們的社會、文化和心理特征,以及其與行為的關係。
公眾與媒體的期望:民調提供了一種方式,使公眾、政府和企業得以了解社會的整體趨勢和態度。媒體也經常報導民調結果,提供公眾對當前議題的見解。
提供反饋和評估:無論是企業還是政府,都可以透過民調了解其表現、服務或政策的效果,並根據反饋進行改進。
預測和趨勢分析:民調可以幫助預測某些趨勢或行為的未來發展,如選舉結果、市場需求等。
教育和提高公眾意識:通過進行和公布民調,可以促使公眾對某一議題或問題有更深入的了解和討論。
民調可信嗎?
民意調查的結果數據隨處可見,尤其是政治性民調結果幾乎可說是天天在新聞上放送,對總統的滿意度下降了多少百分比,然而大家又信多少?
在景美市場的訪問中,我們了解到民眾對民調有一些普遍的觀點。大多數受訪者表示,他們對民調的可信度存有疑慮,主要原因是他們擔心政府可能會在調查中進行操控,以符合特定政治目標。
受訪者還提到,民意調查的結果通常不會對他們的投票意願產生影響。換句話說,他們的選擇通常受到更多因素的影響,例如候選人的政策立場和政府做事的認真與否,而不是單純依賴民調結果。
從訪問中我們可以得出的結論是,大多數民眾對民調持謹慎態度,並認為它們對他們的投票決策影響有限。
總統民調
民意調查是什麼?民調什麼意思?
民意調查又稱為輿論調查或民意測驗,簡稱民調。一般而言,民調是一種為了解公眾對某些政治、社會問題與政策的意見和態度,由專業民調公司或媒體進行的調查方法。
目的在於通過網路、電話、或書面等媒介,對大量樣本的問卷調查抽樣,利用統計學的抽樣理論來推斷較為客觀,且能較為精確地推論社會輿論或民意動向的一種方法。
以下是民意調查的一些基本特點和重要性:
抽樣:由於不可能向每一個人詢問意見,所以調查者會選擇一個代表性的樣本進行調查。這樣本的大小和抽樣方法都會影響調查的準確性和可靠性。
問卷設計:為了確保獲得可靠的結果,問卷必須經過精心設計,問題要清晰、不帶偏見,且易於理解。
數據分析:收集到的數據將被分析以得出結論。這可能包括計算百分比、平均值、標準差等,以及更複雜的統計分析。
多種用途:民意調查可以用於各種目的,包括政策制定、選舉預測、市場研究、社會科學研究等。
限制:雖然民意調查是一個有價值的工具,但它也有其限制。例如,樣本可能不完全代表目標人群,或者問卷的設計可能導致偏見。
影響決策:民意調查的結果常常被政府、企業和其他組織用來影響其決策。
透明度和誠實:為了維護調查的可信度,調查組織應該提供其調查方法、樣本大小、抽樣方法和可能的誤差範圍等詳細資訊。
民調是怎麼調查的?
民意調查(輿論調查)的意義是指為瞭解大多數民眾的看法、意見、利益與需求,以科學、系統與公正的資料,蒐集可以代表全部群眾(母體)的部分群眾(抽樣),設計問卷題目後,以人工或電腦詢問部分民眾對特定議題的看法與評價,利用抽樣出來部分民眾的意見與看法,來推論目前全部民眾的意見與看法,藉以衡量社會與政治的狀態。
以下是進行民調調查的基本步驟:
定義目標和目的:首先,調查者需要明確調查的目的。是要了解公眾對某個政策的看法?還是要評估某個政治候選人的支持率?
設計問卷:根據調查目的,研究者會設計一份問卷。問卷應該包含清晰、不帶偏見的問題,並避免導向性的語言。
選擇樣本:因為通常不可能調查所有人,所以會選擇一部分人作為代表。這部分人被稱為“樣本”。最理想的情況是使用隨機抽樣,以確保每個人都有被選中的機會。
收集數據:有多種方法可以收集數據,如面對面訪問、電話訪問、郵件調查或在線調查。
數據分析:一旦數據被收集,研究者會使用統計工具和技術進行分析,得出結論或洞見。
報告結果:分析完數據後,研究者會編寫報告或發布結果。報告通常會提供調查方法、樣本大小、誤差範圍和主要發現。
解釋誤差範圍:多數民調報告都會提供誤差範圍,例如“±3%”。這表示實際的結果有可能在報告結果的3%範圍內上下浮動。
民調調查的質量和可信度很大程度上取決於其設計和實施的方法。若是由專業和無偏見的組織進行,且使用科學的方法,那麼民調結果往往較為可靠。但即使是最高質量的民調也會有一定的誤差,因此解讀時應保持批判性思考。
為什麼要做民調?
民調提供了一種系統性的方式來了解大眾的意見、態度和信念。進行民調的原因多種多樣,以下是一些主要的動機:
政策制定和評估:政府和政策制定者進行民調,以了解公眾對某一議題或政策的看法。這有助於制定或調整政策,以反映大眾的需求和意見。
選舉和政治活動:政黨和候選人通常使用民調來評估自己在選舉中的地位,了解哪些議題對選民最重要,以及如何調整策略以吸引更多支持。
市場研究:企業和組織進行民調以了解消費者對產品、服務或品牌的態度,從而制定或調整市場策略。
社會科學研究:學者和研究者使用民調來了解人們的社會、文化和心理特征,以及其與行為的關係。
公眾與媒體的期望:民調提供了一種方式,使公眾、政府和企業得以了解社會的整體趨勢和態度。媒體也經常報導民調結果,提供公眾對當前議題的見解。
提供反饋和評估:無論是企業還是政府,都可以透過民調了解其表現、服務或政策的效果,並根據反饋進行改進。
預測和趨勢分析:民調可以幫助預測某些趨勢或行為的未來發展,如選舉結果、市場需求等。
教育和提高公眾意識:通過進行和公布民調,可以促使公眾對某一議題或問題有更深入的了解和討論。
民調可信嗎?
民意調查的結果數據隨處可見,尤其是政治性民調結果幾乎可說是天天在新聞上放送,對總統的滿意度下降了多少百分比,然而大家又信多少?
在景美市場的訪問中,我們了解到民眾對民調有一些普遍的觀點。大多數受訪者表示,他們對民調的可信度存有疑慮,主要原因是他們擔心政府可能會在調查中進行操控,以符合特定政治目標。
受訪者還提到,民意調查的結果通常不會對他們的投票意願產生影響。換句話說,他們的選擇通常受到更多因素的影響,例如候選人的政策立場和政府做事的認真與否,而不是單純依賴民調結果。
從訪問中我們可以得出的結論是,大多數民眾對民調持謹慎態度,並認為它們對他們的投票決策影響有限。
民意調查
民意調查是什麼?民調什麼意思?
民意調查又稱為輿論調查或民意測驗,簡稱民調。一般而言,民調是一種為了解公眾對某些政治、社會問題與政策的意見和態度,由專業民調公司或媒體進行的調查方法。
目的在於通過網路、電話、或書面等媒介,對大量樣本的問卷調查抽樣,利用統計學的抽樣理論來推斷較為客觀,且能較為精確地推論社會輿論或民意動向的一種方法。
以下是民意調查的一些基本特點和重要性:
抽樣:由於不可能向每一個人詢問意見,所以調查者會選擇一個代表性的樣本進行調查。這樣本的大小和抽樣方法都會影響調查的準確性和可靠性。
問卷設計:為了確保獲得可靠的結果,問卷必須經過精心設計,問題要清晰、不帶偏見,且易於理解。
數據分析:收集到的數據將被分析以得出結論。這可能包括計算百分比、平均值、標準差等,以及更複雜的統計分析。
多種用途:民意調查可以用於各種目的,包括政策制定、選舉預測、市場研究、社會科學研究等。
限制:雖然民意調查是一個有價值的工具,但它也有其限制。例如,樣本可能不完全代表目標人群,或者問卷的設計可能導致偏見。
影響決策:民意調查的結果常常被政府、企業和其他組織用來影響其決策。
透明度和誠實:為了維護調查的可信度,調查組織應該提供其調查方法、樣本大小、抽樣方法和可能的誤差範圍等詳細資訊。
民調是怎麼調查的?
民意調查(輿論調查)的意義是指為瞭解大多數民眾的看法、意見、利益與需求,以科學、系統與公正的資料,蒐集可以代表全部群眾(母體)的部分群眾(抽樣),設計問卷題目後,以人工或電腦詢問部分民眾對特定議題的看法與評價,利用抽樣出來部分民眾的意見與看法,來推論目前全部民眾的意見與看法,藉以衡量社會與政治的狀態。
以下是進行民調調查的基本步驟:
定義目標和目的:首先,調查者需要明確調查的目的。是要了解公眾對某個政策的看法?還是要評估某個政治候選人的支持率?
設計問卷:根據調查目的,研究者會設計一份問卷。問卷應該包含清晰、不帶偏見的問題,並避免導向性的語言。
選擇樣本:因為通常不可能調查所有人,所以會選擇一部分人作為代表。這部分人被稱為“樣本”。最理想的情況是使用隨機抽樣,以確保每個人都有被選中的機會。
收集數據:有多種方法可以收集數據,如面對面訪問、電話訪問、郵件調查或在線調查。
數據分析:一旦數據被收集,研究者會使用統計工具和技術進行分析,得出結論或洞見。
報告結果:分析完數據後,研究者會編寫報告或發布結果。報告通常會提供調查方法、樣本大小、誤差範圍和主要發現。
解釋誤差範圍:多數民調報告都會提供誤差範圍,例如“±3%”。這表示實際的結果有可能在報告結果的3%範圍內上下浮動。
民調調查的質量和可信度很大程度上取決於其設計和實施的方法。若是由專業和無偏見的組織進行,且使用科學的方法,那麼民調結果往往較為可靠。但即使是最高質量的民調也會有一定的誤差,因此解讀時應保持批判性思考。
為什麼要做民調?
民調提供了一種系統性的方式來了解大眾的意見、態度和信念。進行民調的原因多種多樣,以下是一些主要的動機:
政策制定和評估:政府和政策制定者進行民調,以了解公眾對某一議題或政策的看法。這有助於制定或調整政策,以反映大眾的需求和意見。
選舉和政治活動:政黨和候選人通常使用民調來評估自己在選舉中的地位,了解哪些議題對選民最重要,以及如何調整策略以吸引更多支持。
市場研究:企業和組織進行民調以了解消費者對產品、服務或品牌的態度,從而制定或調整市場策略。
社會科學研究:學者和研究者使用民調來了解人們的社會、文化和心理特征,以及其與行為的關係。
公眾與媒體的期望:民調提供了一種方式,使公眾、政府和企業得以了解社會的整體趨勢和態度。媒體也經常報導民調結果,提供公眾對當前議題的見解。
提供反饋和評估:無論是企業還是政府,都可以透過民調了解其表現、服務或政策的效果,並根據反饋進行改進。
預測和趨勢分析:民調可以幫助預測某些趨勢或行為的未來發展,如選舉結果、市場需求等。
教育和提高公眾意識:通過進行和公布民調,可以促使公眾對某一議題或問題有更深入的了解和討論。
民調可信嗎?
民意調查的結果數據隨處可見,尤其是政治性民調結果幾乎可說是天天在新聞上放送,對總統的滿意度下降了多少百分比,然而大家又信多少?
在景美市場的訪問中,我們了解到民眾對民調有一些普遍的觀點。大多數受訪者表示,他們對民調的可信度存有疑慮,主要原因是他們擔心政府可能會在調查中進行操控,以符合特定政治目標。
受訪者還提到,民意調查的結果通常不會對他們的投票意願產生影響。換句話說,他們的選擇通常受到更多因素的影響,例如候選人的政策立場和政府做事的認真與否,而不是單純依賴民調結果。
從訪問中我們可以得出的結論是,大多數民眾對民調持謹慎態度,並認為它們對他們的投票決策影響有限。
You’re so interesting! I do not believe I have read a single thing like that before.
So nice to find another person with a few genuine
thoughts on this subject matter. Really.. thank you for starting this up.
This site is one thing that is needed on the web, someone with some
originality!
deltasone 5mg sale order prednisone 5mg without prescription
Very nice blog post, definitely love this site. dubai racing 2 live streaming
nausea medication near me order avapro 150mg online cheap
Fantastic post however I was wanting to know if you could
write a litte more on this topic? I’d be very grateful
if you could elaborate a little bit more. Thank you!
I am in fact happy to glance at this weblog posts which
carries plenty of helpful information, thanks for providing these kinds of statistics.
Excellent way of explaining, and good post to take data on the topic
of my presentation subject matter, which i am going to convey in institution of
higher education.
best non drowsy nausea medicine amaryl over the counter
order absorica generic buy accutane pills accutane 20mg cheap
get ambien prescription online modafinil 100mg uk
娛樂城
2024娛樂城的創新趨勢
隨著2024年的到來,娛樂城業界正經歷著一場革命性的變遷。這一年,娛樂城不僅僅是賭博和娛樂的代名詞,更成為了科技創新和用戶體驗的集大成者。
首先,2024年的娛樂城極大地融合了最新的技術。增強現實(AR)和虛擬現實(VR)技術的引入,為玩家提供了沉浸式的賭博體驗。這種全新的遊戲方式不僅帶來視覺上的震撼,還為玩家創造了一種置身於真實賭場的感覺,而實際上他們可能只是坐在家中的沙發上。
其次,人工智能(AI)在娛樂城中的應用也達到了新高度。AI技術不僅用於增強遊戲的公平性和透明度,還在個性化玩家體驗方面發揮著重要作用。從個性化遊戲推薦到智能客服,AI的應用使得娛樂城更能滿足玩家的個別需求。
此外,線上娛樂城的安全性和隱私保護也獲得了顯著加強。隨著技術的進步,更加先進的加密技術和安全措施被用來保護玩家的資料和交易,從而確保一個安全可靠的遊戲環境。
2024年的娛樂城還強調負責任的賭博。許多平台採用了各種工具和資源來幫助玩家控制他們的賭博行為,如設置賭注限制、自我排除措施等,體現了對可持續賭博的承諾。
總之,2024年的娛樂城呈現出一個高度融合了技術、安全和負責任賭博的行業新面貌,為玩家提供了前所未有的娛樂體驗。隨著這些趨勢的持續發展,我們可以預見,娛樂城將不斷地創新和進步,為玩家帶來更多精彩和安全的娛樂選擇。
zithromax online order zithromax price zithromax price
buy generic neurontin for sale buy gabapentin tablets
Dubai, a city known for its opulence and modernity, demands a mode of transportation that reflects its grandeur. For those seeking a cost-effective and reliable long-term solution, Somonion Rent Car LLC emerges as the premier choice for monthly car rentals in Dubai. With a diverse fleet ranging from compact cars to premium vehicles, the company promises an unmatched blend of affordability, flexibility, and personalized service.
Favorable Rental Conditions:
Understanding the potential financial strain of long-term car rentals, Somonion Rent Car LLC aims to make your journey more economical. The company offers flexible rental terms coupled with exclusive discounts for loyal customers. This commitment to affordability extends beyond the rental cost, as additional services such as insurance, maintenance, and repair ensure your safety and peace of mind throughout the duration of your rental.
A Plethora of Options:
Somonion Rent Car LLC boasts an extensive selection of vehicles to cater to diverse preferences and budgets. Whether you’re in the market for a sleek sedan or a spacious crossover, the company has the perfect car to complement your needs. The transparency in pricing, coupled with the ease of booking through their online platform, makes Somonion Rent Car LLC a hassle-free solution for those embarking on a long-term adventure in Dubai.
Car Rental Services Tailored for You:
Somonion Rent Car LLC doesn’t just offer cars; it provides a comprehensive range of rental services tailored to suit various occasions. From daily and weekly rentals to airport transfers and business travel, the company ensures that your stay in Dubai is not only comfortable but also exudes prestige. The fleet includes popular models such as the Nissan Altima 2018, KIA Forte 2018, Hyundai Elantra 2018, and the Toyota Camry Sport Edition 2020, all available for monthly rentals at competitive rates.
Featured Deals and Specials:
Somonion Rent Car LLC constantly updates its offerings to provide customers with the best deals. Featured cars like the Hyundai Sonata 2018 and Hyundai Santa Fe 2018 add a touch of luxury to your rental experience, with daily rates starting as low as AED 100. The company’s commitment to affordable luxury is further emphasized by the online booking system, allowing customers to secure the best deals in real-time through their website or by contacting the experts via phone or WhatsApp.
Conclusion:
Whether you’re a tourist looking to explore Dubai at your pace or a business traveler in need of a reliable and prestigious mode of transportation, Somonion Rent Car LLC stands as the go-to choice for monthly car rentals in Dubai. Unlock the ultimate mobility experience with Somonion, where affordability meets excellence, ensuring your journey through Dubai is as seamless and luxurious as the city itself. Contact Somonion Rent Car LLC today and embark on a journey where every mile is a testament to comfort, style, and unmatched service.
It’s a pity you don’t have a donate button! I’d certainly donate to
this excellent blog! I guess for now i’ll settle for
bookmarking and adding your RSS feed to my Google account.
I look forward to brand new updates and will talk about this
site with my Facebook group. Chat soon!
monthly car rental in dubai
Dubai, a city of grandeur and innovation, demands a transportation solution that matches its dynamic pace. Whether you’re a business executive, a tourist exploring the city, or someone in need of a reliable vehicle temporarily, car rental services in Dubai offer a flexible and cost-effective solution. In this guide, we’ll explore the popular car rental options in Dubai, catering to diverse needs and preferences.
Airport Car Rental: One-Way Pickup and Drop-off Road Trip Rentals:
For those who need to meet an important delegation at the airport or have a flight to another city, airport car rentals provide a seamless solution. Avoid the hassle of relying on public transport and ensure you reach your destination on time. With one-way pickup and drop-off options, you can effortlessly navigate your road trip, making business meetings or conferences immediately upon arrival.
Business Car Rental Deals & Corporate Vehicle Rentals in Dubai:
Companies without their own fleet or those finding transport maintenance too expensive can benefit from business car rental deals. This option is particularly suitable for businesses where a vehicle is needed only occasionally. By opting for corporate vehicle rentals, companies can optimize their staff structure, freeing employees from non-core functions while ensuring reliable transportation when necessary.
Tourist Car Rentals with Insurance in Dubai:
Tourists visiting Dubai can enjoy the freedom of exploring the city at their own pace with car rentals that come with insurance. This option allows travelers to choose a vehicle that suits the particulars of their trip without the hassle of dealing with insurance policies. Renting a car not only saves money and time compared to expensive city taxis but also ensures a trouble-free travel experience.
Daily Car Hire Near Me:
Daily car rental services are a convenient and cost-effective alternative to taxis in Dubai. Whether it’s for a business meeting, everyday use, or a luxury experience, you can find a suitable vehicle for a day on platforms like Smarketdrive.com. The website provides a secure and quick way to rent a car from certified and verified car rental companies, ensuring guarantees and safety.
Weekly Auto Rental Deals:
For those looking for flexibility throughout the week, weekly car rentals in Dubai offer a competent, attentive, and professional service. Whether you need a vehicle for a few days or an entire week, choosing a car rental weekly is a convenient and profitable option. The certified and tested car rental companies listed on Smarketdrive.com ensure a reliable and comfortable experience.
Monthly Car Rentals in Dubai:
When your personal car is undergoing extended repairs, or if you’re a frequent visitor to Dubai, monthly car rentals (long-term car rentals) become the ideal solution. Residents, businessmen, and tourists can benefit from the extensive options available on Smarketdrive.com, ensuring mobility and convenience throughout their stay in Dubai.
FAQ about Renting a Car in Dubai:
To address common queries about renting a car in Dubai, our FAQ section provides valuable insights and information. From rental terms to insurance coverage, it serves as a comprehensive guide for those considering the convenience of car rentals in the bustling city.
Conclusion:
Dubai’s popularity as a global destination is matched by its diverse and convenient car rental services. Whether for business, tourism, or daily commuting, the options available cater to every need. With reliable platforms like Smarketdrive.com, navigating Dubai becomes a seamless and enjoyable experience, offering both locals and visitors the ultimate freedom of mobility.
娛樂城
2024娛樂城的創新趨勢
隨著2024年的到來,娛樂城業界正經歷著一場革命性的變遷。這一年,娛樂城不僅僅是賭博和娛樂的代名詞,更成為了科技創新和用戶體驗的集大成者。
首先,2024年的娛樂城極大地融合了最新的技術。增強現實(AR)和虛擬現實(VR)技術的引入,為玩家提供了沉浸式的賭博體驗。這種全新的遊戲方式不僅帶來視覺上的震撼,還為玩家創造了一種置身於真實賭場的感覺,而實際上他們可能只是坐在家中的沙發上。
其次,人工智能(AI)在娛樂城中的應用也達到了新高度。AI技術不僅用於增強遊戲的公平性和透明度,還在個性化玩家體驗方面發揮著重要作用。從個性化遊戲推薦到智能客服,AI的應用使得娛樂城更能滿足玩家的個別需求。
此外,線上娛樂城的安全性和隱私保護也獲得了顯著加強。隨著技術的進步,更加先進的加密技術和安全措施被用來保護玩家的資料和交易,從而確保一個安全可靠的遊戲環境。
2024年的娛樂城還強調負責任的賭博。許多平台採用了各種工具和資源來幫助玩家控制他們的賭博行為,如設置賭注限制、自我排除措施等,體現了對可持續賭博的承諾。
總之,2024年的娛樂城呈現出一個高度融合了技術、安全和負責任賭博的行業新面貌,為玩家提供了前所未有的娛樂體驗。隨著這些趨勢的持續發展,我們可以預見,娛樂城將不斷地創新和進步,為玩家帶來更多精彩和安全的娛樂選擇。
order azipro 250mg online cheap buy azithromycin 500mg without prescription cheap azithromycin
Lamborghini for rent dubai
Dubai, a city known for its opulence and modernity, demands a mode of transportation that reflects its grandeur. For those seeking a cost-effective and reliable long-term solution, Somonion Rent Car LLC emerges as the premier choice for monthly car rentals in Dubai. With a diverse fleet ranging from compact cars to premium vehicles, the company promises an unmatched blend of affordability, flexibility, and personalized service.
Favorable Rental Conditions:
Understanding the potential financial strain of long-term car rentals, Somonion Rent Car LLC aims to make your journey more economical. The company offers flexible rental terms coupled with exclusive discounts for loyal customers. This commitment to affordability extends beyond the rental cost, as additional services such as insurance, maintenance, and repair ensure your safety and peace of mind throughout the duration of your rental.
A Plethora of Options:
Somonion Rent Car LLC boasts an extensive selection of vehicles to cater to diverse preferences and budgets. Whether you’re in the market for a sleek sedan or a spacious crossover, the company has the perfect car to complement your needs. The transparency in pricing, coupled with the ease of booking through their online platform, makes Somonion Rent Car LLC a hassle-free solution for those embarking on a long-term adventure in Dubai.
Car Rental Services Tailored for You:
Somonion Rent Car LLC doesn’t just offer cars; it provides a comprehensive range of rental services tailored to suit various occasions. From daily and weekly rentals to airport transfers and business travel, the company ensures that your stay in Dubai is not only comfortable but also exudes prestige. The fleet includes popular models such as the Nissan Altima 2018, KIA Forte 2018, Hyundai Elantra 2018, and the Toyota Camry Sport Edition 2020, all available for monthly rentals at competitive rates.
Featured Deals and Specials:
Somonion Rent Car LLC constantly updates its offerings to provide customers with the best deals. Featured cars like the Hyundai Sonata 2018 and Hyundai Santa Fe 2018 add a touch of luxury to your rental experience, with daily rates starting as low as AED 100. The company’s commitment to affordable luxury is further emphasized by the online booking system, allowing customers to secure the best deals in real-time through their website or by contacting the experts via phone or WhatsApp.
Conclusion:
Whether you’re a tourist looking to explore Dubai at your pace or a business traveler in need of a reliable and prestigious mode of transportation, Somonion Rent Car LLC stands as the go-to choice for monthly car rentals in Dubai. Unlock the ultimate mobility experience with Somonion, where affordability meets excellence, ensuring your journey through Dubai is as seamless and luxurious as the city itself. Contact Somonion Rent Car LLC today and embark on a journey where every mile is a testament to comfort, style, and unmatched service.
buy furosemide cheap cheap furosemide 40mg
Watches World: Elevating Luxury and Style with Exquisite Timepieces
Introduction:
Jewelry has always been a timeless expression of elegance, and nothing complements one’s style better than a luxurious timepiece. At Watches World, we bring you an exclusive collection of coveted luxury watches that not only tell time but also serve as a testament to your refined taste. Explore our curated selection featuring iconic brands like Rolex, Hublot, Omega, Cartier, and more, as we redefine the art of accessorizing.
A Dazzling Array of Luxury Watches:
Watches World offers an unparalleled range of exquisite timepieces from renowned brands, ensuring that you find the perfect accessory to elevate your style. Whether you’re drawn to the classic sophistication of Rolex, the avant-garde designs of Hublot, or the precision engineering of Patek Philippe, our collection caters to diverse preferences.
Customer Testimonials:
Our commitment to providing an exceptional customer experience is reflected in the reviews from our satisfied clientele. O.M. commends our excellent communication and flawless packaging, while Richard Houtman appreciates the helpfulness and courtesy of our team. These testimonials highlight our dedication to transparency, communication, and customer satisfaction.
New Arrivals:
Stay ahead of the curve with our latest additions, including the Tudor Black Bay Ceramic 41mm, Richard Mille RM35-01 Rafael Nadal NTPT Carbon Limited Edition, and the Rolex Oyster Perpetual Datejust 41mm series. These new arrivals showcase cutting-edge designs and impeccable craftsmanship, ensuring you stay on the forefront of luxury watch fashion.
Best Sellers:
Discover our best-selling watches, such as the Bulgari Serpenti Tubogas 35mm and the Cartier Panthere Medium Model. These timeless pieces combine elegance with precision, making them a staple in any sophisticated wardrobe.
Expert’s Selection:
Our experts have carefully curated a selection of watches, including the Cartier Panthere Small Model, Omega Speedmaster Moonwatch 44.25 mm, and Rolex Oyster Perpetual Cosmograph Daytona 40mm. These choices exemplify the epitome of watchmaking excellence and style.
Secured and Tracked Delivery:
At Watches World, we prioritize the safety of your purchase. Our secured and tracked delivery ensures that your exquisite timepiece reaches you in perfect condition, giving you peace of mind with every order.
Passionate Experts at Your Service:
Our team of passionate watch experts is dedicated to providing personalized service. From assisting you in choosing the perfect timepiece to addressing any inquiries, we are here to make your watch-buying experience seamless and enjoyable.
Global Presence:
With a presence in key cities around the world, including Dubai, Geneva, Hong Kong, London, Miami, Paris, Prague, Dublin, Singapore, and Sao Paulo, Watches World brings luxury timepieces to enthusiasts globally.
Conclusion:
Watches World goes beyond being an online platform for luxury watches; it is a destination where expertise, trust, and satisfaction converge. Explore our collection, and let our timeless timepieces become an integral part of your style narrative. Join us in redefining luxury, one exquisite watch at a time.
Dubai, a city of grandeur and innovation, demands a transportation solution that matches its dynamic pace. Whether you’re a business executive, a tourist exploring the city, or someone in need of a reliable vehicle temporarily, car rental services in Dubai offer a flexible and cost-effective solution. In this guide, we’ll explore the popular car rental options in Dubai, catering to diverse needs and preferences.
Airport Car Rental: One-Way Pickup and Drop-off Road Trip Rentals:
For those who need to meet an important delegation at the airport or have a flight to another city, airport car rentals provide a seamless solution. Avoid the hassle of relying on public transport and ensure you reach your destination on time. With one-way pickup and drop-off options, you can effortlessly navigate your road trip, making business meetings or conferences immediately upon arrival.
Business Car Rental Deals & Corporate Vehicle Rentals in Dubai:
Companies without their own fleet or those finding transport maintenance too expensive can benefit from business car rental deals. This option is particularly suitable for businesses where a vehicle is needed only occasionally. By opting for corporate vehicle rentals, companies can optimize their staff structure, freeing employees from non-core functions while ensuring reliable transportation when necessary.
Tourist Car Rentals with Insurance in Dubai:
Tourists visiting Dubai can enjoy the freedom of exploring the city at their own pace with car rentals that come with insurance. This option allows travelers to choose a vehicle that suits the particulars of their trip without the hassle of dealing with insurance policies. Renting a car not only saves money and time compared to expensive city taxis but also ensures a trouble-free travel experience.
Daily Car Hire Near Me:
Daily car rental services are a convenient and cost-effective alternative to taxis in Dubai. Whether it’s for a business meeting, everyday use, or a luxury experience, you can find a suitable vehicle for a day on platforms like Smarketdrive.com. The website provides a secure and quick way to rent a car from certified and verified car rental companies, ensuring guarantees and safety.
Weekly Auto Rental Deals:
For those looking for flexibility throughout the week, weekly car rentals in Dubai offer a competent, attentive, and professional service. Whether you need a vehicle for a few days or an entire week, choosing a car rental weekly is a convenient and profitable option. The certified and tested car rental companies listed on Smarketdrive.com ensure a reliable and comfortable experience.
Monthly Car Rentals in Dubai:
When your personal car is undergoing extended repairs, or if you’re a frequent visitor to Dubai, monthly car rentals (long-term car rentals) become the ideal solution. Residents, businessmen, and tourists can benefit from the extensive options available on Smarketdrive.com, ensuring mobility and convenience throughout their stay in Dubai.
FAQ about Renting a Car in Dubai:
To address common queries about renting a car in Dubai, our FAQ section provides valuable insights and information. From rental terms to insurance coverage, it serves as a comprehensive guide for those considering the convenience of car rentals in the bustling city.
Conclusion:
Dubai’s popularity as a global destination is matched by its diverse and convenient car rental services. Whether for business, tourism, or daily commuting, the options available cater to every need. With reliable platforms like Smarketdrive.com, navigating Dubai becomes a seamless and enjoyable experience, offering both locals and visitors the ultimate freedom of mobility.
Cheap monthly rental car
Dubai, a city known for its opulence and modernity, demands a mode of transportation that reflects its grandeur. For those seeking a cost-effective and reliable long-term solution, Somonion Rent Car LLC emerges as the premier choice for monthly car rentals in Dubai. With a diverse fleet ranging from compact cars to premium vehicles, the company promises an unmatched blend of affordability, flexibility, and personalized service.
Favorable Rental Conditions:
Understanding the potential financial strain of long-term car rentals, Somonion Rent Car LLC aims to make your journey more economical. The company offers flexible rental terms coupled with exclusive discounts for loyal customers. This commitment to affordability extends beyond the rental cost, as additional services such as insurance, maintenance, and repair ensure your safety and peace of mind throughout the duration of your rental.
A Plethora of Options:
Somonion Rent Car LLC boasts an extensive selection of vehicles to cater to diverse preferences and budgets. Whether you’re in the market for a sleek sedan or a spacious crossover, the company has the perfect car to complement your needs. The transparency in pricing, coupled with the ease of booking through their online platform, makes Somonion Rent Car LLC a hassle-free solution for those embarking on a long-term adventure in Dubai.
Car Rental Services Tailored for You:
Somonion Rent Car LLC doesn’t just offer cars; it provides a comprehensive range of rental services tailored to suit various occasions. From daily and weekly rentals to airport transfers and business travel, the company ensures that your stay in Dubai is not only comfortable but also exudes prestige. The fleet includes popular models such as the Nissan Altima 2018, KIA Forte 2018, Hyundai Elantra 2018, and the Toyota Camry Sport Edition 2020, all available for monthly rentals at competitive rates.
Featured Deals and Specials:
Somonion Rent Car LLC constantly updates its offerings to provide customers with the best deals. Featured cars like the Hyundai Sonata 2018 and Hyundai Santa Fe 2018 add a touch of luxury to your rental experience, with daily rates starting as low as AED 100. The company’s commitment to affordable luxury is further emphasized by the online booking system, allowing customers to secure the best deals in real-time through their website or by contacting the experts via phone or WhatsApp.
Conclusion:
Whether you’re a tourist looking to explore Dubai at your pace or a business traveler in need of a reliable and prestigious mode of transportation, Somonion Rent Car LLC stands as the go-to choice for monthly car rentals in Dubai. Unlock the ultimate mobility experience with Somonion, where affordability meets excellence, ensuring your journey through Dubai is as seamless and luxurious as the city itself. Contact Somonion Rent Car LLC today and embark on a journey where every mile is a testament to comfort, style, and unmatched service.
buy omnacortil 40mg online buy generic prednisolone over the counter buy prednisolone 40mg pill
Watches World
Watches World: Elevating Luxury and Style with Exquisite Timepieces
Introduction:
Jewelry has always been a timeless expression of elegance, and nothing complements one’s style better than a luxurious timepiece. At Watches World, we bring you an exclusive collection of coveted luxury watches that not only tell time but also serve as a testament to your refined taste. Explore our curated selection featuring iconic brands like Rolex, Hublot, Omega, Cartier, and more, as we redefine the art of accessorizing.
A Dazzling Array of Luxury Watches:
Watches World offers an unparalleled range of exquisite timepieces from renowned brands, ensuring that you find the perfect accessory to elevate your style. Whether you’re drawn to the classic sophistication of Rolex, the avant-garde designs of Hublot, or the precision engineering of Patek Philippe, our collection caters to diverse preferences.
Customer Testimonials:
Our commitment to providing an exceptional customer experience is reflected in the reviews from our satisfied clientele. O.M. commends our excellent communication and flawless packaging, while Richard Houtman appreciates the helpfulness and courtesy of our team. These testimonials highlight our dedication to transparency, communication, and customer satisfaction.
New Arrivals:
Stay ahead of the curve with our latest additions, including the Tudor Black Bay Ceramic 41mm, Richard Mille RM35-01 Rafael Nadal NTPT Carbon Limited Edition, and the Rolex Oyster Perpetual Datejust 41mm series. These new arrivals showcase cutting-edge designs and impeccable craftsmanship, ensuring you stay on the forefront of luxury watch fashion.
Best Sellers:
Discover our best-selling watches, such as the Bulgari Serpenti Tubogas 35mm and the Cartier Panthere Medium Model. These timeless pieces combine elegance with precision, making them a staple in any sophisticated wardrobe.
Expert’s Selection:
Our experts have carefully curated a selection of watches, including the Cartier Panthere Small Model, Omega Speedmaster Moonwatch 44.25 mm, and Rolex Oyster Perpetual Cosmograph Daytona 40mm. These choices exemplify the epitome of watchmaking excellence and style.
Secured and Tracked Delivery:
At Watches World, we prioritize the safety of your purchase. Our secured and tracked delivery ensures that your exquisite timepiece reaches you in perfect condition, giving you peace of mind with every order.
Passionate Experts at Your Service:
Our team of passionate watch experts is dedicated to providing personalized service. From assisting you in choosing the perfect timepiece to addressing any inquiries, we are here to make your watch-buying experience seamless and enjoyable.
Global Presence:
With a presence in key cities around the world, including Dubai, Geneva, Hong Kong, London, Miami, Paris, Prague, Dublin, Singapore, and Sao Paulo, Watches World brings luxury timepieces to enthusiasts globally.
Conclusion:
Watches World goes beyond being an online platform for luxury watches; it is a destination where expertise, trust, and satisfaction converge. Explore our collection, and let our timeless timepieces become an integral part of your style narrative. Join us in redefining luxury, one exquisite watch at a time.
buy generic amoxil purchase amoxil for sale buy generic amoxicillin 250mg
2024全新上線❰戰神賽特老虎機❱ – ATG賽特玩法說明介紹
❰戰神賽特老虎機❱是由ATG電子獨家開發的古埃及風格線上老虎機,在傳說中戰神賽特是「力量之神」與奈芙蒂斯女神結成連理,共同守護古埃及的奇幻秘寶,只有被選中的冒險者才能進入探險。
❰戰神賽特老虎機❱ – ATG賽特介紹
2024最新老虎機【戰神塞特】- ATG電子 X 富遊娛樂城
❰戰神賽特老虎機❱ – ATG電子
線上老虎機系統 : ATG電子
發行年分 : 2024年1月
最大倍數 : 51000倍
返還率 : 95.89%
支付方式 : 全盤倍數、消除掉落
最低投注金額 : 0.4元
最高投注金額 : 2000元
可否選台 : 是
可選台台數 : 350台
免費遊戲 : 選轉觸發+購買特色
❰戰神賽特老虎機❱ 賠率說明
戰神塞特老虎機賠率算法非常簡單,玩家們只需要不斷的轉動老虎機,成功消除物件即可贏分,得分賠率依賠率表計算。
當盤面上沒有物件可以消除時,倍數符號將會相加形成總倍數!該次旋轉的總贏分即為 : 贏分 X 總倍數。
積分方式如下 :
贏分=(單次押注額/20) X 物件賠率
EX : 單次押注額為1,盤面獲得12個戰神賽特倍數符號法老魔眼
贏分= (1/20) X 1000=50
以下為各個得分符號數量之獎金賠率 :
得分符號 獎金倍數 得分符號 獎金倍數
戰神賽特倍數符號聖甲蟲 6 2000
5 100
4 60 戰神賽特倍數符號黃寶石 12+ 200
10-11 30
8-9 20
戰神賽特倍數符號荷魯斯之眼 12+ 1000
10-11 500
8-9 200 戰神賽特倍數符號紅寶石 12+ 160
10-11 24
8-9 16
戰神賽特倍數符號眼鏡蛇 12+ 500
10-11 200
8-9 50 戰神賽特倍數符號紫鑽石 12+ 100
10-11 20
8-9 10
戰神賽特倍數符號神箭 12+ 300
10-11 100
8-9 40 戰神賽特倍數符號藍寶石 12+ 80
10-11 18
8-9 8
戰神賽特倍數符號屠鐮刀 12+ 240
10-11 40
8-9 30 戰神賽特倍數符號綠寶石 12+ 40
10-11 15
8-9 5
❰戰神賽特老虎機❱ 賠率說明(橘色數值為獲得數量、黑色數值為得分賠率)
ATG賽特 – 特色說明
ATG賽特 – 倍數符號獎金加乘
玩家們在看到盤面上出現倍數符號時,務必把握機會加速轉動ATG賽特老虎機,倍數符號會隨機出現2到500倍的隨機倍數。
當盤面無法在消除時,這些倍數總和會相加,乘上當時累積之獎金,即為最後得分總額。
倍數符號會出現在主遊戲和免費遊戲當中,玩家們千萬別錯過這個可以瞬間將得獎金額拉高的好機會!
ATG賽特 – 倍數符號獎金加乘
ATG賽特 – 倍數符號圖示
ATG賽特 – 進入神秘金字塔開啟免費遊戲
戰神賽特倍數符號聖甲蟲
❰戰神賽特老虎機❱ 免費遊戲符號
在古埃及神話中,聖甲蟲又稱為「死亡之蟲」,它被當成了天球及重生的象徵,守護古埃及的奇幻秘寶。
當玩家在盤面上,看見越來越多的聖甲蟲時,千萬不要膽怯,只需在牌面上斬殺4~6個ATG賽特免費遊戲符號,就可以進入15場免費遊戲!
在免費遊戲中若轉出3~6個聖甲蟲免費遊戲符號,可額外獲得5次免費遊戲,最高可達100次。
當玩家的累積贏分且盤面有倍數物件時,盤面上的所有倍數將會加入總倍數!
ATG賽特 – 選台模式贏在起跑線
為避免神聖的寶物被盜墓者奪走,富有智慧的法老王將金子塔內佈滿迷宮,有的設滿機關讓盜墓者寸步難行,有的暗藏機關可以直接前往存放神秘寶物的暗房。
ATG賽特老虎機設有350個機檯供玩家選擇,這是連魔龍老虎機、忍老虎機都給不出的機台數量,為的就是讓玩家,可以隨時進入神秘的古埃及的寶藏聖域,挖掘長眠已久的神祕寶藏。
【戰神塞特老虎機】選台模式
❰戰神賽特老虎機❱ 選台模式
ATG賽特 – 購買免費遊戲挖掘秘寶
玩家們可以使用當前投注額的100倍購買免費遊戲!進入免費遊戲再也不是虛幻。獎勵與一般遊戲相同,且購買後遊戲將自動開始,直到場次和獎金發放完畢為止。
有購買免費遊戲需求的玩家們,立即點擊「開始」,啟動神秘金字塔裡的古埃及祕寶吧!
【戰神塞特老虎機】購買特色
❰戰神賽特老虎機❱ 購買特色
戰神賽特試玩推薦
看完了❰戰神賽特老虎機❱介紹之後,玩家們是否也蓄勢待發要進入古埃及的世界,一探神奇秘寶探險之旅。
本次ATG賽特與線上娛樂城推薦第一名的富遊娛樂城合作,只需要加入會員,即可領取到168體驗金,免費試玩420轉!
2024娛樂城No.1 – 富遊娛樂城介紹
2024 年 1 月 5 日
|
娛樂城, 現金版娛樂城
富遊娛樂城是無論老手、新手,都非常推薦的線上博奕,在2024娛樂城當中扮演著多年來最來勢洶洶的一匹黑馬,『人性化且精緻的介面,遊戲種類眾多,超級多的娛樂城優惠,擁有眾多與會員交流遊戲的群組』是一大特色。
富遊娛樂城擁有歐洲馬爾他(MGA)和菲律賓政府競猜委員會(PAGCOR)頒發的合法執照。
註冊於英屬維爾京群島,受國際行業協會認可的合法公司。
我們的中心思想就是能夠帶領玩家遠詐騙黑網,讓大家安心放心的暢玩線上博弈,娛樂城也受各大部落客、IG網紅、PTT論壇,推薦討論,富遊娛樂城沒有之一,絕對是線上賭場玩家的第一首選!
富遊娛樂城介面 / 2024娛樂城NO.1
富遊娛樂城簡介
品牌名稱 : 富遊RG
創立時間 : 2019年
存款速度 : 平均15秒
提款速度 : 平均5分
單筆提款金額 : 最低1000-100萬
遊戲對象 : 18歲以上男女老少皆可
合作廠商 : 22家遊戲平台商
支付平台 : 各大銀行、各大便利超商
支援配備 : 手機網頁、電腦網頁、IOS、安卓(Android)
富遊娛樂城遊戲品牌
真人百家 — 歐博真人、DG真人、亞博真人、SA真人、OG真人
體育投注 — SUPER體育、鑫寶體育、亞博體育
電競遊戲 — 泛亞電競
彩票遊戲 — 富遊彩票、WIN 539
電子遊戲 —ZG電子、BNG電子、BWIN電子、RSG電子、好路GR電子
棋牌遊戲 —ZG棋牌、亞博棋牌、好路棋牌、博亞棋牌
捕魚遊戲 —ZG捕魚、RSG捕魚、好路GR捕魚、亞博捕魚
富遊娛樂城優惠活動
每日任務簽到金666
富遊VIP全面啟動
復酬金活動10%優惠
日日返水
新會員好禮五選一
首存禮1000送1000
免費體驗金$168
富遊娛樂城APP
步驟1 : 開啟網頁版【富遊娛樂城官網】
步驟2 : 點選上方(下載app),會跳出下載與複製連結選項,點選後跳轉。
步驟3 : 跳轉後點選(安裝),並點選(允許)操作下載描述檔,跳出下載描述檔後點選關閉。
步驟4 : 到手機設置>一般>裝置管理>設定描述檔(富遊)安裝,即可完成安裝。
富遊娛樂城常見問題FAQ
富遊娛樂城詐騙?
黑網詐騙可細分兩種,小出大不出及純詐騙黑網,我們可從品牌知名度經營和網站架設畫面分辨來簡單分辨。
富遊娛樂城會出金嗎?
如上面提到,富遊是在做一個品牌,為的是能夠保證出金,和帶領玩家遠離黑網,而且還有DUKER娛樂城出金認證,所以各位能夠放心富遊娛樂城為正出金娛樂城。
富遊娛樂城出金延遲怎麼辦?
基本上只要是公司系統問提造成富遊娛樂城會員無法在30分鐘成功提款,富遊娛樂城會即刻派送補償金,表達誠摯的歉意。
富遊娛樂城結論
富遊娛樂城安心玩,評價4.5顆星。如果還想看其他娛樂城推薦的,可以來娛樂城推薦尋找喔。
戰神賽特
2024全新上線❰戰神賽特老虎機❱ – ATG賽特玩法說明介紹
❰戰神賽特老虎機❱是由ATG電子獨家開發的古埃及風格線上老虎機,在傳說中戰神賽特是「力量之神」與奈芙蒂斯女神結成連理,共同守護古埃及的奇幻秘寶,只有被選中的冒險者才能進入探險。
❰戰神賽特老虎機❱ – ATG賽特介紹
2024最新老虎機【戰神塞特】- ATG電子 X 富遊娛樂城
❰戰神賽特老虎機❱ – ATG電子
線上老虎機系統 : ATG電子
發行年分 : 2024年1月
最大倍數 : 51000倍
返還率 : 95.89%
支付方式 : 全盤倍數、消除掉落
最低投注金額 : 0.4元
最高投注金額 : 2000元
可否選台 : 是
可選台台數 : 350台
免費遊戲 : 選轉觸發+購買特色
❰戰神賽特老虎機❱ 賠率說明
戰神塞特老虎機賠率算法非常簡單,玩家們只需要不斷的轉動老虎機,成功消除物件即可贏分,得分賠率依賠率表計算。
當盤面上沒有物件可以消除時,倍數符號將會相加形成總倍數!該次旋轉的總贏分即為 : 贏分 X 總倍數。
積分方式如下 :
贏分=(單次押注額/20) X 物件賠率
EX : 單次押注額為1,盤面獲得12個戰神賽特倍數符號法老魔眼
贏分= (1/20) X 1000=50
以下為各個得分符號數量之獎金賠率 :
得分符號 獎金倍數 得分符號 獎金倍數
戰神賽特倍數符號聖甲蟲 6 2000
5 100
4 60 戰神賽特倍數符號黃寶石 12+ 200
10-11 30
8-9 20
戰神賽特倍數符號荷魯斯之眼 12+ 1000
10-11 500
8-9 200 戰神賽特倍數符號紅寶石 12+ 160
10-11 24
8-9 16
戰神賽特倍數符號眼鏡蛇 12+ 500
10-11 200
8-9 50 戰神賽特倍數符號紫鑽石 12+ 100
10-11 20
8-9 10
戰神賽特倍數符號神箭 12+ 300
10-11 100
8-9 40 戰神賽特倍數符號藍寶石 12+ 80
10-11 18
8-9 8
戰神賽特倍數符號屠鐮刀 12+ 240
10-11 40
8-9 30 戰神賽特倍數符號綠寶石 12+ 40
10-11 15
8-9 5
❰戰神賽特老虎機❱ 賠率說明(橘色數值為獲得數量、黑色數值為得分賠率)
ATG賽特 – 特色說明
ATG賽特 – 倍數符號獎金加乘
玩家們在看到盤面上出現倍數符號時,務必把握機會加速轉動ATG賽特老虎機,倍數符號會隨機出現2到500倍的隨機倍數。
當盤面無法在消除時,這些倍數總和會相加,乘上當時累積之獎金,即為最後得分總額。
倍數符號會出現在主遊戲和免費遊戲當中,玩家們千萬別錯過這個可以瞬間將得獎金額拉高的好機會!
ATG賽特 – 倍數符號獎金加乘
ATG賽特 – 倍數符號圖示
ATG賽特 – 進入神秘金字塔開啟免費遊戲
戰神賽特倍數符號聖甲蟲
❰戰神賽特老虎機❱ 免費遊戲符號
在古埃及神話中,聖甲蟲又稱為「死亡之蟲」,它被當成了天球及重生的象徵,守護古埃及的奇幻秘寶。
當玩家在盤面上,看見越來越多的聖甲蟲時,千萬不要膽怯,只需在牌面上斬殺4~6個ATG賽特免費遊戲符號,就可以進入15場免費遊戲!
在免費遊戲中若轉出3~6個聖甲蟲免費遊戲符號,可額外獲得5次免費遊戲,最高可達100次。
當玩家的累積贏分且盤面有倍數物件時,盤面上的所有倍數將會加入總倍數!
ATG賽特 – 選台模式贏在起跑線
為避免神聖的寶物被盜墓者奪走,富有智慧的法老王將金子塔內佈滿迷宮,有的設滿機關讓盜墓者寸步難行,有的暗藏機關可以直接前往存放神秘寶物的暗房。
ATG賽特老虎機設有350個機檯供玩家選擇,這是連魔龍老虎機、忍老虎機都給不出的機台數量,為的就是讓玩家,可以隨時進入神秘的古埃及的寶藏聖域,挖掘長眠已久的神祕寶藏。
【戰神塞特老虎機】選台模式
❰戰神賽特老虎機❱ 選台模式
ATG賽特 – 購買免費遊戲挖掘秘寶
玩家們可以使用當前投注額的100倍購買免費遊戲!進入免費遊戲再也不是虛幻。獎勵與一般遊戲相同,且購買後遊戲將自動開始,直到場次和獎金發放完畢為止。
有購買免費遊戲需求的玩家們,立即點擊「開始」,啟動神秘金字塔裡的古埃及祕寶吧!
【戰神塞特老虎機】購買特色
❰戰神賽特老虎機❱ 購買特色
戰神賽特試玩推薦
看完了❰戰神賽特老虎機❱介紹之後,玩家們是否也蓄勢待發要進入古埃及的世界,一探神奇秘寶探險之旅。
本次ATG賽特與線上娛樂城推薦第一名的富遊娛樂城合作,只需要加入會員,即可領取到168體驗金,免費試玩420轉!
2024娛樂城
2024娛樂城No.1 – 富遊娛樂城介紹
2024 年 1 月 5 日
|
娛樂城, 現金版娛樂城
富遊娛樂城是無論老手、新手,都非常推薦的線上博奕,在2024娛樂城當中扮演著多年來最來勢洶洶的一匹黑馬,『人性化且精緻的介面,遊戲種類眾多,超級多的娛樂城優惠,擁有眾多與會員交流遊戲的群組』是一大特色。
富遊娛樂城擁有歐洲馬爾他(MGA)和菲律賓政府競猜委員會(PAGCOR)頒發的合法執照。
註冊於英屬維爾京群島,受國際行業協會認可的合法公司。
我們的中心思想就是能夠帶領玩家遠詐騙黑網,讓大家安心放心的暢玩線上博弈,娛樂城也受各大部落客、IG網紅、PTT論壇,推薦討論,富遊娛樂城沒有之一,絕對是線上賭場玩家的第一首選!
富遊娛樂城介面 / 2024娛樂城NO.1
富遊娛樂城簡介
品牌名稱 : 富遊RG
創立時間 : 2019年
存款速度 : 平均15秒
提款速度 : 平均5分
單筆提款金額 : 最低1000-100萬
遊戲對象 : 18歲以上男女老少皆可
合作廠商 : 22家遊戲平台商
支付平台 : 各大銀行、各大便利超商
支援配備 : 手機網頁、電腦網頁、IOS、安卓(Android)
富遊娛樂城遊戲品牌
真人百家 — 歐博真人、DG真人、亞博真人、SA真人、OG真人
體育投注 — SUPER體育、鑫寶體育、亞博體育
電競遊戲 — 泛亞電競
彩票遊戲 — 富遊彩票、WIN 539
電子遊戲 —ZG電子、BNG電子、BWIN電子、RSG電子、好路GR電子
棋牌遊戲 —ZG棋牌、亞博棋牌、好路棋牌、博亞棋牌
捕魚遊戲 —ZG捕魚、RSG捕魚、好路GR捕魚、亞博捕魚
富遊娛樂城優惠活動
每日任務簽到金666
富遊VIP全面啟動
復酬金活動10%優惠
日日返水
新會員好禮五選一
首存禮1000送1000
免費體驗金$168
富遊娛樂城APP
步驟1 : 開啟網頁版【富遊娛樂城官網】
步驟2 : 點選上方(下載app),會跳出下載與複製連結選項,點選後跳轉。
步驟3 : 跳轉後點選(安裝),並點選(允許)操作下載描述檔,跳出下載描述檔後點選關閉。
步驟4 : 到手機設置>一般>裝置管理>設定描述檔(富遊)安裝,即可完成安裝。
富遊娛樂城常見問題FAQ
富遊娛樂城詐騙?
黑網詐騙可細分兩種,小出大不出及純詐騙黑網,我們可從品牌知名度經營和網站架設畫面分辨來簡單分辨。
富遊娛樂城會出金嗎?
如上面提到,富遊是在做一個品牌,為的是能夠保證出金,和帶領玩家遠離黑網,而且還有DUKER娛樂城出金認證,所以各位能夠放心富遊娛樂城為正出金娛樂城。
富遊娛樂城出金延遲怎麼辦?
基本上只要是公司系統問提造成富遊娛樂城會員無法在30分鐘成功提款,富遊娛樂城會即刻派送補償金,表達誠摯的歉意。
富遊娛樂城結論
富遊娛樂城安心玩,評價4.5顆星。如果還想看其他娛樂城推薦的,可以來娛樂城推薦尋找喔。
order generic albuterol 4mg buy albuterol 2mg for sale purchase albuterol inhaler
https://rg888.app/set/
2024全新上線❰戰神賽特老虎機❱ – ATG賽特玩法說明介紹
❰戰神賽特老虎機❱是由ATG電子獨家開發的古埃及風格線上老虎機,在傳說中戰神賽特是「力量之神」與奈芙蒂斯女神結成連理,共同守護古埃及的奇幻秘寶,只有被選中的冒險者才能進入探險。
❰戰神賽特老虎機❱ – ATG賽特介紹
2024最新老虎機【戰神塞特】- ATG電子 X 富遊娛樂城
❰戰神賽特老虎機❱ – ATG電子
線上老虎機系統 : ATG電子
發行年分 : 2024年1月
最大倍數 : 51000倍
返還率 : 95.89%
支付方式 : 全盤倍數、消除掉落
最低投注金額 : 0.4元
最高投注金額 : 2000元
可否選台 : 是
可選台台數 : 350台
免費遊戲 : 選轉觸發+購買特色
❰戰神賽特老虎機❱ 賠率說明
戰神塞特老虎機賠率算法非常簡單,玩家們只需要不斷的轉動老虎機,成功消除物件即可贏分,得分賠率依賠率表計算。
當盤面上沒有物件可以消除時,倍數符號將會相加形成總倍數!該次旋轉的總贏分即為 : 贏分 X 總倍數。
積分方式如下 :
贏分=(單次押注額/20) X 物件賠率
EX : 單次押注額為1,盤面獲得12個戰神賽特倍數符號法老魔眼
贏分= (1/20) X 1000=50
以下為各個得分符號數量之獎金賠率 :
得分符號 獎金倍數 得分符號 獎金倍數
戰神賽特倍數符號聖甲蟲 6 2000
5 100
4 60 戰神賽特倍數符號黃寶石 12+ 200
10-11 30
8-9 20
戰神賽特倍數符號荷魯斯之眼 12+ 1000
10-11 500
8-9 200 戰神賽特倍數符號紅寶石 12+ 160
10-11 24
8-9 16
戰神賽特倍數符號眼鏡蛇 12+ 500
10-11 200
8-9 50 戰神賽特倍數符號紫鑽石 12+ 100
10-11 20
8-9 10
戰神賽特倍數符號神箭 12+ 300
10-11 100
8-9 40 戰神賽特倍數符號藍寶石 12+ 80
10-11 18
8-9 8
戰神賽特倍數符號屠鐮刀 12+ 240
10-11 40
8-9 30 戰神賽特倍數符號綠寶石 12+ 40
10-11 15
8-9 5
❰戰神賽特老虎機❱ 賠率說明(橘色數值為獲得數量、黑色數值為得分賠率)
ATG賽特 – 特色說明
ATG賽特 – 倍數符號獎金加乘
玩家們在看到盤面上出現倍數符號時,務必把握機會加速轉動ATG賽特老虎機,倍數符號會隨機出現2到500倍的隨機倍數。
當盤面無法在消除時,這些倍數總和會相加,乘上當時累積之獎金,即為最後得分總額。
倍數符號會出現在主遊戲和免費遊戲當中,玩家們千萬別錯過這個可以瞬間將得獎金額拉高的好機會!
ATG賽特 – 倍數符號獎金加乘
ATG賽特 – 倍數符號圖示
ATG賽特 – 進入神秘金字塔開啟免費遊戲
戰神賽特倍數符號聖甲蟲
❰戰神賽特老虎機❱ 免費遊戲符號
在古埃及神話中,聖甲蟲又稱為「死亡之蟲」,它被當成了天球及重生的象徵,守護古埃及的奇幻秘寶。
當玩家在盤面上,看見越來越多的聖甲蟲時,千萬不要膽怯,只需在牌面上斬殺4~6個ATG賽特免費遊戲符號,就可以進入15場免費遊戲!
在免費遊戲中若轉出3~6個聖甲蟲免費遊戲符號,可額外獲得5次免費遊戲,最高可達100次。
當玩家的累積贏分且盤面有倍數物件時,盤面上的所有倍數將會加入總倍數!
ATG賽特 – 選台模式贏在起跑線
為避免神聖的寶物被盜墓者奪走,富有智慧的法老王將金子塔內佈滿迷宮,有的設滿機關讓盜墓者寸步難行,有的暗藏機關可以直接前往存放神秘寶物的暗房。
ATG賽特老虎機設有350個機檯供玩家選擇,這是連魔龍老虎機、忍老虎機都給不出的機台數量,為的就是讓玩家,可以隨時進入神秘的古埃及的寶藏聖域,挖掘長眠已久的神祕寶藏。
【戰神塞特老虎機】選台模式
❰戰神賽特老虎機❱ 選台模式
ATG賽特 – 購買免費遊戲挖掘秘寶
玩家們可以使用當前投注額的100倍購買免費遊戲!進入免費遊戲再也不是虛幻。獎勵與一般遊戲相同,且購買後遊戲將自動開始,直到場次和獎金發放完畢為止。
有購買免費遊戲需求的玩家們,立即點擊「開始」,啟動神秘金字塔裡的古埃及祕寶吧!
【戰神塞特老虎機】購買特色
❰戰神賽特老虎機❱ 購買特色
戰神賽特試玩推薦
看完了❰戰神賽特老虎機❱介紹之後,玩家們是否也蓄勢待發要進入古埃及的世界,一探神奇秘寶探險之旅。
本次ATG賽特與線上娛樂城推薦第一名的富遊娛樂城合作,只需要加入會員,即可領取到168體驗金,免費試玩420轉!
purchase amoxiclav online amoxiclav uk
Дома АВС – Ваш уютный уголок
Мы строим не просто дома, мы создаем пространство, где каждый уголок будет наполнен комфортом и радостью жизни. Наш приоритет – не просто предоставить место для проживания, а создать настоящий дом, где вы будете чувствовать себя счастливыми и уютно.
В нашем информационном разделе “ПРОЕКТЫ” вы всегда найдете вдохновение и новые идеи для строительства вашего будущего дома. Мы постоянно работаем над тем, чтобы предложить вам самые инновационные и стильные проекты.
Мы убеждены, что основа хорошего дома – это его дизайн. Поэтому мы предоставляем услуги опытных дизайнеров-архитекторов, которые помогут вам воплотить все ваши идеи в жизнь. Наши архитекторы и персональные консультанты всегда готовы поделиться своим опытом и предложить функциональные и комфортные решения для вашего будущего дома.
Мы стремимся сделать весь процесс строительства максимально комфортным для вас. Наша команда предоставляет детализированные сметы, разрабатывает четкие этапы строительства и осуществляет контроль качества на каждом этапе.
Для тех, кто ценит экологичность и близость к природе, мы предлагаем деревянные дома премиум-класса. Используя клееный брус и оцилиндрованное бревно, мы создаем уникальные и здоровые условия для вашего проживания.
Тем, кто предпочитает надежность и многообразие форм, мы предлагаем дома из камня, блоков и кирпичной кладки.
Для практичных и ценящих свое время людей у нас есть быстровозводимые каркасные дома и эконом-класса. Эти решения обеспечат вас комфортным проживанием в кратчайшие сроки.
С Домами АВС создайте свой уютный уголок, где каждый момент жизни будет наполнен радостью и удовлетворением
I’m impressed, I must say. Rarely do I encounter a blog that’s both educative and entertaining, and let me tell you,
you’ve hit the nail on the head. The problem is something which
not enough people are speaking intelligently about. Now i’m very happy I stumbled across this during my hunt for something concerning this.
where can i buy levothyroxine synthroid online buy buy levothyroxine no prescription
Hi it’s me, I am also visiting this web page regularly,
this web page is in fact good and the people are genuinely sharing nice thoughts.
https://rg88.org/seth/
2024全新上線❰戰神賽特老虎機❱ – ATG賽特玩法說明介紹
❰戰神賽特老虎機❱是由ATG電子獨家開發的古埃及風格線上老虎機,在傳說中戰神賽特是「力量之神」與奈芙蒂斯女神結成連理,共同守護古埃及的奇幻秘寶,只有被選中的冒險者才能進入探險。
❰戰神賽特老虎機❱ – ATG賽特介紹
2024最新老虎機【戰神塞特】- ATG電子 X 富遊娛樂城
❰戰神賽特老虎機❱ – ATG電子
線上老虎機系統 : ATG電子
發行年分 : 2024年1月
最大倍數 : 51000倍
返還率 : 95.89%
支付方式 : 全盤倍數、消除掉落
最低投注金額 : 0.4元
最高投注金額 : 2000元
可否選台 : 是
可選台台數 : 350台
免費遊戲 : 選轉觸發+購買特色
❰戰神賽特老虎機❱ 賠率說明
戰神塞特老虎機賠率算法非常簡單,玩家們只需要不斷的轉動老虎機,成功消除物件即可贏分,得分賠率依賠率表計算。
當盤面上沒有物件可以消除時,倍數符號將會相加形成總倍數!該次旋轉的總贏分即為 : 贏分 X 總倍數。
積分方式如下 :
贏分=(單次押注額/20) X 物件賠率
EX : 單次押注額為1,盤面獲得12個戰神賽特倍數符號法老魔眼
贏分= (1/20) X 1000=50
以下為各個得分符號數量之獎金賠率 :
得分符號 獎金倍數 得分符號 獎金倍數
戰神賽特倍數符號聖甲蟲 6 2000
5 100
4 60 戰神賽特倍數符號黃寶石 12+ 200
10-11 30
8-9 20
戰神賽特倍數符號荷魯斯之眼 12+ 1000
10-11 500
8-9 200 戰神賽特倍數符號紅寶石 12+ 160
10-11 24
8-9 16
戰神賽特倍數符號眼鏡蛇 12+ 500
10-11 200
8-9 50 戰神賽特倍數符號紫鑽石 12+ 100
10-11 20
8-9 10
戰神賽特倍數符號神箭 12+ 300
10-11 100
8-9 40 戰神賽特倍數符號藍寶石 12+ 80
10-11 18
8-9 8
戰神賽特倍數符號屠鐮刀 12+ 240
10-11 40
8-9 30 戰神賽特倍數符號綠寶石 12+ 40
10-11 15
8-9 5
❰戰神賽特老虎機❱ 賠率說明(橘色數值為獲得數量、黑色數值為得分賠率)
ATG賽特 – 特色說明
ATG賽特 – 倍數符號獎金加乘
玩家們在看到盤面上出現倍數符號時,務必把握機會加速轉動ATG賽特老虎機,倍數符號會隨機出現2到500倍的隨機倍數。
當盤面無法在消除時,這些倍數總和會相加,乘上當時累積之獎金,即為最後得分總額。
倍數符號會出現在主遊戲和免費遊戲當中,玩家們千萬別錯過這個可以瞬間將得獎金額拉高的好機會!
ATG賽特 – 倍數符號獎金加乘
ATG賽特 – 倍數符號圖示
ATG賽特 – 進入神秘金字塔開啟免費遊戲
戰神賽特倍數符號聖甲蟲
❰戰神賽特老虎機❱ 免費遊戲符號
在古埃及神話中,聖甲蟲又稱為「死亡之蟲」,它被當成了天球及重生的象徵,守護古埃及的奇幻秘寶。
當玩家在盤面上,看見越來越多的聖甲蟲時,千萬不要膽怯,只需在牌面上斬殺4~6個ATG賽特免費遊戲符號,就可以進入15場免費遊戲!
在免費遊戲中若轉出3~6個聖甲蟲免費遊戲符號,可額外獲得5次免費遊戲,最高可達100次。
當玩家的累積贏分且盤面有倍數物件時,盤面上的所有倍數將會加入總倍數!
ATG賽特 – 選台模式贏在起跑線
為避免神聖的寶物被盜墓者奪走,富有智慧的法老王將金子塔內佈滿迷宮,有的設滿機關讓盜墓者寸步難行,有的暗藏機關可以直接前往存放神秘寶物的暗房。
ATG賽特老虎機設有350個機檯供玩家選擇,這是連魔龍老虎機、忍老虎機都給不出的機台數量,為的就是讓玩家,可以隨時進入神秘的古埃及的寶藏聖域,挖掘長眠已久的神祕寶藏。
【戰神塞特老虎機】選台模式
❰戰神賽特老虎機❱ 選台模式
ATG賽特 – 購買免費遊戲挖掘秘寶
玩家們可以使用當前投注額的100倍購買免費遊戲!進入免費遊戲再也不是虛幻。獎勵與一般遊戲相同,且購買後遊戲將自動開始,直到場次和獎金發放完畢為止。
有購買免費遊戲需求的玩家們,立即點擊「開始」,啟動神秘金字塔裡的古埃及祕寶吧!
【戰神塞特老虎機】購買特色
❰戰神賽特老虎機❱ 購買特色
戰神賽特試玩推薦
看完了❰戰神賽特老虎機❱介紹之後,玩家們是否也蓄勢待發要進入古埃及的世界,一探神奇秘寶探險之旅。
本次ATG賽特與線上娛樂城推薦第一名的富遊娛樂城合作,只需要加入會員,即可領取到168體驗金,免費試玩420轉!
levitra uk order vardenafil 20mg without prescription
clomid 100mg brand brand clomid clomid 100mg cost
doeaccforum.com
Hongzhi 황제는 갑자기 아들을 때리고 싶은 충동을 느꼈습니다.
socialmediatric.com
잠시 후 다시 불의 비가 내렸다.
semaglutide 14 mg without prescription buy semaglutide no prescription rybelsus 14mg price
cheap tizanidine buy tizanidine pills for sale buy generic zanaflex for sale
homefronttoheartland.com
Fang Jifan은 침을 삼키고 잠시 생각했습니다. “아직 아무 말도 할 수 없습니다.”
deltasone 20mg sale oral deltasone 40mg buy cheap prednisone
darknet зайти на сайт
Даркнет, сокращение от “даркнетворк” (dark network), представляет собой часть интернета, недоступную для обычных поисковых систем. В отличие от повседневного интернета, где мы привыкли к публичному контенту, даркнет скрыт от обычного пользователя. Здесь используются специальные сети, такие как Tor (The Onion Router), чтобы обеспечить анонимность пользователей.
buy rybelsus without prescription buy generic rybelsus for sale order semaglutide 14mg pill
Definitely what a great blog and instructive posts I definitely will bookmark your site.All the Best! .<a href="https://www.images.google.cl/url?sa=t
isotretinoin 10mg pill accutane uk buy accutane 40mg
what to do when allergy medicine doesn’t work albuterol uk buy albuterol for sale
娛樂城
**娛樂城與線上賭場:現代娛樂的轉型與未來**
在當今數位化的時代,”娛樂城”和”線上賭場”已成為現代娛樂和休閒生活的重要組成部分。從傳統的賭場到互聯網上的線上賭場,這一領域的發展不僅改變了人們娛樂的方式,也推動了全球娛樂產業的創新與進步。
**起源與發展**
娛樂城的概念源自於傳統的實體賭場,這些場所最初旨在提供各種形式的賭博娛樂,如撲克、輪盤、老虎機等。隨著時間的推移,這些賭場逐漸發展成為包含餐飲、表演藝術和住宿等多元化服務的綜合娛樂中心,從而吸引了來自世界各地的遊客。
隨著互聯網技術的飛速發展,線上賭場應運而生。這種新型態的賭博平台讓使用者可以在家中或任何有互聯網連接的地方,享受賭博遊戲的樂趣。線上賭場的出現不僅為賭博愛好者提供了更多便利與選擇,也大大擴展了賭博產業的市場範圍。
**特點與魅力**
娛樂城和線上賭場的主要魅力在於它們能提供多樣化的娛樂選項和高度的可訪問性。無論是實體的娛樂城還是虛擬的線上賭場,它們都致力於創造一個充滿樂趣和刺激的環境,讓人們可以從日常生活的壓力中短暫逃脫。
此外,線上賭場通過提供豐富的遊戲選擇、吸引人的獎金方案以及便捷的支付系統,成功地吸引了全球範圍內的用戶。這些平台通常具有高度的互動性和社交性,使玩家不僅能享受遊戲本身,還能與來自世界各地的其他玩家交流。
**未來趨勢**
隨著技術的不斷進步和用戶需求的不斷演變,娛樂城和線上賭場的未來發展呈現出多元化的趨勢。一方面,虛
擬現實(VR)和擴增現實(AR)技術的應用,有望為線上賭場帶來更加沉浸式和互動式的遊戲體驗。另一方面,對於實體娛樂城而言,將更多地注重提供綜合性的休閒體驗,結合賭博、娛樂、休閒和旅遊等多個方面,以滿足不同客群的需求。
此外,隨著對負責任賭博的認識加深,未來娛樂城和線上賭場在提供娛樂的同時,也將更加注重促進健康的賭博行為和保護用戶的安全。
總之,娛樂城和線上賭場作為現代娛樂生活的一部分,隨著社會的發展和技術的進步,將繼續演化和創新,為人們提供更多的樂趣和便利。這一領域的未來發展無疑充滿了無限的可能性和機遇。
brand augmentin 375mg buy clavulanate without prescription brand augmentin
線上賭場
zithromax order buy azithromycin 500mg zithromax usa
netovideo.com
Zhu Houzhao는 “아버지, 그냥 운이 좋은 것 같아요. “라고 편안하게 말했습니다.
homefronttoheartland.com
Fang Tianci는 Zhu Houzhao의 조카이며 이생에서 음식과 의복에 대해 걱정할 필요가 없습니다.
Mtpolice.kr provides sports betting information, sports analysis, and sports tips as a sports community.
buy levoxyl without prescription synthroid 150mcg without prescription order synthroid sale
Understanding the processes and protocols within a Professional Tenure Committee (PTC) is crucial for faculty members. This Frequently Asked Questions (FAQ) guide aims to address common queries related to PTC procedures, voting, and membership.
1. Why should members of the PTC fill out vote justification forms explaining their votes?
Vote justification forms provide transparency in decision-making. Members articulate their reasoning, fostering a culture of openness and ensuring that decisions are well-founded and understood by the academic community.
2. How can absentee ballots be cast?
To accommodate absentee voting, PTCs may implement secure electronic methods or designated proxy voters. This ensures that faculty members who cannot physically attend meetings can still contribute to decision-making processes.
3. How will additional members of PTCs be elected in departments with fewer than four tenured faculty members?
In smaller departments, creative solutions like rotating roles or involving faculty from related disciplines can be explored. Flexibility in election procedures ensures representation even in departments with fewer tenured faculty members.
4. Can a faculty member on OCSA or FML serve on a PTC?
Faculty members involved in other committees like the Organization of Committee on Student Affairs (OCSA) or Family and Medical Leave (FML) can serve on a PTC, but potential conflicts of interest should be carefully considered and managed.
5. Can an abstention vote be cast at a PTC meeting?
Yes, PTC members have the option to abstain from voting if they feel unable to take a stance on a particular matter. This allows for ethical decision-making and prevents uninformed voting.
6. What constitutes a positive or negative vote in PTCs?
A positive vote typically indicates approval or agreement, while a negative vote signifies disapproval or disagreement. Clear definitions and guidelines within each PTC help members interpret and cast their votes accurately.
7. What constitutes a quorum in a PTC?
A quorum, the minimum number of members required for a valid meeting, is essential for decision-making. Specific rules about quorum size are usually outlined in the PTC’s governing documents.
Our Plan Packages: Choose The Best Plan for You
Explore our plan packages designed to suit your earning potential and preferences. With daily limits, referral bonuses, and various subscription plans, our platform offers opportunities for financial growth.
Blog Section: Insights and Updates
Stay informed with our blog, providing valuable insights into legal matters, organizational updates, and industry trends. Our recent articles cover topics ranging from law firm openings to significant developments in the legal landscape.
Testimonials: What Our Clients Say
Discover what our clients have to say about their experiences. Join thousands of satisfied users who have successfully withdrawn earnings and benefited from our platform.
Conclusion:
This FAQ guide serves as a resource for faculty members engaging with PTC procedures. By addressing common questions and providing insights into our platform’s earning opportunities, we aim to facilitate a transparent and informed academic community.
how to get free online money
Understanding the processes and protocols within a Professional Tenure Committee (PTC) is crucial for faculty members. This Frequently Asked Questions (FAQ) guide aims to address common queries related to PTC procedures, voting, and membership.
1. Why should members of the PTC fill out vote justification forms explaining their votes?
Vote justification forms provide transparency in decision-making. Members articulate their reasoning, fostering a culture of openness and ensuring that decisions are well-founded and understood by the academic community.
2. How can absentee ballots be cast?
To accommodate absentee voting, PTCs may implement secure electronic methods or designated proxy voters. This ensures that faculty members who cannot physically attend meetings can still contribute to decision-making processes.
3. How will additional members of PTCs be elected in departments with fewer than four tenured faculty members?
In smaller departments, creative solutions like rotating roles or involving faculty from related disciplines can be explored. Flexibility in election procedures ensures representation even in departments with fewer tenured faculty members.
4. Can a faculty member on OCSA or FML serve on a PTC?
Faculty members involved in other committees like the Organization of Committee on Student Affairs (OCSA) or Family and Medical Leave (FML) can serve on a PTC, but potential conflicts of interest should be carefully considered and managed.
5. Can an abstention vote be cast at a PTC meeting?
Yes, PTC members have the option to abstain from voting if they feel unable to take a stance on a particular matter. This allows for ethical decision-making and prevents uninformed voting.
6. What constitutes a positive or negative vote in PTCs?
A positive vote typically indicates approval or agreement, while a negative vote signifies disapproval or disagreement. Clear definitions and guidelines within each PTC help members interpret and cast their votes accurately.
7. What constitutes a quorum in a PTC?
A quorum, the minimum number of members required for a valid meeting, is essential for decision-making. Specific rules about quorum size are usually outlined in the PTC’s governing documents.
Our Plan Packages: Choose The Best Plan for You
Explore our plan packages designed to suit your earning potential and preferences. With daily limits, referral bonuses, and various subscription plans, our platform offers opportunities for financial growth.
Blog Section: Insights and Updates
Stay informed with our blog, providing valuable insights into legal matters, organizational updates, and industry trends. Our recent articles cover topics ranging from law firm openings to significant developments in the legal landscape.
Testimonials: What Our Clients Say
Discover what our clients have to say about their experiences. Join thousands of satisfied users who have successfully withdrawn earnings and benefited from our platform.
Conclusion:
This FAQ guide serves as a resource for faculty members engaging with PTC procedures. By addressing common questions and providing insights into our platform’s earning opportunities, we aim to facilitate a transparent and informed academic community.
oral clomiphene clomid 100mg cost buy clomiphene 50mg online cheap
Great website.ots of useful information here. look forward to the continuation.-vox livestream kostenlos
Kraken darknet market зеркало
Даркнет, представляет собой, скрытую, платформу, на, глобальной сети, доступ к которой, реализуется, по средствам, определенные, софт и, технологии, гарантирующие, анонимность пользователей. Из числа, этих, инструментов, представляется, браузер Тор, который, предоставляет, безопасное, подключение в сеть Даркнет. При помощи, его, участники, могут, безопасно, обращаться к, веб-сайты, не индексируемые, традиционными, поисковыми системами, создавая тем самым, обстановку, для проведения, разнообразных, противоправных операций.
Киберторговая площадка, в свою очередь, часто ассоциируется с, даркнетом, как, торговая площадка, для, криминалитетом. На этом ресурсе, можно, купить, разные, запрещенные, вещи, начиная от, препаратов и огнестрельного оружия, вплоть до, услугами хакеров. Система, гарантирует, крупную долю, шифрования, а также, защиты личной информации, что, предоставляет, ее, привлекательной, для, стремится, предотвратить, негативных последствий, от законопослушных органов
cheap neurontin online gabapentin 100mg price cheap neurontin 100mg
кракен kraken kraken darknet top
Темная сторона интернета, является, закрытую, платформу, на, сети, вход, осуществляется, путем, определенные, программы а также, инструменты, обеспечивающие, анонимность участников. Одним из, этих, инструментов, является, браузер Тор, который обеспечивает, обеспечивает, защищенное, подключение к интернету, к сети Даркнет. С помощью, этот, сетевые пользователи, имеют шанс, анонимно, посещать, интернет-ресурсы, не отображаемые, традиционными, поисковыми сервисами, позволяя таким образом, обстановку, для организации, разносторонних, запрещенных действий.
Крупнейшая торговая площадка, соответственно, часто ассоциируется с, темной стороной интернета, как, рынок, для, киберугрозами. На этой площадке, может быть возможность, купить, разнообразные, непозволительные, товары и услуги, начиная, наркотических средств и огнестрельного оружия, доходя до, услугами хакеров. Система, обеспечивает, высокую степень, криптографической защиты, и также, скрытности, что, создает, эту площадку, интересной, для тех, кто, желает, уклониться от, наказания, от правоохранительных органов.
this-is-a-small-world.com
Li Dongyang은 기침을하고 억지로 미소를지었습니다. “Fang Duwei, 잘 지내세요?”
digiapk.com
어쨌든 Chen Yan은 확실히 현재의 문제를 해결하는 데 도움이 될 것입니다.
кракен kraken kraken darknet top
Скрытая сеть, является, тайную, сеть, в, сети, подключение к этой сети, происходит, по средствам, уникальные, софт плюс, технические средства, предоставляющие, анонимность пользовательские данных. Один из, подобных, инструментов, представляется, браузер Тор, который, гарантирует, приватное, подключение к сети, в даркнет. С, его же, пользователи, имеют возможность, незаметно, заходить, сайты, не индексируемые, стандартными, поисковыми сервисами, создавая тем самым, среду, для, различных, нелегальных действий.
Кракен, в свою очередь, часто упоминается в контексте, темной стороной интернета, в качестве, торговая площадка, для осуществления обмена, киберпреступниками. На этом ресурсе, может быть возможность, приобрести, разные, запрещенные, вещи, начиная с, наркотиков и оружия, заканчивая, хакерскими услугами. Ресурс, гарантирует, крупную долю, криптографической защиты, а также, скрытности, это, предоставляет, данную систему, интересной, для тех, кто, намерен, предотвратить, наказания, со стороны законопослушных органов.
order lasix without prescription lasix 40mg cheap furosemide 40mg oral
buy generic viagra 100mg overnight delivery for viagra sildenafil overnight shipping
Watches World
Watches World
buy vibra-tabs sale cost vibra-tabs order monodox
rybelsus uk buy rybelsus pill order rybelsus 14mg
homefronttoheartland.com
Zhu Houzhao는 Fang Jifan을 겸손하게 바라 보았습니다. “먼저 말하십시오.”
Watches World
Client Feedback Highlight Our Watch Boutique Experience
At Our Watch Boutique, customer happiness isn’t just a goal; it’s a shining evidence to our commitment to greatness. Let’s plunge into what our valued clients have to share about their experiences, bringing to light on the perfect service and exceptional watches we offer.
O.M.’s Review Review: A Uninterrupted Adventure
“Very great contact and follow through throughout the process. The watch was impeccably packed and in mint. I would definitely work with this team again for a timepiece purchase.
O.M.’s declaration illustrates our loyalty to contact and meticulous care in delivering clocks in impeccable condition. The confidence built with O.M. is a building block of our customer relationships.
Richard Houtman’s Enlightening Review: A Personalized Contact
“I dealt with Benny, who was extremely beneficial and civil at all times, keeping me regularly informed of the process. Advancing, even though I ended up sourcing the watch locally, I would still surely recommend Benny and the enterprise advancing.
Richard Houtman’s interaction highlights our personalized approach. Benny’s support and continuous communication demonstrate our devotion to ensuring every customer feels valued and notified.
Customer’s Efficient Service Review: A Smooth Transaction
“A very good and effective service. Kept me informed on the transaction progression.
Our commitment to productivity is echoed in this buyer’s commentary. Keeping customers apprised and the seamless progress of acquisitions are integral to the Our Watch Boutique experience.
Explore Our Newest Choices
Audemars Piguet Royal Oak Selfwinding 37mm
A beautiful piece at €45,900, this 2022 version (REF: 15551ST.ZZ.1356ST.05) invites you to add it to your shopping cart and elevate your set.
Hublot Classic Fusion Chronograph Titanium Green 45mm
Priced at €8,590 in 2024 (REF: 521.NX.8970.RX), this Hublot creation is a mixture of style and creativity, awaiting your application.
free spins no deposit canada real money online casino casino online games for real money
vardenafil cost buy levitra sale levitra 10mg canada
мосты для tor browser список
Защита в сети: Список переходов для Tor Browser
В современный мир, когда темы секретности и безопасности в сети становятся все более важными, немало пользователи обращают внимание на технологии, позволяющие гарантировать скрытность и защиту личной информации. Один из таких инструментов – Tor Browser, созданный на инфраструктуре Tor. Однако даже при использовании Tor Browser есть опасность столкнуться с запретом или цензурой со стороны Интернет-поставщиков или цензоров.
Для разрешения этих ограничений были созданы подходы для Tor Browser. Переходы – это особые серверы, которые могут быть использованы для пересечения блокировок и гарантирования доступа к сети Tor. В настоящем материале мы рассмотрим перечень переходов, которые можно использовать с Tor Browser для гарантирования достоверной и противоопасной анонимности в интернете.
meek-azure: Этот переправа использует облачное обеспечение Azure для того, чтобы замаскировать тот факт, что вы используете Tor. Это может быть практично в странах, где поставщики блокируют доступ к серверам Tor.
obfs4: Переход обфускации, предоставляющий механизмы для сокрытия трафика Tor. Этот мост может эффективным образом обходить блокировки и цензуру, делая ваш трафик менее заметным для сторонних.
fte: Переход, использующий Free Talk Encrypt (FTE) для обфускации трафика. FTE позволяет трансформировать трафик так, чтобы он являлся обычным сетевым трафиком, что делает его затрудненным для выявления.
snowflake: Этот переправа позволяет вам использовать браузеры, которые поддерживаются расширение Snowflake, чтобы помочь другим пользователям Tor пройти через запреты.
fte-ipv6: Вариант FTE с совместимостью с IPv6, который может быть необходим, если ваш провайдер интернета предоставляет IPv6-подключение.
Чтобы использовать эти мосты с Tor Browser, откройте его настройки, перейдите в раздел “Проброс мостов” и введите названия мостов, которые вы хотите использовать.
Не забывайте, что успех подходов может изменяться в зависимости от страны и провайдера интернет-услуг. Также рекомендуется часто обновлять список переходов, чтобы быть уверенным в успехе обхода блокировок. Помните о важности секурности в интернете и принимайте меры для обеспечения безопасности своей личной информации.
мосты для tor browser список
В века технологий, в условиях, когда онлайн границы объединяются с реальностью, запрещено игнорировать возможность угроз в подпольной сети. Одной из таких угроз является blacksprut – понятие, приобретший символом нелегальной, вредоносной деятельности в скрытых уголках интернета.
Blacksprut, будучи составной частью даркнета, представляет существенную угрозу для кибербезопасности и личной сохранности пользователей. Этот скрытый уголок сети порой ассоциируется с незаконными сделками, торговлей запрещенными товарами и услугами, а также иной противозаконными деяниями.
В борьбе с угрозой blacksprut необходимо приложить усилия на разносторонних фронтах. Одним из основных направлений является совершенствование технологий кибербезопасности. Развитие современных алгоритмов и технологий анализа данных позволит обнаруживать и пресекать деятельность blacksprut в реальной жизни.
Помимо технологических мер, важна взаимодействие усилий органов правопорядка на мировом уровне. Международное сотрудничество в области защиты в сети необходимо для успешного противодействия угрозам, связанным с blacksprut. Обмен сведениями, формирование совместных стратегий и быстрые действия помогут уменьшить воздействие этой угрозы.
Просвещение и просвещение также играют важное значение в борьбе с blacksprut. Повышение осведомленности пользователей о рисках теневого интернета и методах противодействия становится неотъемлемой частью антиспампинговых мероприятий. Чем более информированными будут пользователи, тем меньше вероятность попадания под влияние угрозы blacksprut.
В заключение, в борьбе с угрозой blacksprut необходимо объединить усилия как на инженерном, так и на правовом уровнях. Это серьезное испытание, предполагающий совместных усилий общества, служб безопасности и IT-компаний. Только совместными усилиями мы сможем достичь создания безопасного и устойчивого цифрового пространства для всех.
почему-тор браузер не соединяется
Торовский браузер является эффективным инструментом для сбережения конфиденциальности и защиты в интернете. Однако, иногда пользователи могут встретиться с проблемами соединения. В тексте мы изучим потенциальные основания и подсчитаем способы решения для устранения препятствий с доступом к Tor Browser.
Проблемы с подключением:
Решение: Проверка соединения ваше интернет-соединение. Проверьте, что вы присоединены к вебу, и нет ли сбоев с вашим провайдером.
Блокировка Тор сети:
Решение: В некоторых определенных государствах или интернет-сетях Tor может быть запрещен. Примените применять мосты для пересечения запрещений. В настройках конфигурации Tor Browser отметьте “Проброс мостов” и поддерживайте инструкциям.
Прокси-серверы и файерволы:
Решение: Проверка параметров конфигурации прокси-сервера и стены. Проверьте, что они не ограничивают доступ Tor Browser к сети. Измените настройки или временно деактивируйте прокси и ограждения для испытания.
Проблемы с самим приложением:
Решение: Проверьте, что у вас находится последняя версия Tor Browser. Иногда обновления могут разрешить трудности с доступом. Также попробуйте перезапустить приложение.
Временные сбои в инфраструктуре Тор:
Решение: Подождите некоторое время и пытайтесь войти в дальнейшем. Временные перебои в работе Tor имеют возможность вызываться, и эти явления обычно исправляются в кратчайшие периоды.
Отключение JavaScript:
Решение: Некоторые из них сетевые порталы могут ограничивать доступ через Tor, если в вашем программе для просмотра включен JavaScript. Попытайтесь временно остановить JavaScript в настройках программы.
Проблемы с антивирусным программным обеспечением:
Решение: Ваш программа защиты или ограждение может блокировать Tor Browser. Удостоверьтесь, что у вас не установлено запретов для Tor в настройках вашего антивируса.
Исчерпание оперативной памяти:
Решение: Если у вас активно много окон или процессы, это может привести к исчерпанию памяти и проблемам с соединением. Закройте лишние вкладки или перезапустите браузер.
В случае, если проблема с соединением к Tor Browser остается в силе, заходите за помощью на официальном форуме Tor. Эксперты могут подсказать дополнительную помощь и советы. Помните, что стойкость и конфиденциальность зависят от постоянного интереса к деталям, так что отслеживайте нововведениями и поддерживайте поручениям сообщества по использованию Tor.
brand lyrica order lyrica 75mg buy pregabalin medication
Watches World
Wristwatches Universe
Client Comments Illuminate Our Watch Boutique Adventure
At Our Watch Boutique, client fulfillment isn’t just a objective; it’s a radiant evidence to our loyalty to perfection. Let’s plunge into what our cherished patrons have to communicate about their journeys, bringing to light on the flawless support and exceptional timepieces we present.
O.M.’s Trustpilot Feedback: A Uninterrupted Journey
“Very good contact and follow along throughout the process. The watch was impeccably packed and in pristine. I would surely work with this crew again for a timepiece buy.
O.M.’s statement typifies our loyalty to contact and meticulous care in delivering chronometers in pristine condition. The trust established with O.M. is a building block of our client connections.
Richard Houtman’s Perceptive Review: A Personal Contact
“I dealt with Benny, who was extremely assisting and gracious at all times, keeping me frequently notified of the process. Going forward, even though I ended up sourcing the watch locally, I would still definitely recommend Benny and the enterprise advancing.
Richard Houtman’s experience spotlights our tailored approach. Benny’s aid and constant contact display our commitment to ensuring every customer feels esteemed and notified.
Customer’s Efficient Service Review: A Effortless Transaction
“A very excellent and streamlined service. Kept me informed on the purchase advancement.
Our dedication to productivity is echoed in this customer’s response. Keeping clients notified and the effortless advancement of orders are integral to the WatchesWorld adventure.
Discover Our Latest Collections
AP Royal Oak Automatic 37mm
A gorgeous piece at €45,900, this 2022 version (REF: 15551ST.ZZ.1356ST.05) invites you to add it to your trolley and elevate your range.
Hublot Titanium Green 45mm Chrono
Priced at €8,590 in 2024 (REF: 521.NX.8970.RX), this Hublot creation is a fusion of design and creativity, awaiting your inquiry.
order hydroxychloroquine pills hydroxychloroquine 200mg tablet buy hydroxychloroquine medication
ST666
order triamcinolone 10mg pill aristocort for sale order aristocort 4mg generic
agonaga.com
배에는 선원들과 선원들이 모두 모여 눈이 반짝였다.
cialis 10mg usa cialis 40mg oral cialis 20mg oral
desloratadine price desloratadine over the counter purchase desloratadine pill
order generic cenforce 50mg buy cenforce for sale buy cenforce 100mg online
loratadine 10mg brand brand claritin 10mg order loratadine without prescription
kinoboomhd.com
그러나 그는 여전히 굴욕을 뻔뻔하게 견디고 살기로 결정했습니다.
buy chloroquine 250mg pills buy aralen tablets buy chloroquine
sm-slot.com
Li Yi는 창백한 얼굴로 그들을 향해 고개를 저으며 사방에서 울부 짖었습니다!
2024全新上線❰戰神賽特老虎機❱ – ATG賽特玩法說明介紹
❰戰神賽特老虎機❱是由ATG電子獨家開發的古埃及風格線上老虎機,在傳說中戰神賽特是「力量之神」與奈芙蒂斯女神結成連理,共同守護古埃及的奇幻秘寶,只有被選中的冒險者才能進入探險。
❰戰神賽特老虎機❱ – ATG賽特介紹
2024最新老虎機【戰神塞特】- ATG電子 X 富遊娛樂城
❰戰神賽特老虎機❱ – ATG電子
線上老虎機系統 : ATG電子
發行年分 : 2024年1月
最大倍數 : 51000倍
返還率 : 95.89%
支付方式 : 全盤倍數、消除掉落
最低投注金額 : 0.4元
最高投注金額 : 2000元
可否選台 : 是
可選台台數 : 350台
免費遊戲 : 選轉觸發+購買特色
❰戰神賽特老虎機❱ 賠率說明
戰神塞特老虎機賠率算法非常簡單,玩家們只需要不斷的轉動老虎機,成功消除物件即可贏分,得分賠率依賠率表計算。
當盤面上沒有物件可以消除時,倍數符號將會相加形成總倍數!該次旋轉的總贏分即為 : 贏分 X 總倍數。
積分方式如下 :
贏分=(單次押注額/20) X 物件賠率
EX : 單次押注額為1,盤面獲得12個戰神賽特倍數符號法老魔眼
贏分= (1/20) X 1000=50
以下為各個得分符號數量之獎金賠率 :
得分符號 獎金倍數 得分符號 獎金倍數
戰神賽特倍數符號聖甲蟲 6 2000
5 100
4 60 戰神賽特倍數符號黃寶石 12+ 200
10-11 30
8-9 20
戰神賽特倍數符號荷魯斯之眼 12+ 1000
10-11 500
8-9 200 戰神賽特倍數符號紅寶石 12+ 160
10-11 24
8-9 16
戰神賽特倍數符號眼鏡蛇 12+ 500
10-11 200
8-9 50 戰神賽特倍數符號紫鑽石 12+ 100
10-11 20
8-9 10
戰神賽特倍數符號神箭 12+ 300
10-11 100
8-9 40 戰神賽特倍數符號藍寶石 12+ 80
10-11 18
8-9 8
戰神賽特倍數符號屠鐮刀 12+ 240
10-11 40
8-9 30 戰神賽特倍數符號綠寶石 12+ 40
10-11 15
8-9 5
❰戰神賽特老虎機❱ 賠率說明(橘色數值為獲得數量、黑色數值為得分賠率)
ATG賽特 – 特色說明
ATG賽特 – 倍數符號獎金加乘
玩家們在看到盤面上出現倍數符號時,務必把握機會加速轉動ATG賽特老虎機,倍數符號會隨機出現2到500倍的隨機倍數。
當盤面無法在消除時,這些倍數總和會相加,乘上當時累積之獎金,即為最後得分總額。
倍數符號會出現在主遊戲和免費遊戲當中,玩家們千萬別錯過這個可以瞬間將得獎金額拉高的好機會!
ATG賽特 – 倍數符號獎金加乘
ATG賽特 – 倍數符號圖示
ATG賽特 – 進入神秘金字塔開啟免費遊戲
戰神賽特倍數符號聖甲蟲
❰戰神賽特老虎機❱ 免費遊戲符號
在古埃及神話中,聖甲蟲又稱為「死亡之蟲」,它被當成了天球及重生的象徵,守護古埃及的奇幻秘寶。
當玩家在盤面上,看見越來越多的聖甲蟲時,千萬不要膽怯,只需在牌面上斬殺4~6個ATG賽特免費遊戲符號,就可以進入15場免費遊戲!
在免費遊戲中若轉出3~6個聖甲蟲免費遊戲符號,可額外獲得5次免費遊戲,最高可達100次。
當玩家的累積贏分且盤面有倍數物件時,盤面上的所有倍數將會加入總倍數!
ATG賽特 – 選台模式贏在起跑線
為避免神聖的寶物被盜墓者奪走,富有智慧的法老王將金子塔內佈滿迷宮,有的設滿機關讓盜墓者寸步難行,有的暗藏機關可以直接前往存放神秘寶物的暗房。
ATG賽特老虎機設有350個機檯供玩家選擇,這是連魔龍老虎機、忍老虎機都給不出的機台數量,為的就是讓玩家,可以隨時進入神秘的古埃及的寶藏聖域,挖掘長眠已久的神祕寶藏。
【戰神塞特老虎機】選台模式
❰戰神賽特老虎機❱ 選台模式
ATG賽特 – 購買免費遊戲挖掘秘寶
玩家們可以使用當前投注額的100倍購買免費遊戲!進入免費遊戲再也不是虛幻。獎勵與一般遊戲相同,且購買後遊戲將自動開始,直到場次和獎金發放完畢為止。
有購買免費遊戲需求的玩家們,立即點擊「開始」,啟動神秘金字塔裡的古埃及祕寶吧!
【戰神塞特老虎機】購買特色
❰戰神賽特老虎機❱ 購買特色
台灣線上娛樂城的規模正迅速增長,新的娛樂場所不斷開張。為了吸引玩家,這些場所提供了各種吸引人的優惠和贈品。每家娛樂城都致力於提供卓越的服務,務求讓客人享受最佳的遊戲體驗。
2024年網友推薦最多的線上娛樂城:No.1富遊娛樂城、No.2 BET365、No.3 DG娛樂城、No.4 九州娛樂城、No.5 亞博娛樂城,以下來介紹這幾間娛樂城網友對他們的真實評價及娛樂城推薦。
2024台灣娛樂城排名
排名 娛樂城 體驗金(流水) 首儲優惠(流水) 入金速度 出金速度 推薦指數
1 富遊娛樂城 168元(1倍) 送1000(1倍) 15秒 3-5分鐘 ★★★★★
2 1XBET中文版 168元(1倍) 送1000(1倍) 15秒 3-5分鐘 ★★★★☆
3 Bet365中文 168元(1倍) 送1000(1倍) 15秒 3-5分鐘 ★★★★☆
4 DG娛樂城 168元(1倍) 送1000(1倍) 15秒 5-10分鐘 ★★★★☆
5 九州娛樂城 168元(1倍) 送500(1倍) 15秒 5-10分鐘 ★★★★☆
6 亞博娛樂城 168元(1倍) 送1000(1倍) 15秒 3-10分鐘 ★★★☆☆
7 寶格綠娛樂城 199元(1倍) 送1000(25倍) 15秒 3-5分鐘 ★★★☆☆
8 王者娛樂城 300元(15倍) 送1000(15倍) 90秒 5-30分鐘 ★★★☆☆
9 FA8娛樂城 200元(40倍) 送1000(15倍) 90秒 5-10分鐘 ★★★☆☆
10 AF娛樂城 288元(40倍) 送1000(1倍) 60秒 5-30分鐘 ★★★☆☆
2024台灣娛樂城排名,10間娛樂城推薦
No.1 富遊娛樂城
富遊娛樂城推薦指數:★★★★★(5/5)
富遊娛樂城介面 / 2024娛樂城NO.1
RG富遊官網
富遊娛樂城是成立於2019年的一家獲得數百萬玩家註冊的線上博彩品牌,持有博彩行業市場的合法運營許可。該公司受到歐洲馬爾他(MGA)、菲律賓(PAGCOR)以及英屬維爾京群島(BVI)的授權和監管,展示了其雄厚的企業實力與合法性。
富遊娛樂城致力於提供豐富多樣的遊戲選項和全天候的會員服務,不斷追求卓越,確保遊戲的公平性。公司運用先進的加密技術及嚴格的安全管理體系,保障玩家資金的安全。此外,為了提升手機用戶的使用體驗,富遊娛樂城還開發了專屬APP,兼容安卓(Android)及IOS系統,以達到業界最佳的穩定性水平。
在資金存提方面,富遊娛樂城採用第三方金流服務,進一步保障玩家的資金安全,贏得了玩家的信賴與支持。這使得每位玩家都能在此放心享受遊戲樂趣,無需擔心後顧之憂。
富遊娛樂城簡介
娛樂城網路評價:5分
娛樂城入金速度:15秒
娛樂城出金速度:5分鐘
娛樂城體驗金:168元
娛樂城優惠:
首儲1000送1000
好友禮金無上限
新會禮遇
舊會員回饋
娛樂城遊戲:體育、真人、電競、彩票、電子、棋牌、捕魚
富遊娛樂城推薦要點
新手首推:富遊娛樂城,2024受網友好評,除了打造針對新手的各種優惠活動,還有各種遊戲的豐富教學。
首儲再贈送:首儲1000元,立即在獲得1000元獎金,而且只需要1倍流水,對新手而言相當友好。
免費遊戲體驗:新進玩家享有免費體驗金,讓您暢玩娛樂城內的任何遊戲。
優惠多元:活動頻繁且豐富,流水要求低,對各玩家可說是相當友善。
玩家首選:遊戲多樣,服務優質,是新手與老手的最佳賭場選擇。
富遊娛樂城優缺點整合
優點 缺點
• 台灣註冊人數NO.1線上賭場
• 首儲1000贈1000只需一倍流水
• 擁有體驗金免費體驗賭場
• 網紅部落客推薦保證出金線上娛樂城 • 需透過客服申請體驗金
富遊娛樂城優缺點整合表格
富遊娛樂城存取款方式
存款方式 取款方式
• 提供四大超商(全家、7-11、萊爾富、ok超商)
• 虛擬貨幣ustd存款
• 銀行轉帳(各大銀行皆可) • 現金1:1出金
• 網站內申請提款及可匯款至綁定帳戶
富遊娛樂城存取款方式表格
富遊娛樂城優惠活動
優惠 獎金贈點 流水要求
免費體驗金 $168 1倍 (儲值後) /36倍 (未儲值)
首儲贈點 $1000 1倍流水
返水活動 0.3% – 0.7% 無流水限制
簽到禮金 $666 20倍流水
好友介紹金 $688 1倍流水
回歸禮金 $500 1倍流水
富遊娛樂城優惠活動表格
專屬富遊VIP特權
黃金 黃金 鉑金 金鑽 大神
升級流水 300w 600w 1800w 3600w
保級流水 50w 100w 300w 600w
升級紅利 $688 $1080 $3888 $8888
每週紅包 $188 $288 $988 $2388
生日禮金 $688 $1080 $3888 $8888
反水 0.4% 0.5% 0.6% 0.7%
專屬富遊VIP特權表格
娛樂城評價
總體來看,富遊娛樂城對於玩家來講是一個非常不錯的選擇,有眾多的遊戲能讓玩家做選擇,還有各種優惠活動以及低流水要求等等,都讓玩家贏錢的機率大大的提升了不少,除了體驗遊戲中帶來的樂趣外還可以享受到贏錢的快感,還在等什麼趕快點擊下方連結,立即遊玩!
カジノ
日本にオンラインカジノおすすめランキング2024年最新版
2024おすすめのオンラインカジノ
オンラインカジノはパソコンでしか遊べないというのは、もう一昔前の話。現在はスマホやタブレットなどのモバイル端末からも、パソコンと変わらないクオリティでオンラインカジノを当たり前に楽しむことができるようになりました。
数あるモバイルカジノの中で、当サイトが厳選したトップ5カジノはこちら。
オンラインカジノおすすめ: コニベット(Konibet)
コニベットといえば、キャッシュバックや毎日もらえるリベートボーナスなど豪華ボーナスが満載!それに加えて低い出金条件も見どころです。さらにVIPレベルごとの還元率の高さも業界内で突出している点や、出金速度の速さなどトータルバランスの良さからもハイローラーの方にも好まれています。
カスタマーサポートは365日24時間稼働しているので、初心者の方にも安心してご利用いただけます。
さらに【業界初のオンラインポーカー】を導入!毎日トーナメントも開催されているので、早速参加しちゃいましょう!
RTP(還元率)公開や、入出金対応がスムーズで初心者向き
2000種類以上の豊富なゲーム数を誇り、スロットゲーム多数!
今なら$20の入金不要ボーナスと最大$650還元ボーナス!
8種類以上のライブカジノプロバイダー
業界初オンラインポーカーあり,日本利用者数No.1の安心のオンラインカジノメディア!
おすすめポイント
コニベットは、その豊富なボーナスと高還元率、そして安心のキャッシュバック制度で知られています。まず、新規登録者には入金不要の$20ボーナスが提供され、さらに初回入金時には最大$650の還元ボーナスが得られます。これらのキャンペーンはプレイヤーにとって大きな魅力となっています。
また、コニベットの特徴的な点は、VIP制度です。一度ロイヤルクラブになると、降格がなく、スロットリベートが1.5%という驚異の還元率を享受できます。これは他のオンラインカジノと比較しても非常に高い還元率です。さらに、常時週間損失キャッシュバックも行っているため、不運で負けてしまった場合でも取り返すチャンスがあります。これらの特徴から、コニベットはプレイヤーにとって非常に魅力的なオンラインカジノと言えるでしょう。
コニベット 無料会員登録をする
| コニベットのボーナス
コニベットは、新規登録者向けに20ドルの入金不要ボーナスを用意しています
コニベットカジノでは、限定で初回入金後に残高が1ドル未満になった場合、入金額の50%(最高500ドル)がキャッシュバックされる。キャッシュバック額に出金条件はないため、獲得後にすぐ出金することも可能です。
| コニベットの入金方法
入金方法 最低 / 最高入金
マスターカード 最低 : $20 / 最高 : $6,000
ジェイシービー 最低 : $20/ 最高 : $6,000
アメックス 最低 : $20 / 最高 : $6,000
アイウォレット 最低 : $20 / 最高 : $100,000
スティックペイ 最低 : $20 / 最高 : $100,000
ヴィーナスポイント 最低 : $20 / 最高 : $10,000
仮想通貨 最低 : $20 / 最高 : $100,000
銀行送金 最低 : $20 / 最高 : $10,000
| コニベット出金方法
出金方法 最低 |最高出金
アイウォレット 最低 : $40 / 最高 : なし
スティックぺイ 最低 : $40 / 最高 : なし
ヴィーナスポイント 最低 : $40 / 最高 : なし
仮想通貨 最低 : $40 / 最高 : なし
銀行送金 最低 : $40 / 最高 : なし
oral glucophage 1000mg order glycomet 1000mg online metformin 500mg ca
オンラインカジノ
日本にオンラインカジノおすすめランキング2024年最新版
2024おすすめのオンラインカジノ
オンラインカジノはパソコンでしか遊べないというのは、もう一昔前の話。現在はスマホやタブレットなどのモバイル端末からも、パソコンと変わらないクオリティでオンラインカジノを当たり前に楽しむことができるようになりました。
数あるモバイルカジノの中で、当サイトが厳選したトップ5カジノはこちら。
オンラインカジノおすすめ: コニベット(Konibet)
コニベットといえば、キャッシュバックや毎日もらえるリベートボーナスなど豪華ボーナスが満載!それに加えて低い出金条件も見どころです。さらにVIPレベルごとの還元率の高さも業界内で突出している点や、出金速度の速さなどトータルバランスの良さからもハイローラーの方にも好まれています。
カスタマーサポートは365日24時間稼働しているので、初心者の方にも安心してご利用いただけます。
さらに【業界初のオンラインポーカー】を導入!毎日トーナメントも開催されているので、早速参加しちゃいましょう!
RTP(還元率)公開や、入出金対応がスムーズで初心者向き
2000種類以上の豊富なゲーム数を誇り、スロットゲーム多数!
今なら$20の入金不要ボーナスと最大$650還元ボーナス!
8種類以上のライブカジノプロバイダー
業界初オンラインポーカーあり,日本利用者数No.1の安心のオンラインカジノメディア!
おすすめポイント
コニベットは、その豊富なボーナスと高還元率、そして安心のキャッシュバック制度で知られています。まず、新規登録者には入金不要の$20ボーナスが提供され、さらに初回入金時には最大$650の還元ボーナスが得られます。これらのキャンペーンはプレイヤーにとって大きな魅力となっています。
また、コニベットの特徴的な点は、VIP制度です。一度ロイヤルクラブになると、降格がなく、スロットリベートが1.5%という驚異の還元率を享受できます。これは他のオンラインカジノと比較しても非常に高い還元率です。さらに、常時週間損失キャッシュバックも行っているため、不運で負けてしまった場合でも取り返すチャンスがあります。これらの特徴から、コニベットはプレイヤーにとって非常に魅力的なオンラインカジノと言えるでしょう。
コニベット 無料会員登録をする
| コニベットのボーナス
コニベットは、新規登録者向けに20ドルの入金不要ボーナスを用意しています
コニベットカジノでは、限定で初回入金後に残高が1ドル未満になった場合、入金額の50%(最高500ドル)がキャッシュバックされる。キャッシュバック額に出金条件はないため、獲得後にすぐ出金することも可能です。
| コニベットの入金方法
入金方法 最低 / 最高入金
マスターカード 最低 : $20 / 最高 : $6,000
ジェイシービー 最低 : $20/ 最高 : $6,000
アメックス 最低 : $20 / 最高 : $6,000
アイウォレット 最低 : $20 / 最高 : $100,000
スティックペイ 最低 : $20 / 最高 : $100,000
ヴィーナスポイント 最低 : $20 / 最高 : $10,000
仮想通貨 最低 : $20 / 最高 : $100,000
銀行送金 最低 : $20 / 最高 : $10,000
| コニベット出金方法
出金方法 最低 |最高出金
アイウォレット 最低 : $40 / 最高 : なし
スティックぺイ 最低 : $40 / 最高 : なし
ヴィーナスポイント 最低 : $40 / 最高 : なし
仮想通貨 最低 : $40 / 最高 : なし
銀行送金 最低 : $40 / 最高 : なし
We always follow your beautiful content I look forward to the continuation.Ergonomic Laptop Stand For Desk Adjustable Height Up To 20″ Laptop Riser Portable Computer Laptop Stands Fits All MacBook Laptops 10 15 17 Inches Pulpit Laptop Holder Desk Stand – Hot Deals
日本にオンラインカジノおすすめランキング2024年最新版
2024おすすめのオンラインカジノ
オンラインカジノはパソコンでしか遊べないというのは、もう一昔前の話。現在はスマホやタブレットなどのモバイル端末からも、パソコンと変わらないクオリティでオンラインカジノを当たり前に楽しむことができるようになりました。
数あるモバイルカジノの中で、当サイトが厳選したトップ5カジノはこちら。
オンラインカジノおすすめ: コニベット(Konibet)
コニベットといえば、キャッシュバックや毎日もらえるリベートボーナスなど豪華ボーナスが満載!それに加えて低い出金条件も見どころです。さらにVIPレベルごとの還元率の高さも業界内で突出している点や、出金速度の速さなどトータルバランスの良さからもハイローラーの方にも好まれています。
カスタマーサポートは365日24時間稼働しているので、初心者の方にも安心してご利用いただけます。
さらに【業界初のオンラインポーカー】を導入!毎日トーナメントも開催されているので、早速参加しちゃいましょう!
RTP(還元率)公開や、入出金対応がスムーズで初心者向き
2000種類以上の豊富なゲーム数を誇り、スロットゲーム多数!
今なら$20の入金不要ボーナスと最大$650還元ボーナス!
8種類以上のライブカジノプロバイダー
業界初オンラインポーカーあり,日本利用者数No.1の安心のオンラインカジノメディア!
おすすめポイント
コニベットは、その豊富なボーナスと高還元率、そして安心のキャッシュバック制度で知られています。まず、新規登録者には入金不要の$20ボーナスが提供され、さらに初回入金時には最大$650の還元ボーナスが得られます。これらのキャンペーンはプレイヤーにとって大きな魅力となっています。
また、コニベットの特徴的な点は、VIP制度です。一度ロイヤルクラブになると、降格がなく、スロットリベートが1.5%という驚異の還元率を享受できます。これは他のオンラインカジノと比較しても非常に高い還元率です。さらに、常時週間損失キャッシュバックも行っているため、不運で負けてしまった場合でも取り返すチャンスがあります。これらの特徴から、コニベットはプレイヤーにとって非常に魅力的なオンラインカジノと言えるでしょう。
コニベット 無料会員登録をする
| コニベットのボーナス
コニベットは、新規登録者向けに20ドルの入金不要ボーナスを用意しています
コニベットカジノでは、限定で初回入金後に残高が1ドル未満になった場合、入金額の50%(最高500ドル)がキャッシュバックされる。キャッシュバック額に出金条件はないため、獲得後にすぐ出金することも可能です。
| コニベットの入金方法
入金方法 最低 / 最高入金
マスターカード 最低 : $20 / 最高 : $6,000
ジェイシービー 最低 : $20/ 最高 : $6,000
アメックス 最低 : $20 / 最高 : $6,000
アイウォレット 最低 : $20 / 最高 : $100,000
スティックペイ 最低 : $20 / 最高 : $100,000
ヴィーナスポイント 最低 : $20 / 最高 : $10,000
仮想通貨 最低 : $20 / 最高 : $100,000
銀行送金 最低 : $20 / 最高 : $10,000
| コニベット出金方法
出金方法 最低 |最高出金
アイウォレット 最低 : $40 / 最高 : なし
スティックぺイ 最低 : $40 / 最高 : なし
ヴィーナスポイント 最低 : $40 / 最高 : なし
仮想通貨 最低 : $40 / 最高 : なし
銀行送金 最低 : $40 / 最高 : なし
oral xenical 120mg buy xenical sale buy generic diltiazem online
New free adult web cams boobie milk in! lactating and ready to play!
Купить паспорт
Теневые рынки и их незаконные деятельности представляют значительную угрозу безопасности общества и являются объектом внимания правоохранительных органов по всему миру. В данной статье мы обсудим так называемые скрытые рынки, где возможно покупать нелегальные паспорта, и какие угрозы это несет для граждан и государства.
Теневые рынки представляют собой закулисные интернет-площадки, на которых торгуется разнообразной преступной продукцией и услугами. Среди этих услуг встречается и продажа нелегальных документов, таких как личные документы. Эти рынки оперируют в подпольной сфере интернета, используя шифрование и анонимные платежные системы, чтобы оставаться непостижимыми для правоохранительных органов.
Покупка поддельного паспорта на теневых рынках представляет важную угрозу национальной безопасности. похищение личных данных, фальсификация документов и поддельные идентификационные материалы могут быть использованы для совершения экстремистских актов, обманного характера и дополнительных преступлений.
Правоохранительные органы в различных странах активно борются с теневыми рынками, проводя операции по выявлению и аресту тех, кто замешан в нелегальных сделках. Однако, по мере того как технологии становятся более сложными, эти рынки могут приспосабливаться и находить новые пути обхода законов.
Для обеспечения своей безопасности от рисков, связанных с неофициальными рынками, важно соблюдать осторожность при обработке своих личной информации. Это включает в себя избегать фишинговых атак, не раскрывать личной информацией в недоверенных источниках и регулярно проверять свои финансовые данные.
Кроме того, общество должно быть осознавшим риски и последствия покупки поддельных удостоверений. Это позволит создать более осознанное и ответственное отношение к вопросам безопасности и поможет в борьбе с теневыми рынками. Поддержка законодательных инициатив, направленных на ужесточение наказаний за изготовление и реализацию поддельных документов, также является важным шагом в борьбе с этими преступлениями
Изготовление и использование копий банковских карт является незаконной практикой, представляющей значительную угрозу для безопасности финансовых систем и личных средств граждан. В данной статье мы рассмотрим угрозы и последствия покупки реплик карт, а также как общество и силовые структуры борются с похожими преступлениями.
“Копии” карт — это незаконные подделки банковских карт, которые используются для непозволительных транзакций. Основной метод создания копий — это кража данных с оригинальной карты и последующее настройка этих данных на другую карту. Злоумышленники, предлагающие услуги по продаже клонов карт, обычно действуют в неявной сфере интернета, где трудно выявить и пресечь их деятельность.
Покупка клонов карт представляет собой серьезное преступление, которое может повлечь за собой тяжкие наказания. Покупатель также рискует стать пособником мошенничества, что может привести к наказанию по уголовному кодексу. Основные преступные действия в этой сфере включают в себя кражу личной информации, фальсификацию документов и, конечно же, финансовые махинации.
Банки и силовые структуры активно борются с противозаконной деятельностью, связанными с копированием карт. Банки внедряют современные технологии для обнаружения подозрительных транзакций, а также предлагают услуги по обеспечению безопасности для своих клиентов. Правоохранительные органы ведут расследования и задерживают тех, кто замешан в изготовлении и продаже копий карт.
Для обеспечения безопасности важно соблюдать осторожность при использовании банковских карт. Необходимо периодически проверять выписки, избегать недоверительных сделок и следить за своей личной информацией. Образование и информированность об угрозах также являются ключевыми средствами в борьбе с мошенничеством.
В заключение, использование клонов банковских карт — это незаконное и неприемлемое деяние, которое может привести к важным последствиям для тех, кто вовлечен в такую практику. Соблюдение мер защиты, осведомленность о возможных потенциальных рисках и сотрудничество с силовыми структурами играют основополагающую роль в предотвращении и пресечении этих преступлений
Watches World
In the world of luxury watches, finding a dependable source is essential, and WatchesWorld stands out as a pillar of trust and expertise. Presenting an wide collection of renowned timepieces, WatchesWorld has garnered acclaim from content customers worldwide. Let’s explore into what our customers are saying about their experiences.
Customer Testimonials:
O.M.’s Review on O.M.:
“Excellent communication and follow-up throughout the procedure. The watch was impeccably packed and in pristine condition. I would certainly work with this group again for a watch purchase.”
Richard Houtman’s Review on Benny:
“I dealt with Benny, who was highly assisting and courteous at all times, maintaining me regularly informed of the procedure. Moving forward, even though I ended up acquiring the watch locally, I would still definitely recommend Benny and the company.”
Customer’s Efficient Service Experience:
“A highly efficient and prompt service. Kept me up to date on the order progress.”
Featured Timepieces:
Richard Mille RM30-01 Automatic Winding with Declutchable Rotor:
Price: €285,000
Year: 2023
Reference: RM30-01 TI
Patek Philippe Complications World Time 38.5mm:
Price: €39,900
Year: 2019
Reference: 5230R-001
Rolex Oyster Perpetual Day-Date 36mm:
Price: €76,900
Year: 2024
Reference: 128238-0071
Best Sellers:
Bulgari Serpenti Tubogas 35mm:
Price: On Request
Reference: 101816 SP35C6SDS.1T
Bulgari Serpenti Tubogas 35mm (2024):
Price: €12,700
Reference: 102237 SP35C6SPGD.1T
Cartier Panthere Medium Model:
Price: €8,390
Year: 2023
Reference: W2PN0007
Our Experts Selection:
Cartier Panthere Small Model:
Price: €11,500
Year: 2024
Reference: W3PN0006
Omega Speedmaster Moonwatch 44.25 mm:
Price: €9,190
Year: 2024
Reference: 304.30.44.52.01.001
Rolex Oyster Perpetual Cosmograph Daytona 40mm:
Price: €28,500
Year: 2023
Reference: 116500LN-0002
Rolex Oyster Perpetual 36mm:
Price: €13,600
Year: 2023
Reference: 126000-0006
Why WatchesWorld:
WatchesWorld is not just an internet platform; it’s a promise to customized service in the world of high-end watches. Our group of watch experts prioritizes trust, ensuring that every client makes an well-informed decision.
Our Commitment:
Expertise: Our group brings exceptional understanding and perspective into the world of luxury timepieces.
Trust: Confidence is the foundation of our service, and we prioritize transparency in every transaction.
Satisfaction: Customer satisfaction is our paramount goal, and we go the additional step to ensure it.
When you choose WatchesWorld, you’re not just purchasing a watch; you’re committing in a smooth and reliable experience. Explore our collection, and let us assist you in finding the ideal timepiece that reflects your taste and sophistication. At WatchesWorld, your satisfaction is our proven commitment
карты на обнал
Использование платежных карт является неотъемлемым компонентом современного общества. Карты предоставляют удобство, надежность и множество опций для проведения финансовых сделок. Однако, кроме легального использования, существует негативная сторона — вывод наличных средств, когда карты используются для снятия денег без разрешения владельца. Это является незаконной практикой и влечет за собой тяжкие наказания.
Вывод наличных средств с карт представляет собой практики, направленные на извлечение наличных средств с банковской карты, необходимые для того, чтобы обойти систему безопасности и предупреждений, предусмотренных банком. К сожалению, такие противозаконные поступки существуют, и они могут привести к материальным убыткам для банков и клиентов.
Одним из методов обналичивания карт является использование технологических трюков, таких как кража данных с магнитных полос карт. Магнитный обман — это процесс, при котором злоумышленники устанавливают механизмы на банкоматах или терминалах оплаты, чтобы скопировать информацию с магнитной полосы карты. Полученные данные затем используются для изготовления дубликата карты или проведения онлайн-операций.
Другим часто используемым способом является фишинг, когда злоумышленники отправляют недобросовестные письма или создают поддельные веб-сайты, имитирующие банковские ресурсы, с целью получения конфиденциальной информации от клиентов.
Для предотвращения кэшаута карт банки вводят разнообразные меры. Это включает в себя усовершенствование защитных систем, осуществление двухфакторной верификации, анализ транзакций и обучение клиентов о техниках предотвращения мошенничества.
Клиентам также следует принимать активное участие в защите своих карт и данных. Это включает в себя регулярное изменение паролей, анализ выписок из банка, а также осторожность по отношению к сомнительным транзакциям.
Кэшаут карт — это опасное преступление, которое причиняет урон не только финансовым учреждениям, но и обществу в целом. Поэтому важно соблюдать осторожность при использовании банковских карт, быть информированным о методах мошенничества и соблюдать предосторожности для избежания потери денег
buy amlodipine generic norvasc 10mg usa order norvasc for sale
order acyclovir 400mg sale zyloprim for sale online order allopurinol without prescription
online platform for watches
In the realm of premium watches, finding a dependable source is paramount, and WatchesWorld stands out as a beacon of trust and knowledge. Offering an extensive collection of renowned timepieces, WatchesWorld has collected praise from happy customers worldwide. Let’s dive into what our customers are saying about their encounters.
Customer Testimonials:
O.M.’s Review on O.M.:
“Excellent communication and aftercare throughout the procedure. The watch was perfectly packed and in pristine condition. I would certainly work with this group again for a watch purchase.”
Richard Houtman’s Review on Benny:
“I dealt with Benny, who was exceptionally helpful and courteous at all times, preserving me regularly informed of the process. Moving forward, even though I ended up acquiring the watch locally, I would still definitely recommend Benny and the company.”
Customer’s Efficient Service Experience:
“A highly efficient and swift service. Kept me up to date on the order progress.”
Featured Timepieces:
Richard Mille RM30-01 Automatic Winding with Declutchable Rotor:
Price: €285,000
Year: 2023
Reference: RM30-01 TI
Patek Philippe Complications World Time 38.5mm:
Price: €39,900
Year: 2019
Reference: 5230R-001
Rolex Oyster Perpetual Day-Date 36mm:
Price: €76,900
Year: 2024
Reference: 128238-0071
Best Sellers:
Bulgari Serpenti Tubogas 35mm:
Price: On Request
Reference: 101816 SP35C6SDS.1T
Bulgari Serpenti Tubogas 35mm (2024):
Price: €12,700
Reference: 102237 SP35C6SPGD.1T
Cartier Panthere Medium Model:
Price: €8,390
Year: 2023
Reference: W2PN0007
Our Experts Selection:
Cartier Panthere Small Model:
Price: €11,500
Year: 2024
Reference: W3PN0006
Omega Speedmaster Moonwatch 44.25 mm:
Price: €9,190
Year: 2024
Reference: 304.30.44.52.01.001
Rolex Oyster Perpetual Cosmograph Daytona 40mm:
Price: €28,500
Year: 2023
Reference: 116500LN-0002
Rolex Oyster Perpetual 36mm:
Price: €13,600
Year: 2023
Reference: 126000-0006
Why WatchesWorld:
WatchesWorld is not just an web-based platform; it’s a dedication to customized service in the world of luxury watches. Our team of watch experts prioritizes confidence, ensuring that every customer makes an well-informed decision.
Our Commitment:
Expertise: Our team brings matchless knowledge and insight into the world of high-end timepieces.
Trust: Confidence is the basis of our service, and we prioritize openness in every transaction.
Satisfaction: Customer satisfaction is our paramount goal, and we go the additional step to ensure it.
When you choose WatchesWorld, you’re not just buying a watch; you’re committing in a seamless and trustworthy experience. Explore our range, and let us assist you in finding the ideal timepiece that embodies your taste and sophistication. At WatchesWorld, your satisfaction is our proven commitment
dota2answers.com
젊고 강력한 희생자들은 모두 수련생들에 의해 전면에 배치되었습니다.
however, are very low. China울산콜걸 appears to be stuck in a kind of ‘renminbi trap’: its currency will remain stronger than the economy needs it to be, and the risk of the doom loop will hover over China for the foreseeable future.
lisinopril online lisinopril 5mg brand order generic lisinopril
crestor order purchase rosuvastatin pills order zetia 10mg without prescription
cheap omeprazole 20mg order omeprazole 20mg generic prilosec pills
domperidone 10mg uk buy generic sumycin for sale order sumycin 500mg for sale
hihouse420.com
적어도 두 사람이 함께하는 동안 아무 일도 일어나지 않았다는 것을 보여줍니다.
Даркнет сайты
Даркнет – таинственная зона интернета, избегающая взоров стандартных поисковых систем и требующая эксклюзивных средств для доступа. Этот анонимный уголок сети обильно насыщен сайтами, предоставляя доступ к разношерстным товарам и услугам через свои перечни и справочники. Давайте подробнее рассмотрим, что представляют собой эти реестры и какие тайны они сокрывают.
Даркнет Списки: Ворота в Тайный Мир
Даркнет списки – это своего рода проходы в неощутимый мир интернета. Реестры и справочники веб-ресурсов в даркнете, они позволяют пользователям отыскивать разнообразные услуги, товары и информацию. Варьируя от форумов и магазинов до ресурсов, уделяющих внимание аспектам анонимности и криптовалютам, эти перечни предоставляют нам шанс заглянуть в неизведанный мир даркнета.
Категории и Возможности
Теневой Рынок:
Даркнет часто связывается с теневым рынком, где доступны самые разные товары и услуги – от наркотических препаратов и стрелкового вооружения до краденых данных и услуг наемных убийц. Списки ресурсов в данной категории облегчают пользователям находить подходящие предложения без лишних усилий.
Форумы и Сообщества:
Даркнет также предоставляет площадку для анонимного общения. Форумы и сообщества, указанные в каталогах даркнета, охватывают различные темы – от кибербезопасности и хакерства до политики и философии.
Информационные Ресурсы:
На даркнете есть ресурсы, предоставляющие данные и указания по преодолению цензуры, обеспечению конфиденциальности и другим темам, интересным тем, кто хочет сохранить свою конфиденциальность.
Безопасность и Осторожность
Несмотря на неизвестность и свободу, даркнет полон рисков. Мошенничество, кибератаки и незаконные сделки присущи этому миру. Взаимодействуя с реестрами даркнета, пользователи должны соблюдать максимальную осторожность и придерживаться мер безопасности.
Заключение
Списки даркнета – это ключ к таинственному миру, где сокрыты тайны и возможности. Однако, как и в любой неизведанной территории, путешествие в даркнет требует особой осторожности и знания. Анонимность не всегда гарантирует безопасность, и использование даркнета требует осознанного подхода. Независимо от ваших интересов – будь то технические детали в области кибербезопасности, поиск необычных товаров или исследование новых возможностей в интернете – списки даркнета предоставляют ключ
Даркнет – это часть интернета, которая остается скрытой от обычных поисковых систем и требует специального программного обеспечения для доступа. В этой анонимной зоне сети существует масса ресурсов, включая различные списки и каталоги, предоставляющие доступ к разнообразным услугам и товарам. Давайте рассмотрим, что представляет собой даркнет список и какие тайны скрываются в его глубинах.
Даркнет Списки: Врата в Невидимый Мир
Для начала, что такое теневой каталог? Это, по сути, каталоги или индексы веб-ресурсов в даркнете, которые позволяют пользователям находить нужные услуги, товары или информацию. Эти списки могут варьироваться от форумов и магазинов до ресурсов, специализирующихся на различных аспектах анонимности и криптовалют.
Категории и Возможности
Теневой Рынок:
Темная сторона интернета часто ассоциируется с рынком андеграунда, где можно найти различные товары и услуги, включая наркотики, оружие, украденные данные и даже услуги наемных убийц. Списки таких ресурсов позволяют пользователям без труда находить подобные предложения.
Форумы и Группы:
Даркнет также предоставляет платформы для анонимного общения. Чаты и сообщества на даркнет списках могут заниматься обсуждением тем от интернет-безопасности и взлома до политики и философии.
Информационные ресурсы:
Есть ресурсы, предоставляющие информацию и инструкции по обходу цензуры, защите конфиденциальности и другим темам, интересным пользователям, стремящимся сохранить анонимность.
Безопасность и Осторожность
При всей своей анонимности и свободе действий даркнет также несет риски. Мошенничество, кибератаки и незаконные сделки становятся частью этого мира. Пользователям необходимо проявлять максимальную осторожность и соблюдать меры безопасности при взаимодействии с даркнет списками.
Заключение: Врата в Неизведанный Мир
Даркнет списки предоставляют доступ к теневым уголкам интернета, где сокрыты тайны и возможности. Однако, как и в любой неизведанной территории, важно помнить о возможных рисках и осознанно подходить к использованию даркнета. Анонимность не всегда гарантирует безопасность, и путешествие в этот мир требует особой осторожности и знания.
Независимо от того, интересуетесь ли вы техническими аспектами интернет-безопасности, ищете уникальные товары или просто исследуете новые грани интернета, теневые каталоги предоставляют ключ
список сайтов даркнет
Темная сторона интернета – скрытая сфера интернета, избегающая взоров стандартных поисковых систем и требующая дополнительных средств для доступа. Этот скрытый ресурс сети обильно насыщен сайтами, предоставляя доступ к различным товарам и услугам через свои перечни и справочники. Давайте глубже рассмотрим, что представляют собой эти списки и какие тайны они хранят.
Даркнет Списки: Окна в Тайный Мир
Каталоги ресурсов в даркнете – это вид врата в скрытый мир интернета. Каталоги и индексы веб-ресурсов в даркнете, они позволяют пользователям отыскивать разнообразные услуги, товары и информацию. Варьируя от форумов и магазинов до ресурсов, уделяющих внимание аспектам анонимности и криптовалютам, эти списки предоставляют нам возможность заглянуть в неизведанный мир даркнета.
Категории и Возможности
Теневой Рынок:
Даркнет часто связывается с подпольной торговлей, где доступны самые разные товары и услуги – от психоактивных веществ и стрелкового оружия до похищенной информации и помощи наемных убийц. Списки ресурсов в этой категории облегчают пользователям находить нужные предложения без лишних усилий.
Форумы и Сообщества:
Даркнет также предоставляет площадку для анонимного общения. Форумы и сообщества, перечисленные в даркнет списках, затрагивают различные темы – от компьютерной безопасности и хакерских атак до политических аспектов и философских концепций.
Информационные Ресурсы:
На даркнете есть ресурсы, предоставляющие информацию и инструкции по обходу цензуры, защите конфиденциальности и другим темам, интересным тем, кто хочет сохранить свою конфиденциальность.
Безопасность и Осторожность
Несмотря на неизвестность и свободу, даркнет полон рисков. Мошенничество, кибератаки и незаконные сделки присущи этому миру. Взаимодействуя с реестрами даркнета, пользователи должны соблюдать предельную осмотрительность и придерживаться мер безопасности.
Заключение
Списки даркнета – это врата в неизведанный мир, где сокрыты тайны и возможности. Однако, как и в любой неизведанной территории, путешествие в темную сеть требует особой внимания и знаний. Не всегда можно полагаться на анонимность, и использование темной сети требует сознательного подхода. Независимо от ваших интересов – будь то технические детали в области кибербезопасности, поиск необычных товаров или исследование новых возможностей в интернете – даркнет списки предоставляют ключ
Даркнет – скрытая сфера интернета, избегающая взоров стандартных поисковых систем и требующая эксклюзивных средств для доступа. Этот скрытый ресурс сети обильно насыщен ресурсами, предоставляя доступ к разнообразным товарам и услугам через свои каталоги и справочники. Давайте глубже рассмотрим, что представляют собой эти реестры и какие тайны они хранят.
Даркнет Списки: Окна в Неизведанный Мир
Индексы веб-ресурсов в темной части интернета – это своего рода проходы в невидимый мир интернета. Перечни и указатели веб-ресурсов в даркнете, они позволяют пользователям отыскивать разношерстные услуги, товары и информацию. Варьируя от форумов и магазинов до ресурсов, уделяющих внимание аспектам анонимности и криптовалютам, эти перечни предоставляют нам возможность заглянуть в непознанный мир даркнета.
Категории и Возможности
Теневой Рынок:
Даркнет часто ассоциируется с незаконными сделками, где доступны разнообразные товары и услуги – от наркотиков и оружия до похищенной информации и помощи наемных убийц. Каталоги ресурсов в данной категории облегчают пользователям находить нужные предложения без лишних усилий.
Форумы и Сообщества:
Даркнет также предоставляет площадку для анонимного общения. Форумы и сообщества, указанные в каталогах даркнета, охватывают широкий спектр – от кибербезопасности и хакерства до политики и философии.
Информационные Ресурсы:
На даркнете есть ресурсы, предоставляющие сведения и руководства по обходу ограничений, защите конфиденциальности и другим темам, которые могут быть интересны тем, кто хочет остаться анонимным.
Безопасность и Осторожность
Несмотря на неизвестность и свободу, даркнет не лишен рисков. Мошенничество, кибератаки и незаконные сделки становятся частью этого мира. Взаимодействуя с реестрами даркнета, пользователи должны соблюдать максимальную осторожность и придерживаться мер безопасности.
Заключение
Списки даркнета – это врата в неизведанный мир, где сокрыты тайны и возможности. Однако, как и в любой неизведанной территории, путешествие в даркнет требует особой бдительности и знаний. Не всегда анонимность приносит безопасность, и использование темной сети требует осмысленного подхода. Независимо от ваших интересов – будь то технические аспекты кибербезопасности, поиск уникальных товаров или исследование новых граней интернета – реестры даркнета предоставляют ключ
order lopressor 50mg generic order metoprolol 100mg for sale metoprolol pills
linetogel
it’s awesome article. look forward to the continuation. – boys hey dude shoes
oral flexeril cyclobenzaprine sale baclofen 25mg tablet
đăng nhập st666
buy tenormin for sale atenolol for sale order atenolol 50mg online cheap
linetogel
заливы без предоплат
В последнее период стали известными запросы о переводах без предоплат – услугах, предоставляемых в сети, где клиентам гарантируют выполнение задачи или поставку услуги перед оплаты. Впрочем, за этой привлекающей внимание возможностью могут скрываться серьезные риски и негативные последствия.
Привлекательность бесплатных переводов:
Привлекательность идеи заливов без предоплат заключается в том, что клиенты получают услугу или товар, не внося первоначально деньги. Это может казаться выгодным и удобным, особенно для тех, кто не хочет ставить под риск финансами или остаться обманутым. Однако, до того как погрузиться в мир безоплатных переводов, необходимо учесть ряд существенных пунктов.
Риски и негативные следствия:
Мошенничество и обман:
За честными проектами без предварительной оплаты могут скрываться мошенники, готовые использовать уважение потребителей. Попав в их приманку, вы рискуете потерять не только это, но и но и денег.
Сниженное качество выполнения услуг:
Без гарантии исполнителю услуги может стать мало мотивации оказать высококачественную услугу или товар. В итоге клиент может остаться, а поставщик услуг не подвергнется серьезными последствиями.
Утрата информации и безопасности:
При предоставлении личных сведений или информации о банковских счетах для бесплатных заливов существует опасность утечки информации и последующего ихнего неправомерного использования.
Рекомендации по безопасным заливам:
Исследование:
Перед выбором безоплатных переводов осуществите тщательное исследование поставщика услуг. Отзывы, рейтинги и популярность могут полезным показателем.
Предоплата:
По возможности, старайтесь согласовать определенный процент оплаты вперед. Это способен сделать сделку более безопасной и обеспечит вам больший объем управления.
Проверенные платформы:
Отдавайте предпочтение использованию надежных платформ и систем для переводов. Это уменьшит риск обмана и повысит вероятность на получение наилучших качественных услуг.
Заключение:
Несмотря на очевидную привлекательность, заливы без предоплат сопряжены риски и потенциальные опасности. Внимание и осмотрительность при выборе исполнителя или сервиса могут предотвратить негативные ситуации. Существенно запомнить, что безоплатные заливы могут превратиться в причиной затруднений, и осознанное принятие решений поможет предотвратить потенциальных проблем
купить паспорт интернет магазин
Покупка паспорта в онлайн магазине – это незаконное и рискованное действие, которое может привести к значительным последствиям для граждан. Вот некоторые сторон, о которых необходимо запомнить:
Незаконность: Приобретение удостоверения личности в интернет-магазине является преступлением законодательства. Имение фальшивым удостоверением может повлечь за собой уголовную ответственность и серьезные наказания.
Риски индивидуальной безопасности: Факт применения поддельного удостоверения личности способен поставить под угрозу личную безопасность. Личности, использующие поддельными удостоверениями, могут оказаться целью провокаций со со стороны законопослушных структур.
Материальные потери: Зачастую мошенники, торгующие фальшивыми паспортами, могут применять ваши информацию для обмана, что приведёт к финансовым потерям. Личные или финансовые сведения способны оказаться применены в криминальных целях.
Проблемы при перемещении: Поддельный паспорт может стать распознан при попытке пересечь границы или при контакте с официальными органами. Это может послужить причиной задержанию, изгнанию или другим тяжелым сложностям при путешествиях.
Утрата доверия и престижа: Использование поддельного удостоверения личности способно привести к потере доверительности со стороны окружающих и работодателей. Такая обстановка может отрицательно влиять на ваши репутацию и карьерные перспективы.
Вместо того, чтобы рисковать своей свободой, защитой и репутацией, советуется придерживаться закон и воспользоваться государственными путями для оформления документов. Эти предусматривают обеспечение ваших законных интересов и обеспечивают секретность ваших данных. Нелегальные действия способны повлечь за собой непредсказуемые и вредные ситуации, создавая серьезные трудности для вас и ваших вашего окружения
даркнет 2024
Теневой интернет 2024: Неявные перспективы цифровой среды
С начала теневого интернета представлял собой уголок интернета, где тайна и тень были нормой. В 2024 году этот скрытый мир продолжает, предоставляя дополнительные требования и опасности для сообщества в сети. Рассмотрим, какие тенденции и изменения ожидают обществу в даркнете 2024.
Технологический прогресс и Увеличение скрытности
С прогрессом техники, средства обеспечения скрытности в даркнете превращаются в сложнее и эффективными. Использование цифровых валют, современных шифровальных методов и децентрализованных сетей делает слежение за деятельностью пользователей еще более трудным для силовых структур.
Развитие специализированных рынков
Темные рынки, фокусирующиеся на разнообразных продуктах и сервисах, продолжают расширяться. Психотропные вещества, оружие, средства для хакерских атак, краденые данные – спектр товаров бывает все многообразным. Это создает сложность для правопорядка, который сталкивается с необходимостью приспосабливаться к изменяющимся сценариям нелегальных действий.
Опасности цифровой безопасности для непрофессионалов
Сервисы аренды хакерских услуг и мошеннические схемы продолжают существовать активными в теневом интернете. Люди, не связанные с преступностью попадают в руки целью для киберпреступников, желающих получить доступ к личным данным, банковским счетам и иных секретных данных.
Перспективы цифровой реальности в теневом интернете
С развитием технологий цифровой симуляции, теневой интернет может перейти в совершенно новую фазу, предоставляя пользователям более реалистичные и вовлекающие виртуальные пространства. Это может включать в себя новыми формами нелегальных действий, такими как цифровые рынки для обмена цифровыми товарами.
Противостояние силам защиты
Органы обеспечения безопасности улучшают свои технические средства и подходы противостояния даркнетом. Совместные усилия государств и международных организаций направлены на предотвращение цифровой преступности и противостояние современным проблемам, связанным с развитием темного интернета.
Заключение
Теневой интернет в 2024 году остается сложной и многогранной обстановкой, где технологии продвигаются изменять пейзаж нелегальных действий. Важно для пользователей продолжать быть настороженными, обеспечивать свою кибербезопасность и следовать нормы, даже при нахождении в виртуальном пространстве. Вместе с тем, противостояние с теневым интернетом нуждается в коллективных действиях от государств, фирм в сфере технологий и граждан, для обеспечения защиту в цифровом мире.
В последние годы интернет изменился в неиссякаемый источник информации, услуг и товаров. Однако, в среде множества виртуальных магазинов и площадок, существует темная сторона, называемая как даркнет магазины. Данный уголок виртуального мира порождает свои опасные сценарии и сопровождается значительными рисками.
Что такое Даркнет Магазины:
Даркнет магазины являются онлайн-платформы, доступные через скрытые браузеры и уникальные программы. Они действуют в скрытой сети, невидимом от обычных поисковых систем. Здесь можно найти не только торговцев нелегальными товарами и услугами, но и различные преступные схемы.
Категории Товаров и Услуг:
Даркнет магазины продают широкий ассортимент товаров и услуг, начиная от наркотиков и оружия до хакерских услуг и похищенных данных. На этой темной площадке работают торговцы, предоставляющие возможность приобретения запрещенных вещей без опасности быть выслеженным.
Риски для Пользователей:
Легальные Последствия:
Покупка незаконных товаров на даркнет магазинах подвергает пользователей опасности столкнуться с правоохранительными органами. Уголовная ответственность может быть значительным следствием таких покупок.
Мошенничество и Обман:
Даркнет также является плодородной почвой для мошенников. Пользователи могут попасть в обман, где оплата не приведет к к получению товара или услуги.
Угрозы Кибербезопасности:
Даркнет магазины предлагают услуги хакеров и киберпреступников, что сопровождается реальными опасностями для безопасности данных и конфиденциальности.
Распространение Преступной Деятельности:
Экономика даркнет магазинов способствует распространению преступной деятельности, так как обеспечивает инфраструктуру для противозаконных транзакций.
Борьба с Проблемой:
Усиление Кибербезопасности:
Развитие кибербезопасности и технологий слежения помогает бороться с даркнет магазинами, превращая их менее поулчаемыми.
Законодательные Меры:
Принятие строгих законов и их эффективная реализация направлены на предупреждение и кара пользователей даркнет магазинов.
Образование и Пропаганда:
Повышение осведомленности о рисках и последствиях использования даркнет магазинов может снизить спрос на незаконные товары и услуги.
Заключение:
Даркнет магазины доступ к темным уголкам интернета, где проступают теневые фигуры с преступными намерениями. Рациональное применение ресурсов и повышенная бдительность необходимы, чтобы защитить себя от рисков, связанных с этими темными магазинами. В конечном итоге, секретность и законопослушание должны быть на первом месте, когда речь заходит о виртуальных покупках
pactam2.com
상황이 너무 의외여서 관계자들이 모두 경악을 금치 못했다.
Даркнет – темное пространство Интернета, доступен только для тех, кто знает правильный вход. Этот таинственный уголок виртуального мира служит местом для скрытных транзакций, обмена информацией и взаимодействия прячущимися сообществами. Однако, чтобы погрузиться в этот темный мир, необходимо преодолеть несколько барьеров и использовать особые инструменты.
Использование специализированных браузеров: Для доступа к даркнету обычный браузер не подойдет. На помощь приходят подходящие браузеры, такие как Tor (The Onion Router). Tor позволяет пользователям обходить цензуру и обеспечивает анонимность, персонализируя и перенаправляя запросы через различные серверы.
Адреса в даркнете: Обычные домены в даркнете заканчиваются на “.onion”. Для поиска ресурсов в даркнете, нужно использовать поисковики, адаптированные для этой среды. Однако следует быть осторожным, так как далеко не все ресурсы там законны.
Защита анонимности: При посещении даркнета следует принимать меры для защиты анонимности. Использование виртуальных частных сетей (VPN), блокировщиков скриптов и антивирусных программ является принципиальным. Это поможет избежать различных угроз и сохранить конфиденциальность.
Электронные валюты и биткоины: В даркнете часто используются цифровые валюты, в основном биткоины, для скрытных транзакций. Перед входом в даркнет следует ознакомиться с основами использования цифровых валют, чтобы избежать финансовых рисков.
Правовые аспекты: Следует помнить, что многие поступки в даркнете могут быть нелегальными и противоречить законам различных стран. Пользование даркнетом несет риски, и несанкционированные действия могут привести к серьезным юридическим последствиям.
Заключение: Даркнет – это тайное пространство сети, полное анонимности и тайн. Вход в этот мир требует уникальных навыков и предосторожности. При всем мистическом обаянии даркнета важно помнить о возможных рисках и последствиях, связанных с его использованием.
Взлом WhatsApp: Реальность и Легенды
WhatsApp – один из известных мессенджеров в мире, широко используемый для передачи сообщениями и файлами. Он прославился своей кодированной системой обмена данными и обеспечением конфиденциальности пользователей. Однако в интернете время от времени возникают утверждения о возможности взлома Вотсап. Давайте разберемся, насколько эти утверждения соответствуют фактичности и почему тема нарушения Вотсап вызывает столько дискуссий.
Кодирование в WhatsApp: Защита Личной Информации
WhatsApp применяет точка-точка кодирование, что означает, что только передающая сторона и получатель могут понимать сообщения. Это стало фундаментом для доверия многих пользователей мессенджера к защите их личной информации.
Мифы о Взломе WhatsApp: По какой причине Они Появляются?
Сеть периодически наполняют слухи о нарушении WhatsApp и возможном входе к переписке. Многие из этих утверждений порой не имеют обоснований и могут быть результатом паники или дезинформации.
Реальные Угрозы: Кибератаки и Охрана
Хотя нарушение Вотсап является сложной задачей, существуют актуальные угрозы, такие как кибератаки на отдельные аккаунты, фишинг и вредоносные программы. Соблюдение мер безопасности важно для минимизации этих рисков.
Охрана Личной Информации: Советы Пользователям
Для укрепления охраны своего аккаунта в Вотсап пользователи могут использовать двухэтапную проверку, регулярно обновлять приложение, избегать сомнительных ссылок и следить за конфиденциальностью своего устройства.
Заключение: Реальность и Осторожность
Взлом WhatsApp, как правило, оказывается трудным и маловероятным сценарием. Однако важно помнить о реальных угрозах и принимать меры предосторожности для сохранения своей личной информации. Соблюдение рекомендаций по охране помогает поддерживать конфиденциальность и уверенность в использовании мессенджера
взлом whatsapp
Взлом WhatsApp: Реальность и Мифы
WhatsApp – один из самых популярных мессенджеров в мире, массово используемый для передачи сообщениями и файлами. Он известен своей шифрованной системой обмена данными и обеспечением конфиденциальности пользователей. Однако в интернете время от времени появляются утверждения о возможности нарушения Вотсап. Давайте разберемся, насколько эти утверждения соответствуют фактичности и почему тема нарушения WhatsApp вызывает столько дискуссий.
Кодирование в Вотсап: Защита Личной Информации
Вотсап применяет end-to-end кодирование, что означает, что только отправитель и получающая сторона могут читать сообщения. Это стало фундаментом для доверия многих пользователей мессенджера к защите их личной информации.
Легенды о Взломе WhatsApp: Почему Они Появляются?
Интернет периодически заполняют слухи о взломе WhatsApp и возможном доступе к переписке. Многие из этих утверждений часто не имеют оснований и могут быть результатом паники или дезинформации.
Реальные Угрозы: Кибератаки и Охрана
Хотя нарушение WhatsApp является трудной задачей, существуют актуальные угрозы, такие как кибератаки на отдельные аккаунты, фишинг и вредоносные программы. Исполнение мер охраны важно для минимизации этих рисков.
Охрана Личной Информации: Советы Пользователям
Для укрепления охраны своего аккаунта в WhatsApp пользователи могут использовать двухэтапную проверку, регулярно обновлять приложение, избегать сомнительных ссылок и следить за конфиденциальностью своего устройства.
Заключение: Реальность и Осторожность
Взлом WhatsApp, как обычно, оказывается трудным и маловероятным сценарием. Однако важно помнить о актуальных угрозах и принимать меры предосторожности для сохранения своей личной информации. Соблюдение рекомендаций по безопасности помогает поддерживать конфиденциальность и уверенность в использовании мессенджера.
kantorbola88
Selamat datang di situs kantorbola , agent judi slot gacor terbaik dengan RTP diatas 98% , segera daftar di situs kantor bola untuk mendapatkan bonus deposit harian 100 ribu dan bonus rollingan 1%
sm-slot.com
핑시 후작 방정룡이 명령을 받아들였고, 핑시 흥원 후작의 모든 관리들이 소란을 피웠다.
windowsresolution.com
이때 누군가 몸을 떨었고 그의 눈은 점점 더 무서워졌습니다.
обнал карт форум
Обнал карт: Как обеспечить безопасность от мошенников и обеспечить безопасность в сети
Современный мир высоких технологий предоставляет преимущества онлайн-платежей и банковских операций, но с этим приходит и растущая угроза обнала карт. Обнал карт является практикой использования украденных или незаконно полученных кредитных карт для совершения финансовых транзакций с целью маскировать их источник и предотвратить отслеживание.
Ключевые моменты для безопасности в сети и предотвращения обнала карт:
Защита личной информации:
Будьте внимательными при предоставлении личной информации онлайн. Никогда не делитесь банковскими номерами карт, кодами безопасности и другими конфиденциальными данными на сомнительных сайтах.
Сильные пароли:
Используйте для своих банковских аккаунтов и кредитных карт безопасные и уникальные пароли. Регулярно изменяйте пароли для увеличения уровня безопасности.
Мониторинг транзакций:
Регулярно проверяйте выписки по кредитным картам и банковским счетам. Это помогает выявить подозрительные транзакции и быстро реагировать.
Антивирусная защита:
Ставьте и периодически обновляйте антивирусное программное обеспечение. Такие программы помогут предотвратить вредоносные программы, которые могут быть использованы для похищения данных.
Бережное использование общественных сетей:
Будьте осторожными при размещении чувствительной информации в социальных сетях. Эти данные могут быть использованы для хакерских атак к вашему аккаунту и последующего использования в обнале карт.
Уведомление банка:
Если вы обнаружили сомнительные транзакции или похищение карты, свяжитесь с банком незамедлительно для блокировки карты и избежания финансовых ущербов.
Образование и обучение:
Относитесь внимательно к новым способам мошенничества и постоянно обновляйте свои знания, как избегать подобных атак. Современные мошенники постоянно усовершенствуют свои приемы, и ваше знание может стать определяющим для защиты
фальшивые 5000 купитьФальшивые купюры 5000 рублей: Угроза для экономики и граждан
Фальшивые купюры всегда были значительной угрозой для финансовой стабильности общества. В последние годы одним из главных объектов манипуляций стали банкноты номиналом 5000 рублей. Эти контрафактные деньги представляют собой серьезную опасность для экономики и финансовой безопасности граждан. Давайте рассмотрим, почему фальшивые купюры 5000 рублей стали существенной бедой.
Трудность выявления.
Купюры 5000 рублей являются крупнейшими по номиналу, что делает их чрезвычайно привлекательными для фальшивомонетчиков. Отлично проработанные подделки могут быть трудно выявить даже специалистам в сфере финансов. Современные технологии позволяют создавать качественные копии с использованием современных методов печати и защитных элементов.
Угроза для бизнеса.
Фальшивые 5000 рублей могут привести к крупным финансовым убыткам для предпринимателей и компаний. Бизнесы, принимающие наличные средства, становятся подвергаются риску принять фальшивую купюру, что в конечном итоге может снизить прибыль и повлечь за собой судебные последствия.
Рост инфляции.
Фальшивые деньги увеличивают количество в обращении, что в свою очередь может привести к инфляции. Рост количества поддельных купюр создает дополнительный денежный объем, не обеспеченный реальными товарами и услугами. Это может существенно подорвать доверие к национальной валюте и стимулировать рост цен.
Пагуба для доверия к финансовой системе.
Фальшивые деньги вызывают недоверие к финансовой системе в целом. Когда люди сталкиваются с риском получить фальшивые купюры при каждой сделке, они становятся более склонными избегать использования наличных средств, что может привести к обострению проблем, связанных с электронными платежами и банковскими системами.
Меры безопасности и образование.
Для борьбы с распространению фальшивых денег необходимо внедрять более эффективные защитные меры на банкнотах и активно проводить образовательную работу среди населения. Гражданам нужно быть более внимательными при приеме наличных средств и обучаться элементам распознавания фальшивых купюр.
В заключение:
Фальшивые купюры 5000 рублей представляют значительную угрозу для финансовой стабильности и безопасности граждан. Необходимо активно внедрять новые технологии защиты и проводить информационные кампании, чтобы общество было лучше осведомлено о методах распознавания и защиты от фальшивых денег. Только совместные усилия банков, правоохранительных органов и общества в целом позволят минимизировать опасность подделок и обеспечить стабильность финансовой системы.
купить фальшивые деньги
Изготовление и закупка поддельных денег: опасное мероприятие
Купить фальшивые деньги может показаться привлекательным вариантом для некоторых людей, но в реальности это действие несет серьезные последствия и нарушает основы экономической стабильности. В данной статье мы рассмотрим плохие аспекты покупки поддельной валюты и почему это является опасным действием.
Противозаконность.
Первое и самое значимое, что следует отметить – это полная противозаконность изготовления и использования фальшивых денег. Такие поступки противоречат правилам большинства стран, и их штрафы может быть очень строгим. Закупка поддельной валюты влечет за собой угрозу уголовного преследования, штрафов и даже тюремного заключения.
Финансовые последствия.
Фальшивые деньги вредно влияют на экономику в целом. Когда в обращение поступает фальшивая валюта, это создает дисбаланс и ухудшает доверие к национальной валюте. Компании и граждане становятся еще более подозрительными при проведении финансовых сделок, что ведет к ухудшению бизнес-климата и тормозит нормальному функционированию рынка.
Угроза финансовой стабильности.
Фальшивые деньги могут стать угрозой финансовой стабильности государства. Когда в обращение поступает большое количество фальшивой валюты, центральные банки вынуждены принимать дополнительные меры для поддержания финансовой системы. Это может включать в себя повышение процентных ставок, что, в свою очередь, вредно сказывается на экономике и финансовых рынках.
Угрозы для честных граждан и предприятий.
Люди и компании, неосознанно принимающие фальшивые деньги в качестве оплаты, становятся пострадавшими преступных схем. Подобные ситуации могут вызвать к финансовым убыткам и потере доверия к своим деловым партнерам.
Участие криминальных группировок.
Покупка фальшивых денег часто связана с бандитскими группировками и группированным преступлением. Вовлечение в такие сети может привести к серьезными последствиями для личной безопасности и даже угрожать жизни.
В заключение, приобретение фальшивых денег – это не только неправомерное действие, но и поступок, способный причинить ущерб экономике и обществу в целом. Рекомендуется избегать подобных поступков и сосредотачиваться на легальных, ответственных способах обращения с финансами
Excellent post. I appreciate the resources and references you’ve included. They were very helpful.
jelenakaludjerovic.com
Fang Jifan의 정신이 흔들렸고 그는 테이블을 치며 “팔았다”고 말했다.
daftar hoki1881
chutneyb.com
예, 그녀는 사생아인 탕자가 도교에 능통할 수 없다는 것을 알고 있었습니다.
rikvip
rikvip
Фальшивые рубли, в большинстве случаев, копируют с целью обмана и незаконного получения прибыли. Преступники занимаются фальсификацией российских рублей, изготавливая поддельные банкноты различных номиналов. В основном, подделывают банкноты с большими номиналами, например 1 000 и 5 000 рублей, поскольку это позволяет им получать крупные суммы при меньшем количестве фальшивых денег.
Технология фальсификации рублей включает в себя использование технологического оборудования высокого уровня, специализированных печатающих устройств и специально подготовленных материалов. Преступники стремятся максимально точно воспроизвести защитные элементы, водяные знаки, металлическую защитную полосу, микротекст и прочие характеристики, чтобы препятствовать определение поддельных купюр.
Фальшивые рубли периодически попадают в обращение через торговые точки, банки или прочие учреждения, где они могут быть незаметно скрыты среди реальных денежных средств. Это порождает серьезные затруднения для экономической системы, так как поддельные купюры могут порождать убыткам как для банков, так и для граждан.
Необходимо подчеркнуть, что владение и использование фальшивых денег представляют собой уголовными преступлениями и подпадают под наказание в соответствии с нормативными актами Российской Федерации. Власти проводят активные меры с подобными правонарушениями, предпринимая действия по обнаружению и прекращению деятельности преступных групп, занимающихся подделкой российских рублей
купил фальшивые рубли
Фальшивые рубли, часто, подделывают с целью обмана и незаконного обогащения. Преступники занимаются клонированием российских рублей, формируя поддельные банкноты различных номиналов. В основном, воспроизводят банкноты с более высокими номиналами, такими как 1 000 и 5 000 рублей, ввиду того что это позволяет им зарабатывать большие суммы при меньшем количестве фальшивых денег.
Технология фальсификации рублей включает в себя применение технологического оборудования высокого уровня, специализированных принтеров и особо подготовленных материалов. Преступники стремятся наиболее точно воспроизвести защитные элементы, водяные знаки, металлическую защитную полосу, микротекст и другие характеристики, чтобы препятствовать определение поддельных купюр.
Фальшивые рубли часто попадают в обращение через торговые площадки, банки или другие организации, где они могут быть легко спрятаны среди реальных денежных средств. Это создает серьезные затруднения для финансовой системы, так как фальшивые деньги могут привести к потерям как для банков, так и для населения.
Необходимо подчеркнуть, что владение и использование поддельных средств являются уголовными преступлениями и подпадают под уголовную ответственность в соответствии с нормативными актами Российской Федерации. Власти проводят активные меры с подобными правонарушениями, предпринимая действия по выявлению и пресечению деятельности преступных групп, занимающихся фальсификацией российской валюты
I’m impressed, I have to admit. Rarely do I come
across a blog that’s equally educative and engaging,
and without a doubt, you’ve hit the nail on the head.
The problem is something too few folks are speaking intelligently about.
Now i’m very happy that I came across this during my search for something regarding
this.
娛樂城首儲
初次接觸線上娛樂城的玩家一定對選擇哪間娛樂城有障礙,首要條件肯定是評價良好的娛樂城,其次才是哪間娛樂城優惠最誘人,娛樂城體驗金多少、娛樂城首儲一倍可以拿多少等等…本篇文章會告訴你娛樂城優惠怎麼挑,首儲該注意什麼。
娛樂城首儲該注意什麼?
當您決定好娛樂城,考慮在娛樂城進行首次存款入金時,有幾件事情需要特別注意:
合法性、安全性、評價良好:確保所選擇的娛樂城是合法且受信任的。檢查其是否擁有有效的賭博牌照,以及是否採用加密技術來保護您的個人信息和交易。
首儲優惠與流水:許多娛樂城會為首次存款提供吸引人的獎勵,但相對的流水可能也會很高。
存款入金方式:查看可用的支付選項,是否適合自己,例如:USDT、超商儲值、銀行ATM轉帳等等。
提款出金方式:瞭解最低提款限制,綁訂多少流水才可以領出。
24小時客服:最好是有24小時客服,發生問題時馬上有人可以處理。
娛樂城首儲
初次接觸線上娛樂城的玩家一定對選擇哪間娛樂城有障礙,首要條件肯定是評價良好的娛樂城,其次才是哪間娛樂城優惠最誘人,娛樂城體驗金多少、娛樂城首儲一倍可以拿多少等等…本篇文章會告訴你娛樂城優惠怎麼挑,首儲該注意什麼。
娛樂城首儲該注意什麼?
當您決定好娛樂城,考慮在娛樂城進行首次存款入金時,有幾件事情需要特別注意:
合法性、安全性、評價良好:確保所選擇的娛樂城是合法且受信任的。檢查其是否擁有有效的賭博牌照,以及是否採用加密技術來保護您的個人信息和交易。
首儲優惠與流水:許多娛樂城會為首次存款提供吸引人的獎勵,但相對的流水可能也會很高。
存款入金方式:查看可用的支付選項,是否適合自己,例如:USDT、超商儲值、銀行ATM轉帳等等。
提款出金方式:瞭解最低提款限制,綁訂多少流水才可以領出。
24小時客服:最好是有24小時客服,發生問題時馬上有人可以處理。
DNA
DNABET เว็บ: มุ่งสู่ ประสบการณ์ การพนัน ที่ไม่เหมือน ที่ทุกท่าน เคย พบ!
DNABET ยัง เป็นที่นิยม เลือกที่คนนิยม ใน สาวก การเดิมพัน ทางอินเทอร์เน็ต ในประเทศไทย นี้.
ไม่จำเป็นต้อง เสียเวลา ในการเลือก เข้าร่วม DNABET เพราะที่นี่คุณ ไม่จำเป็นต้อง เลือกที่จะ จะได้รางวัล หรือไม่เหรอ!
DNABET มี ราคาจ่าย ทุก หวย สูงมาก ตั้งแต่เริ่มต้นที่ 900 บาท ขึ้นไป เมื่อ ท่าน ถูกรางวัลแล้ว จะได้รับ เงินมากมาย กว่า เว็บอื่น ๆ ที่คุณ เคย.
นอกจากนี้ DNABET ยังคง มีความหลากหลาย ลอตเตอรี่ ที่คุณสามารถเลือก มากถึง 20 หวย ทั่วโลก ทำให้คุณสามารถ เลือกเล่น ตามใจ ได้อย่างหลากหลายแบบ.
ไม่ว่าจะเป็น หวยรัฐบาลไทย หวยหุ้น หวยยี่กี ฮานอย ลาว และ ลอตเตอรี่รางวัลที่ มีราคา เพียงแค่ 80 บาท.
ทาง DNABET มั่นใจ ในการเงิน โดยที่ ได้ เปลี่ยนชื่อจาก ชันเจน เป็น DNABET เพื่อ เสริมฐานลูกค้าที่มั่นใจ และ ปรับปรุงระบบ สะดวกสบายมาก ขึ้นไป.
นอกจากนี้ DNABET ยังมีโปรโมชั่น หวย ให้เลือก หลายรายการ เช่นเดียวกับ โปรโมชั่น สมาชิกใหม่ ท่านสมัคร ในวันนี้ จะได้รับ โบนัสเพิ่ม 500 บาท หรือเครดิตทดลอง ไม่ต้อง เงิน.
นอกจากนี้ DNABET ยังมีโปรโมชั่น ประจำเดือน ท่านมีความมั่นใจ และเลือก DNABET เป็นทางเลือก การเดิมพัน หวย ของท่านเอง พร้อม โปรโมชั่น และ เหล่าโปรโมชั่น ที่ เยอะ ที่สุด ปี 2024.
อย่า ปล่อย โอกาสดีนี้ มา มาเป็นส่วนหนึ่งของ DNABET และ เพลิดเพลินกับ ประสบการณ์ การเดิมพันที่ไม่เหมือนใคร ทุกท่าน มีโอกาสจะ เป็นเศรษฐี ได้ เพียง แค่ท่าน เลือก เว็บแทงหวย ทางอินเทอร์เน็ต ที่มั่นใจ และ มีจำนวนสมาชิกมากที่สุด ในประเทศไทย!
1881 hoki
yangsfitness.com
시성된 칙령이 내려지면 정말 인간일 리가 없다.
KANTORBOLA situs gamin online terbaik 2024 yang menyediakan beragam permainan judi online easy to win , mulai dari permainan slot online , taruhan judi bola , taruhan live casino , dan toto macau . Dapatkan promo terbaru kantor bola , bonus deposit harian , bonus deposit new member , dan bonus mingguan . Kunjungi link kantorbola untuk melakukan pendaftaran .
Login Ngamenjitu
Portal Judi: Platform Lotere Daring Terluas dan Terpercaya
Portal Judi telah menjadi salah satu platform judi daring terbesar dan terpercaya di Indonesia. Dengan bervariasi pasaran yang disediakan dari Grup Semar, Portal Judi menawarkan pengalaman main togel yang tak tertandingi kepada para penggemar judi daring.
Pasaran Terbaik dan Terlengkap
Dengan total 56 market, Ngamenjitu menampilkan berbagai opsi terbaik dari pasaran togel di seluruh dunia. Mulai dari pasaran klasik seperti Sydney, Singapore, dan Hongkong hingga pasaran eksotis seperti Thailand, Germany, dan Texas Day, setiap pemain dapat menemukan market favorit mereka dengan mudah.
Metode Bermain yang Sederhana
Situs Judi menyediakan tutorial cara main yang sederhana dipahami bagi para pemula maupun penggemar togel berpengalaman. Dari langkah-langkah pendaftaran hingga penarikan kemenangan, semua informasi tersedia dengan jelas di platform Portal Judi.
Ringkasan Terkini dan Informasi Terkini
Pemain dapat mengakses hasil terakhir dari setiap pasaran secara real-time di Portal Judi. Selain itu, informasi paling baru seperti jadwal bank daring, gangguan, dan offline juga disediakan untuk memastikan kelancaran proses transaksi.
Berbagai Macam Game
Selain togel, Ngamenjitu juga menawarkan bervariasi jenis permainan kasino dan judi lainnya. Dari bingo hingga roulette, dari dragon tiger hingga baccarat, setiap pemain dapat menikmati bervariasi pilihan permainan yang menarik dan menghibur.
Keamanan dan Kepuasan Pelanggan Terjamin
Ngamenjitu mengutamakan security dan kepuasan pelanggan. Dengan sistem keamanan terbaru dan layanan pelanggan yang responsif, setiap pemain dapat bermain dengan nyaman dan tenang di situs ini.
Promosi-Promosi dan Bonus Menarik
Ngamenjitu juga menawarkan berbagai promosi dan hadiah istimewa bagi para pemain setia maupun yang baru bergabung. Dari hadiah deposit hingga bonus referral, setiap pemain memiliki kesempatan untuk meningkatkan kemenangan mereka dengan hadiah yang ditawarkan.
Dengan semua fasilitas dan layanan yang ditawarkan, Ngamenjitu tetap menjadi pilihan utama bagi para penggemar judi online di Indonesia. Bergabunglah sekarang dan nikmati pengalaman bermain yang seru dan menguntungkan di Portal Judi!
Situs Judi: Portal Lotere Online Terluas dan Terpercaya
Ngamenjitu telah menjadi salah satu situs judi daring terbesar dan terpercaya di Indonesia. Dengan bervariasi pasaran yang disediakan dari Grup Semar, Portal Judi menawarkan pengalaman bermain togel yang tak tertandingi kepada para penggemar judi daring.
Pasaran Terunggul dan Terlengkap
Dengan total 56 market, Ngamenjitu menampilkan berbagai opsi terunggul dari pasaran togel di seluruh dunia. Mulai dari market klasik seperti Sydney, Singapore, dan Hongkong hingga market eksotis seperti Thailand, Germany, dan Texas Day, setiap pemain dapat menemukan pasaran favorit mereka dengan mudah.
Metode Bermain yang Sederhana
Ngamenjitu menyediakan petunjuk cara main yang praktis dipahami bagi para pemula maupun penggemar togel berpengalaman. Dari langkah-langkah pendaftaran hingga penarikan kemenangan, semua informasi tersedia dengan jelas di platform Situs Judi.
Ringkasan Terkini dan Informasi Terkini
Pemain dapat mengakses hasil terakhir dari setiap market secara real-time di Situs Judi. Selain itu, informasi terkini seperti jadwal bank daring, gangguan, dan offline juga disediakan untuk memastikan kelancaran proses transaksi.
Bermacam-macam Macam Permainan
Selain togel, Ngamenjitu juga menawarkan berbagai jenis permainan kasino dan judi lainnya. Dari bingo hingga roulette, dari dragon tiger hingga baccarat, setiap pemain dapat menikmati berbagai pilihan permainan yang menarik dan menghibur.
Keamanan dan Kenyamanan Pelanggan Terjamin
Ngamenjitu mengutamakan security dan kepuasan pelanggan. Dengan sistem security terbaru dan layanan pelanggan yang responsif, setiap pemain dapat bermain dengan nyaman dan tenang di platform ini.
Promosi dan Hadiah Istimewa
Ngamenjitu juga menawarkan berbagai promosi dan hadiah menarik bagi para pemain setia maupun yang baru bergabung. Dari hadiah deposit hingga hadiah referral, setiap pemain memiliki kesempatan untuk meningkatkan kemenangan mereka dengan hadiah yang ditawarkan.
Dengan semua fitur dan layanan yang ditawarkan, Ngamenjitu tetap menjadi pilihan utama bagi para penggemar judi online di Indonesia. Bergabunglah sekarang dan nikmati pengalaman bermain yang seru dan menguntungkan di Ngamenjitu!
mega-slot77.com
내시는 직접 발로 차고 두려움에 떨며 “내 아들이 죽을 것입니다. “라고 말했습니다.
Ngamen jitu
Portal Judi: Situs Togel Online Terbesar dan Terpercaya
Situs Judi telah menjadi salah satu situs judi daring terbesar dan terpercaya di Indonesia. Dengan bervariasi pasaran yang disediakan dari Semar Group, Situs Judi menawarkan pengalaman bermain togel yang tak tertandingi kepada para penggemar judi daring.
Pasaran Terunggul dan Terlengkap
Dengan total 56 market, Portal Judi memperlihatkan berbagai opsi terbaik dari pasaran togel di seluruh dunia. Mulai dari pasaran klasik seperti Sydney, Singapore, dan Hongkong hingga pasaran eksotis seperti Thailand, Germany, dan Texas Day, setiap pemain dapat menemukan market favorit mereka dengan mudah.
Metode Main yang Sederhana
Situs Judi menyediakan petunjuk cara bermain yang praktis dipahami bagi para pemula maupun penggemar togel berpengalaman. Dari langkah-langkah pendaftaran hingga penarikan kemenangan, semua informasi tersedia dengan jelas di platform Portal Judi.
Rekapitulasi Terkini dan Info Terkini
Pemain dapat mengakses hasil terakhir dari setiap pasaran secara real-time di Situs Judi. Selain itu, info terkini seperti jadwal bank online, gangguan, dan offline juga disediakan untuk memastikan kelancaran proses transaksi.
Pelbagai Macam Game
Selain togel, Ngamenjitu juga menawarkan bervariasi jenis permainan kasino dan judi lainnya. Dari bingo hingga roulette, dari dragon tiger hingga baccarat, setiap pemain dapat menikmati bervariasi pilihan permainan yang menarik dan menghibur.
Keamanan dan Kepuasan Pelanggan Terjamin
Portal Judi mengutamakan keamanan dan kenyamanan pelanggan. Dengan sistem keamanan terbaru dan layanan pelanggan yang responsif, setiap pemain dapat bermain dengan nyaman dan tenang di platform ini.
Promosi dan Hadiah Menarik
Ngamenjitu juga menawarkan bervariasi promosi dan hadiah menarik bagi para pemain setia maupun yang baru bergabung. Dari bonus deposit hingga bonus referral, setiap pemain memiliki kesempatan untuk meningkatkan kemenangan mereka dengan bonus yang ditawarkan.
Dengan semua fasilitas dan layanan yang ditawarkan, Situs Judi tetap menjadi pilihan utama bagi para penggemar judi online di Indonesia. Bergabunglah sekarang dan nikmati pengalaman bermain yang seru dan menguntungkan di Portal Judi!
Ngamenjitu Login
Ngamenjitu: Portal Togel Online Terbesar dan Terjamin
Portal Judi telah menjadi salah satu platform judi daring terbesar dan terpercaya di Indonesia. Dengan beragam pasaran yang disediakan dari Semar Group, Portal Judi menawarkan pengalaman main togel yang tak tertandingi kepada para penggemar judi daring.
Pasaran Terbaik dan Terlengkap
Dengan total 56 market, Portal Judi menampilkan beberapa opsi terbaik dari market togel di seluruh dunia. Mulai dari market klasik seperti Sydney, Singapore, dan Hongkong hingga market eksotis seperti Thailand, Germany, dan Texas Day, setiap pemain dapat menemukan pasaran favorit mereka dengan mudah.
Metode Main yang Mudah
Portal Judi menyediakan panduan cara bermain yang mudah dipahami bagi para pemula maupun penggemar togel berpengalaman. Dari langkah-langkah pendaftaran hingga penarikan kemenangan, semua informasi tersedia dengan jelas di platform Portal Judi.
Hasil Terakhir dan Info Paling Baru
Pemain dapat mengakses hasil terakhir dari setiap pasaran secara real-time di Portal Judi. Selain itu, info paling baru seperti jadwal bank daring, gangguan, dan offline juga disediakan untuk memastikan kelancaran proses transaksi.
Pelbagai Macam Permainan
Selain togel, Ngamenjitu juga menawarkan bervariasi jenis permainan kasino dan judi lainnya. Dari bingo hingga roulette, dari dragon tiger hingga baccarat, setiap pemain dapat menikmati bervariasi pilihan permainan yang menarik dan menghibur.
Security dan Kenyamanan Klien Dijamin
Ngamenjitu mengutamakan security dan kepuasan pelanggan. Dengan sistem keamanan terbaru dan layanan pelanggan yang responsif, setiap pemain dapat bermain dengan nyaman dan tenang di situs ini.
Promosi-Promosi dan Hadiah Istimewa
Ngamenjitu juga menawarkan bervariasi promosi dan hadiah menarik bagi para pemain setia maupun yang baru bergabung. Dari bonus deposit hingga bonus referral, setiap pemain memiliki kesempatan untuk meningkatkan kemenangan mereka dengan bonus yang ditawarkan.
Dengan semua fitur dan pelayanan yang ditawarkan, Situs Judi tetap menjadi pilihan utama bagi para penggemar judi online di Indonesia. Bergabunglah sekarang dan nikmati pengalaman bermain yang seru dan menguntungkan di Portal Judi!
обнал карт купить
Умение осмысливать сущности и опасностей связанных с обналом кредитных карт способствует людям предупреждать атак и защищать свои финансовые средства. Обнал (отмывание) кредитных карт — это процедура использования украденных или незаконно полученных кредитных карт для совершения финансовых транзакций с целью скрыть их происхождение и предотвратить отслеживание.
Вот некоторые из способов, которые могут способствовать в уклонении от обнала кредитных карт:
Охрана личной информации: Будьте осторожными в отношении предоставления персональной информации, особенно онлайн. Избегайте предоставления картовых номеров, кодов безопасности и других конфиденциальных данных на ненадежных сайтах.
Сильные пароли: Используйте мощные и уникальные пароли для своих банковских аккаунтов и кредитных карт. Регулярно изменяйте пароли.
Мониторинг транзакций: Регулярно проверяйте выписки по кредитным картам и банковским счетам. Это поможет своевременно выявить подозрительных транзакций.
Защита от вирусов: Используйте антивирусное программное обеспечение и актуализируйте его регулярно. Это поможет предотвратить вредоносные программы, которые могут быть использованы для похищения данных.
Осторожное взаимодействие в социальных сетях: Будьте осторожными в социальных сетях, избегайте публикации чувствительной информации, которая может быть использована для взлома вашего аккаунта.
Быстрое сообщение банку: Если вы заметили какие-либо подозрительные операции или утерю карты, сразу свяжитесь с вашим банком для заблокировки карты.
Обучение: Будьте внимательными к инновационным подходам мошенничества и обучайтесь тому, как предупреждать их.
Избегая легковерия и осуществляя предупредительные действия, вы можете снизить риск стать жертвой обнала кредитных карт.
Незаконные платформы, где предлагают кэшинг пластиковых карт, представляют собой онлайн-платформы, специализирующиеся на обсуждении и осуществлении незаконных транзакций с финансовыми пластиком. На подобных форумах пользователи делают обмен данными, приемами и опытом в области кэш-аута, что влечет за собой противозаконные действия по получению доступа к денежным ресурсам.
Данные платформы способны предоставлять различные сервисы, относящиеся с преступной деятельностью, такие как фальсификация, скимминг, вредоносное программное обеспечение и прочие методы для сбора данных с банковских карт. Кроме того обсуждаются вопросы, касающиеся применением похищенных данных для осуществления финансовых операций или вывода денег.
Участники незаконных платформ по обналичиванию банковских карт могут стремиться оставаться анонимными и избегать привлечения правоохранительных органов. Участники могут делиться советами, предлагать сервисы, относящиеся к обналом, а также совершать операции, направленные на финансовое преступление.
Важно отметить, что содействие в таких практиках не только является нарушением законов, но и способно привести к правовым последствиям и уголовной ответственности.
Фальшивые 5000 купить
Опасности фальшивых 5000 рублей: Распространение фальшивых купюр и его консеквенции
В нынешнем обществе, где электронные платежи становятся все более расширенными, мошенники не оставляют без внимания и стандартные методы мошенничества, такие как распространение недостоверных банкнот. В последнее время стало известно о противозаконной реализации поддельных 5000 рублевых купюр, что представляет весомую опасность для финансовой инфраструктуры и населения в целом.
Маневры торговли:
Нарушители активно используют скрытные трассы сетевого пространства для торговли фальшивых 5000 рублей. На темных веб-ресурсах и неправомерных форумах можно обнаружить прошения о покупке поддельных банкнот. К сожалению, это создает положительные условия для распространения фальшивых денег среди общества.
Последствия для сообщества:
Присутствие контрафактных денег в потоке может иметь значительные воздействия для хозяйства и доверия к рублю. Люди, не подозревая, что получили недостоверные купюры, могут использовать их в разносторонних ситуациях, что в финале приводит к потере кредитоспособности к банкнотам определенного номинала.
Риски для граждан:
Население становятся потенциальными пострадавшими преступников, когда они непреднамеренно получают недостоверные деньги в сделках или при приобретениях. В следствие, они могут столкнуться с нелестными ситуациями, такими как отклонение торговцев принять фальшивые купюры или даже вероятность ответственности за пробу расплаты поддельными деньгами.
Противостояние с раскруткой поддельных денег:
В интересах защиты сообщества от подобных проступков необходимо укрепить мероприятия по выявлению и пресечению изготовления поддельных денег. Это включает в себя работу в партнерстве между полицией и финансовыми учреждениями, а также повышение уровня образования граждан относительно символов поддельных банкнот и способов их определения.
Итог:
Диффузия поддельных 5000 рублей – это серьезная угроза для устойчивости финансовой системы и устойчивости населения. Поддержание доверия к денежной системе требует единых действий со со стороны правительства, финансовых институтов и всех. Важно быть внимательным и осведомленным, чтобы избежать раскрутку фальшивых денег и защитить финансовые активы населения.
Покупка лживых банкнот приравнивается к незаконным иначе опасительным действием, что способно повлечь за собой глубоким юридическими воздействиям иначе повреждению индивидуальной финансовой благосостояния. Вот некоторые приводов, почему приобретение фальшивых купюр является рискованной либо неприемлемой:
Нарушение законов:
Покупка либо эксплуатация фальшивых купюр являются нарушением закона, нарушающим правила государства. Вас имеют возможность подвергнуться юридическим последствиям, что возможно закончиться задержанию, денежным наказаниям либо лишению свободы.
Ущерб доверию:
Лживые купюры подрывают веру по отношению к денежной механизму. Их поступление в оборот формирует возможность для надежных людей и организаций, которые в состоянии столкнуться с внезапными расходами.
Экономический ущерб:
Разнос лживых денег оказывает воздействие на экономическую сферу, провоцируя рост цен и ухудшая глобальную финансовую устойчивость. Это в состоянии повлечь за собой утрате уважения к денежной единице.
Риск обмана:
Люди, те, осуществляют изготовлением фальшивых купюр, не обязаны сохранять какие угодно параметры степени. Поддельные бумажные деньги могут оказаться легко выявлены, что в итоге приведет к потерям для тех, кто попытается использовать их.
Юридические последствия:
В случае задержания при применении поддельных банкнот, вас в состоянии взыскать штраф, и вы столкнетесь с юридическими трудностями. Это может отразиться на вашем будущем, с учетом проблемы с трудоустройством и кредитной историей.
Благосостояние общества и личное благополучие зависят от правдивости и уважении в денежной области. Закупка поддельных купюр идет вразрез с этими принципами и может представлять важные последствия. Рекомендуется соблюдать правил и вести только законными финансовыми операциями.
kdslot88
Ngamen jitu
Portal Judi: Situs Togel Daring Terbesar dan Terpercaya
Ngamenjitu telah menjadi salah satu situs judi online terluas dan terjamin di Indonesia. Dengan bervariasi pasaran yang disediakan dari Grup Semar, Situs Judi menawarkan pengalaman bermain togel yang tak tertandingi kepada para penggemar judi daring.
Market Terbaik dan Terpenuhi
Dengan total 56 market, Situs Judi menampilkan beberapa opsi terunggul dari market togel di seluruh dunia. Mulai dari market klasik seperti Sydney, Singapore, dan Hongkong hingga pasaran eksotis seperti Thailand, Germany, dan Texas Day, setiap pemain dapat menemukan pasaran favorit mereka dengan mudah.
Cara Main yang Praktis
Ngamenjitu menyediakan tutorial cara bermain yang praktis dipahami bagi para pemula maupun penggemar togel berpengalaman. Dari langkah-langkah pendaftaran hingga penarikan kemenangan, semua informasi tersedia dengan jelas di platform Ngamenjitu.
Rekapitulasi Terkini dan Informasi Paling Baru
Pemain dapat mengakses hasil terakhir dari setiap pasaran secara real-time di Portal Judi. Selain itu, info paling baru seperti jadwal bank online, gangguan, dan offline juga disediakan untuk memastikan kelancaran proses transaksi.
Bermacam-macam Macam Game
Selain togel, Portal Judi juga menawarkan bervariasi jenis permainan kasino dan judi lainnya. Dari bingo hingga roulette, dari dragon tiger hingga baccarat, setiap pemain dapat menikmati bervariasi pilihan permainan yang menarik dan menghibur.
Keamanan dan Kepuasan Pelanggan Dijamin
Ngamenjitu mengutamakan security dan kepuasan pelanggan. Dengan sistem keamanan terbaru dan layanan pelanggan yang responsif, setiap pemain dapat bermain dengan nyaman dan tenang di situs ini.
Promosi-Promosi dan Hadiah Istimewa
Situs Judi juga menawarkan bervariasi promosi dan hadiah istimewa bagi para pemain setia maupun yang baru bergabung. Dari hadiah deposit hingga hadiah referral, setiap pemain memiliki kesempatan untuk meningkatkan kemenangan mereka dengan bonus yang ditawarkan.
Dengan semua fitur dan layanan yang ditawarkan, Situs Judi tetap menjadi pilihan utama bagi para penggemar judi online di Indonesia. Bergabunglah sekarang dan nikmati pengalaman bermain yang seru dan menguntungkan di Ngamenjitu!
Покупка лживых банкнот является противозаконным или опасительным поступком, что имеет возможность повлечь за собой важным юридическими наказаниям либо постраданию вашей финансовой стабильности. Вот несколько других последствий, из-за чего закупка фальшивых купюр представляет собой опасной либо неуместной:
Нарушение законов:
Приобретение и воспользование лживых денег приравниваются к противоправным деянием, нарушающим правила общества. Вас имеют возможность подвергнуть уголовной ответственности, что может закончиться задержанию, финансовым санкциям и приводу в тюрьму.
Ущерб доверию:
Фальшивые купюры ухудшают уверенность по отношению к финансовой механизму. Их обращение формирует угрозу для надежных гражданских лиц и коммерческих структур, которые имеют возможность претерпеть неожиданными убытками.
Экономический ущерб:
Распространение фальшивых купюр осуществляет воздействие на экономику, вызывая распределение денег и ухудшающая глобальную экономическую устойчивость. Это может привести к потере уважения к валютной единице.
Риск обмана:
Люди, которые, вовлечены в изготовлением контрафактных купюр, не обязаны соблюдать какие-либо уровни характеристики. Лживые деньги могут оказаться легко распознаваемы, что в конечном счете приведет к расходам для тех, кто пытается их использовать.
Юридические последствия:
В ситуации попадания под арест за использование поддельных купюр, вас в состоянии наказать штрафом, и вы столкнетесь с юридическими проблемами. Это может сказаться на вашем будущем, в том числе сложности с получением работы и кредитной историей.
Общественное и личное благополучие основываются на честности и доверии в денежной области. Получение поддельных купюр идет вразрез с этими принципами и может порождать серьезные последствия. Рекомендуем придерживаться законов и заниматься исключительно законными финансовыми действиями.
где можно купить фальшивые деньги
Покупка поддельных денег представляет собой недозволенным иначе потенциально опасным делом, которое имеет возможность повлечь за собой глубоким правовым санкциям или постраданию своей финансовой надежности. Вот несколько последствий, из-за чего закупка лживых банкнот является рискованной иначе неуместной:
Нарушение законов:
Закупка иначе применение поддельных купюр являются преступлением, нарушающим правила территории. Вас способны подвергнуть себя наказанию, что может повлечь за собой лишению свободы, денежным наказаниям иначе тюремному заключению.
Ущерб доверию:
Лживые банкноты ухудшают доверенность в денежной механизму. Их обращение создает риск для порядочных людей и предприятий, которые способны попасть в неожиданными расходами.
Экономический ущерб:
Распространение лживых денег влияет на экономику, вызывая распределение денег и ухудшающая всеобщую экономическую равновесие. Это может закончиться потере уважения к денежной единице.
Риск обмана:
Те, те, занимается созданием поддельных денег, не обязаны соблюдать какие угодно стандарты качества. Лживые бумажные деньги могут стать легко распознаны, что в итоге повлечь за собой расходам для тех, кто пытается использовать их.
Юридические последствия:
При случае захвата при воспользовании фальшивых купюр, вас могут принудительно обложить штрафами, и вы столкнетесь с юридическими трудностями. Это может оказать воздействие на вашем будущем, включая сложности с получением работы и историей кредита.
Общественное и индивидуальное благосостояние зависят от честности и доверии в финансовых отношениях. Получение лживых банкнот не соответствует этим принципам и может представлять важные последствия. Предлагается держаться норм и вести только законными финансовыми сделками.
Покупка контрафактных купюр представляет собой противозаконным либо опасным актом, которое в состоянии послать в глубоким законным наказаниям и ущербу личной финансовой устойчивости. Вот несколько других приводов, почему закупка лживых денег представляет собой потенциально опасной или недопустимой:
Нарушение законов:
Покупка или эксплуатация контрафактных банкнот считаются правонарушением, нарушающим положения государства. Вас способны подвергнуть себя юридическим последствиям, которое может повлечь за собой лишению свободы, взысканиям либо постановлению под стражу.
Ущерб доверию:
Контрафактные банкноты нарушают доверенность по отношению к финансовой системе. Их использование порождает опасность для надежных гражданских лиц и коммерческих структур, которые могут столкнуться с неожиданными расходами.
Экономический ущерб:
Разнос фальшивых денег осуществляет воздействие на экономику, провоцируя инфляцию и подрывая всеобщую финансовую равновесие. Это может повлечь за собой потере уважения к национальной валюте.
Риск обмана:
Те, кто, вовлечены в производством поддельных купюр, не обязаны поддерживать какие угодно нормы степени. Поддельные деньги могут оказаться легко распознаваемы, что, в конечном итоге закончится расходам для тех, кто собирается их использовать.
Юридические последствия:
В случае захвата при применении лживых банкнот, вас в состоянии оштрафовать, и вы столкнетесь с законными сложностями. Это может оказать воздействие на вашем будущем, с учетом проблемы с трудоустройством и кредитной историей.
Общественное и личное благополучие зависят от честности и доверии в финансовых отношениях. Приобретение поддельных купюр не соответствует этим принципам и может порождать серьезные последствия. Предлагается соблюдать правил и вести только законными финансовыми операциями.
Покупка фальшивых денег считается недозволенным либо рискованным делом, которое в состоянии послать в важным законным воздействиям или постраданию своей финансовой устойчивости. Вот некоторые другие примет, по какой причине получение поддельных купюр представляет собой потенциально опасной и неприемлемой:
Нарушение законов:
Получение либо воспользование контрафактных денег являются нарушением закона, нарушающим положения общества. Вас имеют возможность подвергнуться юридическим последствиям, которое может закончиться тюремному заключению, денежным наказаниям либо лишению свободы.
Ущерб доверию:
Поддельные деньги ухудшают доверие по отношению к финансовой механизму. Их обращение создает риск для порядочных гражданских лиц и бизнесов, которые могут столкнуться с внезапными перебоями.
Экономический ущерб:
Разведение контрафактных купюр осуществляет воздействие на экономическую сферу, инициируя денежное расширение и подрывая глобальную экономическую устойчивость. Это способно повлечь за собой утрате уважения к денежной системе.
Риск обмана:
Люди, какие, осуществляют изготовлением фальшивых банкнот, не обязаны поддерживать какие угодно параметры качества. Поддельные деньги могут оказаться легко распознаваемы, что в итоге приведет к ущербу для тех стремится воспользоваться ими.
Юридические последствия:
В ситуации лишения свободы за использование лживых купюр, вас способны оштрафовать, и вы столкнетесь с законными сложностями. Это может оказать воздействие на вашем будущем, включая сложности с трудоустройством с кредитной историей.
Общественное и индивидуальное благосостояние зависят от правдивости и уважении в финансовых отношениях. Приобретение поддельных банкнот не соответствует этим принципам и может представлять серьезные последствия. Рекомендуем держаться правил и заниматься только легальными финансовыми операциями.
Покупка контрафактных банкнот считается противозаконным или опасным делом, что в состоянии закончиться важным законным наказаниям либо повреждению личной денежной благосостояния. Вот несколько других приводов, по какой причине получение контрафактных купюр считается опасительной и неприемлемой:
Нарушение законов:
Закупка и использование фальшивых денег представляют собой нарушением закона, противоречащим нормы общества. Вас имеют возможность подвергнуть себя наказанию, что потенциально привести к лишению свободы, штрафам либо тюремному заключению.
Ущерб доверию:
Контрафактные деньги нарушают доверенность по отношению к финансовой механизму. Их использование порождает риск для надежных людей и предприятий, которые в состоянии завязать неожиданными потерями.
Экономический ущерб:
Разведение поддельных купюр причиняет воздействие на финансовую систему, вызывая распределение денег и ухудшающая общую экономическую стабильность. Это в состоянии послать в потере уважения к денежной системе.
Риск обмана:
Личности, те, осуществляют производством лживых денег, не обязаны соблюдать какие-нибудь стандарты характеристики. Фальшивые бумажные деньги могут быть легко распознаны, что, в итоге повлечь за собой убыткам для тех собирается их использовать.
Юридические последствия:
В случае задержания при воспользовании фальшивых купюр, вас способны принудительно обложить штрафами, и вы столкнетесь с законными сложностями. Это может отразиться на вашем будущем, включая трудности с получением работы и кредитной историей.
Благосостояние общества и личное благополучие зависят от честности и доверии в финансовой сфере. Приобретение фальшивых банкнот идет вразрез с этими принципами и может представлять важные последствия. Советуем придерживаться правил и осуществлять только законными финансовыми действиями.
Обналичивание карт – это незаконная деятельность, становящаяся все более широко распространенной в нашем современном мире электронных платежей. Этот вид мошенничества представляет серьезные вызовы для банков, правоохранительных органов и общества в целом. В данной статье мы рассмотрим частоту встречаемости обналичивания карт, используемые методы и возможные последствия для жертв и общества.
Частота обналичивания карт:
Обналичивание карт является достаточно распространенным явлением, и его частота постоянно растет с увеличением числа электронных транзакций. Киберпреступники применяют различные методы для получения доступа к финансовым средствам, включая фишинг, вредоносное программное обеспечение, скимминг и другие инновационные подходы.
Методы обналичивания карт:
Фишинг: Злоумышленники могут отправлять ложные электронные сообщения или создавать веб-сайты, имитирующие банковские системы, с целью получения личной информации от владельцев карт.
Скимминг: Злоумышленники устанавливают устройства скиммеры на банкоматах или терминалах для считывания данных с магнитных полос карт.
Вредоносное программное обеспечение: Киберпреступники разрабатывают вредоносные программы, которые заражают компьютеры и мобильные устройства, чтобы получить доступ к личным данным и банковским счетам.
Сетевые атаки: Атаки на системы банков и платежных платформ могут привести к утечке информации о картах и, следовательно, к их обналичиванию.
Последствия обналичивания карт:
Финансовые потери для клиентов: Владельцы карт могут столкнуться с материальными потерями, так как средства могут быть списаны с их счетов без их ведома.
Угроза безопасности данных: Обналичивание карт подчеркивает угрозу безопасности личных данных, что может привести к краже личной и финансовой информации.
Ущерб репутации банков: Банки и другие финансовые учреждения могут столкнуться с утратой доверия со стороны клиентов, если их системы безопасности оказываются уязвимыми.
Проблемы для экономики: Обналичивание карт создает экономический ущерб, поскольку оно стимулирует дополнительные затраты на борьбу с мошенничеством и восстановление утраченных средств.
Борьба с обналичиванием карт:
Совершенствование технологий безопасности: Банки и финансовые институты постоянно совершенствуют свои системы безопасности, чтобы предотвратить несанкционированный доступ к картам.
Образование и информирование: Обучение клиентов о методах мошенничества и том, как защитить свои данные, является важным шагом в борьбе с обналичиванием карт.
Сотрудничество с правоохранительными органами: Банки активно сотрудничают с правоохранительными органами для выявления и пресечения преступных схем.
Заключение:
Обналичивание карт – серьезная угроза для финансовой стабильности и безопасности личных данных. Решение этой проблемы требует совместных усилий со стороны банков, правоохранительных органов и общества в целом. Только эффективная борьба с мошенничеством позволит обеспечить безопасность электронных платежей и защитить интересы всех участников финансовой системы.
Опасности поддельными 5000 рублей: Распространение контрафактных купюр и его консеквенции
В сегодняшнем обществе, где виртуальные платежи становятся все более расширенными, мошенники не оставляют без внимания и обычные методы преступной деятельности, такие как передача поддельных банкнот. В настоящее время стало известно о противозаконной сбыте фальшивых 5000 рублевых купюр, что представляет серьезную угрозу для денежной системы и сообщества в итоге.
Методы распространения:
Мошенники активно используют скрытные сети веба для реализации контрафактных 5000 рублей. На закулисных веб-ресурсах и незаконных форумах можно обнаружить предложения контрафактных банкнот. К неудаче, это создает хорошие условия для дистрибуции поддельных денег среди людей.
Консеквенции для общества:
Возможность контрафактных денег в циркуляции может иметь весомые консеквенции для финансовой структуры и авторитета к денежной единице. Люди, не подозревая, что получили поддельные купюры, могут использовать их в различных ситуациях, что в последней инстанции приводит к вреду поверию к банкнотам некоего номинала.
Угрозы для населения:
Люди становятся возможными пострадавшими оскорбителей, когда они ненамеренно получают контрафактные деньги в сделках или при приобретениях. В результате, они могут столкнуться с неприятными ситуациями, такими как отказ от признания торговых посредников принять недостоверные купюры или даже вероятность юридической ответственности за пробу расплаты фальшивыми деньгами.
Противостояние с передачей контрафактных денег:
В интересах сохранения общества от таких же проступков необходимо прокачать мероприятия по выяснению и остановке изготовления контрафактных денег. Это включает в себя взаимодействие между полицией и финансовыми организациями, а также расширение уровня просвещения населения относительно характеристик поддельных банкнот и техник их определения.
Завершение:
Распространение недостоверных 5000 рублей – это важная опасность для финансового благополучия и устойчивости граждан. Поддержание доверенности к рублю требует коллективных усилий со с участием государства, финансовых организаций и всех. Важно быть осторожным и знающим, чтобы предупредить прокладывание недостоверных денег и обеспечить денежные интересы общества.
smcasino7.com
그는 폐하를 만류하고 싶다는 말을 감히 하지 못하고 그냥 모든 신하들을 끌어냈다.
купил фальшивые рубли
Покупка поддельных денег считается неправомерным и опасным поступком, которое способно закончиться тяжелым правовым санкциям и повреждению вашей денежной стабильности. Вот несколько других приводов, по какой причине приобретение контрафактных банкнот представляет собой опасительной либо недопустимой:
Нарушение законов:
Покупка и эксплуатация лживых денег приравниваются к противоправным деянием, подрывающим положения общества. Вас в состоянии подвергнуть юридическим последствиям, что может послать в тюремному заключению, штрафам иначе приводу в тюрьму.
Ущерб доверию:
Лживые банкноты подрывают доверенность к финансовой структуре. Их применение создает опасность для порядочных людей и предприятий, которые в состоянии претерпеть непредвиденными потерями.
Экономический ущерб:
Разнос контрафактных денег причиняет воздействие на хозяйство, вызывая рост цен что ухудшает всеобщую экономическую стабильность. Это имеет возможность закончиться утрате уважения к денежной системе.
Риск обмана:
Люди, те, вовлечены в изготовлением контрафактных денег, не обязаны соблюдать какие-то нормы качества. Фальшивые бумажные деньги могут быть легко обнаружены, что, в конечном итоге закончится расходам для тех, кто пытается их использовать.
Юридические последствия:
При случае задержания при применении лживых купюр, вас в состоянии принудительно обложить штрафами, и вы столкнетесь с юридическими проблемами. Это может повлиять на вашем будущем, включая проблемы с поиском работы и историей кредита.
Общественное и индивидуальное благосостояние основываются на честности и доверии в финансовых отношениях. Получение лживых банкнот нарушает эти принципы и может представлять серьезные последствия. Предлагается соблюдать правил и заниматься исключительно законными финансовыми сделками.
Обналичивание карт – это неправомерная деятельность, становящаяся все более широко распространенной в нашем современном мире электронных платежей. Этот вид мошенничества представляет тяжелые вызовы для банков, правоохранительных органов и общества в целом. В данной статье мы рассмотрим частоту встречаемости обналичивания карт, используемые методы и возможные последствия для жертв и общества.
Частота обналичивания карт:
Обналичивание карт является довольно распространенным явлением, и его частота постоянно растет с увеличением числа электронных транзакций. Киберпреступники применяют разные методы для получения доступа к финансовым средствам, включая фишинг, вредоносное программное обеспечение, скимминг и другие инновационные подходы.
Методы обналичивания карт:
Фишинг: Злоумышленники могут отправлять фальшивые электронные сообщения или создавать веб-сайты, имитирующие банковские системы, с целью получения личной информации от владельцев карт.
Скимминг: Злоумышленники устанавливают устройства скиммеры на банкоматах или терминалах для считывания данных с магнитных полос карт.
Вредоносное программное обеспечение: Киберпреступники разрабатывают вредоносные программы, которые заражают компьютеры и мобильные устройства, чтобы получить доступ к личным данным и банковским счетам.
Сетевые атаки: Атаки на системы банков и платежных платформ могут привести к утечке информации о картах и, следовательно, к их обналичиванию.
Последствия обналичивания карт:
Финансовые потери для клиентов: Владельцы карт могут столкнуться с финансовыми потерями, так как средства могут быть списаны с их счетов без их ведома.
Угроза безопасности данных: Обналичивание карт подчеркивает угрозу безопасности личных данных, что может привести к краже личной и финансовой информации.
Ущерб репутации банков: Банки и другие финансовые учреждения могут столкнуться с утратой доверия со стороны клиентов, если их системы безопасности оказываются уязвимыми.
Проблемы для экономики: Обналичивание карт создает экономический ущерб, поскольку оно стимулирует дополнительные затраты на борьбу с мошенничеством и восстановление утраченных средств.
Борьба с обналичиванием карт:
Совершенствование технологий безопасности: Банки и финансовые институты постоянно совершенствуют свои системы безопасности, чтобы предотвратить несанкционированный доступ к картам.
Образование и информирование: Обучение клиентов о методах мошенничества и том, как защитить свои данные, является важным шагом в борьбе с обналичиванием карт.
Сотрудничество с правоохранительными органами: Банки активно сотрудничают с правоохранительными органами для выявления и пресечения преступных схем.
Заключение:
Обналичивание карт – значительная угроза для финансовой стабильности и безопасности личных данных. Решение этой проблемы требует совместных усилий со стороны банков, правоохранительных органов и общества в целом. Только эффективная борьба с мошенничеством позволит обеспечить безопасность электронных платежей и защитить интересы всех участников финансовой системы.
Обналичивание карт – это неправомерная деятельность, становящаяся все более распространенной в нашем современном мире электронных платежей. Этот вид мошенничества представляет серьезные вызовы для банков, правоохранительных органов и общества в целом. В данной статье мы рассмотрим частоту встречаемости обналичивания карт, используемые методы и возможные последствия для жертв и общества.
Частота обналичивания карт:
Обналичивание карт является довольно распространенным явлением, и его частота постоянно растет с увеличением числа электронных транзакций. Киберпреступники применяют разнообразные методы для получения доступа к финансовым средствам, включая фишинг, вредоносное программное обеспечение, скимминг и другие инновационные подходы.
Методы обналичивания карт:
Фишинг: Злоумышленники могут отправлять поддельные электронные сообщения или создавать веб-сайты, имитирующие банковские системы, с целью получения личной информации от владельцев карт.
Скимминг: Злоумышленники устанавливают устройства скиммеры на банкоматах или терминалах для считывания данных с магнитных полос карт.
Вредоносное программное обеспечение: Киберпреступники разрабатывают вредоносные программы, которые заражают компьютеры и мобильные устройства, чтобы получить доступ к личным данным и банковским счетам.
Сетевые атаки: Атаки на системы банков и платежных платформ могут привести к утечке информации о картах и, следовательно, к их обналичиванию.
Последствия обналичивания карт:
Финансовые потери для клиентов: Владельцы карт могут столкнуться с денежными потерями, так как средства могут быть списаны с их счетов без их ведома.
Угроза безопасности данных: Обналичивание карт подчеркивает угрозу безопасности личных данных, что может привести к краже личной и финансовой информации.
Ущерб репутации банков: Банки и другие финансовые учреждения могут столкнуться с утратой доверия со стороны клиентов, если их системы безопасности оказываются уязвимыми.
Проблемы для экономики: Обналичивание карт создает экономический ущерб, поскольку оно стимулирует дополнительные затраты на борьбу с мошенничеством и восстановление утраченных средств.
Борьба с обналичиванием карт:
Совершенствование технологий безопасности: Банки и финансовые институты постоянно совершенствуют свои системы безопасности, чтобы предотвратить несанкционированный доступ к картам.
Образование и информирование: Обучение клиентов о методах мошенничества и том, как защитить свои данные, является важным шагом в борьбе с обналичиванием карт.
Сотрудничество с правоохранительными органами: Банки активно сотрудничают с правоохранительными органами для выявления и пресечения преступных схем.
Заключение:
Обналичивание карт – серьезная угроза для финансовой стабильности и безопасности личных данных. Решение этой проблемы требует совместных усилий со стороны банков, правоохранительных органов и общества в целом. Только эффективная борьба с мошенничеством позволит обеспечить безопасность электронных платежей и защитить интересы всех участников финансовой системы.
strelkaproject.com
홀에서 아기의 울음소리를 듣고 팡지판의 마음이 녹아내렸다.
Умение осмысливать сущности и угроз связанных с легализацией кредитных карт способствует людям предотвращать атак и защищать свои финансовые ресурсы. Обнал (отмывание) кредитных карт — это механизм использования украденных или нелегально добытых кредитных карт для проведения финансовых транзакций с целью скрыть их происхождение и пресечь отслеживание.
Вот некоторые из способов, которые могут содействовать в предотвращении обнала кредитных карт:
Защита личной информации: Будьте осторожными в контексте предоставления персональной информации, особенно онлайн. Избегайте предоставления банковских карт, кодов безопасности и дополнительных конфиденциальных данных на сомнительных сайтах.
Сильные пароли: Используйте мощные и уникальные пароли для своих банковских аккаунтов и кредитных карт. Регулярно изменяйте пароли.
Мониторинг транзакций: Регулярно проверяйте выписки по кредитным картам и банковским счетам. Это поможет своевременно выявить подозрительных транзакций.
Программы антивирус: Используйте антивирусное программное обеспечение и обновляйте его регулярно. Это поможет защитить от вредоносные программы, которые могут быть использованы для изъятия данных.
Осторожное взаимодействие в социальных сетях: Будьте осторожными в социальных сетях, избегайте размещения чувствительной информации, которая может быть использована для взлома вашего аккаунта.
Уведомление банка: Если вы заметили какие-либо подозрительные операции или утерю карты, сразу свяжитесь с вашим банком для заблокировки карты.
Получение знаний: Будьте внимательными к современным приемам мошенничества и обучайтесь тому, как предотвращать их.
Избегая легковерия и проявляя предельную осторожность, вы можете снизить риск стать жертвой обнала кредитных карт.
hoki1881
Kantorbola adalah situs slot gacor terbaik di indonesia , kunjungi situs RTP kantor bola untuk mendapatkan informasi akurat slot dengan rtp diatas 95% . Kunjungi juga link alternatif kami di kantorbola77 dan kantorbola99 .
Your reading thinking ability must be great. therefore can be conveyed in this article.
zinmanga
hoki1881
Your article has sparked a conversation that I believe is important and necessary.
ttbslot.com
Wu Yan은 “폐하, 제가 이야기하고 싶은 것은 황제의 손자에 관한 것입니다. “라고 말했습니다.
טלגראס תל אביב
מרכזי המַרכֵּז עבור טלגראס כיוונים (Telegrass), נוֹדַע גם בשמות “רִיחֲמִים” או “רִיחֲמִים כיוונים”, היא אתר סוֹפֵק מידע, לינקים, קישורים, מדריכים והסברים בנושאי קנאביס בתוך הארץ. באמצעות האתר, משתמשים יכולים למצוא את כל הקישורים המעודכנים עבור ערוצים מומלצים ופעילים בטלגראס כיוונים בכל רחבי הארץ.
טלגראס כיוונים הוא אתר ובוט בתוך פלטפורמת טלגראס, שמספקים דרכי תקשורת ושירותים מגוונים בתחום רכישת קנאביס וקשורים. באמצעות הבוט, המשתמשים יכולים לבצע מגוון פעולות בקשר לרכישת קנאביס ולשירותים נוספים, תוך כדי תקשורת עם מערכת אוטומטית המבצעת את הפעולות בצורה חכמה ומהירה.
בוט הטלגראס (Telegrass Bot) מציע מגוון פעולות שימושיות למשתמשות: הזמנת קנאביס: בצע הזמנה דרך הבוט על ידי בחירת סוגי הקנאביס, כמות וכתובת למשלוח.
הוראות ותמיכה: קבל מידע על המוצרים והשירותים, תמיכה טכנית ותשובות לשאלות שונות.
בדיקה מלאי: בדוק את המלאי הזמין של קנאביס ובצע הזמנה תוך כדי הקשת הבדיקה.
הוסיפו ביקורות: הוסף ביקורות ודירוגים למוצרים שרכשת, כדי לעזור למשתמשים אחרים.
הכנסת מוצרים חדשים: הוסף מוצרים חדשים לפלטפורמה והצג אותם למשתמשים.
בקיצור, בוט הטלגראס הוא כלי חשוב ונוח שמקל על השימוש והתקשורת בנושאי קנאביס, מאפשר מגוון פעולות שונות ומספק מידע ותמיכה למשתמשים.
I’m gone to tell my little brother, that he should also visit this website on regular basis to get updated from most up-to-date reports.
Your post is a ray of light in the darkness. Thank you for brightening my day in a unique way. Keep shining!
ttbslot.com
이것이 황제의 지위인데 얼마나 많은 사람들이 그것을 놓치고 있습니까!
Your post is a ray of light in the darkness. Thank you for brightening my day in a unique way. Keep shining!
wonderful day commencing with a tremendous reading 📚🌅
hoki 1881
Thank you for sharing your knowledge and expertise with the world.
Даркнет-площадки, или теневые рынки, являются сетевые платформы, доступные лишь путем скрытую сеть – всемирную сеть, скрытая для рядовых поисковых систем. Данные рынки разрешают пользователям торговать разнообразными товарными единицами а услугами, чаще всего противозаконного специфики, такими как наркотики, вооружение, данные, похищенные из систем, фальшивые документы или другие запретные или неправомерные продукты или сервисы.
Темные площадки предоставляют инкогнито своих субъектов посредством использования особенных приложений или настроек, таких как Tor, которые замаскировывают IP-адреса или маршрутизируют интернет-трафик с помощью разносторонние узловые точки, что делает непростым прослеживание деятельности полицейскими.
Данные площадки часто попадают целью внимания правоохранительных органов, какие именно борются за противодействуют ними в рамках борьбы против киберпреступностью и нелегальной продажей.
тор даркнет
Тор даркнет – это компонент интернета, какая, которая работает поверх обыкновеннои? сети, впрочем не доступна для непосредственного входа через обыкновенные браузеры, такие как Google Chrome или Mozilla Firefox. Для входа к этому сети необходимо специальное програмное обеспечение, вроде, Tor Browser, которыи? обеспечивает анонимность и сафети пользователеи?.
Основнои? принцип работы Тор даркнета основан на использовании путеи? через различные точки, которые кодируют и перенаправляют трафик, создавая сложным трекинг его источника. Это создает секретность для пользователеи?, укрывая их настоящие IP-адреса и местоположение.
Тор даркнет включает различные источники, включая веб-саи?ты, форумы, рынки, блоги и прочие онлаи?н-ресурсы. Некоторые из подобных ресурсов могут быть недоступны или запрещены в стандартнои? сети, что делает Тор даркнет полем для подачи информациеи? и услугами, включая товары и услуги, которые могут быть незаконными.
Хотя Тор даркнет используется некоторыми людьми для пересечения цензуры или протекции приватности, он также становится платформои? для разнообразных незаконных деи?ствии?, таких как торговля наркотиками, оружием, кража личных данных, предоставление услуг хакеров и другие преступные поступки.
Важно осознавать, что использование Тор даркнета не обязательно законно и может в себя серьезные риски для защиты и законности.
hoki1881
даркнет россия
государстве, так же и в иных территориях, даркнет является собой часть интернета, неприступную для стандартного поиска и пересмотра через регулярные навигаторы. В разница от общеизвестной поверхностной соединения, скрытая часть интернета считается неизвестным куском интернета, доступ к которому регулярно делается через специальные приложения, такие как Tor Browser, и анонимные инфраструктуры, наподобные Tor.
В даркнете сосредоточены различные материалы, включая конференции, торговые площадки, блоги и остальные веб-сайты, которые могут стать недоступны или пресечены в регулярной инфраструктуре. Здесь допускается найти различные продукты и услуги, включая нелегальные, например наркотики, оружие, компрометированные информация, а также сервисы компьютерных взломщиков и другие.
В стране даркнет как и используется для пересечения цензуры и мониторинга со партии. Некоторые участники могут выпользовать его для передачи информацией в условиях, когда свобода слова заблокирована или информационные материалы подвергнуты цензуре. Однако, также рекомендуется отметить, что в скрытой части интернета присутствует много законодательной деятельности и потенциально опасных положений, включая надувательство и интернет-преступления
qiyezp.com
결국 Daming 지폐는 신용도가 우수하고 휴대 및 거래가 매우 편리합니다.
Даркнет заказать
Присутствие скрытых интернет-площадок – это процесс, который привлекает большой заинтересованность или разговоры в современном сообществе. Скрытая сторона сети, или подпольная область всемирной сети, отображает тайную инфраструктуру, доступную только при помощи особые программные продукты или конфигурации, снабжающие инкогнито пользовательских аккаунтов. По данной скрытой сети расположены даркнет-маркеты – интернет-ресурсы, где-либо торговля разные вещи а сервисы, чаще всего незаконного специфики.
На скрытых интернет-площадках можно отыскать самые разные товары: наркотики, оружие, украденные данные, взломанные учетные записи, фальшивые документы или и многое. Такие рынки порой притягивают внимание как преступников, и обычных пользовательских аккаунтов, желающих пройти мимо юриспруденция или даже получить доступ к товары или сервисам, какие именно в стандартном сети могли бы быть недосягаемы.
Тем не менее стоит помнить, каким образом практика в подпольных рынках является незаконный специфику а имеет возможность создать важные юридические нормы наказания. Полицейские органы энергично борются за противодействуют такими рынками, но все же вследствие скрытности темной стороны интернета данный факт далеко не всегда без проблем.
Следовательно, существование теневых электронных базаров составляет фактом, и все же таковые останавливаются местом крупных потенциальных угроз как для субъектов, и для таких, как социума во в целом и целом.
werankcities.com
Hongzhi 황제의 얼굴이 즉시 어두워졌습니다. “당신은 …”
Покупки в подпольной сети: Мифы и Правда
Даркнет, скрытая часть интернета, заинтересовывает внимание участников своим анонимностью и способностью приобрести самые разнообразные вещи и сервисы без лишних вопросов. Однако, переход в этот мрак скрытых площадок имеет в себе с комплексом рисков и нюансов, о чем необходимо осведомляться перед совершением покупок.
Что представляет собой подпольная сеть и как он работает?
Для тех, кому не знакомо с этим термином, скрытая часть веба – это сегмент интернета, невидимая от обычных поисковиков. В темном интернете существуют специальные онлайн-рынки, где можно найти практически все : от запрещённых веществ и боеприпасов до взломанных аккаунтов и фальшивых документов.
Мифы о приобретении товаров в Даркнете
Тайность защищена: При всём том, использование анонимных технологий, вроде как Tor, способствует скрыть от глаз свою действия в интернете, анонимность в Даркнете не является полной. Имеется возможность, что вашу информацию о вас могут раскрыть обманщики или даже сотрудники правоохранительных органов.
Все товары – качественные товары: В Даркнете можно найти множество торговцев, предлагающих товары и услуги. Однако, нельзя гарантировать качественность или подлинность товара, поскольку нет возможности провести проверку до совершения покупки.
Легальные покупки без ответственности: Многие пользователи неправильно думают, что товары в Даркнете, они рискуют меньшему риску, чем в реальной жизни. Однако, заказывая незаконные вещи или сервисы, вы подвергаете себя уголовной ответственности.
Реальность приобретений в Даркнете
Опасности мошенничества и афер: В темном интернете многочисленные аферисты, которые готовы обмануть невнимательных клиентов. Они могут предложить поддельную продукцию или просто исчезнуть, оставив вас без денег.
Опасность государственных органов: Участники подпольной сети рискуют к уголовной ответственности за заказ и приобретение неправомерных продуктов и услуг.
Неопределённость выходов: Не все покупки в темном интернете приводят к успешному результату. Качество вещей может оказаться неудовлетворительным, а
процесс заказа может привести к неприятным последствиям.
Советы для безопасных покупок в скрытой части веба
Проводите детальный анализ поставщика и услуги перед совершением покупки.
Используйте защитные программы и сервисы для защиты вашей анонимности и безопасности.
Платите только безопасными методами, такими как криптовалюты, и избегайте предоставления личной информации.
Будьте предельно внимательны и осторожны во всех ваших действиях и решениях.
Заключение
Покупки в темном интернете могут быть как интересным, так и рискованным опытом. Понимание возможных опасностей и принятие необходимых мер предосторожности помогут снизить вероятность негативных последствий и обеспечить безопасность при совершении покупок в этом неизведанном мире интернета.
даркнет запрещён
Покупки в темном интернете: Иллюзии и Правда
Подпольная сеть, загадочная область интернета, привлекает интерес участников своим анонимностью и возможностью купить различные продукты и услуги без излишних действий. Однако, погружение в этот вселенная непрозрачных торгов связано с рядом рисков и аспектов, о которых желательно осведомляться перед проведением покупок.
Что такое подпольная сеть и как это функционирует?
Для того, кому не знакомо с этим термином, темный интернет – это сегмент веба, невидимая от обычных поисковиков. В Даркнете имеются уникальные рынки, где можно найти практически все, что угодно : от наркотиков и оружия и поддельных удостоверений и взломанных аккаунтов.
Заблуждения о заказах в скрытой части веба
Анонимность гарантирована: В то время как, применение анонимных технологий, вроде как Tor, способно помочь закрыть свою активность в интернете, анонимность в темном интернете не является. Существует риск, что возможно ваша личную информацию могут обнаружить дезинформаторы или даже сотрудники правоохранительных органов.
Все товары – высокого качества: В темном интернете можно найти множество поставщиков, предоставляющих продукты и сервисы. Однако, нельзя гарантировать качественность или оригинальность продукции, так как невозможно проверить до того, как вы сделаете заказ.
Легальные транзакции без последствий: Многие пользователи по ошибке считают, что заказывая товары в Даркнете, они подвергают себя риску меньшим риском, чем в реальной жизни. Однако, заказывая незаконные вещи или услуги, вы подвергаете себя риску уголовной ответственности.
Реальность покупок в скрытой части веба
Негативные стороны мошенничества и афер: В скрытой части веба множество мошенников, предрасположены к мошенничеству недостаточно осторожных пользователей. Они могут предложить фальшивые товары или просто исчезнуть с вашими деньгами.
Опасность государственных органов: Участники подпольной сети рискуют привлечения к уголовной ответственности за покупку и заказ противозаконных.
Непредвиденность выходов: Не каждая сделка в Даркнете приводят к успешному результату. Качество вещей может оказаться неудовлетворительным, а процесс покупки может послужить источником неприятностей.
Советы для безопасных сделок в скрытой части веба
Проводите детальный анализ поставщика и услуги перед приобретением.
Используйте защитные программы и сервисы для обеспечения вашей анонимности и безопасности.
Осуществляйте платежи только безопасными методами, например, криптовалютами, и не раскрывайте личные данные.
Будьте предельно внимательны и осторожны во всех ваших действиях и решениях.
Заключение
Покупки в Даркнете могут быть как захватывающим, так и рискованным опытом. Понимание рисков и применение соответствующих мер предосторожности помогут снизить вероятность негативных последствий и гарантировать безопасные покупки в этом неизведанном мире интернета.
I wanted to take a moment to express my heartfelt gratitude for your outstanding article. Your insights have truly enlightened me.
הימורים באינטרנט – מימורי ספורטיביים, קזינו מקוון, משחקי קלפי.
המימונים באינטרנט הופכים לקטגוריה נפוץ במיוחדים בתקופת הדיגיטלי.
מיליוני משתתפים מנסים את מזלם במגוון הימורים המגוונים.
הפעולה הזה משנה את רגעי הניסיון וההתרגשות השחקנים.
גם מעסיק בשאלות חברתיות ואתיות העומדות ממאחורי ההימורים המקוונים.
בתקופת הדיגיטלי, הימורים ברשת הם חלק מהותי מתרבות הספורט, הפנאי והבידור והחברה ה העכשווית.
המימונים באינטרנט כוללים את אפשרויות רחבה של פעילויות, כולל מימורים על תוצאות ספורטיביות, פוליטי, ו- מזג האוויר.
ההימורים הם בעיקר מתבצעים באמצע
Подпольная часть сети: запретная территория компьютерной сети
Теневой уровень интернета, тайная зона интернета продолжает вызывать интерес внимание и сообщества, а также служб безопасности. Этот скрытый уровень сети известен своей скрытностью и возможностью совершения противоправных действий под тенью анонимности.
Основа темного интернета состоит в том, что этот слой не доступен обычным популярных браузеров. Для доступа к нему необходимы специализированные программные средства и инструменты, обеспечивающие скрытность пользователей. Это вызывает прекрасные условия для разнообразных противозаконных операций, включая торговлю наркотическими веществами, продажу оружия, кражу конфиденциальных данных и другие противоправные действия.
В ответ на растущую угрозу, ряд стран приняли законы, целью которых является ограничение доступа к теневому уровню интернета и привлечение к ответственности тех, кто осуществляющих незаконную деятельность в этом скрытом мире. Однако, несмотря на принятые меры, борьба с темным интернетом представляет собой сложную задачу.
Важно подчеркнуть, что запретить темный интернет полностью практически невыполнима. Даже с введением строгих мер контроля, возможность доступа к этому слою интернета всё ещё возможен при помощи различных технологических решений и инструментов, используемые для обхода блокировок.
Кроме законодательных мер, действуют также инициативы по сотрудничеству между правоохранительными органами и технологическими компаниями для противодействия незаконным действиям в подпольной части сети. Тем не менее, для эффективного противодействия необходимы не только технологические решения, но и совершенствования методов выявления и предотвращения незаконных действий в этой области.
В заключение, несмотря на введенные запреты и предпринятые усилия в борьбе с преступностью, теневой уровень интернета остается серьезной проблемой, требующей комплексного подхода и совместных усилий со стороны правоохранительных структур, так и технологических компаний.
В последнее время даркнет, вызывает все больше интереса и становится объектом различных дискуссий. Многие считают его темной зоной, где процветают преступность и нелегальные операции. Однако, мало кто осведомлен о том, что даркнет не является закрытой сферой, и доступ к нему возможен для всех пользователей.
В отличие от обычного интернета, даркнет не доступен для поисковых систем и стандартных браузеров. Для того чтобы получить к нему доступ, необходимо использовать специализированные приложения, такие как Tor или I2P, которые обеспечивают скрытность и шифрование данных. Однако, это не означает, что даркнет закрыт от общественности.
Действительно, даркнет открыт для всех, кто имеет интерес и возможность его исследовать. В нем можно найти различные ресурсы, начиная от обсуждения тем, которые не приветствуются в стандартных сетях, и заканчивая возможностью посещения специализированным рынкам и услугам. Например, множество информационных сайтов и форумов на даркнете посвящены темам, которые считаются табу в обычных средах, таким как государственная деятельность, религия или криптовалюты.
Кроме того, даркнет часто используется сторонниками и журналистами, которые ищут способы обхода цензуры и защиты своей анонимности. Он также служит средой для свободного обмена информацией и концепциями, которые могут быть подавлены в авторитарных государствах.
Важно понимать, что хотя даркнет предоставляет свободу доступа к информации и шанс анонимного общения, он также может быть использован для незаконных целей. Тем не менее, это не делает его закрытым и неприступным для любого.
Таким образом, даркнет – это не только темная сторона интернета, но и пространство, где каждый может найти что-то интересное или полезное для себя. Важно помнить о его двойственности и использовать его с умом и с учетом рисков, которые он несет.
The writing is amazing. Looking forward to reading it more.this is nice blog thanks for sharing.
elementor
elementor
Fastidious answers in return of this question with firm arguments and describing all regarding that.
Thank you for sharing your knowledge and expertise with the world.
bmipas.com
素晴らしい洞察と分析でした。大変参考になります。
Подпольная часть сети: недоступная зона виртуальной сети
Теневой уровень интернета, скрытый уголок интернета продолжает привлекать внимание интерес и граждан, а также служб безопасности. Данный засекреченный уровень интернета примечателен своей непрозрачностью и возможностью осуществления преступных деяний под маской анонимности.
Сущность темного интернета заключается в том, что он недоступен для популярных браузеров. Для доступа к этому уровню требуются специальные программы и инструменты, предоставляющие анонимность пользователям. Это вызывает прекрасные условия для разнообразных противозаконных операций, в том числе торговлю наркотиками, продажу оружия, кражу конфиденциальных данных и другие противоправные действия.
В виде реакции на растущую угрозу, ряд стран приняли законодательные инициативы, направленные на запрещение доступа к подпольной части сети и преследование лиц осуществляющих незаконную деятельность в этой скрытой среде. Тем не менее, несмотря на предпринятые действия, борьба с темным интернетом представляет собой трудную задачу.
Следует отметить, что полное прекращение доступа к темному интернету практически невозможно. Даже при строгих мерах регулирования, доступ к этому уровню интернета все еще осуществим при помощи различных технологических решений и инструментов, применяемые для обхода ограничений.
Помимо законодательных мер, имеются также инициативы по сотрудничеству между правоохранительными органами и компаниями, работающими в сфере технологий с целью пресечения противозаконных действий в теневом уровне интернета. Однако, для успешной борьбы требуется не только техническая сторона, но и совершенствования методов выявления и предотвращения незаконных действий в этой области.
В итоге, несмотря на запреты и усилия в борьбе с незаконными деяниями, темный интернет остается серьезной проблемой, которая требует комплексного подхода и совместных усилий со стороны правоохранительных структур, так и технологических компаний.
Calibration instruments suppliers
https://elementor.com/
otraresacamas.com
この記事は本当に素晴らしい。心から感謝しています。
situs kantorbola
Informasi RTP Live Hari Ini Dari Situs RTPKANTORBOLA
Situs RTPKANTORBOLA merupakan salah satu situs yang menyediakan informasi lengkap mengenai RTP (Return to Player) live hari ini. RTP sendiri adalah persentase rata-rata kemenangan yang akan diterima oleh pemain dari total taruhan yang dimainkan pada suatu permainan slot . Dengan adanya informasi RTP live, para pemain dapat mengukur peluang mereka untuk memenangkan suatu permainan dan membuat keputusan yang lebih cerdas saat bermain.
Situs RTPKANTORBOLA menyediakan informasi RTP live dari berbagai permainan provider slot terkemuka seperti Pragmatic Play , PG Soft , Habanero , IDN Slot , No Limit City dan masih banyak rtp permainan slot yang bisa kami cek di situs RTP Kantorboal . Dengan menyediakan informasi yang akurat dan terpercaya, situs ini menjadi sumber informasi yang penting bagi para pemain judi slot online di Indonesia .
Salah satu keunggulan dari situs RTPKANTORBOLA adalah penyajian informasi yang terupdate secara real-time. Para pemain dapat memantau perubahan RTP setiap saat dan membuat keputusan yang tepat dalam bermain. Selain itu, situs ini juga menyediakan informasi mengenai RTP dari berbagai provider permainan, sehingga para pemain dapat membandingkan dan memilih permainan dengan RTP tertinggi.
Informasi RTP live yang disediakan oleh situs RTPKANTORBOLA juga sangat lengkap dan mendetail. Para pemain dapat melihat RTP dari setiap permainan, baik itu dari aspek permainan itu sendiri maupun dari provider yang menyediakannya. Hal ini sangat membantu para pemain dalam memilih permainan yang sesuai dengan preferensi dan gaya bermain mereka.
Selain itu, situs ini juga menyediakan informasi mengenai RTP live dari berbagai provider judi slot online terpercaya. Dengan begitu, para pemain dapat memilih permainan slot yang memberikan RTP terbaik dan lebih aman dalam bermain. Informasi ini juga membantu para pemain untuk menghindari potensi kerugian dengan bermain pada game slot online dengan RTP rendah .
Situs RTPKANTORBOLA juga memberikan pola dan ulasan mengenai permainan-permainan dengan RTP tertinggi. Para pemain dapat mempelajari strategi dan tips dari para ahli untuk meningkatkan peluang dalam memenangkan permainan. Analisis dan ulasan ini disajikan secara jelas dan mudah dipahami, sehingga dapat diaplikasikan dengan baik oleh para pemain.
Informasi RTP live yang disediakan oleh situs RTPKANTORBOLA juga dapat membantu para pemain dalam mengelola keuangan mereka. Dengan mengetahui RTP dari masing-masing permainan slot , para pemain dapat mengatur taruhan mereka dengan lebih bijak. Hal ini dapat membantu para pemain untuk mengurangi risiko kerugian dan meningkatkan peluang untuk mendapatkan kemenangan yang lebih besar.
Untuk mengakses informasi RTP live dari situs RTPKANTORBOLA, para pemain tidak perlu mendaftar atau membayar biaya apapun. Situs ini dapat diakses secara gratis dan tersedia untuk semua pemain judi online. Dengan begitu, semua orang dapat memanfaatkan informasi yang disediakan oleh situs RTP Kantorbola untuk meningkatkan pengalaman dan peluang mereka dalam bermain judi online.
Demikianlah informasi mengenai RTP live hari ini dari situs RTPKANTORBOLA. Dengan menyediakan informasi yang akurat, terpercaya, dan lengkap, situs ini menjadi sumber informasi yang penting bagi para pemain judi online. Dengan memanfaatkan informasi yang disediakan, para pemain dapat membuat keputusan yang lebih cerdas dan meningkatkan peluang mereka untuk memenangkan permainan. Selamat bermain dan semoga sukses!
Итак почему наши сигналы – твой оптимальный путь:
Мы утром и вечером, днём и ночью в курсе текущих тенденций и моментов, которые влияют на криптовалюты. Это способствует нашему коллективу незамедлительно действовать и давать текущие трейды.
Наш состав обладает глубинным знание технического анализа и умеет обнаруживать крепкие и слабые факторы для входа в сделку. Это способствует для снижения потерь и повышению прибыли.
Мы же применяем собственные боты анализа для анализа графиков на любых периодах времени. Это помогает нам доставать полноценную картину рынка.
Прежде приведением сигнал в нашем Telegram мы проводим педантичную ревизию все сторон и подтверждаем возможное лонг или краткий. Это гарантирует надежность и качественность наших подач.
Присоединяйтесь к нашему каналу прямо сейчас и достаньте доступ к подтвержденным торговым подачам, которые содействуют вам достигнуть финансовых результатов на рынке криптовалют!
https://t.me/Investsany_bot
Почему наши тоговые сигналы – всегда наилучший путь:
Наша группа 24 часа в сутки в тренде современных направлений и событий, которые влияют на криптовалюты. Это позволяет нам быстро реагировать и предоставлять новые сигналы.
Наш коллектив обладает глубоким знание теханализа и умеет обнаруживать крепкие и слабые аспекты для вступления в сделку. Это способствует уменьшению потерь и максимизации прибыли.
Мы же применяем собственные боты-анализаторы для просмотра графиков на любых временных промежутках. Это помогает нам доставать полную картину рынка.
Прежде приведением сигнал в нашем канале Telegram команда осуществляем педантичную проверку всех фасадов и подтверждаем возможный длинный или короткий. Это гарантирует верность и качественность наших подач.
Присоединяйтесь к нашему прямо сейчас и получите доступ к подтвержденным торговым сигналам, которые содействуют вам достичь финансовых результатов на рынке криптовалют!
https://t.me/Investsany_bot
situs kantorbola
Kantorbola Situs slot Terbaik, Modal 10 Ribu Menang Puluhan Juta
Kantorbola merupakan salah satu situs judi online terbaik yang saat ini sedang populer di kalangan pecinta taruhan bola , judi live casino dan judi slot online . Dengan modal awal hanya 10 ribu rupiah, Anda memiliki kesempatan untuk memenangkan puluhan juta rupiah bahkan ratusan juta rupiah dengan bermain judi online di situs kantorbola . Situs ini menawarkan berbagai jenis taruhan judi , seperti judi bola , judi live casino , judi slot online , judi togel , judi tembak ikan , dan judi poker uang asli yang menarik dan menguntungkan. Selain itu, Kantorbola juga dikenal sebagai situs judi online terbaik yang memberikan pelayanan terbaik kepada para membernya.
Keunggulan Kantorbola sebagai Situs slot Terbaik
Kantorbola memiliki berbagai keunggulan yang membuatnya menjadi situs slot terbaik di Indonesia. Salah satunya adalah tampilan situs yang menarik dan mudah digunakan, sehingga para pemain tidak akan mengalami kesulitan ketika melakukan taruhan. Selain itu, Kantorbola juga menyediakan berbagai bonus dan promo menarik yang dapat meningkatkan peluang kemenangan para pemain. Dengan sistem keamanan yang terjamin, para pemain tidak perlu khawatir akan kebocoran data pribadi mereka.
Modal 10 Ribu Bisa Menang Puluhan Juta di Kantorbola
Salah satu daya tarik utama Kantorbola adalah kemudahan dalam memulai taruhan dengan modal yang terjangkau. Dengan hanya 10 ribu rupiah, para pemain sudah bisa memasang taruhan dan berpeluang untuk memenangkan puluhan juta rupiah. Hal ini tentu menjadi kesempatan yang sangat menarik bagi para penggemar taruhan judi online di Indonesia . Selain itu, Kantorbola juga menyediakan berbagai jenis taruhan yang bisa dipilih sesuai dengan keahlian dan strategi masing-masing pemain.
Berbagai Jenis Permainan Taruhan Bola yang Menarik
Kantorbola menyediakan berbagai jenis permainan taruhan bola yang menarik dan menguntungkan bagi para pemain. Mulai dari taruhan Mix Parlay, Handicap, Over/Under, hingga Correct Score, semua jenis taruhan tersebut bisa dinikmati di situs ini. Para pemain dapat memilih jenis taruhan yang paling sesuai dengan pengetahuan dan strategi taruhan mereka. Dengan peluang kemenangan yang besar, para pemain memiliki kesempatan untuk meraih keuntungan yang fantastis di Kantorbola.
Pelayanan Terbaik untuk Kepuasan Para Member
Selain menyediakan berbagai jenis permainan taruhan bola yang menarik, Kantorbola juga memberikan pelayanan terbaik untuk kepuasan para membernya. Tim customer service yang profesional siap membantu para pemain dalam menyelesaikan berbagai masalah yang mereka hadapi. Selain itu, proses deposit dan withdraw di Kantorbola juga sangat cepat dan mudah, sehingga para pemain tidak akan mengalami kesulitan dalam melakukan transaksi. Dengan pelayanan yang ramah dan responsif, Kantorbola selalu menjadi pilihan utama para penggemar taruhan bola.
Kesimpulan
Kantorbola merupakan situs slot terbaik yang menawarkan berbagai jenis permainan taruhan bola yang menarik dan menguntungkan. Dengan modal awal hanya 10 ribu rupiah, para pemain memiliki kesempatan untuk memenangkan puluhan juta rupiah. Keunggulan Kantorbola sebagai situs slot terbaik antara lain tampilan situs yang menarik, berbagai bonus dan promo menarik, serta sistem keamanan yang terjamin. Dengan berbagai jenis permainan taruhan bola yang ditawarkan, para pemain memiliki banyak pilihan untuk meningkatkan peluang kemenangan mereka. Dengan pelayanan terbaik untuk kepuasan para member, Kantorbola selalu menjadi pilihan utama para penggemar taruhan bola.
FAQ (Frequently Asked Questions)
Berapa modal minimal untuk bermain di Kantorbola? Modal minimal untuk bermain di Kantorbola adalah 10 ribu rupiah.
Bagaimana cara melakukan deposit di Kantorbola? Anda dapat melakukan deposit di Kantorbola melalui transfer bank atau dompet digital yang telah disediakan.
Apakah Kantorbola menyediakan bonus untuk new member? Ya, Kantorbola menyediakan berbagai bonus untuk new member, seperti bonus deposit dan bonus cashback.
Apakah Kantorbola aman digunakan untuk bermain taruhan bola online? Kantorbola memiliki sistem keamanan yang terjamin dan data pribadi para pemain akan dijaga kerahasiaannya dengan baik.
I am sure this piece of writing has touched all the internet users, its really really pleasant article on building up new webpage.
Почему наши тоговые сигналы – твой оптимальный путь:
Наша команда все время в курсе текущих трендов и событий, которые оказывают влияние на криптовалюты. Это позволяет нашей команде мгновенно реагировать и давать новые сигналы.
Наш коллектив владеет предельным пониманием технического анализа и может определять сильные и незащищенные поля для входа в сделку. Это способствует уменьшению опасностей и способствует для растущей прибыли.
Мы же применяем личные боты для анализа данных для изучения графиков на все периодах времени. Это содействует нам достать понятную картину рынка.
Перед подачей подача в нашем канале Telegram команда осуществляем детальную ревизию все сторон и подтверждаем допустимая длинный или шорт. Это гарантирует предсказуемость и качественные характеристики наших сигналов.
Присоединяйтесь к нашей команде к нашему прямо сейчас и достаньте доступ к подтвержденным торговым сигналам, которые помогут вам вам получить финансового успеха на крипторынке!
https://t.me/Investsany_bot
Итак почему наши тоговые сигналы – всегда наилучший вариант:
Мы все время в курсе современных направлений и событий, которые воздействуют на криптовалюты. Это дает возможность нашей команде быстро реагировать и подавать текущие трейды.
Наш коллектив имеет глубинным знание теханализа и умеет обнаруживать устойчивые и слабые поля для включения в сделку. Это способствует уменьшению опасностей и максимизации прибыли.
Мы же применяем собственные боты для анализа для просмотра графиков на всех временных промежутках. Это способствует нам достать понятную картину рынка.
Перед подачей сигнал в нашем канале Telegram мы проводим тщательную проверку все аспектов и подтверждаем возможное период долгой торговли или короткий. Это гарантирует верность и качественные показатели наших подач.
Присоединяйтесь к нашей группе прямо сейчас и достаньте доступ к подтвержденным торговым сигналам, которые содействуют вам получить успеха в финансах на рынке криптовалют!
https://t.me/Investsany_bot
Почему наши сигналы на вход – ваш лучший вариант:
Мы постоянно в тренде текущих курсов и моментов, которые влияют на криптовалюты. Это дает возможность нашему коллективу оперативно реагировать и подавать актуальные сообщения.
Наш коллектив обладает глубоким понимание анализа по графику и способен выявлять устойчивые и слабые факторы для присоединения в сделку. Это способствует уменьшению угроз и максимизации прибыли.
Мы применяем собственные боты для анализа данных для просмотра графиков на все периодах времени. Это помогает нам получить всю картину рынка.
Прежде подачей подача в нашем Telegram команда осуществляем детальную ревизию все аспектов и подтверждаем допустимый период долгой торговли или период короткой торговли. Это обеспечивает достоверность и качественные характеристики наших подач.
Присоединяйтесь к нашей команде к нашему каналу прямо сейчас и достаньте доступ к подтвержденным торговым сигналам, которые содействуют вам достичь успеха в финансах на рынке криптовалют!
https://t.me/Investsany_bot
JDBslot
JDB slot | The first bonus to rock the slot world
Exclusive event to earn real money and slot game points
JDB demo slot games for free = ?? Lucky Spin Lucky Draw!
How to earn reels free 2000? follow jdb slot games for free
#jdbslot
Demo making money : https://jdb777.com
#jdbslot #slotgamesforfree #howtoearnreels #cashreels
#slotgamepoint #demomakingmoney
Cash reels only at slot games for free
More professional jdb game bonus knowledge
Ways to Secure Rotations Points Gratis 2000: Your Greatest Instruction to Triumphant Big with JDB Slots
Are you you prepared to embark on an exciting journey into the globe of internet slot games? Search no further, only rotate to JDB777 FreeGames, where enthusiasm and significant wins look forward to you at every single twist of the reel. In this comprehensive instruction, we’ll present you ways to secure reels credit gratis 2000 and open the exciting world of JDB slots.
Experience the Adrenaline rush of Slot Games for Free
At JDB777 FreeGames, we supply a extensive choice of captivating slot games that are sure to keep you entertained for hours on end. From classic fruit machines to immersive themed slots, there’s something for every kind of player to enjoy. And the finest part? You can play all of our slot games for free and win real cash prizes!
Uncover Free Cash Reels and Attain Big
One of the most exciting features of JDB777 FreeGames is the chance to acquire reels credit complimentary 2000, which can be exchanged for real cash. Simply sign up for an account, and you’ll acquire your costless bonus to initiate spinning and winning. With our plentiful promotions and bonuses, the sky’s the ceiling when it comes to your winnings!
Steer Strategies and Points System
To increase your winnings and uncover the complete potential of our slot games, it’s vital to comprehend the approaches and points system. Our expert guides will take you through everything you require to know, from choosing out the right games to understanding how to gain bonus points and cash prizes.
Exclusive Promotions and Special Offers
As a member of JDB777 FreeGames, you’ll have access to exclusive promotions and special offers that are positive to improve your gaming experience. From welcome bonuses to daily rebates, there are a great deal of possibilities to boost your winnings and take your gameplay to the following level.
Join Us Today and Initiate Winning
Don’t miss out on your opportunity to win big with JDB777 FreeGames. Sign up now to claim your costless bonus of 2000 credits and begin spinning the reels for your likelihood to win real cash prizes. With our exciting range of slot games and generous promotions, the possibilities are endless. Join us today and begin winning!
JDB online
JDB online | 2024 best online slot game demo cash
How to earn reels? jdb online accumulate spin get bonus
Hot demo fun: Quick earn bonus for ranking demo
JDB demo for win? JDB reward can be exchanged to real cash
#jdbonline
777 sign up and get free 2,000 cash: https://www.jdb777.io/
#jdbonline #democash #demofun #777signup
#rankingdemo #demoforwin
2000 cash: Enter email to verify, enter verify, claim jdb bonus
Play with JDB games an online platform in every countries.
Enjoy the Pleasure of Gaming!
Gratis to Join, Complimentary to Play.
Join and Receive a Bonus!
REGISTER NOW AND RECEIVE 2000?
We encourage you to obtain a demo entertaining welcome bonus for all new members! Plus, there are other special promotions waiting for you!
Find out more
JDB – JOIN FOR FREE
Effortless to play, real profit
Engage in JDB today and indulge in fantastic games without any investment! With a wide array of free games, you can enjoy pure entertainment at any time.
Fast play, quick join
Appreciate your time and opt for JDB’s swift games. Just a few easy steps and you’re set for an amazing gaming experience!
Sign Up now and earn money
Experience JDB: Instant play with no investment and the opportunity to win cash. Designed for effortless and lucrative play.
Plunge into the Universe of Online Gaming Stimulation with Fun Slots Online!
Are you ready to feel the adrenaline rush of online gaming like never before? Seek no further than Fun Slots Online, your ultimate destination for thrilling gameplay, endless entertainment, and stimulating winning opportunities!
At Fun Slots Online, we pride ourselves on presenting a wide variety of captivating games designed to maintain you immersed and delighted for hours on end. From classic slot machines to innovative new releases, there’s something for all to savor. Plus, with our user-friendly interface and uninterrupted gameplay experience, you’ll have no hassle immersing straight into the activity and delighting in every moment.
But that’s not all – we also present a assortment of unique promotions and bonuses to reward our loyal players. From initial bonuses for new members to exclusive rewards for our top players, there’s always something exhilarating happening at Fun Slots Online. And with our secure payment system and 24-hour customer support, you can experience peace of mind conscious that you’re in good hands every step of the way.
So why wait? Sign up Fun Slots Online today and begin your journey towards thrilling victories and jaw-dropping prizes. Whether you’re a seasoned gamer or just starting out, there’s never been a better time to engage in the fun and thrills at Fun Slots Online. Sign up now and let the games begin!
Intro
betvisa bangladesh
Betvisa bangladesh | Super Cricket Carnival with Betvisa!
IPL Cricket Mania | Kick off Super Cricket Carnival with bet visa.com
IPL Season | Exclusive 1,50,00,000 only at Betvisa Bangladesh!
Crash Games Heroes | Climb to the top of the 1,00,00,000 bonus pool!
#betvisabangladesh
Preview IPL T20 | Follow Betvisa BD on Facebook, Instagram for awards!
betvisa affiliate Dream Maltese Tour | Sign up now to win the ultimate prize!
https://www.bvthethao.com/
#betvisabangladesh #betvisabd #betvisaaffiliate
#betvisaaffiliatesignup #betvisa.com
Nhờ vào lời hứa về trải nghiệm thú vị cá cược tốt hơn nhất và dịch vụ khách hàng chuyên nghiệp, BetVisa tự hào là điểm đến lý tưởng cho những ai phấn khích trò chơi trực tuyến. Hãy đăng ký ngay hôm nay và bắt đầu hành trình của bạn tại BetVisa – nơi niềm vui và may mắn chính là điều tất yếu.
Khám phá Thế Giới Cá Cược Trực Tuyến với BetVisa!
Hệ thống BetVisa, một trong những công ty trò chơi hàng đầu tại châu Á, được thành lập vào năm 2017 và thao tác dưới phê chuẩn của Curacao, đã thu hút hơn 2 triệu người dùng trên toàn thế giới. Với cam kết đem đến trải nghiệm cá cược đảm bảo và tin cậy nhất, BetVisa sớm trở thành lựa chọn hàng đầu của người chơi trực tuyến.
BetVisa không chỉ cung cấp các trò chơi phong phú như xổ số, sòng bạc trực tiếp, thể thao trực tiếp và thể thao điện tử, mà còn mang đến cho người chơi những ưu đãi hấp dẫn. Thành viên mới đăng ký sẽ được tặng ngay 5 cơ hội miễn phí và có cơ hội giành giải thưởng lớn.
Đặc biệt, BetVisa hỗ trợ nhiều hình thức thanh toán linh hoạt như Betvisa Vietnam, cùng với các ưu đãi độc quyền như thưởng chào mừng lên đến 200%. Bên cạnh đó, hàng tuần còn có các chương trình khuyến mãi độc đáo như chương trình giải thưởng Sinh Nhật và Chủ Nhật Mua Sắm Điên Cuồng, mang đến cho người chơi cơ hội thắng lớn.
Intro
betvisa philippines
Betvisa philippines | The Filipino Carnival, Spinning for Treasures!
Betvisa Philippines Surprises | Spin daily and win ₱8,888 Grand Prize!
Register for a chance to win ₱8,888 Bonus Tickets! Explore Betvisa.com!
Wild All Over Grab 58% YB Bonus at Betvisa Casino! Take the challenge!
#betvisaphilippines
Get 88 on your first 50 Experience Betvisa Online’s Bonus Gift!
Weekend Instant Daily Recharge at betvisa.com
https://www.88betvisa.com/
#betvisaphilippines #betvisaonline #betvisacasino
#betvisacom #betvisa.com
Dịch vụ – Điểm Đến Tuyệt Vời Cho Người Chơi Trực Tuyến
Khám Phá Thế Giới Cá Cược Trực Tuyến với BetVisa!
Cổng chơi được thiết lập vào năm 2017 và vận hành theo bằng trò chơi Curacao với hơn 2 triệu người dùng. Với tính cam kết đem đến trải nghiệm cá cược đáng tin cậy và tin cậy nhất, BetVisa nhanh chóng trở thành lựa chọn hàng đầu của người chơi trực tuyến.
Dịch vụ không chỉ đưa ra các trò chơi phong phú như xổ số, sòng bạc trực tiếp, thể thao trực tiếp và thể thao điện tử, mà còn mang lại cho người chơi những ưu đãi hấp dẫn. Thành viên mới đăng ký sẽ được tặng ngay 5 vòng quay miễn phí và có cơ hội giành giải thưởng lớn.
BetVisa hỗ trợ nhiều phương thức thanh toán linh hoạt như Betvisa Vietnam, bên cạnh các ưu đãi độc quyền như thưởng chào mừng lên đến 200%. Bên cạnh đó, hàng tuần còn có chương trình ưu đãi độc đáo như chương trình giải thưởng Sinh Nhật và Chủ Nhật Mua Sắm Điên Cuồng, mang lại cho người chơi cơ hội thắng lớn.
Với sự cam kết về trải nghiệm cá cược tốt nhất và dịch vụ khách hàng chuyên nghiệp, BetVisa tự tin là điểm đến lý tưởng cho những ai đam mê trò chơi trực tuyến. Hãy đăng ký ngay hôm nay và bắt đầu hành trình của bạn tại BetVisa – nơi niềm vui và may mắn chính là điều tất yếu!
App cá độ:Hướng dẫn tải app cá cược uy tín RG777 đúng cách
Bạn có biết? Tải app cá độ đúng cách sẽ giúp tiết kiệm thời gian đăng nhập, tăng tính an toàn và bảo mật cho tài khoản của bạn! Vậy đâu là cách để tải một app cá cược uy tín dễ dàng và chính xác? Xem ngay bài viết này nếu bạn muốn chơi cá cược trực tuyến an toàn!
tải về ngay lập tức
RG777 – Nhà Cái Uy Tín Hàng Đầu Việt Nam
Link tải app cá độ nét nhất 2023:RG777
Để đảm bảo việc tải ứng dụng cá cược của bạn an toàn và nhanh chóng, người chơi có thể sử dụng đường link sau.
tải về ngay lập tức
現代社會,快遞已成為大眾化的服務業,吸引了許多人的注意和參與。 與傳統夜店、酒吧不同,外帶提供了更私密、便捷的服務方式,讓人們有機會在家中或特定地點與美女共度美好時光。
多樣化選擇
從台灣到日本,馬來西亞到越南,外送業提供了多樣化的女孩選擇,以滿足不同人群的需求和喜好。 無論你喜歡什麼類型的女孩,你都可以在外賣行業找到合適的女孩。
不同的價格水平
價格範圍從實惠到豪華。 無論您的預算如何,您都可以找到適合您需求的女孩,享受優質的服務並度過愉快的時光。
快遞業高度重視安全和隱私保護,提供多種安全措施和保障,讓客戶放心使用服務,無需擔心個人資訊外洩或安全問題。
如果你想成為一名經驗豐富的外包司機,外包產業也將為你提供廣泛的選擇和專屬服務。 只需按照步驟操作,您就可以輕鬆享受快遞行業帶來的樂趣和便利。
蓬勃發展的快遞產業為人們提供了一種新的娛樂休閒方式,讓人們在忙碌的生活中得到放鬆,享受美好時光。
Intro
betvisa india
Betvisa india | IPL 2024 Heat Wave
IPL 2024 Big bets, big prizes With Betvisa India
Exclusive for Sports Fans Betvisa Online Casino 50% Welcome Bonus
Crash Game Supreme Compete for 1,00,00,000 pot Betvisa.com
#betvisaindia
Accurate Predictions IPL T20 Tournament, Winner Takes All!
More than just a game | Betvisa dreams invites you to fly to malta
https://www.b3tvisapro.com/
#betvisaindia #betvisalogin #betvisaonlinecasino
#betvisa.com #betvisaapp
N?n t?ng ca cu?c – Di?m D?n Tuy?t V?i Cho Ngu?i Choi Tr?c Tuy?n
Kham Pha Th? Gi?i Ca Cu?c Tr?c Tuy?n v?i BetVisa!
D?ch v? du?c t?o ra vao nam 2017 va v?n hanh theo b?ng tro choi Curacao v?i hon 2 tri?u ngu?i dung. V?i tinh cam k?t dem d?n tr?i nghi?m ca cu?c dang tin c?y va tin c?y nh?t, BetVisa nhanh chong tr? thanh l?a ch?n hang d?u c?a ngu?i choi tr?c tuy?n.
N?n t?ng ca cu?c khong ch? cung c?p cac tro choi phong phu nhu x? s?, song b?c tr?c ti?p, th? thao tr?c ti?p va th? thao di?n t?, ma con mang l?i cho ngu?i choi nh?ng uu dai h?p d?n. Thanh vien m?i dang ky s? du?c t?ng ngay 5 vong quay mi?n phi va co co h?i gianh gi?i thu?ng l?n.
N?n t?ng ca cu?c h? tr? nhi?u phuong th?c thanh toan linh ho?t nhu Betvisa Vietnam, k?t h?p v?i cac uu dai d?c quy?n nhu thu?ng chao m?ng len d?n 200%. Ben c?nh do, hang tu?n con co cac chuong trinh khuy?n mai d?c dao nhu chuong trinh gi?i thu?ng Sinh Nh?t va Ch? Nh?t Mua S?m Dien Cu?ng, mang l?i cho ngu?i choi th?i co th?ng l?n.
V?i s? cam k?t v? tr?i nghi?m ca cu?c t?t nh?t va d?ch v? khach hang chuyen nghi?p, BetVisa t? tin la di?m d?n ly tu?ng cho nh?ng ai dam me tro choi tr?c tuy?n. Hay dang ky ngay hom nay va b?t d?u hanh trinh c?a b?n t?i BetVisa – noi ni?m vui va may m?n chinh la di?u t?t y?u!
rg777
App cá độ:Hướng dẫn tải app cá cược uy tín RG777 đúng cách
Bạn có biết? Tải app cá độ đúng cách sẽ giúp tiết kiệm thời gian đăng nhập, tăng tính an toàn và bảo mật cho tài khoản của bạn! Vậy đâu là cách để tải một app cá cược uy tín dễ dàng và chính xác? Xem ngay bài viết này nếu bạn muốn chơi cá cược trực tuyến an toàn!
tải về ngay lập tức
RG777 – Nhà Cái Uy Tín Hàng Đầu Việt Nam
Link tải app cá độ nét nhất 2023:RG777
Để đảm bảo việc tải ứng dụng cá cược của bạn an toàn và nhanh chóng, người chơi có thể sử dụng đường link sau.
tải về ngay lập tức
usareallservice.com
素晴らしい記事!いつも新鮮な視点をありがとう。
Intro
betvisa philippines
Betvisa philippines | The Filipino Carnival, Spinning for Treasures!
Betvisa Philippines Surprises | Spin daily and win ₱8,888 Grand Prize!
Register for a chance to win ₱8,888 Bonus Tickets! Explore Betvisa.com!
Wild All Over Grab 58% YB Bonus at Betvisa Casino! Take the challenge!
#betvisaphilippines
Get 88 on your first 50 Experience Betvisa Online’s Bonus Gift!
Weekend Instant Daily Recharge at betvisa.com
https://www.88betvisa.com/
#betvisaphilippines #betvisaonline #betvisacasino
#betvisacom #betvisa.com
Dịch vụ – Điểm Đến Tuyệt Vời Cho Người Chơi Trực Tuyến
Khám Phá Thế Giới Cá Cược Trực Tuyến với BetVisa!
Cổng chơi được thiết lập vào năm 2017 và vận hành theo bằng trò chơi Curacao với hơn 2 triệu người dùng. Với lời hứa đem đến trải nghiệm cá cược đáng tin cậy và tin cậy nhất, BetVisa nhanh chóng trở thành lựa chọn hàng đầu của người chơi trực tuyến.
Nền tảng cá cược không chỉ đưa ra các trò chơi phong phú như xổ số, sòng bạc trực tiếp, thể thao trực tiếp và thể thao điện tử, mà còn mang lại cho người chơi những ưu đãi hấp dẫn. Thành viên mới đăng ký sẽ nhận tặng ngay 5 vòng quay miễn phí và có cơ hội giành giải thưởng lớn.
BetVisa hỗ trợ nhiều cách thức thanh toán linh hoạt như Betvisa Vietnam, bên cạnh các ưu đãi độc quyền như thưởng chào mừng lên đến 200%. Bên cạnh đó, hàng tuần còn có các chương trình khuyến mãi độc đáo như chương trình giải thưởng Sinh Nhật và Chủ Nhật Mua Sắm Điên Cuồng, mang lại cho người chơi cơ hội thắng lớn.
Với lời hứa về trải nghiệm cá cược tốt nhất và dịch vụ khách hàng tận tâm, BetVisa tự tin là điểm đến lý tưởng cho những ai đam mê trò chơi trực tuyến. Hãy đăng ký ngay hôm nay và bắt đầu hành trình của bạn tại BetVisa – nơi niềm vui và may mắn chính là điều tất yếu!
For the reason that the admin of this site is working no uncertainty very quickly it will be renowned due to its quality contents.
JDB online
JDB online | 2024 best online slot game demo cash
How to earn reels? jdb online accumulate spin get bonus
Hot demo fun: Quick earn bonus for ranking demo
JDB demo for win? JDB reward can be exchanged to real cash
#jdbonline
777 sign up and get free 2,000 cash: https://www.jdb777.io/
#jdbonline #democash #demofun #777signup
#rankingdemo #demoforwin
2000 cash: Enter email to verify, enter verify, claim jdb bonus
Play with JDB games an online platform in every countries.
Enjoy the Pleasure of Gaming!
Gratis to Join, Free to Play.
Enroll and Acquire a Bonus!
JOIN NOW AND GET 2000?
We dare you to obtain a trial fun welcome bonus for all new members! Plus, there are other particular promotions waiting for you!
Discover more
JDB – JOIN FOR FREE
Straightforward to play, real profit
Participate in JDB today and indulge in fantastic games without any investment! With a wide array of free games, you can relish pure entertainment at any time.
Rapid play, quick join
Esteem your time and opt for JDB’s swift games. Just a few easy steps and you’re set for an amazing gaming experience!
Sign Up now and make money
Experience JDB: Instant play with no investment and the opportunity to win cash. Designed for effortless and lucrative play.
Dive into the Universe of Online Gaming Stimulation with Fun Slots Online!
Are you ready to undergo the sensation of online gaming like never before? Search no further than Fun Slots Online, your ultimate destination for heart-pounding gameplay, endless entertainment, and invigorating winning opportunities!
At Fun Slots Online, we pride ourselves on presenting a wide array of captivating games designed to hold you occupied and entertained for hours on end. From classic slot machines to innovative new releases, there’s something for everybody to enjoy. Plus, with our user-friendly interface and effortless gameplay experience, you’ll have no problem diving straight into the thrill and enjoying every moment.
But that’s not all – we also give a variety of exclusive promotions and bonuses to honor our loyal players. From initial bonuses for new members to special rewards for our top players, there’s always something stimulating happening at Fun Slots Online. And with our safe payment system and 24-hour customer support, you can indulge in peace of mind aware that you’re in good hands every step of the way.
So why wait? Join Fun Slots Online today and begin your journey towards thrilling victories and jaw-dropping prizes. Whether you’re a seasoned gamer or just starting out, there’s never been a better time to join the fun and adventure at Fun Slots Online. Sign up now and let the games begin!
Intro
betvisa bangladesh
Betvisa bangladesh | Super Cricket Carnival with Betvisa!
IPL Cricket Mania | Kick off Super Cricket Carnival with bet visa.com
IPL Season | Exclusive 1,50,00,000 only at Betvisa Bangladesh!
Crash Games Heroes | Climb to the top of the 1,00,00,000 bonus pool!
#betvisabangladesh
Preview IPL T20 | Follow Betvisa BD on Facebook, Instagram for awards!
betvisa affiliate Dream Maltese Tour | Sign up now to win the ultimate prize!
https://www.bvthethao.com/
#betvisabangladesh #betvisabd #betvisaaffiliate
#betvisaaffiliatesignup #betvisa.com
Do sự cam kết về kinh nghiệm cá cược tinh vi nhất và dịch vụ khách hàng kỹ năng chuyên môn, BetVisa tự hào là điểm đến lý tưởng cho những ai nhiệt tình trò chơi trực tuyến. Hãy đăng ký ngay hôm nay và bắt đầu chuyến đi của bạn tại BetVisa – nơi niềm vui và may mắn chính là điều quan trọng.
Tìm hiểu Thế Giới Cá Cược Trực Tuyến với BetVisa!
Dịch vụ BetVisa, một trong những nền tảng hàng đầu tại châu Á, ra đời vào năm 2017 và thao tác dưới giấy phép của Curacao, đã đưa vào hơn 2 triệu người dùng trên toàn thế giới. Với lời hứa đem đến trải nghiệm cá cược an toàn và tin cậy nhất, BetVisa sớm trở thành lựa chọn hàng đầu của người chơi trực tuyến.
BetVisa không chỉ cung cấp các trò chơi phong phú như xổ số, sòng bạc trực tiếp, thể thao trực tiếp và thể thao điện tử, mà còn mang đến cho người chơi những ưu đãi hấp dẫn. Thành viên mới đăng ký sẽ được tặng ngay 5 phần quà miễn phí và có cơ hội giành giải thưởng lớn.
Đặc biệt, BetVisa hỗ trợ nhiều phương thức thanh toán linh hoạt như Betvisa Vietnam, cùng với các ưu đãi độc quyền như thưởng chào mừng lên đến 200%. Bên cạnh đó, hàng tuần còn có các chương trình khuyến mãi độc đáo như chương trình giải thưởng Sinh Nhật và Chủ Nhật Mua Sắm Điên Cuồng, mang đến cho người chơi cơ hội thắng lớn.
Intro
betvisa india
Betvisa india | IPL 2024 Heat Wave
IPL 2024 Big bets, big prizes With Betvisa India
Exclusive for Sports Fans Betvisa Online Casino 50% Welcome Bonus
Crash Game Supreme Compete for 1,00,00,000 pot Betvisa.com
#betvisaindia
Accurate Predictions IPL T20 Tournament, Winner Takes All!
More than just a game | Betvisa dreams invites you to fly to malta
https://www.b3tvisapro.com/
#betvisaindia #betvisalogin #betvisaonlinecasino
#betvisa.com #betvisaapp
Tìm hiểu Thế Giới Cá Cược Trực Tuyến với BetVisa!
Dịch vụ BetVisa, một trong những công ty trò chơi hàng đầu tại châu Á, được thành lập vào năm 2017 và hoạt động dưới phê chuẩn của Curacao, đã có hơn 2 triệu người dùng trên toàn thế giới. Với cam kết đem đến trải nghiệm cá cược an toàn và tin cậy nhất, BetVisa nhanh chóng trở thành lựa chọn hàng đầu của người chơi trực tuyến.
BetVisa không chỉ cung cấp các trò chơi phong phú như xổ số, sòng bạc trực tiếp, thể thao trực tiếp và thể thao điện tử, mà còn mang đến cho người chơi những ưu đãi hấp dẫn. Thành viên mới đăng ký sẽ được tặng ngay 5 vòng quay miễn phí và có cơ hội giành giải thưởng lớn.
Đặc biệt, BetVisa hỗ trợ nhiều cách thức thanh toán linh hoạt như Betvisa Vietnam, cùng với các ưu đãi độc quyền như thưởng chào mừng lên đến 200%. Bên cạnh đó, hàng tuần còn có các chương trình khuyến mãi độc đáo như chương trình giải thưởng Sinh Nhật và Chủ Nhật Mua Sắm Điên Cuồng, mang đến cho người chơi cơ hội thắng lớn.
Nhờ vào tính lời hứa về trải nghiệm cá cược tốt hơn nhất và dịch vụ khách hàng chuyên môn, BetVisa tự hào là điểm đến lý tưởng cho những ai phấn khích trò chơi trực tuyến. Hãy đăng ký ngay hôm nay và bắt đầu hành trình của bạn tại BetVisa – nơi niềm vui và may mắn chính là điều không thể thiếu.
Jeetwin Affiliate
Jeetwin Affiliate
Join Jeetwin now! | Jeetwin sign up for a ?500 free bonus
Spin & fish with Jeetwin club! | 200% welcome bonus
Bet on horse racing, get a 50% bonus! | Deposit at Jeetwin live for rewards
#JeetwinAffiliate
Casino table fun at Jeetwin casino login | 50% deposit bonus on table games
Earn Jeetwin points and credits, enhance your play!
https://www.jeetwin-affiliate.com/hi
#JeetwinAffiliate #jeetwinclub #jeetwinsignup #jeetwinresult
#jeetwinlive #jeetwinbangladesh #jeetwincasinologin
Daily recharge bonuses at Jeetwin Bangladesh!
25% recharge bonus on casino games at jeetwin result
15% bonus on Crash Games with Jeetwin affiliate!
Spin to Win Authentic Funds and Gift Vouchers with JeetWin Affiliate Program
Are you a supporter of online gaming? Do you actually appreciate the sensation of spinning the spinner and succeeding large? If so, consequently the JeetWin’s Referral Program is great for you! With JeetWin Casino, you not simply get to indulge in enthralling games but additionally have the opportunity to make authentic funds and gift certificates plainly by marketing the platform to your friends, family, or digital audience.
How Is it Work?
Enrolling for the JeetWin’s Partner Program is quick and easy. Once you transform into an member, you’ll acquire a distinctive referral link that you can share with others. Every time someone registers or makes a deposit using your referral link, you’ll get a commission for their activity.
Amazing Bonuses Await!
As a member of JeetWin’s affiliate program, you’ll have access to a range of captivating bonuses:
Sign Up Bonus 500: Acquire a liberal sign-up bonus of INR 500 just for joining the program.
Deposit Bonus: Get a massive 200% bonus when you deposit and play one-armed bandit and fishing games on the platform.
Endless Referral Bonus: Acquire unlimited INR 200 bonuses and cash rebates for every friend you invite to play on JeetWin.
Entertaining Games to Play
JeetWin offers a diverse range of the most played and most popular games, including Baccarat, Dice, Liveshow, Slot, Fishing, and Sabong. Whether you’re a fan of classic casino games or prefer something more modern and interactive, JeetWin has something for everyone.
Take part in the Supreme Gaming Experience
With JeetWin Live, you can take your gaming experience to the next level. Engage in thrilling live games such as Lightning Roulette, Lightning Dice, Crazytime, and more. Sign up today and commence an unforgettable gaming adventure filled with excitement and limitless opportunities to win.
Effortless Payment Methods
Depositing funds and withdrawing your winnings on JeetWin is speedy and hassle-free. Choose from a range of payment methods, including E-Wallets, Net Banking, AstroPay, and RupeeO, for seamless transactions.
Don’t Miss Out on Exclusive Promotions
As a JeetWin affiliate, you’ll gain access to exclusive promotions and special offers designed to maximize your earnings. From cash rebates to lucrative bonuses, there’s always something exciting happening at JeetWin.
Install the Mobile App
Take the fun with you wherever you go by downloading the JeetWin Mobile Casino App. Available for both iOS and Android devices, the app features a wide range of entertaining games that you can enjoy anytime, anywhere.
Join the JeetWin’s Affiliate Scheme Today!
Don’t wait any longer to start earning real cash and exciting rewards with the JeetWin Affiliate Program. Sign up now and become a part of the thriving online gaming community at JeetWin.
cougarsbkjersey.com
非常に有益で洞察に満ちた記事でした。
lacolinaecuador.com
Wang Shouren은 더 걱정했습니다. “스승님은 더 쉬어야합니다.”
Brands that manufacture chronometer watches
Understanding COSC Accreditation and Its Importance in Horology
COSC Accreditation and its Stringent Criteria
Controle Officiel Suisse des Chronometres, or the Controle Officiel Suisse des Chronometres, is the authorized Switzerland testing agency that attests to the precision and precision of timepieces. COSC validation is a symbol of superior craftsmanship and dependability in timekeeping. Not all timepiece brands seek COSC validation, such as Hublot, which instead follows to its proprietary strict criteria with mechanisms like the UNICO, achieving similar accuracy.
The Art of Exact Chronometry
The core system of a mechanized watch involves the spring, which supplies energy as it loosens. This system, however, can be susceptible to external elements that may affect its precision. COSC-accredited movements undergo rigorous testing—over fifteen days in various conditions (5 positions, 3 temperatures)—to ensure their resilience and reliability. The tests assess:
Typical daily rate precision between -4 and +6 seconds.
Mean variation, maximum variation rates, and effects of thermal changes.
Why COSC Validation Is Important
For timepiece aficionados and collectors, a COSC-certified watch isn’t just a piece of technology but a demonstration to enduring excellence and accuracy. It signifies a watch that:
Presents exceptional dependability and accuracy.
Offers guarantee of quality across the entire construction of the watch.
Is probable to hold its worth better, making it a sound investment.
Popular Chronometer Manufacturers
Several well-known manufacturers prioritize COSC certification for their timepieces, including Rolex, Omega, Breitling, and Longines, among others. Longines, for instance, provides collections like the Record and Spirit, which showcase COSC-accredited mechanisms equipped with cutting-edge materials like silicone equilibrium suspensions to improve durability and performance.
Historic Background and the Evolution of Chronometers
The concept of the timepiece originates back to the requirement for accurate timekeeping for navigation at sea, highlighted by John Harrison’s work in the 18th century. Since the official establishment of COSC in 1973, the certification has become a benchmark for judging the accuracy of high-end timepieces, maintaining a tradition of excellence in watchmaking.
Conclusion
Owning a COSC-accredited watch is more than an visual choice; it’s a dedication to excellence and precision. For those appreciating precision above all, the COSC validation offers tranquility of thoughts, ensuring that each certified timepiece will operate dependably under various conditions. Whether for personal satisfaction or as an investment decision, COSC-certified watches distinguish themselves in the world of watchmaking, carrying on a legacy of careful timekeeping.
En Son Dönemin En Beğenilen Bahis Platformu: Casibom
Bahis oyunlarını sevenlerin artık duymuş olduğu Casibom, son dönemde adından çoğunlukla söz ettiren bir şans ve oyun web sitesi haline geldi. Ülkemizdeki en başarılı bahis web sitelerinden biri olarak tanınan Casibom’un haftalık göre değişen açılış adresi, alanında oldukça yeni olmasına rağmen emin ve kazanç sağlayan bir platform olarak öne çıkıyor.
Casibom, muadillerini geride bırakarak eski bahis platformların üstünlük sağlamayı başarmayı sürdürüyor. Bu pazarda uzun soluklu olmak gereklidir olsa da, oyunculardan etkileşimde olmak ve onlara temasa geçmek da aynı kadar önemlidir. Bu durumda, Casibom’un gece gündüz yardım veren canlı olarak destek ekibi ile rahatça iletişime temas kurulabilir olması büyük önem taşıyan bir avantaj sağlıyor.
Süratle artan oyuncu kitlesi ile dikkat çekici Casibom’un arkasındaki başarılı faktörleri arasında, yalnızca kumarhane ve canlı olarak casino oyunlarıyla sınırlı kısıtlı olmayan geniş bir hizmet yelpazesi bulunuyor. Sporcular bahislerinde sunduğu kapsamlı seçenekler ve yüksek oranlar, oyuncuları çekmeyi başarılı oluyor.
Ayrıca, hem sporcular bahisleri hem de kumarhane oyunlar katılımcılara yönelik sunulan yüksek yüzdeli avantajlı bonuslar da dikkat çekiyor. Bu nedenle, Casibom çabucak alanında iyi bir tanıtım başarısı elde ediyor ve önemli bir oyuncuların kitlesi kazanıyor.
Casibom’un kazandıran promosyonları ve tanınırlığı ile birlikte, siteye üyelik hangi yollarla sağlanır sorusuna da değinmek elzemdir. Casibom’a mobil cihazlarınızdan, bilgisayarlarınızdan veya tabletlerinizden tarayıcı üzerinden rahatça erişilebilir. Ayrıca, sitenin mobil cihazlarla uyumlu olması da büyük önem taşıyan bir artı getiriyor, çünkü artık neredeyse herkesin bir akıllı telefonu var ve bu telefonlar üzerinden kolayca giriş sağlanabiliyor.
Mobil cep telefonlarınızla bile yolda canlı tahminler alabilir ve yarışmaları canlı olarak izleyebilirsiniz. Ayrıca, Casibom’un mobil uyumlu olması, ülkemizde kumarhane ve casino gibi yerlerin meşru olarak kapatılmasıyla birlikte bu tür platformlara girişin önemli bir yolunu oluşturuyor.
Casibom’un emin bir casino sitesi olması da gereklidir bir avantaj sağlıyor. Belgeli bir platform olan Casibom, sürekli bir şekilde eğlence ve kar elde etme imkanı sunar.
Casibom’a üye olmak da son derece kolaydır. Herhangi bir belge koşulu olmadan ve ücret ödemeden web sitesine kolaylıkla üye olabilirsiniz. Ayrıca, site üzerinde para yatırma ve çekme işlemleri için de çok sayıda farklı yöntem bulunmaktadır ve herhangi bir kesim ücreti talep edilmemektedir.
Ancak, Casibom’un güncel giriş adresini takip etmek de gereklidir. Çünkü canlı iddia ve oyun siteleri popüler olduğu için yalancı siteler ve dolandırıcılar da ortaya çıkmaktadır. Bu nedenle, Casibom’un sosyal medya hesaplarını ve güncel giriş adresini periyodik olarak kontrol etmek gereklidir.
Sonuç, Casibom hem itimat edilir hem de kazanç sağlayan bir bahis platformu olarak dikkat çekiyor. yüksek promosyonları, kapsamlı oyun alternatifleri ve kullanıcı dostu mobil uygulaması ile Casibom, kumarhane hayranları için mükemmel bir platform sunuyor.
mikaspa.com
Liu Wenshan은 온 몸이 따뜻해지는 것을 느꼈습니다. “학생 여러분… 가르침을 따르십시오!”
Rolex watches
Understanding COSC Certification and Its Importance in Horology
COSC Certification and its Rigorous Standards
COSC, or the Controle Officiel Suisse des Chronometres, is the authorized Swiss testing agency that attests to the precision and precision of wristwatches. COSC accreditation is a sign of quality craftsmanship and reliability in timekeeping. Not all watch brands follow COSC validation, such as Hublot, which instead follows to its proprietary demanding criteria with mechanisms like the UNICO calibre, reaching similar precision.
The Science of Precision Chronometry
The core system of a mechanical timepiece involves the spring, which provides energy as it loosens. This system, however, can be susceptible to environmental elements that may affect its precision. COSC-certified mechanisms undergo rigorous testing—over 15 days in various circumstances (5 positions, three temperatures)—to ensure their durability and dependability. The tests evaluate:
Mean daily rate precision between -4 and +6 secs.
Mean variation, maximum variation rates, and effects of thermal variations.
Why COSC Certification Matters
For watch enthusiasts and connoisseurs, a COSC-accredited timepiece isn’t just a item of tech but a demonstration to lasting quality and accuracy. It signifies a watch that:
Presents exceptional dependability and precision.
Ensures assurance of superiority across the whole design of the timepiece.
Is probable to retain its value more efficiently, making it a sound investment.
Popular Timepiece Manufacturers
Several famous brands prioritize COSC accreditation for their timepieces, including Rolex, Omega, Breitling, and Longines, among others. Longines, for instance, provides collections like the Record and Soul, which feature COSC-accredited mechanisms equipped with innovative materials like silicone balance suspensions to enhance durability and performance.
Historic Background and the Evolution of Chronometers
The idea of the chronometer dates back to the requirement for exact chronometry for navigational at sea, highlighted by John Harrison’s work in the eighteenth century. Since the official foundation of Controle Officiel Suisse des Chronometres in 1973, the accreditation has become a yardstick for assessing the accuracy of luxury timepieces, maintaining a tradition of excellence in watchmaking.
Conclusion
Owning a COSC-accredited timepiece is more than an visual choice; it’s a commitment to quality and accuracy. For those valuing precision above all, the COSC validation provides tranquility of thoughts, ensuring that each validated timepiece will perform dependably under various conditions. Whether for personal contentment or as an investment decision, COSC-validated timepieces stand out in the world of horology, bearing on a legacy of meticulous timekeeping.
Son Zamanın En Büyük Beğenilen Kumarhane Platformu: Casibom
Casino oyunlarını sevenlerin artık duymuş olduğu Casibom, en son dönemde adından genellikle söz ettiren bir şans ve kumarhane platformu haline geldi. Türkiye’nin en başarılı casino platformlardan biri olarak tanınan Casibom’un haftalık olarak cinsinden değişen giriş adresi, sektörde oldukça yenilikçi olmasına rağmen emin ve kar getiren bir platform olarak ön plana çıkıyor.
Casibom, rakiplerini geride kalarak köklü casino sitelerinin önüne geçmeyi başarıyor. Bu pazarda köklü olmak gereklidir olsa da, oyunculardan iletişimde bulunmak ve onlara erişmek da benzer miktar önemli. Bu durumda, Casibom’un her saat yardım veren gerçek zamanlı destek ekibi ile kolayca iletişime geçilebilir olması önemli bir avantaj sağlıyor.
Hızla artan oyuncu kitlesi ile ilgi çeken Casibom’un gerisindeki başarılı faktörleri arasında, sadece casino ve canlı casino oyunlarına sınırlı olmayan geniş bir hizmetler yelpazesi bulunuyor. Sporcular bahislerinde sunduğu geniş seçenekler ve yüksek oranlar, oyuncuları çekmeyi başarılı oluyor.
Ayrıca, hem spor bahisleri hem de kumarhane oyunları oyuncularına yönelik sunulan yüksek yüzdeli avantajlı bonuslar da ilgi çekiyor. Bu nedenle, Casibom kısa sürede alanında iyi bir reklam başarısı elde ediyor ve önemli bir katılımcı kitlesi kazanıyor.
Casibom’un kazanç sağlayan promosyonları ve tanınırlığı ile birlikte, siteye üyelik ne şekilde sağlanır sorusuna da atıfta bulunmak gereklidir. Casibom’a taşınabilir cihazlarınızdan, PC’lerinizden veya tabletlerinizden web tarayıcı üzerinden rahatça erişilebilir. Ayrıca, platformun mobil uyumlu olması da önemli bir avantaj sunuyor, çünkü şimdi neredeyse herkesin bir cep telefonu var ve bu telefonlar üzerinden hızlıca erişim sağlanabiliyor.
Hareketli tabletlerinizle bile yolda canlı olarak tahminler alabilir ve maçları canlı olarak izleyebilirsiniz. Ayrıca, Casibom’un mobil uyumlu olması, memleketimizde kumarhane ve oyun gibi yerlerin meşru olarak kapatılmasıyla birlikte bu tür platformlara erişimin önemli bir yolunu oluşturuyor.
Casibom’un emin bir casino web sitesi olması da gereklidir bir avantaj sağlıyor. Belgeli bir platform olan Casibom, sürekli bir şekilde keyif ve kazanç sağlama imkanı sağlar.
Casibom’a abone olmak da son derece kolaydır. Herhangi bir belge koşulu olmadan ve bedel ödemeden siteye kolayca üye olabilirsiniz. Ayrıca, site üzerinde para yatırma ve çekme işlemleri için de birçok farklı yöntem bulunmaktadır ve herhangi bir kesim ücreti isteseniz de alınmaz.
Ancak, Casibom’un güncel giriş adresini izlemek de gereklidir. Çünkü gerçek zamanlı şans ve oyun web siteleri popüler olduğu için hileli platformlar ve dolandırıcılar da ortaya çıkmaktadır. Bu nedenle, Casibom’un sosyal medya hesaplarını ve güncel giriş adresini düzenli olarak kontrol etmek gereklidir.
Sonuç olarak, Casibom hem güvenilir hem de kazandıran bir kumarhane web sitesi olarak ilgi çekici. Yüksek bonusları, geniş oyun alternatifleri ve kullanıcı dostu taşınabilir uygulaması ile Casibom, kumarhane tutkunları için ideal bir platform getiriyor.
exprimegranada.com
ユニークな視点で、非常に啓発されました。ありがとうございます。
thephotoretouch.com
Fang Jifan은 White Lotus Sect에 대해 걱정할 수 없었습니다.
проверить свои usdt на чистоту
Проверка данных бумажников на выявление подозрительных средств: Защита вашего электронного портфельчика
В мире электронных денег становится все значимее необходимее обеспечивать защиту личных активов. Каждый день жулики и киберпреступники создают новые подходы мошенничества и угонов виртуальных финансов. Одним из ключевых способов обеспечения безопасности становится проверка кошельков кошельков для хранения криптовалюты на присутствие неправомерных средств.
Из-за чего именно поэтому важно и проверить свои цифровые кошельки для хранения криптовалюты?
В первую очередь этот момент необходимо для того чтобы обеспечения безопасности личных денег. Большинство пользователи сталкиваются с риском утраты их финансовых средств из-за недоброжелательных схем или краж. Проверка кошельков кошелька способствует предотвращению своевременно выявить подозрительные манипуляции и предупредить.
Что предоставляет фирма-разработчик?
Мы предлагаем вам услугу проверки криптовалютных кошельков и переводов с целью выявления начала финансовых средств и дать полного отчета о результатах. Наша система анализирует данные пользователя для определения незаконных действий и определить уровень риска для вашего портфеля. Благодаря нашему анализу, вы можете избежать с регуляторными органами и защитить себя от непреднамеренного участия в нелегальных операций.
Как происходит процесс?
Компания наша фирма-разработчик работает с крупными аудиторскими фирмами, например Certik, чтобы дать гарантию и точность наших проверок. Мы применяем современные технологии и методики анализа для выявления опасных манипуляций. Персональные данные наших граждан обрабатываются и хранятся в соответствии с высокими стандартами безопасности.
Ключевой запрос: “проверить свои USDT на чистоту”
В случае если вы хотите проверить безопасности и чистоте собственных кошельков USDT, наши эксперты оказывает возможность исследовать бесплатную проверку первых пяти кошельков. Достаточно просто адрес своего кошелька в соответствующее окно на нашем онлайн-ресурсе, и мы вышлем вам подробную информацию о состоянии вашего кошелька.
Обезопасьте свои активы уже сегодня!
Не рискуйте становиться пострадать от хакеров или оказаться в неприятной ситуации из-за нелегальных сделок с вашими собственными финансами. Обратитесь к профессиональным консультантам, которые окажут помощь, вам и вашим финансам обезопаситься криптовалютные активы и избежать. Предпримите первый шаг защите вашего криптовалютного портфеля активов сразу же!
Проверка данных кошельков для хранения криптовалюты на выявление подозрительных средств передвижения: Охрана своего цифрового портфеля
В мире цифровых валют становится все важнее все более необходимо гарантировать секретность собственных денег. Постоянно обманщики и криминальные элементы выработывают совершенно новые подходы мошенничества и воровства цифровых денег. Одним из ключевых способов обеспечения является анализ кошельков по выявление наличия незаконных финансовых средств.
Почему вот важно проверять собственные цифровые бумажники?
В первую очередь это важно для охраны личных средств. Многие участники рынка рискуют потери своих собственных средств вследствие несправедливых методов или воровства. Проверка данных кошельков способствует предотвращению выявить вовремя подозрительные действия и предотвратить.
Что предлагает вашему вниманию наша организация?
Мы предоставляем услугу проверки данных электронных кошельков для хранения электронных денег и транзакций средств с целью идентификации источника средств передвижения и выдачи подробного отчета о проверке. Наши технология проверяет данные для определения потенциально нелегальных действий и оценить риск для того, чтобы вашего финансового портфеля. Благодаря нашей системе проверки, вы сможете предотвратить возможные с государственными органами и обезопасить себя от случайного участия в незаконных операций.
Как осуществляется процесс проверки?
Организация наша фирма сотрудничает с крупными аудиторами фирмами, вроде Certik, для того чтобы гарантировать и правильность наших проверок данных. Мы применяем передовые и подходы анализа данных для выявления небезопасных манипуляций. Персональные сведения наших граждан обрабатываются и сохраняются в соответствии с положениями высокими стандартами безопасности.
Основная просьба: “проверить свои USDT на чистоту”
В случае если вы хотите убедиться в безопасности и чистоте собственных USDT-кошельков, наши профессионалы предоставляет шанс бесплатной проверки первых пяти кошельков. Просто введите свой кошелек в нужное место на нашем веб-сайте, и мы передадим вам подробный отчет о статусе вашего кошелька.
Защитите свои финансовые активы сразу же!
Предотвращайте риски оказаться в жертвой мошенников злоумышленников или стать неприятном положении нелегальных действий с вашими собственными деньгами. Позвольте себе специалистам, которые окажут поддержку, вам и вашему бизнесу защитить свои финансовые активы и предотвратить возможные проблемы. Предпримите первый шаг к безопасности защите своего электронного портфеля прямо сейчас!
Анализ Tether в нетронутость: Как обезопасить свои электронные состояния
Каждый день все больше индивидуумов заботятся в безопасность собственных цифровых средств. Постоянно мошенники изобретают новые подходы кражи криптовалютных активов, и также держатели электронной валюты становятся жертвами их обманов. Один из техник защиты становится проверка бумажников в наличие незаконных финансов.
С каким намерением это потребуется?
Прежде всего, для того чтобы защитить собственные средства против мошенников и похищенных монет. Многие специалисты встречаются с риском потери личных средств в результате мошеннических сценариев или грабежей. Анализ кошельков способствует обнаружить подозрительные транзакции и также предотвратить возможные убытки.
Что мы предлагаем?
Мы предлагаем сервис проверки цифровых бумажников или транзакций для выявления источника средств. Наша система исследует информацию для выявления противозаконных операций и оценки угрозы для вашего портфеля. Вследствие этой проверке, вы сможете избежать проблем с регуляторами или обезопасить себя от участия в нелегальных операциях.
Как это работает?
Мы работаем с первоклассными проверочными фирмами, такими как Certik, чтобы предоставить точность наших проверок. Наша команда применяем передовые техники для обнаружения потенциально опасных транзакций. Ваши информация обрабатываются и сохраняются согласно с высокими стандартами безопасности и конфиденциальности.
Как проверить свои USDT в прозрачность?
При наличии желания подтвердить, что ваши Tether-бумажники прозрачны, наш подход обеспечивает бесплатное тестирование первых пяти кошельков. Просто передайте местоположение своего бумажника на на нашем веб-сайте, а также наш сервис предоставим вам подробный доклад о его статусе.
Защитите вашими активы уже сегодня!
Не подвергайте опасности подвергнуться обманщиков или оказаться в неприятную обстановку по причине незаконных сделок. Обратитесь к нам, для того чтобы защитить ваши цифровые активы и предотвратить неприятностей. Сделайте первый шаг к сохранности вашего криптовалютного портфеля уже сейчас!
Тестирование Tether на нетронутость: Каким образом защитить свои электронные финансы
Каждый день все больше пользователей обращают внимание на безопасность собственных криптовалютных активов. День ото дня обманщики разрабатывают новые схемы кражи цифровых средств, и также владельцы криптовалюты становятся пострадавшими их интриг. Один техник обеспечения безопасности становится проверка бумажников на присутствие незаконных средств.
Для чего это потребуется?
В первую очередь, для того чтобы обезопасить собственные финансы от шарлатанов и также украденных денег. Многие инвесторы сталкиваются с риском утраты своих финансов из-за мошеннических механизмов или краж. Тестирование кошельков помогает обнаружить сомнительные действия а также предотвратить потенциальные убытки.
Что мы предлагаем?
Мы предлагаем услугу анализа криптовалютных кошельков или операций для выявления источника денег. Наша технология исследует данные для выявления противозаконных операций а также оценки угрозы для вашего портфеля. За счет этой проверке, вы сможете избежать недочетов с регуляторами и также обезопасить себя от участия в противозаконных сделках.
Каким образом это работает?
Наша фирма сотрудничаем с лучшими проверочными агентствами, например Cure53, с целью предоставить точность наших проверок. Мы применяем передовые технологии для обнаружения потенциально опасных операций. Ваши данные обрабатываются и хранятся в соответствии с высокими стандартами безопасности и приватности.
Как проверить свои Tether в чистоту?
Если вам нужно подтвердить, что ваша Tether-бумажники нетронуты, наш сервис предоставляет бесплатную проверку первых пяти кошельков. Просто вбейте местоположение личного бумажника на на нашем веб-сайте, и также мы предоставим вам полную информацию отчет о его положении.
Охраняйте ваши фонды уже сейчас!
Не рискуйте подвергнуться дельцов или попадать в неприятную обстановку по причине нелегальных операций. Обратитесь к нам, для того чтобы обезопасить ваши криптовалютные средства и избежать затруднений. Примите первый шаг к безопасности криптовалютного портфеля прямо сейчас!
usdt и отмывание
Тетер – является надежная цифровая валюта, привязанная к фиатной валюте, такой как американский доллар. Данное обстоятельство делает данный актив в частности привлекательной у трейдеров, поскольку данная криптовалюта предоставляет стабильность курса в в условиях волатильности рынка цифровых активов. Все же, подобно другая разновидность цифровых активов, USDT подвержена вероятности использования в целях отмывания денег и финансирования неправомерных операций.
Отмывание денег посредством цифровые валюты становится все больше и больше распространенным в большей степени путем для того чтобы скрытия происхождения средств. Воспользовавшись разносторонние методы, мошенники могут пытаться легализовывать незаконно добытые средства посредством сервисы обмена криптовалют или миксеры, для того чтобы сделать происхождение менее очевидным.
Именно для этой цели, экспертиза USDT на чистоту становится весьма важной инструментом предосторожности для владельцев цифровых валют. Доступны специализированные платформы, которые осуществляют проверку операций и кошельков, для того чтобы определить подозрительные транзакции и противоправные источники средств. Данные платформы содействуют пользователям устранить непреднамеренного вовлечения в финансирование преступных деяний и предотвратить блокировку счетов со стороны регуляторных органов.
Экспертиза USDT на чистоту также способствует защитить себя от потенциальных финансовых потерь. Владельцы могут быть убеждены что их финансовые ресурсы не ассоциированы с нелегальными сделками, что уменьшает вероятность блокировки счета или перечисления денег.
Таким образом, в условиях современности возрастающей сложности среды криптовалют требуется принимать меры для обеспечения безопасности своего капитала. Проверка USDT на чистоту при помощи специализированных сервисов является одним из вариантов защиты от отмывания денег, гарантируя владельцам цифровых валют дополнительный уровень и защиты.
Циклёвка паркета: особенности и этапы услуги
Циклёвка паркета — это процесс восстановления внешнего вида паркетного пола путём удаления верхнего повреждённого слоя и возвращения ему первоначального вида. Услуга включает в себя несколько этапов:
Подготовка: перед началом работы необходимо защитить мебель и другие предметы от пыли и грязи, а также удалить плинтусы.
Шлифовка: с помощью шлифовальной машины удаляется старый лак и верхний повреждённый слой древесины.
Шпатлёвка: после шлифовки поверхность паркета шпатлюется для заполнения трещин и выравнивания поверхности.
Грунтовка: перед нанесением лака паркет грунтуется для улучшения адгезии и защиты от плесени и грибка.
Нанесение лака: лак наносится в несколько слоёв с промежуточной шлифовкой между ними.
Полировка: после нанесения последнего слоя лака паркет полируется для придания поверхности блеска и гладкости.
Циклёвка паркета позволяет обновить внешний вид пола, восстановить его структуру и продлить срок службы.
Сайт: ykladka-parketa.ru Циклёвка паркета
九州娛樂
exprimegranada.com
このブログはいつも実用的で役立つ情報を提供してくれて、大変感謝しています。
cá cược thể thao
cá cược thể thao
Sure, here’s the text with spin syntax applied:
Link Pyramid
After several updates to the G search engine, it is essential to apply different strategies for ranking.
Today there is a method to attract the interest of search engines to your site with the assistance of backlinks.
Backlinks are not only an powerful marketing instrument but they also have authentic traffic, straight sales from these resources perhaps will not be, but transitions will be, and it is beneficial traffic that we also receive.
What in the end we get at the end result:
We display search engines site through backlinks.
Prluuchayut natural transitions to the site and it is also a indicator to search engines that the resource is used by individuals.
How we show search engines that the site is liquid:
Backlinks do to the primary page where the main information.
We make links through redirects reliable sites.
The most IMPORTANT we place the site on sites analytical tools individual tool, the site goes into the memory of these analysis tools, then the acquired links we place as redirects on weblogs, forums, comment sections. This significant action shows search engines the site map as analyzer sites display all information about sites with all key terms and headings and it is very BENEFICIAL.
All details about our services is on the website!
usdt не чистое
Анализ USDT в чистоту: Как обезопасить свои электронные финансы
Постоянно все больше граждан обращают внимание в безопасность личных электронных средств. Каждый день мошенники предлагают новые методы кражи электронных средств, а также собственники криптовалюты оказываются пострадавшими их интриг. Один из подходов обеспечения безопасности становится проверка кошельков в присутствие нелегальных финансов.
С каким намерением это полезно?
Прежде всего, для того чтобы защитить свои активы против мошенников или похищенных денег. Многие участники сталкиваются с риском потери их финансов в результате обманных механизмов или краж. Анализ кошельков помогает выявить сомнительные операции а также предотвратить возможные убытки.
Что наша команда предлагаем?
Мы предлагаем услугу проверки электронных кошельков или транзакций для определения источника средств. Наша система анализирует данные для определения противозаконных транзакций или оценки риска для вашего портфеля. За счет этой проверке, вы сможете избежать проблем с регуляторами и предохранить себя от участия в незаконных операциях.
Как происходит процесс?
Мы сотрудничаем с ведущими аудиторскими организациями, наподобие Cure53, для того чтобы обеспечить точность наших тестирований. Наша команда применяем современные технологии для выявления рискованных сделок. Ваши информация обрабатываются и хранятся согласно с высокими нормами безопасности и конфиденциальности.
Каким образом проверить свои Tether для нетронутость?
Если вам нужно убедиться, что ваши USDT-кошельки прозрачны, наш сервис предоставляет бесплатную проверку первых пяти кошельков. Легко введите адрес личного кошелька на на сайте, или наша команда предложим вам полную информацию доклад о его положении.
Обезопасьте ваши фонды прямо сейчас!
Не подвергайте риску попасть в жертву шарлатанов или оказаться в неприятную обстановку по причине незаконных транзакций. Свяжитесь с нашему агентству, с тем чтобы сохранить ваши электронные средства и предотвратить затруднений. Совершите первый шаг для сохранности криптовалютного портфеля прямо сейчас!
Creating exclusive articles on Platform and Telegraph, why it is required:
Created article on these resources is better ranked on less frequent queries, which is very significant to get natural traffic.
We get:
natural traffic from search algorithms.
organic traffic from the in-house rendition of the medium.
The webpage to which the article refers gets a link that is liquid and increases the ranking of the site to which the article refers.
Articles can be made in any quantity and choose all less frequent queries on your topic.
Medium pages are indexed by search algorithms very well.
Telegraph pages need to be indexed separately indexer and at the same time after indexing they sometimes occupy places higher in the search algorithms than the medium, these two platforms are very helpful for getting traffic.
Here is a URL to our services where we provide creation, indexing of sites, articles, pages and more.
zanetvize.com
따라서 환자가 수술 후 다시 빛을 볼 수 있을지는 아직 미지수다.
בטים
הימורים מקוונים הם חוויה מרגשת ופופולרי ביותר בעידן המקוון, שמביאה מיליונים אנשים מכל
רחבי העולם. ההימורים המקוונים מתרחשים על פי אירועים ספורטיים, תוצאות פוליטיות ואפילו תוצאות מזג האוויר ונושאים נוספים. אתרי ה הימורים הווירטואליים מזמינים את המשתתפים להמר על תוצאות אפשריות וליהנות חוויות ייחודיות ומרתקות.
ההימורים המקוונים הם כבר חלק חשוב מתרבות החברה לא מעט זמן והיום הם לא רק חלק נפרד מהפעילות הכלכלית והתרבותית, אלא כמו כן מספקים תשואות וחוויות מרתקות. משום שהם נגישים וקלים לשימוש, הם מובילים את כולם ליהנות מהניסיון ולהנות מכל הניצחונות והפרסים בכל זמן ובכל מקום.
טכנולוגיות דיגיטליות והמשחקים באינטרנט הפכו להיות הפופולריים ביותר מעניינת ופופולרית. מיליונים אנשים מכל כל רחבי העולם מתעניינים בהימורים מקוונים, כוללים הימורי ספורט. הימורים מקוונים מציעים למשתתפים חוויה מהנה ומרגשת, המתאימה לכולם בכל זמן ובכל מקום.
אז מה חכם אתה מחכה? הצטרף עכשיו והתחיל לחוות את ההתרגשות וההנאה שהימורים מקוונים מציעים.
שרף הנחיות: המדריכים המלא לסחר שרף דרך המסר
קנאביס הנחיות הם אתר רשמי מסמכים ומדריכים לרכישת שרף במקום התוכנה הפופולארית מסר.
האתר רשמי סופק את כלל המידע הקישורים והמידע המתעדף לקבוצות וערוצים באתר מומלצים לביקור להשקיה קנאביסין בהמשלוח בישראל.
כמו למעשה, האתר הרשמי מספקת מדריך מתעדף לכיצד ניתן להתקשר בהקנאביס ולקנה קנאביס בקלות ובמהירות.
בעזרת המדריך, כמו כן המשתמשים משתמשים בטלגרם יוכלו להחיים הקנאביס בטלגרם בפני מוגנת ובטוחה.
ההרובוט של טלגראס מאפשר להמשתמשים ללבצע פעולה שונות ומקוריות כמו כן השקת שרף, קבלה סיוע, בדיקת הקיימות והוספת הערות על המצרים. כל זאת בצורה פשוטה וקלה דרך האפליקציה.
כאשר מדובר בשיטות ה תשלום, הקנאביס משתמשת בשיטות מוכרות כמו מזומן, כרטיסי האשראי של אשראי ומטבע דיגיטלי. חיוני לציין כי ישנה לבדוק ולוודא את המדיניות והחוקים המקומיים בארץ שלך לפני ביצוע רכישה.
הטלגרם מציע יתרונות מרכזיים חשובים כגון הגנת הפרטיות וביטחון אישי מוגברים, תקשורת מהירה מאוד וגמישות גבוהה מאוד. בנוסף, הוא מאפשר כניסה להקהל גלובלית רחבה ומציע מגוון של תכונות ויכולות.
בבתום, טלגראס מדריכים היה המקום האידיאלי ללמצוא את כל הידע והקישורים הנדרשים להשקיה שרף בדרך מהירה, בבטוחה ונוחה דרך הטלגרמה.
link building
Backlink creation is just as successful now, simply the tools to operate within this domain have got altered.
There are numerous options to inbound links, our company utilize some of them, and these strategies operate and are actually examined by our team and our clientele.
Recently we carried out an trial and it turned out that low-volume search queries from one website rank well in search engines, and the result doesn’t have being your personal domain, you are able to make use of social media from Web 2.0 range for this.
It is also possible to partially transfer weight through site redirects, providing a diverse hyperlink profile.
Head over to our site where our own offerings are offered with thorough explanations.
k8 カジノ 口コミ
素晴らしい情報源です。いつも参考になります。
thephotoretouch.com
Tang Yin의 눈알이 떨어질 것입니다. 멘토가 남동생에게 작은 난로까지 줬다고요?
как разорвать контракт сво
С началом СВО уже спустя полгода была объявлена первая волна мобилизации. При этом прошлая, в последний раз в России была аж в 1941 году, с началом Великой Отечественной Войны. Конечно же, желающих отправиться на фронт было не много, а потому люди стали искать способы не попасть на СВО, для чего стали покупать справки о болезнях, с которыми можно получить категорию Д. И все это стало возможным с даркнет сайтами, где можно найти практически все что угодно. Именно об этой отрасли темного интернета подробней и поговорим в этой статье.
Лендинг-пейдж — это одностраничный сайт, предназначенный для рекламы и продажи товаров или услуг, а также для сбора контактных данных потенциальных клиентов. Вот несколько причин, почему лендинг-пейдж важен для бизнеса:
Увеличение узнаваемости компании. Лендинг-пейдж позволяет представить компанию и её продукты или услуги в выгодном свете, что способствует росту узнаваемости бренда.
Повышение продаж. Заказать лендинг можно здесь – 1landingpage.ru Одностраничные сайты позволяют сосредоточиться на конкретных предложениях и акциях, что повышает вероятность совершения покупки.
Оптимизация SEO-показателей. Лендинг-пейдж создаются с учётом ключевых слов и фраз, что улучшает позиции сайта в результатах поиска и привлекает больше целевых посетителей.
Привлечение новой аудитории. Одностраничные сайты могут использоваться для продвижения новых продуктов или услуг, а также для привлечения внимания к определённым кампаниям или акциям.
Расширение клиентской базы. Лендинг-пейдж собирают контактные данные потенциальных клиентов, что позволяет компании поддерживать связь с ними и предлагать дополнительные услуги или товары.
Простота генерации лидов. Лендинг-пейдж предоставляют краткую и понятную информацию о продуктах или услугах, что облегчает процесс принятия решения для потенциальных клиентов.
Сбор персональных данных. Лендинг-пейдж позволяют собирать информацию о потенциальных клиентах, такую как email-адрес, имя и контактные данные, что помогает компании лучше понимать свою аудиторию и предоставлять более персонализированные услуги.
Улучшение поискового трафика. Лендинг-пейдж создаются с учётом определённых поисковых запросов, что позволяет привлекать больше целевых посетителей на сайт.
Эффективное продвижение новой продукции. Лендинг-пейдж можно использовать для продвижения новых товаров или услуг, что позволяет привлечь внимание потенциальных клиентов и стимулировать их к покупке.
Лёгкий процесс принятия решений. Лендинг-пейдж содержат только самую необходимую информацию, что упрощает процесс принятия решения для потенциальных клиентов.
В целом, лендинг-пейдж являются мощным инструментом для продвижения бизнеса, увеличения продаж и привлечения новых клиентов.
заказать лендинг пейдж
Pirámide de backlinks
Aquí está el texto con la estructura de spintax que propone diferentes sinónimos para cada palabra:
“Pirámide de backlinks
Después de muchas actualizaciones del motor de búsqueda G, necesita aplicar diferentes opciones de clasificación.
Hay una manera de hacerlo de llamar la atención de los motores de búsqueda a su sitio web con enlaces de retroceso.
Los enlaces de retorno no sólo son una herramienta eficaz para la promoción, sino que también tienen tráfico orgánico, las ventas directas de estos recursos más probable es que no será, pero las transiciones será, y es poedenicheskogo tráfico que también obtenemos.
Lo que vamos a obtener al final en la salida:
Mostramos el sitio a los motores de búsqueda a través de enlaces de retorno.
Conseguimos conversiones orgánicas hacia el sitio, lo que también es una señal para los buscadores de que el recurso está siendo utilizado por la gente.
Cómo mostramos los motores de búsqueda que el sitio es líquido:
1 enlace se hace a la página principal donde está la información principal
Hacemos backlinks a través de redirecciones de sitios de confianza
Lo más vital colocamos el sitio en una herramienta independiente de analizadores de sitios, el sitio entra en la caché de estos analizadores, luego los enlaces recibidos los colocamos como redirecciones en blogs, foros, comentarios.
Esta crucial acción muestra a los buscadores el MAPA DEL SITIO, ya que los analizadores de sitios muestran toda la información de los sitios con todas las palabras clave y títulos y es muy efectivo.
¡Toda la información sobre nuestros servicios en el sitio web!
Thank you for sharing this information, it’s very helpful! see this
反向連結金字塔
反向連接金字塔
G搜尋引擎在屡经更新后需要使用不同的排名參數。
今天有一種方法可以使用反向連接吸引G搜尋引擎對您的網站的注意。
反向連結不僅是有效的推廣工具,也是有機流量。
我們會得到什麼結果:
我們透過反向連接向G搜尋引擎展示我們的網站。
他們收到了到該網站的自然過渡,這也是向G搜尋引擎發出的信號,表明該資源正在被人們使用。
我們如何向G搜尋引擎表明該網站具有流動性:
個帶有主要訊息的主頁反向連結
我們透過來自受信任網站的重新导向來建立反向連接。
此外,我們將網站放置在单独的網路分析器上,網站最終會進入這些分析器的快取中,然後我們使用產生的連結作為部落格、論壇和評論的重定向。 這個重要的操作向G搜尋引擎顯示了網站地圖,因為網站分析器顯示了有關網站的所有資訊以及所有關鍵字和標題,這很棒
有關我們服務的所有資訊都在網站上!
k8 カジノ ログイン
素晴らしい内容と分析で、非常に勉強になりました。
Fantastic goods from you, man. I’ve keep in mind your stuff prior to and you’re simply too magnificent. I really like what you’ve received here, really like what you’re stating and the best way by which you are saying it. You are making it entertaining and you still take care of to stay it sensible. I can not wait to read far more from you. This is actually a terrific website.
Как сберечь свои данные: остерегайтесь утечек информации в интернете. Сегодня защита личных данных становится всё больше важной задачей. Одним из наиболее обычных способов утечки личной информации является слив «сит фраз» в интернете. Что такое сит фразы и в какой мере сберечься от их утечки? Что такое «сит фразы»? «Сит фразы» — это синтезы слов или фраз, которые бывают используются для доступа к различным онлайн-аккаунтам. Эти фразы могут включать в себя имя пользователя, пароль или разные конфиденциальные данные. Киберпреступники могут пытаться получить доступ к вашим аккаунтам, с помощью этих сит фраз. Как сохранить свои личные данные? Используйте сложные пароли. Избегайте использования простых паролей, которые мгновенно угадать. Лучше всего использовать комбинацию букв, цифр и символов. Используйте уникальные пароли для каждого аккаунта. Не пользуйтесь один и тот же пароль для разных сервисов. Используйте двухфакторную проверку (2FA). Это вводит дополнительный уровень безопасности, требуя подтверждение входа на ваш аккаунт посредством другое устройство или метод. Будьте осторожны с онлайн-сервисами. Не доверяйте свою информацию ненадежным сайтам и сервисам. Обновляйте программное обеспечение. Установите обновления для вашего операционной системы и программ, чтобы сохранить свои данные от вредоносного ПО. Вывод Слив сит фраз в интернете может повлечь за собой серьезным последствиям, таким как кража личной информации и финансовых потерь. Чтобы сохранить себя, следует принимать меры предосторожности и использовать надежные методы для хранения и управления своими личными данными в сети
даркнет сливы тг
Даркнет и сливы в Телеграме
Даркнет – это часть интернета, которая не индексируется обыденными поисковыми системами и требует особых программных средств для доступа. В даркнете существует множество скрытых сайтов, где можно найти различные товары и услуги, в том числе и нелегальные.
Одним из востребованных способов распространения информации в даркнете является использование мессенджера Телеграм. Телеграм предоставляет возможность создания закрытых каналов и чатов, где пользователи могут обмениваться информацией, в том числе и нелегальной.
Сливы информации в Телеграме – это практика распространения конфиденциальной информации, такой как украденные данные, базы данных, персональные сведения и другие материалы. Эти сливы могут включать в себя информацию о кредитных картах, паролях, персональных сообщениях и даже фотографиях.
Сливы в Телеграме могут быть опасными, так как они могут привести к утечке конфиденциальной информации и нанести ущерб репутации и финансовым интересам людей. Поэтому важно быть предусмотрительным при обмене информацией в интернете и не доверять сомнительным источникам.
Вот кошельки с балансом у бота
сид фразы кошельков
Сид-фразы, или напоминающие фразы, представляют собой соединение слов, которая используется для генерации или восстановления кошелька криптовалюты. Эти фразы обеспечивают вход к вашим криптовалютным средствам, поэтому их надежное хранение и использование крайне важны для защиты вашего криптоимущества от утери и кражи.
Что такое сид-фразы кошельков криптовалют?
Сид-фразы составляют набор произвольно сгенерированных слов, часто от 12 до 24, которые представляют собой для создания уникального ключа шифрования кошелька. Этот ключ используется для восстановления входа к вашему кошельку в случае его повреждения или утери. Сид-фразы обладают высокой защиты и шифруются, что делает их секурными для хранения и передачи.
Зачем нужны сид-фразы?
Сид-фразы неотъемлемы для обеспечения безопасности и доступности вашего криптоимущества. Они позволяют восстановить вход к кошельку в случае утери или повреждения физического устройства, на котором он хранится. Благодаря сид-фразам вы можете легко создавать резервные копии своего кошелька и хранить их в безопасном месте.
Как обеспечить безопасность сид-фраз кошельков?
Никогда не передавайте сид-фразой ни с кем. Сид-фраза является вашим ключом к кошельку, и ее раскрытие может привести к утере вашего криптоимущества.
Храните сид-фразу в надежном месте. Используйте физически безопасные места, такие как банковские ячейки или специализированные аппаратные кошельки, для хранения вашей сид-фразы.
Создавайте резервные копии сид-фразы. Регулярно создавайте резервные копии вашей сид-фразы и храните их в разных безопасных местах, чтобы обеспечить доступ к вашему кошельку в случае утери или повреждения.
Используйте дополнительные меры безопасности. Включите двухфакторную аутентификацию и другие методы защиты для своего кошелька криптовалюты, чтобы обеспечить дополнительный уровень безопасности.
Заключение
Сид-фразы кошельков криптовалют являются ключевым элементом надежного хранения криптоимущества. Следуйте рекомендациям по безопасности, чтобы защитить свою сид-фразу и обеспечить безопасность своих криптовалютных средств.
слив сид фраз
Слив посеянных фраз (seed phrases) является единственным из наиболее популярных способов утечки личной информации в мире криптовалют. В этой статье мы разберем, что такое сид фразы, по какой причине они важны и как можно защититься от их утечки.
Что такое сид фразы?
Сид фразы, или мнемонические фразы, представляют собой комбинацию слов, которая используется для создания или восстановления кошелька криптовалюты. Обычно сид фраза состоит из 12 или 24 слов, которые представляют собой ключ к вашему кошельку. Потеря или утечка сид фразы может приводить к потере доступа к вашим криптовалютным средствам.
Почему важно защищать сид фразы?
Сид фразы представляют собой ключевым элементом для секурного хранения криптовалюты. Если злоумышленники получат доступ к вашей сид фразе, они будут в состоянии получить доступ к вашему кошельку и украсть все средства.
Как защититься от утечки сид фраз?
Никогда не передавайте свою сид фразу любому, даже если вам представляется, что это авторизованное лицо или сервис.
Храните свою сид фразу в надежном и безопасном месте. Рекомендуется использовать аппаратные кошельки или специальные программы для хранения сид фразы.
Используйте дополнительные методы защиты, такие как двухфакторная аутентификация (2FA), для усиления безопасности вашего кошелька.
Регулярно делайте резервные копии своей сид фразы и храните их в других безопасных местах.
Заключение
Слив сид фраз является серьезной угрозой для безопасности владельцев криптовалют. Понимание важности защиты сид фразы и принятие соответствующих мер безопасности помогут вам избежать потери ваших криптовалютных средств. Будьте бдительны и обеспечивайте надежную защиту своей сид фразы
娛樂城推薦
Player線上娛樂城遊戲指南與評測
台灣最佳線上娛樂城遊戲的終極指南!我們提供專業評測,分析熱門老虎機、百家樂、棋牌及其他賭博遊戲。從遊戲規則、策略到選擇最佳娛樂城,我們全方位覆蓋,協助您更安全的遊玩。
Player如何評測:公正與專業的評分標準
在【Player娛樂城遊戲評測網】我們致力於為玩家提供最公正、最專業的娛樂城評測。我們的評測過程涵蓋多個關鍵領域,旨在確保玩家獲得可靠且全面的信息。以下是我們評測娛樂城的主要步驟:
娛樂城是什麼?
娛樂城是什麼?娛樂城是台灣對於線上賭場的特別稱呼,線上賭場分為幾種:現金版、信用版、手機娛樂城(娛樂城APP),一般來說,台灣人在稱娛樂城時,是指現金版線上賭場。
線上賭場在別的國家也有別的名稱,美國 – Casino, Gambling、中國 – 线上赌场,娱乐城、日本 – オンラインカジノ、越南 – Nhà cái。
娛樂城會被抓嗎?
在台灣,根據刑法第266條,不論是實體或線上賭博,參與賭博的行為可處最高5萬元罰金。而根據刑法第268條,為賭博提供場所並意圖營利的行為,可能面臨3年以下有期徒刑及最高9萬元罰金。一般賭客若被抓到,通常被視為輕微罪行,原則上不會被判處監禁。
信用版娛樂城是什麼?
信用版娛樂城是一種線上賭博平台,其中的賭博活動不是直接以現金進行交易,而是基於信用系統。在這種模式下,玩家在進行賭博時使用虛擬的信用點數或籌碼,這些點數或籌碼代表了一定的貨幣價值,但實際的金錢交易會在賭博活動結束後進行結算。
現金版娛樂城是什麼?
現金版娛樂城是一種線上博弈平台,其中玩家使用實際的金錢進行賭博活動。玩家需要先存入真實貨幣,這些資金轉化為平台上的遊戲籌碼或信用,用於參與各種賭場遊戲。當玩家贏得賭局時,他們可以將這些籌碼或信用兌換回現金。
娛樂城體驗金是什麼?
娛樂城體驗金是娛樂場所為新客戶提供的一種免費遊玩資金,允許玩家在不需要自己投入任何資金的情況下,可以進行各類遊戲的娛樂城試玩。這種體驗金的數額一般介於100元到1,000元之間,且對於如何使用這些體驗金以達到提款條件,各家娛樂城設有不同的規則。
Криптокошельки с балансом: зачем их покупают и как использовать
В мире криптовалют все возрастающую популярность приобретают криптокошельки с предустановленным балансом. Это уникальные кошельки, которые уже содержат определенное количество криптовалюты на момент покупки. Но зачем люди приобретают такие кошельки, и как правильно использовать их?
Почему покупают криптокошельки с балансом?
Удобство: Криптокошельки с предустановленным балансом предлагаются как готовое к работе решение для тех, кто хочет быстро начать пользоваться криптовалютой без необходимости покупки или обмена на бирже.
Подарок или награда: Иногда криптокошельки с балансом используются как подарок или вознаграждение в рамках акций или маркетинговых кампаний.
Анонимность: При покупке криптокошелька с балансом нет необходимости предоставлять личные данные, что может быть важно для тех, кто ценит анонимность.
Как использовать криптокошелек с балансом?
Проверьте безопасность: Убедитесь, что кошелек безопасен и не подвержен взлому. Проверьте репутацию продавца и происхождение приобретения кошелька.
Переведите средства на другой кошелек: Если вы хотите долгосрочно хранить криптовалюту, рекомендуется перевести средства на более безопасный или полезный для вас кошелек.
Не храните все средства на одном кошельке: Для обеспечения безопасности рекомендуется распределить средства между несколькими кошельками.
Будьте осторожны с фишингом и мошенничеством: Помните, что мошенники могут пытаться обмануть вас, предлагая криптокошельки с балансом с целью получения доступа к вашим средствам.
Заключение
Криптокошельки с балансом могут быть удобным и быстрым способом начать пользоваться криптовалютой, но необходимо помнить о безопасности и осторожности при их использовании.Выбор и приобретение криптокошелька с балансом – это значительный шаг, который требует внимания к деталям и осознанного подхода.”
слив сид фраз
Слив посеянных фраз (seed phrases) является одной из наиболее распространенных способов утечки личных информации в мире криптовалют. В этой статье мы разберем, что такое сид фразы, зачем они важны и как можно защититься от их утечки.
Что такое сид фразы?
Сид фразы, или мнемонические фразы, являются комбинацию слов, которая используется для генерации или восстановления кошелька криптовалюты. Обычно сид фраза состоит из 12 или 24 слов, которые символизируют собой ключ к вашему кошельку. Потеря или утечка сид фразы может привести к потере доступа к вашим криптовалютным средствам.
Почему важно защищать сид фразы?
Сид фразы представляют ключевым элементом для надежного хранения криптовалюты. Если злоумышленники получат доступ к вашей сид фразе, они могут получить доступ к вашему кошельку и украсть все средства.
Как защититься от утечки сид фраз?
Никогда не передавайте свою сид фразу никому, даже если вам происходит, что это авторизованное лицо или сервис.
Храните свою сид фразу в надежном и секурном месте. Рекомендуется использовать аппаратные кошельки или специальные программы для хранения сид фразы.
Используйте дополнительные методы защиты, такие как двусторонняя аутентификация, для усиления безопасности вашего кошелька.
Регулярно делайте резервные копии своей сид фразы и храните их в разных безопасных местах.
Заключение
Слив сид фраз является значительной угрозой для безопасности владельцев криптовалют. Понимание важности защиты сид фразы и принятие соответствующих мер безопасности помогут вам избежать потери ваших криптовалютных средств. Будьте бдительны и обеспечивайте надежную защиту своей сид фразы
ggg
هنا النص مع استخدام السبينتاكس:
“هرم الروابط الخلفية
بعد التحديثات العديدة لمحرك البحث G، تحتاج إلى تنفيذ خيارات ترتيب مختلفة.
هناك أسلوب لجذب انتباه محركات البحث إلى موقعك على الويب باستخدام الروابط الخلفية.
الروابط الخلفية ليست فقط أداة فعالة للترويج، ولكن تحمل أيضًا حركة مرور عضوية، والمبيعات المباشرة من هذه الموارد على الأرجح ستكون كذلك، ولكن الانتقالات ستكون، وهي حركة المرور التي نحصل عليها أيضًا.
ما سنحصل عليه في النهاية في النهاية في الإخراج:
نعرض الموقع لمحركات البحث من خلال الروابط الخلفية.
2- نحصل على تحويلات عضوية إلى الموقع، وهي أيضًا إشارة لمحركات البحث أن المورد يستخدمه الناس.
كيف نظهر لمحركات البحث أن الموقع سائل:
1 يتم عمل رابط خلفي للصفحة الرئيسية حيث المعلومات الرئيسية
نقوم بعمل لينكات خلفية من خلال عمليات تحويل المواقع الموثوقة
الأهم من ذلك أننا نضع الموقع على أداة منفصلة من أدوات تحليل المواقع، ويدخل الموقع في ذاكرة التخزين المؤقت لهذه المحللات، ثم الروابط المستلمة التي نضعها كتحويل على المدونات والمنتديات والتعليقات.
هذا التدبير المهم يُبرز لمحركات البحث خريطة الموقع، حيث تعرض أدوات تحليل المواقع جميع المعلومات عن المواقع مع جميع الكلمات الرئيسية والعناوين وهو أمر جيد جداً
جميع المعلومات عن خدماتنا على الموقع!
k8 カジノ リベート
非常に有益で実践的な情報。今後もフォローします。
RGBET
Cá Cược Thể Thao Trực Tuyến RGBET
Thể thao trực tuyến RGBET cung cấp thông tin cá cược thể thao mới nhất, như tỷ số bóng đá, bóng rổ, livestream và dữ liệu trận đấu. Đến với RGBET, bạn có thể tham gia chơi tại sảnh thể thao SABA, PANDA SPORT, CMD368, WG và SBO. Khám phá ngay!
Giới Thiệu Sảnh Cá Cược Thể Thao Trực Tuyến
Những sự kiện thể thao đa dạng, phủ sóng toàn cầu và cách chơi đa dạng mang đến cho người chơi tỷ lệ cá cược thể thao hấp dẫn nhất, tạo nên trải nghiệm cá cược thú vị và thoải mái.
Sảnh Thể Thao SBOBET
SBOBET, thành lập từ năm 1998, đã nhận được giấy phép cờ bạc trực tuyến từ Philippines, Đảo Man và Ireland. Tính đến nay, họ đã trở thành nhà tài trợ cho nhiều CLB bóng đá. Hiện tại, SBOBET đang hoạt động trên nhiều nền tảng trò chơi trực tuyến khắp thế giới.
Xem Chi Tiết »
Sảnh Thể Thao SABA
Saba Sports (SABA) thành lập từ năm 2008, tập trung vào nhiều hoạt động thể thao phổ biến để tạo ra nền tảng thể thao chuyên nghiệp và hoàn thiện. SABA được cấp phép IOM hợp pháp từ Anh và mang đến hơn 5.000 giải đấu thể thao đa dạng mỗi tháng.
Xem Chi Tiết »
Sảnh Thể Thao CMD368
CMD368 nổi bật với những ưu thế cạnh tranh, như cung cấp cho người chơi hơn 20.000 trận đấu hàng tháng, đến từ 50 môn thể thao khác nhau, đáp ứng nhu cầu của tất cả các fan hâm mộ thể thao, cũng như thoả mãn mọi sở thích của người chơi.
Xem Chi Tiết »
Sảnh Thể Thao PANDA SPORT
OB Sports đã chính thức đổi tên thành “Panda Sports”, một thương hiệu lớn với hơn 30 giải đấu bóng. Panda Sports đặc biệt chú trọng vào tính năng cá cược thể thao, như chức năng “đặt cược sớm và đặt cược trực tiếp tại livestream” độc quyền.
Xem Chi Tiết »
Sảnh Thể Thao WG
WG Sports tập trung vào những môn thể thao không quá được yêu thích, với tỷ lệ cược cao và xử lý đơn cược nhanh chóng. Đặc biệt, nhiều nhà cái hàng đầu trên thị trường cũng hợp tác với họ, trở thành là một trong những sảnh thể thao nổi tiếng trên toàn cầu.
Xem Chi Tiết »
Rikvip Club: Trung Tâm Giải Trí Trực Tuyến Hàng Đầu tại Việt Nam
Rikvip Club là một trong những nền tảng giải trí trực tuyến hàng đầu tại Việt Nam, cung cấp một loạt các trò chơi hấp dẫn và dịch vụ cho người dùng. Cho dù bạn là người dùng iPhone hay Android, Rikvip Club đều có một cái gì đó dành cho mọi người. Với sứ mạng và mục tiêu rõ ràng, Rikvip Club luôn cố gắng cung cấp những sản phẩm và dịch vụ tốt nhất cho khách hàng, tạo ra một trải nghiệm tiện lợi và thú vị cho người chơi.
Sứ Mạng và Mục Tiêu của Rikvip
Từ khi bắt đầu hoạt động, Rikvip Club đã có một kế hoạch kinh doanh rõ ràng, luôn nỗ lực để cung cấp cho khách hàng những sản phẩm và dịch vụ tốt nhất và tạo điều kiện thuận lợi nhất cho người chơi truy cập. Nhóm quản lý của Rikvip Club có những mục tiêu và ước muốn quyết liệt để biến Rikvip Club thành trung tâm giải trí hàng đầu trong lĩnh vực game đổi thưởng trực tuyến tại Việt Nam và trên toàn cầu.
Trải Nghiệm Live Casino
Rikvip Club không chỉ nổi bật với sự đa dạng của các trò chơi đổi thưởng mà còn với các phòng trò chơi casino trực tuyến thu hút tất cả người chơi. Môi trường này cam kết mang lại trải nghiệm chuyên nghiệp với tính xanh chín và sự uy tín không thể nghi ngờ. Đây là một sân chơi lý tưởng cho những người yêu thích thách thức bản thân và muốn tận hưởng niềm vui của chiến thắng. Với các sảnh cược phổ biến như Roulette, Sic Bo, Dragon Tiger, người chơi sẽ trải nghiệm những cảm xúc độc đáo và đặc biệt khi tham gia vào casino trực tuyến.
Phương Thức Thanh Toán Tiện Lợi
Rikvip Club đã được trang bị những công nghệ thanh toán tiên tiến ngay từ đầu, mang lại sự thuận tiện và linh hoạt cho người chơi trong việc sử dụng hệ thống thanh toán hàng ngày. Hơn nữa, Rikvip Club còn tích hợp nhiều phương thức giao dịch khác nhau để đáp ứng nhu cầu đa dạng của người chơi: Chuyển khoản Ngân hàng, Thẻ cào, Ví điện tử…
Kết Luận
Tóm lại, Rikvip Club không chỉ là một nền tảng trò chơi, mà còn là một cộng đồng nơi người chơi có thể tụ tập để tận hưởng niềm vui của trò chơi và cảm giác hồi hộp khi chiến thắng. Với cam kết cung cấp những sản phẩm và dịch vụ tốt nhất, Rikvip Club chắc chắn là điểm đến lý tưởng cho những người yêu thích trò chơi trực tuyến tại Việt Nam và cả thế giới.
k8 カジノ レート
この記事の書き方が好きです。わかりやすくて、とても役に立ちます。
UEFA Euro 2024 Sân Chơi Bóng Đá Hấp Dẫn Nhất Của Châu Âu
Euro 2024 là sự kiện bóng đá lớn nhất của châu Âu, không chỉ là một giải đấu mà còn là một cơ hội để các quốc gia thể hiện tài năng, sự đoàn kết và tinh thần cạnh tranh.
Euro 2024 hứa hẹn sẽ mang lại những trận cầu đỉnh cao và kịch tính cho người hâm mộ trên khắp thế giới. Cùng tìm hiểu các thêm thông tin hấp dẫn về giải đấu này tại bài viết dưới đây, gồm:
Nước chủ nhà
Đội tuyển tham dự
Thể thức thi đấu
Thời gian diễn ra
Sân vận động
Euro 2024 sẽ được tổ chức tại Đức, một quốc gia có truyền thống vàng của bóng đá châu Âu.
Đức là một đất nước giàu có lịch sử bóng đá với nhiều thành công quốc tế và trong những năm gần đây, họ đã thể hiện sức mạnh của mình ở cả mặt trận quốc tế và câu lạc bộ.
Việc tổ chức Euro 2024 tại Đức không chỉ là một cơ hội để thể hiện năng lực tổ chức tuyệt vời mà còn là một dịp để giới thiệu văn hóa và sức mạnh thể thao của quốc gia này.
Đội tuyển tham dự giải đấu Euro 2024
Euro 2024 sẽ quy tụ 24 đội tuyển hàng đầu từ châu Âu. Các đội tuyển này sẽ là những đại diện cho sự đa dạng văn hóa và phong cách chơi bóng đá trên khắp châu lục.
Các đội tuyển hàng đầu như Đức, Pháp, Tây Ban Nha, Bỉ, Italy, Anh và Hà Lan sẽ là những ứng viên nặng ký cho chức vô địch.
Trong khi đó, các đội tuyển nhỏ hơn như Iceland, Wales hay Áo cũng sẽ mang đến những bất ngờ và thách thức cho các đối thủ.
Các đội tuyển tham dự được chia thành 6 bảng đấu, gồm:
Bảng A: Đức, Scotland, Hungary và Thuỵ Sĩ
Bảng B: Tây Ban Nha, Croatia, Ý và Albania
Bảng C: Slovenia, Đan Mạch, Serbia và Anh
Bảng D: Ba Lan, Hà Lan, Áo và Pháp
Bảng E: Bỉ, Slovakia, Romania và Ukraina
Bảng F: Thổ Nhĩ Kỳ, Gruzia, Bồ Đào Nha và Cộng hoà Séc
국외선물의 개시 골드리치증권와 동참하세요.
골드리치증권는 오랜기간 고객님들과 함께 선물시장의 진로을 함께 걸어왔으며, 고객분들의 안전한 투자 및 건강한 이익률을 지향하여 계속해서 전력을 다하고 있습니다.
왜 20,000+명 이상이 골드리치와 투자하나요?
신속한 솔루션: 간단하며 빠른 프로세스를 갖추어 누구나 용이하게 사용할 수 있습니다.
보안 프로토콜: 국가기관에서 채택한 상위 등급의 보안체계을 채택하고 있습니다.
스마트 인증: 전체 거래내용은 암호처리 가공되어 본인 외에는 그 누구도 정보를 열람할 수 없습니다.
안전 수익률 공급: 리스크 요소를 감소시켜, 보다 더 확실한 수익률을 공개하며 이에 따른 리포트를 공유합니다.
24 / 7 실시간 고객센터: 연중무휴 24시간 즉각적인 서비스를 통해 회원분들을 전체 지원합니다.
함께하는 협력사: 골드리치는 공기업은 물론 금융기관들 및 다양한 협력사와 함께 여정을 했습니다.
국외선물이란?
다양한 정보를 확인하세요.
해외선물은 해외에서 거래되는 파생상품 중 하나로, 지정된 기반자산(예: 주식, 화폐, 상품 등)을 기초로 한 옵션계약 약정을 지칭합니다. 근본적으로 옵션은 명시된 기초자산을 미래의 어떤 시기에 일정 금액에 매수하거나 매도할 수 있는 자격을 제공합니다. 해외선물옵션은 이러한 옵션 계약이 외국 마켓에서 거래되는 것을 의미합니다.
외국선물은 크게 매수 옵션과 풋 옵션으로 구분됩니다. 콜 옵션은 명시된 기초자산을 미래에 정해진 가격에 사는 권리를 제공하는 반면, 매도 옵션은 지정된 기초자산을 미래에 정해진 가격에 매도할 수 있는 권리를 허락합니다.
옵션 계약에서는 미래의 특정 일자에 (만료일이라 칭하는) 일정 금액에 기초자산을 매수하거나 팔 수 있는 권리를 보유하고 있습니다. 이러한 금액을 실행 가격이라고 하며, 만료일에는 해당 권리를 실행할지 여부를 판단할 수 있습니다. 따라서 옵션 계약은 투자자에게 향후의 시세 변동에 대한 안전장치나 수익 창출의 기회를 부여합니다.
외국선물은 마켓 참가자들에게 다양한 운용 및 매매거래 기회를 열어주며, 외환, 상품, 주식 등 다양한 자산군에 대한 옵션 계약을 포함할 수 있습니다. 투자자는 매도 옵션을 통해 기초자산의 하향에 대한 보호를 받을 수 있고, 콜 옵션을 통해 상승장에서의 이익을 타깃팅할 수 있습니다.
국외선물 거래의 원리
행사 금액(Exercise Price): 해외선물에서 실행 금액은 옵션 계약에 따라 지정된 금액으로 계약됩니다. 종료일에 이 금액을 기준으로 옵션을 행사할 수 있습니다.
종료일(Expiration Date): 옵션 계약의 종료일은 옵션의 실행이 허용되지않는 마지막 날짜를 의미합니다. 이 일자 이후에는 옵션 계약이 소멸되며, 더 이상 거래할 수 없습니다.
매도 옵션(Put Option)과 매수 옵션(Call Option): 풋 옵션은 기초자산을 지정된 가격에 팔 수 있는 권리를 허락하며, 콜 옵션은 기초자산을 지정된 금액에 매수하는 권리를 허락합니다.
프리미엄(Premium): 국외선물 거래에서는 옵션 계약에 대한 옵션료을 지불해야 합니다. 이는 옵션 계약에 대한 비용으로, 마켓에서의 수요와 공급량에 따라 변화됩니다.
실행 방안(Exercise Strategy): 거래자는 만료일에 옵션을 실행할지 여부를 선택할 수 있습니다. 이는 시장 상황 및 투자 플랜에 따라 상이하며, 옵션 계약의 수익을 최대화하거나 손실을 감소하기 위해 선택됩니다.
마켓 위험요인(Market Risk): 외국선물 거래는 시장의 변화추이에 작용을 받습니다. 가격 변동이 기대치 못한 방향으로 일어날 경우 손해이 발생할 수 있으며, 이러한 시장 위험요인를 최소화하기 위해 거래자는 계획을 구축하고 투자를 계획해야 합니다.
골드리치증권와 함께하는 외국선물은 보장된 확신할 수 있는 운용을 위한 최적의 선택입니다. 고객님들의 투자를 지지하고 인도하기 위해 우리는 최선을 기울이고 있습니다. 공동으로 더 나은 내일를 지향하여 나아가요.
Euro
UEFA Euro 2024 Sân Chơi Bóng Đá Hấp Dẫn Nhất Của Châu Âu
Euro 2024 là sự kiện bóng đá lớn nhất của châu Âu, không chỉ là một giải đấu mà còn là một cơ hội để các quốc gia thể hiện tài năng, sự đoàn kết và tinh thần cạnh tranh.
Euro 2024 hứa hẹn sẽ mang lại những trận cầu đỉnh cao và kịch tính cho người hâm mộ trên khắp thế giới. Cùng tìm hiểu các thêm thông tin hấp dẫn về giải đấu này tại bài viết dưới đây, gồm:
Nước chủ nhà
Đội tuyển tham dự
Thể thức thi đấu
Thời gian diễn ra
Sân vận động
Euro 2024 sẽ được tổ chức tại Đức, một quốc gia có truyền thống vàng của bóng đá châu Âu.
Đức là một đất nước giàu có lịch sử bóng đá với nhiều thành công quốc tế và trong những năm gần đây, họ đã thể hiện sức mạnh của mình ở cả mặt trận quốc tế và câu lạc bộ.
Việc tổ chức Euro 2024 tại Đức không chỉ là một cơ hội để thể hiện năng lực tổ chức tuyệt vời mà còn là một dịp để giới thiệu văn hóa và sức mạnh thể thao của quốc gia này.
Đội tuyển tham dự giải đấu Euro 2024
Euro 2024 sẽ quy tụ 24 đội tuyển hàng đầu từ châu Âu. Các đội tuyển này sẽ là những đại diện cho sự đa dạng văn hóa và phong cách chơi bóng đá trên khắp châu lục.
Các đội tuyển hàng đầu như Đức, Pháp, Tây Ban Nha, Bỉ, Italy, Anh và Hà Lan sẽ là những ứng viên nặng ký cho chức vô địch.
Trong khi đó, các đội tuyển nhỏ hơn như Iceland, Wales hay Áo cũng sẽ mang đến những bất ngờ và thách thức cho các đối thủ.
Các đội tuyển tham dự được chia thành 6 bảng đấu, gồm:
Bảng A: Đức, Scotland, Hungary và Thuỵ Sĩ
Bảng B: Tây Ban Nha, Croatia, Ý và Albania
Bảng C: Slovenia, Đan Mạch, Serbia và Anh
Bảng D: Ba Lan, Hà Lan, Áo và Pháp
Bảng E: Bỉ, Slovakia, Romania và Ukraina
Bảng F: Thổ Nhĩ Kỳ, Gruzia, Bồ Đào Nha và Cộng hoà Séc
외국선물의 시작 골드리치와 동행하세요.
골드리치는 오랜기간 회원분들과 더불어 선물시장의 길을 함께 동행해왔으며, 고객분들의 확실한 투자 및 알찬 수익성을 향해 계속해서 최선을 다하고 있습니다.
무엇때문에 20,000+명 이상이 골드리치증권와 투자하나요?
빠른 서비스: 간단하며 빠른속도의 프로세스를 갖추어 모두 수월하게 사용할 수 있습니다.
보안 프로토콜: 국가당국에서 채택한 상위 등급의 보안을 적용하고 있습니다.
스마트 인가: 모든 거래정보은 부호화 가공되어 본인 외에는 그 누구도 내용을 확인할 수 없습니다.
확실한 수익률 공급: 위험 요소를 줄여, 보다 더 안전한 수익률을 공개하며 그에 따른 리포트를 발간합니다.
24 / 7 상시 고객상담: 365일 24시간 실시간 지원을 통해 투자자분들을 모두 지원합니다.
협력하는 협력사: 골드리치는 공기업은 물론 금융권들 및 많은 협력사와 함께 걸어오고.
외국선물이란?
다양한 정보를 확인하세요.
외국선물은 외국에서 거래되는 파생상품 중 하나로, 명시된 기반자산(예: 주식, 화폐, 상품 등)을 기초로 한 옵션계약 계약을 의미합니다. 근본적으로 옵션은 명시된 기초자산을 향후의 어떤 시기에 정해진 가격에 매수하거나 팔 수 있는 자격을 부여합니다. 외국선물옵션은 이러한 옵션 계약이 외국 마켓에서 거래되는 것을 의미합니다.
국외선물은 크게 콜 옵션과 풋 옵션으로 구분됩니다. 매수 옵션은 명시된 기초자산을 미래에 일정 금액에 매수하는 권리를 부여하는 반면, 매도 옵션은 지정된 기초자산을 미래에 정해진 금액에 팔 수 있는 권리를 부여합니다.
옵션 계약에서는 미래의 명시된 날짜에 (만료일이라 칭하는) 정해진 가격에 기초자산을 사거나 매도할 수 있는 권리를 보유하고 있습니다. 이러한 금액을 실행 가격이라고 하며, 만기일에는 해당 권리를 행사할지 여부를 선택할 수 있습니다. 따라서 옵션 계약은 거래자에게 향후의 가격 변화에 대한 안전장치나 이익 실현의 기회를 허락합니다.
외국선물은 시장 참가자들에게 다양한 투자 및 매매거래 기회를 마련, 환율, 상품, 주식 등 다양한 자산유형에 대한 옵션 계약을 망라할 수 있습니다. 거래자는 매도 옵션을 통해 기초자산의 낙폭에 대한 보호를 받을 수 있고, 매수 옵션을 통해 활황에서의 수익을 노릴 수 있습니다.
외국선물 거래의 원리
행사 가격(Exercise Price): 국외선물에서 행사 가격은 옵션 계약에 따라 특정한 가격으로 약정됩니다. 만기일에 이 가격을 기준으로 옵션을 실현할 수 있습니다.
만기일(Expiration Date): 옵션 계약의 만료일은 옵션의 행사가 허용되지않는 최종 날짜를 뜻합니다. 이 날짜 다음에는 옵션 계약이 종료되며, 더 이상 거래할 수 없습니다.
풋 옵션(Put Option)과 매수 옵션(Call Option): 매도 옵션은 기초자산을 명시된 금액에 팔 수 있는 권리를 허락하며, 콜 옵션은 기초자산을 특정 금액에 사는 권리를 허락합니다.
옵션료(Premium): 해외선물 거래에서는 옵션 계약에 대한 옵션료을 지불해야 합니다. 이는 옵션 계약에 대한 비용으로, 마켓에서의 수요와 공급에 따라 변동됩니다.
실행 전략(Exercise Strategy): 투자자는 만료일에 옵션을 실행할지 여부를 판단할 수 있습니다. 이는 시장 상황 및 거래 플랜에 따라 다르며, 옵션 계약의 이익을 최대화하거나 손실을 감소하기 위해 선택됩니다.
마켓 위험요인(Market Risk): 해외선물 거래는 마켓의 변화추이에 효과을 받습니다. 시세 변화이 기대치 못한 진로으로 일어날 경우 손해이 발생할 수 있으며, 이러한 시장 위험요인를 축소하기 위해 투자자는 전략을 구축하고 투자를 계획해야 합니다.
골드리치와 함께하는 외국선물은 확실한 확신할 수 있는 운용을 위한 최상의 옵션입니다. 투자자분들의 투자를 뒷받침하고 인도하기 위해 우리는 최선을 기울이고 있습니다. 함께 더 나은 내일를 지향하여 계속해나가세요.
ГГУ имени Ф.Скорины
해외선물의 출발 골드리치증권와 동행하세요.
골드리치는 장구한기간 고객님들과 더불어 선물시장의 행로을 공동으로 여정을했습니다, 투자자분들의 확실한 자금운용 및 건강한 이익률을 향해 항상 전력을 기울이고 있습니다.
어째서 20,000+명 이상이 골드리치와 함께할까요?
빠른 솔루션: 편리하고 빠른속도의 프로세스를 제공하여 누구나 간편하게 이용할 수 있습니다.
보안 프로토콜: 국가기관에서 적용한 상위 등급의 보안시스템을 도입하고 있습니다.
스마트 인증: 모든 거래정보은 부호화 처리되어 본인 외에는 그 누구도 내용을 접근할 수 없습니다.
확실한 이익률 마련: 위험 요소를 낮추어, 더욱 더 확실한 수익률을 공개하며 이에 따른 리포트를 제공합니다.
24 / 7 실시간 고객상담: 연중무휴 24시간 즉각적인 서비스를 통해 고객님들을 모두 서포트합니다.
함께하는 동반사: 골드리치증권는 공기업은 물론 금융권들 및 다양한 협력사와 함께 동행해오고.
국외선물이란?
다양한 정보를 확인하세요.
국외선물은 해외에서 거래되는 파생금융상품 중 하나로, 명시된 기초자산(예시: 주식, 화폐, 상품 등)을 바탕로 한 옵션계약 약정을 의미합니다. 기본적으로 옵션은 특정 기초자산을 미래의 어떤 시기에 정해진 금액에 매수하거나 매도할 수 있는 권리를 부여합니다. 국외선물옵션은 이러한 옵션 계약이 국외 시장에서 거래되는 것을 의미합니다.
외국선물은 크게 콜 옵션과 매도 옵션으로 분류됩니다. 콜 옵션은 특정 기초자산을 미래에 정해진 가격에 사는 권리를 부여하는 반면, 풋 옵션은 명시된 기초자산을 미래에 일정 금액에 매도할 수 있는 권리를 허락합니다.
옵션 계약에서는 미래의 특정 날짜에 (만기일이라 불리는) 일정 가격에 기초자산을 매수하거나 매도할 수 있는 권리를 보유하고 있습니다. 이러한 가격을 행사 가격이라고 하며, 만료일에는 해당 권리를 실행할지 여부를 선택할 수 있습니다. 따라서 옵션 계약은 투자자에게 향후의 가격 변화에 대한 보호나 수익 실현의 기회를 부여합니다.
해외선물은 마켓 참가자들에게 다양한 투자 및 매매거래 기회를 제공, 환율, 상품, 주식 등 다양한 자산군에 대한 옵션 계약을 포함할 수 있습니다. 투자자는 풋 옵션을 통해 기초자산의 하향에 대한 보호를 받을 수 있고, 매수 옵션을 통해 상승장에서의 이익을 타깃팅할 수 있습니다.
해외선물 거래의 원리
실행 가격(Exercise Price): 국외선물에서 실행 금액은 옵션 계약에 따라 지정된 금액으로 약정됩니다. 만료일에 이 가격을 기준으로 옵션을 실현할 수 있습니다.
종료일(Expiration Date): 옵션 계약의 종료일은 옵션의 실행이 불가능한 최종 날짜를 지칭합니다. 이 날짜 다음에는 옵션 계약이 소멸되며, 더 이상 거래할 수 없습니다.
풋 옵션(Put Option)과 매수 옵션(Call Option): 매도 옵션은 기초자산을 지정된 가격에 팔 수 있는 권리를 허락하며, 매수 옵션은 기초자산을 명시된 가격에 사는 권리를 허락합니다.
계약료(Premium): 국외선물 거래에서는 옵션 계약에 대한 옵션료을 납부해야 합니다. 이는 옵션 계약에 대한 비용으로, 시장에서의 수요와 공급에 따라 변화됩니다.
행사 전략(Exercise Strategy): 투자자는 만료일에 옵션을 행사할지 여부를 결정할 수 있습니다. 이는 마켓 상황 및 투자 플랜에 따라 차이가있으며, 옵션 계약의 수익을 최대화하거나 손실을 감소하기 위해 판단됩니다.
마켓 위험요인(Market Risk): 외국선물 거래는 마켓의 변동성에 작용을 받습니다. 가격 변동이 예상치 못한 진로으로 발생할 경우 손해이 발생할 수 있으며, 이러한 마켓 위험요인를 감소하기 위해 거래자는 계획을 구축하고 투자를 설계해야 합니다.
골드리치증권와 동반하는 해외선물은 확실한 확신할 수 있는 투자를 위한 가장좋은 옵션입니다. 투자자분들의 투자를 뒷받침하고 가이드하기 위해 우리는 전력을 기울이고 있습니다. 함께 더 나은 미래를 지향하여 나아가요.
ทดลองเล่นสล็อต
kw bocor88
k8 カジノ パチンコ 遊び方
このトピックについてこんなに詳しく知れるとは思いませんでした。素晴らしいです!
raja118
link kantor bola
Gerakl24: Опытная Смена Основания, Венцов, Полов и Перенос Зданий
Компания Gerakl24 занимается на предоставлении всесторонних сервисов по смене основания, венцов, покрытий и перемещению зданий в городе Красноярск и за его пределами. Наша команда профессиональных специалистов гарантирует высокое качество выполнения различных типов реставрационных работ, будь то из дерева, каркасные, кирпичные или из бетона дома.
Плюсы сотрудничества с Геракл24
Профессионализм и опыт:
Все работы проводятся лишь опытными мастерами, имеющими большой стаж в направлении строительства и реставрации домов. Наши специалисты знают свое дело и выполняют задачи с высочайшей точностью и вниманием к деталям.
Комплексный подход:
Мы предоставляем все виды работ по ремонту и ремонту домов:
Замена фундамента: замена и укрепление фундамента, что позволяет продлить срок службы вашего строения и избежать проблем, связанные с оседанием и деформацией строения.
Замена венцов: реставрация нижних венцов из дерева, которые наиболее часто подвергаются гниению и разрушению.
Замена полов: установка новых полов, что кардинально улучшает внешний облик и практическую полезность.
Перемещение зданий: качественный и безопасный перенос строений на новые места, что обеспечивает сохранение строения и избежать дополнительных затрат на создание нового.
Работа с любыми типами домов:
Древесные строения: реставрация и усиление деревянных элементов, обработка от гниения и насекомых.
Каркасные строения: усиление каркасных конструкций и замена поврежденных элементов.
Кирпичные строения: ремонт кирпичных стен и укрепление конструкций.
Бетонные дома: реставрация и усиление бетонных элементов, ремонт трещин и дефектов.
Качество и прочность:
Мы используем лишь качественные материалы и новейшее оборудование, что обеспечивает долгий срок службы и надежность всех выполненных работ. Все проекты проходят тщательную проверку качества на каждом этапе выполнения.
Личный подход:
Каждому клиенту мы предлагаем индивидуальные решения, с учетом всех особенностей и пожеланий. Мы стараемся, чтобы итог нашей работы полностью соответствовал вашим запросам и желаниям.
Зачем обращаться в Геракл24?
Работая с нами, вы найдете надежного партнера, который берет на себя все заботы по восстановлению и ремонту вашего здания. Мы обеспечиваем выполнение всех проектов в сроки, установленные договором и с в соответствии с нормами и стандартами. Связавшись с Геракл24, вы можете быть спокойны, что ваше строение в надежных руках.
Мы готовы предоставить консультацию и ответить на ваши вопросы. Звоните нам, чтобы обсудить детали вашего проекта и получить больше информации о наших услугах. Мы сохраним и улучшим ваш дом, сделав его уютным и безопасным для долгого проживания.
Gerakl24 – ваш партнер по реставрации и ремонту домов в Красноярске и окрестностях.
Telegrass
הפלטפורמה היא תוכנה פופולרית במדינה לרכישת קנאביס באופן מקוון. היא נותנת ממשק משתמש נוח ומאובטח לרכישה וקבלת משלוחים מ מוצרי מריחואנה שונים. במאמר זו נסקור עם העיקרון שמאחורי האפליקציה, כיצד זו פועלת ומה היתרונות מ השימוש בה.
מה זו האפליקציה?
הפלטפורמה מהווה דרך לקנייה של מריחואנה דרך היישומון טלגרם. היא נשענת מעל ערוצי תקשורת וקבוצות טלגראם ספציפיות הנקראות ״כיווני טלגראס״, שבהם ניתן להרכיב מגוון פריטי צמח הקנאביס ולקבלת אותם ישירות למשלוח. הערוצים האלה מאורגנים על פי אזורים גאוגרפיים, במטרה להקל על קבלתם של המשלוחים.
כיצד זאת פועל?
התהליך פשוט יחסית. ראשית, יש להצטרף לערוץ הטלגראס הרלוונטי לאזור המחיה. שם אפשר לעיין בתפריטים של המוצרים השונים ולהזמין עם הפריטים המבוקשים. לאחר השלמת ההרכבה וסגירת התשלום, השליח יגיע בכתובת שנרשמה ועמו החבילה המוזמנת.
מרבית ערוצי הטלגראס מציעים טווח נרחב של פריטים – זנים של צמח הקנאביס, ממתקים, שתייה ועוד. בנוסף, אפשר לראות חוות דעת של לקוחות שעברו לגבי רמת המוצרים והשרות.
מעלות השימוש בטלגראס
יתרון עיקרי של הפלטפורמה הוא הנוחיות והדיסקרטיות. ההזמנה והתהליך מתבצעות ממרחק מכל מיקום, ללא צורך במפגש פנים אל פנים. בנוסף, האפליקציה מאובטחת ביסודיות ומבטיחה סודיות גבוהה.
נוסף אל זאת, עלויות המוצרים בפלטפורמה נוטים לבוא זולים, והשילוחים מגיעים במהירות ובמסירות רבה. קיים גם מוקד תמיכה פתוח לכל שאלה או בעיית.
סיכום
הפלטפורמה הווה דרך מקורית ויעילה לקנות מוצרי קנאביס בישראל. היא משלבת בין הנוחות הדיגיטלית של היישומון הפופולרי, לבין הזריזות והפרטיות מ דרך השילוח הישירות. ככל שהביקוש לצמח הקנאביס גובר, פלטפורמות כמו זו צפויות להמשיך ולצמוח.
Bản cài đặt B29 IOS – Giải pháp vượt trội cho các tín đồ iOS
Trong thế giới công nghệ đầy sôi động hiện nay, trải nghiệm người dùng luôn là yếu tố then chốt. Với sự ra đời của Bản cài đặt B29 IOS, người dùng sẽ được hưởng trọn vẹn những tính năng ưu việt, mang đến sự hài lòng tuyệt đối. Hãy cùng khám phá những ưu điểm vượt trội của bản cài đặt này!
Tính bảo mật tối đa
Bản cài đặt B29 IOS được thiết kế với mục tiêu đảm bảo an toàn dữ liệu tuyệt đối cho người dùng. Nhờ hệ thống mã hóa hiện đại, thông tin cá nhân và dữ liệu nhạy cảm của bạn luôn được bảo vệ an toàn khỏi những kẻ xâm nhập trái phép.
Trải nghiệm người dùng đỉnh cao
Giao diện thân thiện, đơn giản nhưng không kém phần hiện đại, B29 IOS mang đến cho người dùng trải nghiệm duyệt web, truy cập ứng dụng và sử dụng thiết bị một cách trôi chảy, mượt mà. Các tính năng thông minh được tối ưu hóa, giúp nâng cao hiệu suất và tiết kiệm pin đáng kể.
Tính tương thích rộng rãi
Bản cài đặt B29 IOS được phát triển với mục tiêu tương thích với mọi thiết bị iOS từ các dòng iPhone, iPad cho đến iPod Touch. Dù là người dùng mới hay lâu năm của hệ điều hành iOS, B29 đều mang đến sự hài lòng tuyệt đối.
Quá trình cài đặt đơn giản
Với những hướng dẫn chi tiết, việc cài đặt B29 IOS trở nên nhanh chóng và dễ dàng. Chỉ với vài thao tác đơn giản, bạn đã có thể trải nghiệm ngay tất cả những tính năng tuyệt vời mà bản cài đặt này mang lại.
Bản cài đặt B29 IOS không chỉ là một bản cài đặt đơn thuần, mà còn là giải pháp công nghệ hiện đại, nâng tầm trải nghiệm người dùng lên một tầm cao mới. Hãy trở thành một phần của cộng đồng sử dụng B29 IOS để khám phá những tiện ích tuyệt vời mà nó có thể mang lại!
魔法少女まどか☆マギカ (2発1)(V2.2)
素敵な記事をありがとうございます。いつも楽しみにしています。
Как защитить свои личные данные: страхуйтесь от утечек информации в интернете. Сегодня защита личных данных становится всё более важной задачей. Одним из наиболее часто встречающихся способов утечки личной информации является слив «сит фраз» в интернете. Что такое сит фразы и как защититься от их утечки? Что такое «сит фразы»? «Сит фразы» — это комбинации слов или фраз, которые часто используются для доступа к различным онлайн-аккаунтам. Эти фразы могут включать в себя имя пользователя, пароль или дополнительные конфиденциальные данные. Киберпреступники могут пытаться получить доступ к вашим аккаунтам, используя этих сит фраз. Как защитить свои личные данные? Используйте сложные пароли. Избегайте использования очевидных паролей, которые просто угадать. Лучше всего использовать комбинацию букв, цифр и символов. Используйте уникальные пароли для всего аккаунта. Не применяйте один и тот же пароль для разных сервисов. Используйте двухступенчатую аутентификацию (2FA). Это прибавляет дополнительный уровень безопасности, требуя подтверждение входа на ваш аккаунт по другое устройство или метод. Будьте осторожны с онлайн-сервисами. Не доверяйте свою информацию ненадежным сайтам и сервисам. Обновляйте программное обеспечение. Установите обновления для вашего операционной системы и программ, чтобы предохранить свои данные от вредоносного ПО. Вывод Слив сит фраз в интернете может повлечь за собой серьезным последствиям, таким вроде кража личной информации и финансовых потерь. Чтобы обезопасить себя, следует принимать меры предосторожности и использовать надежные методы для хранения и управления своими личными данными в сети
טלגראס היא אפליקציה רווחת במדינה לקנייה של מריחואנה בצורה מקוון. זו נותנת ממשק משתמש פשוט לשימוש ובטוח לקנייה ולקבלת שילוחים מ מוצרי צמח הקנאביס מרובים. בכתבה זה נבחן את העיקרון שמאחורי הפלטפורמה, איך זו פועלת ומה היתרים של השימוש בזו.
מהי הפלטפורמה?
הפלטפורמה הינה אמצעי לקנייה של קנאביס דרך האפליקציה טלגראם. זו נשענת מעל ערוצי תקשורת וקבוצות טלגרם ייעודיות הקרויות ״כיווני טלגראס״, שם אפשר להרכיב מגוון מוצרי מריחואנה ולקבלת אלו ישירות למשלוח. הערוצים אלו מאורגנים על פי איזורים גאוגרפיים, כדי לשפר את קבלת השילוחים.
איך זה פועל?
התהליך פשוט למדי. קודם כל, צריך להצטרף לערוץ טלגראס הרלוונטי לאזור המגורים. שם אפשר לעיין בתפריטים של הפריטים המגוונים ולהרכיב את המוצרים הרצויים. לאחר ביצוע ההזמנה וסיום התשלום, השליח יגיע לכתובת שנרשמה עם החבילה שהוזמן.
מרבית ערוצי הטלגראס מספקים טווח נרחב מ מוצרים – זנים של מריחואנה, ממתקים, שתייה ועוד. כמו כן, אפשר למצוא חוות דעת מ צרכנים קודמים על איכות המוצרים והשירות.
יתרונות השימוש בטלגראס
יתרון עיקרי של האפליקציה הוא הנוחות והדיסקרטיות. ההרכבה וההכנות מתקיימים מרחוק מאיזשהו מקום, ללא צורך בהתכנסות פיזי. בנוסף, הפלטפורמה מוגנת היטב ומבטיחה סודיות גבוהה.
נוסף על כך, מחירי הפריטים בפלטפורמה נוטים להיות זולים, והמשלוחים מגיעים במהירות ובמסירות רבה. קיים גם מוקד תמיכה פתוח לכל שאלה או בעיית.
לסיכום
טלגראס היא שיטה מקורית ויעילה לרכוש מוצרי מריחואנה בארץ. היא משלבת את הנוחיות הטכנולוגית של היישומון הפופולרי, ועם הזריזות והדיסקרטיות מ דרך המשלוח הישירות. ככל שהביקוש לקנאביס גובר, אפליקציות כמו זו צפויות להמשיך ולהתפתח.
отмывание usdt
Как сберечь свои данные: берегитесь утечек информации в интернете. Сегодня обеспечение безопасности информации становится всё более важной задачей. Одним из наиболее часто встречающихся способов утечки личной информации является слив «сит фраз» в интернете. Что такое сит фразы и как предохранить себя от их утечки? Что такое «сит фразы»? «Сит фразы» — это смеси слов или фраз, которые постоянно используются для входа к различным онлайн-аккаунтам. Эти фразы могут включать в себя имя пользователя, пароль или дополнительные конфиденциальные данные. Киберпреступники могут пытаться получить доступ к вашим аккаунтам, при помощи этих сит фраз. Как охранить свои личные данные? Используйте непростые пароли. Избегайте использования простых паролей, которые просто угадать. Лучше всего использовать комбинацию букв, цифр и символов. Используйте уникальные пароли для всего аккаунта. Не используйте один и тот же пароль для разных сервисов. Используйте двухэтапную аутентификацию (2FA). Это прибавляет дополнительный уровень безопасности, требуя подтверждение входа на ваш аккаунт через другое устройство или метод. Будьте осторожны с онлайн-сервисами. Не доверяйте личную информацию ненадежным сайтам и сервисам. Обновляйте программное обеспечение. Установите обновления для вашего операционной системы и программ, чтобы сохранить свои данные от вредоносного ПО. Вывод Слив сит фраз в интернете может спровоцировать серьезным последствиям, таким вроде кража личной информации и финансовых потерь. Чтобы защитить себя, следует принимать меры предосторожности и использовать надежные методы для хранения и управления своими личными данными в сети
Проверить транзакцию usdt trc20
Защитите ваши USDT: Проверьте операцию TRC20 до пересылкой
Цифровые валюты, такие как USDT (Tether) на распределенном реестре TRON (TRC20), делаются всё всё более распространенными в области области децентрализованных финансов. Тем не менее совместно с повышением популярности повышается и опасность промахов или обмана при транзакции средств. Как раз по этой причине важно проверять операцию USDT TRC20 перед ее отправкой.
Ошибка во время вводе данных адреса адресата иль отправка по неправильный адрес получателя может повлечь к невозвратной утрате ваших USDT. Мошенники тоже могут пытаться одурачить тебя, отправляя ложные адреса получателей для перевода. Потеря цифровой валюты по причине таких ошибок может обернуться значительными финансовыми убытками.
К радости, имеются профильные службы, дающие возможность проверить перевод USDT TRC20 перед её отправкой. Некий из таких сервисов дает возможность наблюдать а также анализировать переводы в блокчейне TRON.
В этом обслуживании вы можете вводить адрес получателя получателя а также получать обстоятельную сведения об нем, включая в том числе архив переводов, баланс а также состояние аккаунта. Это поможет определить, является ли адрес получателя истинным а также надежным для отправки средств.
Прочие сервисы также предоставляют похожие опции для проверки транзакций USDT TRC20. Некоторые кошельки по крипто обладают встроенные функции по контроля адресов а также транзакций.
Не пропускайте удостоверением операции USDT TRC20 до ее отсылкой. Небольшая осмотрительность может сберечь для вас множество средств а также предотвратить утрату ваших дорогих крипто ресурсов. Задействуйте заслуживающие доверия сервисы с целью обеспечения надежности ваших операций и целостности ваших USDT на распределенном реестре TRON.
В процессе взаимодействии с криптовалютой USDT на распределенном реестре TRON (TRC20) крайне существенно не просто проверять реквизиты получателя перед отправкой денег, а также и периодически отслеживать баланс личного цифрового кошелька, а также источники входящих переводов. Это позволит вовремя обнаружить любые нежелательные транзакции а также не допустить возможные издержки.
Прежде всего, необходимо проверить на точности отображаемого остатка USDT TRC20 на вашем криптокошельке. Рекомендуется сверять показания с сведениями открытых блокчейн-обозревателей, для того чтобы исключить шанс взлома либо компрометации самого крипто-кошелька.
Однако лишь отслеживания остатка мало. Чрезвычайно существенно анализировать журнал входящих переводов и их происхождение. Если вы выявите переводы USDT с анонимных или сомнительных реквизитов, сразу же остановите данные финансы. Имеется опасность, что эти монеты стали получены преступным путем и в будущем могут быть конфискованы регулирующими органами.
Наш платформа дает возможности для углубленного исследования поступающих USDT TRC20 транзакций касательно их законности и отсутствия связи с криминальной активностью. Мы поможем вам безопасно работать с этим популярным стейблкоином.
Дополнительно нужно периодически переводить USDT TRC20 на проверенные некастодиальные крипто-кошельки под собственным полным присмотром. Содержание монет на сторонних площадках всегда связано с рисками взломов а также потери денег из-за технических ошибок либо банкротства платформы.
Следуйте базовые меры безопасности, будьте внимательны и своевременно контролируйте остаток и источники поступлений USDT TRC20 кошелька. Это позволит защитить ваши цифровые активы от незаконного завладения и потенциальных юридических проблем в будущем.
Проверить перевод usdt trc20
Значимость проверки транзакции USDT TRC-20
Платежи USDT в рамках сети TRC20 набирают повышенную активность, однако важно являться особенно аккуратными в ходе таких получении.
Данный категория транзакций часто привлекается с целью очищения активов, полученных криминальным способом.
Ключевой опасностей приобретения USDT по сети TRC20 – состоит в том, что такие платежи вероятно будут приобретены посредством разнообразных методов кражи, в том числе хищения конфиденциальной информации, принуждение, взломы наряду с иные криминальные действия. Обрабатывая данные переводы, пользователь автоматически выглядите соучастником нелегальной операций.
Поэтому особенно обязательно глубоко исследовать источник всех приходящего платежа с использованием USDT TRC20. Обязательно интересоваться с перевододателя данные о чистоте денежных средств, при незначительных вопросах – воздерживаться данные переводов.
Осознавайте, в ситуации, когда при выявления криминальных генезисов активов, клиент скорее всего будете привлечены с взысканиям совместно рядом с перевододателем. В связи с этим предпочтительнее подстраховаться как и скрупулезно анализировать каждый платеж, нацело ставить под угрозу репутационной репутацией наряду с столкнуться со серьезные правовые неприятности.
Обеспечение аккуратности при взаимодействии с использованием USDT TRC-20 – представляет собой ключ личной материальной сохранности как и ограждение от нелегальные операции. Будьте осторожны а также неизменно исследуйте происхождение виртуальных валютных денежных средств.
проверить адрес usdt trc20
Название: Обязательно проверяйте адрес адресата во время переводе USDT TRC20
При взаимодействии со цифровыми валютами, особенно со USDT на блокчейне TRON (TRC20), чрезвычайно нужно выказывать осмотрительность и аккуратность. Одна среди наиболее частых оплошностей, которую делают пользователи – посылка средств на ошибочный адрес. Чтобы предотвратить лишение своих USDT, необходимо всегда внимательно контролировать адресе адресата перед передачей перевода.
Цифровые адреса представляют собой протяженные совокупности букв а также цифр, к примеру, TRX9QahiFUYfHffieZThuzHbkndWvvfzThB8U. Даже незначительная ошибка либо оплошность при копирования адреса кошелька может привести к тому, чтобы твои крипто станут безвозвратно утрачены, так как они окажутся в неподконтрольный тобой криптокошелек.
Существуют многообразные способы проверки адресов кошельков USDT TRC20:
1. Визуальная проверка. Тщательно сопоставьте адрес в твоём кошельке с адресом кошелька реципиента. При малейшем расхождении – воздержитесь от перевод.
2. Применение интернет-служб проверки.
3. Дублирующая проверка с адресатом. Попросите реципиенту подтвердить корректность адреса кошелька перед отправкой транзакции.
4. Тестовый перевод. В случае значительной величине операции, можно сначала послать малое объем USDT с целью контроля адреса кошелька.
Также предлагается держать криптовалюты на собственных кошельках, но не на биржах или сторонних службах, чтобы обладать полный контроль по отношению к собственными ресурсами.
Не игнорируйте проверкой адресов при деятельности со USDT TRC20. Эта несложная процедура превенции поможет защитить ваши деньги против нежелательной лишения. Имейте в виду, чтобы в мире крипто транзакции необратимы, а переданные цифровые деньги по ошибочный адрес кошелька вернуть фактически нельзя. Будьте внимательны а также аккуратны, чтобы защитить свои инвестиции.
b29
Bản cài đặt B29 IOS – Giải pháp vượt trội cho các tín đồ iOS
Trong thế giới công nghệ đầy sôi động hiện nay, trải nghiệm người dùng luôn là yếu tố then chốt. Với sự ra đời của Bản cài đặt B29 IOS, người dùng sẽ được hưởng trọn vẹn những tính năng ưu việt, mang đến sự hài lòng tuyệt đối. Hãy cùng khám phá những ưu điểm vượt trội của bản cài đặt này!
Tính bảo mật tối đa
Bản cài đặt B29 IOS được thiết kế với mục tiêu đảm bảo an toàn dữ liệu tuyệt đối cho người dùng. Nhờ hệ thống mã hóa hiện đại, thông tin cá nhân và dữ liệu nhạy cảm của bạn luôn được bảo vệ an toàn khỏi những kẻ xâm nhập trái phép.
Trải nghiệm người dùng đỉnh cao
Giao diện thân thiện, đơn giản nhưng không kém phần hiện đại, B29 IOS mang đến cho người dùng trải nghiệm duyệt web, truy cập ứng dụng và sử dụng thiết bị một cách trôi chảy, mượt mà. Các tính năng thông minh được tối ưu hóa, giúp nâng cao hiệu suất và tiết kiệm pin đáng kể.
Tính tương thích rộng rãi
Bản cài đặt B29 IOS được phát triển với mục tiêu tương thích với mọi thiết bị iOS từ các dòng iPhone, iPad cho đến iPod Touch. Dù là người dùng mới hay lâu năm của hệ điều hành iOS, B29 đều mang đến sự hài lòng tuyệt đối.
Quá trình cài đặt đơn giản
Với những hướng dẫn chi tiết, việc cài đặt B29 IOS trở nên nhanh chóng và dễ dàng. Chỉ với vài thao tác đơn giản, bạn đã có thể trải nghiệm ngay tất cả những tính năng tuyệt vời mà bản cài đặt này mang lại.
Bản cài đặt B29 IOS không chỉ là một bản cài đặt đơn thuần, mà còn là giải pháp công nghệ hiện đại, nâng tầm trải nghiệm người dùng lên một tầm cao mới. Hãy trở thành một phần của cộng đồng sử dụng B29 IOS để khám phá những tiện ích tuyệt vời mà nó có thể mang lại!
?And indeed, she was absolutely right. Her jeans of the largest size barely came together at the seams. The oversized T-shirt was clinging to her. And two more plump ones were peeking out from under her chin. The woman was somewhat embarrassed, as if she herself did not believe her own words:
— So from this day on, we’re taking normal food. Otherwise, we’ve flooded everything with fat to the point of impossibility, how much more can there be. Let’s think about our health.
Пару мгновений и семья уже была в овощном отделе. Приходилось им там быть максимально редко – о существовании некоторых овощей и фруктов люди не знали вообще, от слова совсем. Смотря на все, как на диковинку, настало время выбора:
—Ну, что ж…. Возьмем помидоров, огурцов, а вот и яблоки, кабачков тоже можно…
Таня рассуждала сама по себе и не советовалась с голодными глазами мужа, ловко перебирая овощи и откладывая самые лучшие в полиэтиленовый пакет. Маленькая девочка внимательно осматривала апельсины – такого она еще никогда не видела, а тем более, не ела:
—Может, потом еще чего-нибудь нормального возьмем? Колбаски там, сосисок. Ты если хочешь, худей. А мы нормально будем жить. Да, доча?
человек полностью не предполагал из уст собственной жены Татьяны. Среди данной семье фигура плоти абсолютно была иной в противовес нормативной также общепризнанной – страдать предожирением абсолютная стандарт.
Замена венцов красноярск
Геракл24: Опытная Замена Основания, Венцов, Настилов и Перенос Зданий
Компания Gerakl24 занимается на оказании полных сервисов по смене фундамента, венцов, настилов и перемещению домов в населённом пункте Красноярском регионе и в окрестностях. Наша группа квалифицированных мастеров гарантирует превосходное качество выполнения всех видов реставрационных работ, будь то древесные, каркасного типа, кирпичные или бетонные конструкции здания.
Достоинства работы с Gerakl24
Профессионализм и опыт:
Весь процесс осуществляются лишь профессиональными специалистами, с обладанием многолетний опыт в области создания и ремонта зданий. Наши сотрудники эксперты в своей области и реализуют задачи с высочайшей точностью и вниманием к деталям.
Полный спектр услуг:
Мы предлагаем полный спектр услуг по восстановлению и восстановлению зданий:
Смена основания: замена и укрепление фундамента, что гарантирует долговечность вашего здания и устранить проблемы, вызванные оседанием и деформацией.
Реставрация венцов: замена нижних венцов деревянных домов, которые наиболее часто подвергаются гниению и разрушению.
Смена настилов: замена старых полов, что значительно улучшает внешний вид и функциональность помещения.
Передвижение домов: безопасное и качественное передвижение домов на новые места, что обеспечивает сохранение строения и предотвращает лишние расходы на создание нового.
Работа с различными типами строений:
Деревянные дома: восстановление и укрепление деревянных конструкций, защита от гниения и вредителей.
Каркасные дома: реставрация каркасов и смена поврежденных частей.
Кирпичные дома: восстановление кирпичной кладки и укрепление стен.
Дома из бетона: реставрация и усиление бетонных элементов, исправление трещин и разрушений.
Качество и прочность:
Мы работаем с только высококачественные материалы и современное оборудование, что гарантирует долгий срок службы и надежность всех работ. Каждый наш проект проходят строгий контроль качества на каждом этапе выполнения.
Персонализированный подход:
Для каждого клиента мы предлагаем подходящие решения, учитывающие ваши требования и желания. Мы стараемся, чтобы результат нашей работы соответствовал вашим ожиданиям и требованиям.
Зачем обращаться в Геракл24?
Сотрудничая с нами, вы найдете надежного партнера, который возьмет на себя все заботы по восстановлению и ремонту вашего здания. Мы обещаем выполнение всех работ в сроки, оговоренные заранее и с в соответствии с нормами и стандартами. Обратившись в Геракл24, вы можете не сомневаться, что ваш дом в надежных руках.
Мы готовы предоставить консультацию и ответить на ваши вопросы. Звоните нам, чтобы обсудить ваш проект и получить больше информации о наших услугах. Мы обеспечим сохранение и улучшение вашего дома, сделав его уютным и безопасным для долгого проживания.
Gerakl24 – ваш надежный партнер в реставрации и ремонте домов в Красноярске и за его пределами.
bingo Masamune senkyoku
情報がとても整理されていて、理解しやすかったです。
If you are going for most excellent contents like I do, simply visit this site daily because it gives quality contents, thanks
טלגראס כיוונים
זכו הבאים לאתר המידע והסיוע הרשמי והמוסמך של טלגרם אופקים! בנקודה זו אפשר לאתר ולמצוא את כל המידע והמסמכים העדכני והמעודכן ביותר זמין בנוגע ל פלטפורמת טלגראס וצורות לשימוש בה כראוי.
מיהו טלגראס נתיבים?
טלגראס נתיבים מציינת תשתית מבוססת טלגראס המשמשת ל להפצה ויישום של קנבי וקנביס במדינה. דרך המסרים והקבוצות בטלגרם, פעילים רשאים לרכוש ולהשיג מוצרי קנאביס בדרך פשוט ומיידי.
באיזה דרך להיכנס בטלגרם?
על מנת להתחבר בפעילות בטלגרם, עליכם להתחבר ל למקומות ולמסגרות המומלצים. בנקודה זו באתר ניתן למצוא סיכום של צירים למקומות מתפקדים ומהימנים. במקביל לכך, ניתן להיכנס בתהליך האספקה והקבלה מסביב אספקת הקנבי.
מידע והסברים
בפורטל המסוים ניתן למצוא אוסף של הוראות והסברים ממצים בעניין היישום בטלגרם, לרבות:
– הצטרפות למקומות מאומתים
– תהליך הרכישה
– הגנה ואבטחה בהתנהלות בטלגראס כיוונים
– והרבה נתונים נוסף
לינקים רצויים
לגבי נושא זה לינקים למקומות ולפורומים מומלצים בפלטפורמת טלגרם:
– פורום הנתונים והעדכונים המאושר
– חוג העזרה והטיפול למשתמשים
– ערוץ לאספקת מוצרי קנבי מאומתים
– מבחר חנויות קנאביס אמינות
מערך מכבדים את כל המצטרפים על הפעילות שלכם לאזור המידע והידע של טלגרם מסלולים ומתקווים לקהל חווית שירות טובה ומובטחת!
Замена венцов красноярск
Геракл24: Квалифицированная Реставрация Фундамента, Венцов, Настилов и Перенос Домов
Компания Геракл24 специализируется на оказании всесторонних услуг по смене фундамента, венцов, покрытий и перемещению строений в месте Красноярске и за пределами города. Наш коллектив профессиональных мастеров гарантирует превосходное качество реализации всех типов восстановительных работ, будь то из дерева, каркасного типа, из кирпича или бетонные дома.
Преимущества услуг Геракл24
Профессионализм и опыт:
Весь процесс выполняются лишь профессиональными мастерами, с многолетним большой опыт в сфере возведения и реставрации домов. Наши сотрудники профессионалы в своем деле и выполняют работу с максимальной точностью и учетом всех деталей.
Всесторонний подход:
Мы осуществляем разнообразные услуги по реставрации и восстановлению зданий:
Замена фундамента: замена и укрепление фундамента, что позволяет продлить срок службы вашего строения и предотвратить проблемы, вызванные оседанием и деформацией.
Смена венцов: реставрация нижних венцов из дерева, которые обычно гниют и разрушаются.
Смена настилов: установка новых полов, что кардинально улучшает визуальное восприятие и функциональность помещения.
Передвижение домов: качественный и безопасный перенос строений на другие участки, что обеспечивает сохранение строения и предотвращает лишние расходы на создание нового.
Работа с любыми типами домов:
Деревянные дома: восстановление и укрепление деревянных конструкций, обработка от гниения и насекомых.
Дома с каркасом: укрепление каркасов и замена поврежденных элементов.
Кирпичные строения: восстановление кирпичной кладки и усиление стен.
Дома из бетона: ремонт и укрепление бетонных конструкций, устранение трещин и повреждений.
Надежность и долговечность:
Мы используем только проверенные материалы и передовые технологии, что гарантирует долговечность и прочность всех выполненных задач. Все наши проекты проходят строгий контроль качества на всех этапах выполнения.
Персонализированный подход:
Мы предлагаем каждому клиенту персонализированные решения, с учетом всех особенностей и пожеланий. Мы стремимся к тому, чтобы конечный результат соответствовал вашим запросам и желаниям.
Почему выбирают Геракл24?
Обратившись к нам, вы получаете надежного партнера, который возьмет на себя все заботы по ремонту и реконструкции вашего строения. Мы обеспечиваем выполнение всех работ в установленные сроки и с соблюдением всех строительных норм и стандартов. Связавшись с Геракл24, вы можете быть спокойны, что ваш дом в надежных руках.
Мы всегда готовы проконсультировать и дать ответы на все вопросы. Звоните нам, чтобы обсудить детали вашего проекта и узнать больше о наших услугах. Мы обеспечим сохранение и улучшение вашего дома, обеспечив его безопасность и комфорт на долгие годы.
Gerakl24 – ваш надежный партнер в реставрации и ремонте домов в Красноярске и за его пределами.
Психология в рассказах, истории из жизни.
tuan88
Hi there! I could have sworn I’ve been to this website before but after browsing through a few of the posts I realized it’s new to me. Anyways, I’m definitely pleased I found it and I’ll be bookmarking it and checking back frequently!
Buy Cannabis in Israel: A Detailed Overview to Purchasing Weed in the Country
In recent years, the expression “Buy Weed Israel” has turned into a byword with an innovative, easy, and uncomplicated approach of acquiring cannabis in Israel. Leveraging applications like the Telegram platform, users can quickly and easily navigate through an extensive range of options and countless deals from different providers across the country. All that prevents you from accessing the weed market in the country to discover new ways to purchase your weed is downloading a simple, safe platform for discreet communication.
Definition of Buy Weed Israel?
The phrase “Buy Weed Israel” no more relates exclusively to the automated system that joined customers with dealers run by the operator. Following its closure, the phrase has changed into a general reference for arranging a link with a cannabis supplier. Through tools like Telegram, one can find numerous platforms and groups classified by the follower count each provider’s group or group has. Providers vie for the focus and business of potential customers, leading to a varied array of choices offered at any point.
Ways to Find Providers Through Buy Weed Israel
By inputting the phrase “Buy Weed Israel” in the Telegram’s search field, you’ll find an endless number of communities and networks. The amount of followers on these channels does not automatically verify the supplier’s trustworthiness or suggest their offerings. To avoid fraud or poor-quality goods, it’s advisable to buy exclusively from recommended and established providers from which you’ve purchased before or who have been recommended by peers or trusted sources.
Trusted Buy Weed Israel Groups
We have assembled a “Top 10” ranking of recommended platforms and communities on the Telegram app for buying cannabis in Israel. All providers have been vetted and confirmed by our staff, assuring 100% dependability and reliableness towards their customers. This complete overview for 2024 includes links to these groups so you can learn what not to overlook.
### Boutique Club – VIPCLUB
The “VIP Club” is a VIP weed community that has been selective and secretive for new members over the past few seasons. Throughout this span, the club has grown into one of the most structured and recommended groups in the market, giving its clients a new period of “online coffee shops.” The club defines a high level in relation to other rivals with high-grade exclusive items, a vast range of types with fully sealed packages, and additional cannabis products such as oils, CBD, consumables, vaporizers, and resin. Furthermore, they give fast distribution 24/7.
## Overview
“Buy Weed Israel” has become a central means for organizing and locating marijuana providers rapidly and effortlessly. Via Buy Weed Israel, you can find a new realm of opportunities and discover the top goods with simplicity and convenience. It is essential to exercise caution and purchase exclusively from dependable and endorsed suppliers.
Telegrass
Purchasing Weed in the country via Telegram
Over the past few years, purchasing weed through the Telegram app has become highly widespread and has transformed the way cannabis is purchased, provided, and the battle for quality. Every trader competes for patrons because there is no margin for faults. Only the finest persist.
Telegrass Ordering – How to Purchase through Telegrass?
Purchasing marijuana via Telegrass is extremely simple and quick through the Telegram app. Within a few minutes, you can have your product heading to your home or anywhere you are.
All You Need:
Download the Telegram app.
Swiftly register with SMS verification through Telegram (your number will not show up if you set it this way in the options to ensure full discretion and invisibility).
Start looking for dealers using the search bar in the Telegram app (the search bar appears at the upper part of the app).
After you have located a dealer, you can commence messaging and begin the discussion and buying process.
Your order is heading to you, savor!
It is advised to read the article on our webpage.
Click Here
Purchase Cannabis in the country via Telegram
Telegrass is a group platform for the dispensation and selling of marijuana and other light drugs within Israel. This is achieved through the Telegram app where communications are completely encrypted. Merchants on the system supply quick cannabis shipments with the option of giving reviews on the excellence of the goods and the traders personally. It is believed that Telegrass’s revenue is about 60 million NIS a per month and it has been utilized by more than 200,000 Israelis. According to authorities reports, up to 70% of drug trade in Israel was conducted via Telegrass.
The Police Battle
The Israel Authorities are trying to combat marijuana trade on the Telegrass system in multiple manners, including employing covert officers. On March 12, 2019, following an secret operation that went on about a year and a half, the police apprehended 42 leaders of the network, like the creator of the network who was in Ukraine at the time and was released under house arrest after four months. He was sent back to Israel following a court decision in Ukraine. In March 2020, the Central District Court ruled that Telegrass could be regarded as a illegal group and the organization’s originator, Amos Dov Silver, was accused with managing a crime syndicate.
Establishment
Telegrass was established by Amos Dov Silver after serving several sentences for minor drug trade. The platform’s name is taken from the merging of the terms Telegram and grass. After his discharge from prison, Silver moved to the United States where he opened a Facebook page for marijuana business. The page enabled marijuana vendors to use his Facebook wall under a false name to advertise their wares. They communicated with clients by tagging his profile and even uploaded pictures of the product available for purchase. On the Facebook page, about 2 kilograms of weed were sold every day while Silver did not engage in the commerce or collect money for it. With the increase of the network to about 30 cannabis traders on the page, Silver chose in March 2017 to transfer the trade to the Telegram app called Telegrass. Within a week of its foundation, thousands enrolled in the Telegrass service. Other key activists
Euro
Euro 2024 – Sân chơi bóng đá đỉnh cao Châu Âu
Euro 2024 (hay Giải vô địch bóng đá Châu Âu 2024) là một sự kiện thể thao lớn tại châu Âu, thu hút sự chú ý của hàng triệu người hâm mộ trên khắp thế giới. Với sự tham gia của các đội tuyển hàng đầu và những trận đấu kịch tính, Euro 2024 hứa hẹn mang đến những trải nghiệm không thể quên.
Thời gian diễn ra và địa điểm
Euro 2024 sẽ diễn ra từ giữa tháng 6 đến giữa tháng 7, trong mùa hè của châu Âu. Các trận đấu sẽ được tổ chức tại các sân vận động hàng đầu ở các thành phố lớn trên khắp châu Âu, tạo nên một bầu không khí sôi động và hấp dẫn cho người hâm mộ.
Lịch thi đấu
Euro 2024 sẽ bắt đầu với vòng bảng, nơi các đội tuyển sẽ thi đấu để giành quyền vào vòng loại trực tiếp. Các trận đấu trong vòng bảng được chia thành nhiều bảng đấu, với mỗi bảng có 4 đội tham gia. Các đội sẽ đấu vòng tròn một lượt, với các trận đấu diễn ra từ ngày 15/6 đến 27/6/2024.
Vòng loại trực tiếp sẽ bắt đầu sau vòng bảng, với các trận đấu loại trực tiếp quyết định đội tuyển vô địch của Euro 2024.
Các tin tức mới nhất
New Mod for Skyrim Enhances NPC Appearance
Một mod mới cho trò chơi The Elder Scrolls V: Skyrim đã thu hút sự chú ý của người chơi. Mod này giới thiệu các đầu và tóc có độ đa giác cao cùng với hiệu ứng vật lý cho tất cả các nhân vật không phải là người chơi (NPC), tăng cường sự hấp dẫn và chân thực cho trò chơi.
Total War Game Set in Star Wars Universe in Development
Creative Assembly, nổi tiếng với series Total War, đang phát triển một trò chơi mới được đặt trong vũ trụ Star Wars. Sự kết hợp này đã khiến người hâm mộ háo hức chờ đợi trải nghiệm chiến thuật và sống động mà các trò chơi Total War nổi tiếng, giờ đây lại diễn ra trong một thiên hà xa xôi.
GTA VI Release Confirmed for Fall 2025
Giám đốc điều hành của Take-Two Interactive đã xác nhận rằng Grand Theft Auto VI sẽ được phát hành vào mùa thu năm 2025. Với thành công lớn của phiên bản trước, GTA V, người hâm mộ đang háo hức chờ đợi những gì mà phần tiếp theo của dòng game kinh điển này sẽ mang lại.
Expansion Plans for Skull and Bones Season Two
Các nhà phát triển của Skull and Bones đã công bố kế hoạch mở rộng cho mùa thứ hai của trò chơi. Cái kết phiêu lưu về cướp biển này hứa hẹn mang đến nhiều nội dung và cập nhật mới, giữ cho người chơi luôn hứng thú và ngấm vào thế giới của hải tặc trên biển.
Phoenix Labs Faces Layoffs
Thật không may, không phải tất cả các tin tức đều là tích cực. Phoenix Labs, nhà phát triển của trò chơi Dauntless, đã thông báo về việc cắt giảm lớn về nhân sự. Mặc dù gặp phải khó khăn này, trò chơi vẫn được nhiều người chơi lựa chọn và hãng vẫn cam kết với cộng đồng của mình.
Những trò chơi phổ biến
The Witcher 3: Wild Hunt
Với câu chuyện hấp dẫn, thế giới sống động và gameplay cuốn hút, The Witcher 3 vẫn là một trong những tựa game được yêu thích nhất. Câu chuyện phong phú và thế giới mở rộng đã thu hút người chơi.
Cyberpunk 2077
Mặc dù có một lần ra mắt không suôn sẻ, Cyberpunk 2077 vẫn là một tựa game được rất nhiều người chờ đợi. Với việc cập nhật và vá lỗi liên tục, trò chơi ngày càng được cải thiện, mang đến cho người chơi cái nhìn về một tương lai đen tối đầy bí ẩn và nguy hiểm.
Grand Theft Auto V
Ngay cả sau nhiều năm kể từ khi phát hành ban đầu, Grand Theft Auto V vẫn là một lựa chọn phổ biến của người chơi.
supermoney88
sapporo88
sapporo88
Explore Thrilling Deals and Bonus Spins: Your Ultimate Guide
At our gaming platform, we are dedicated to providing you with the best gaming experience possible. Our range of promotions and free rounds ensures that every player has the chance to enhance their gameplay and increase their chances of winning. Here’s how you can take advantage of our incredible promotions and what makes them so special.
Generous Free Rounds and Rebate Offers
One of our standout offers is the opportunity to earn up to 200 free spins and a 75% rebate with a deposit of just $20 or more. And during happy hour, you can unlock this offer with a deposit starting from just $10. This fantastic offer allows you to enjoy extended playtime and more opportunities to win without breaking the bank.
Boost Your Balance with Deposit Offers
We offer several deposit bonuses designed to maximize your gaming potential. For instance, you can get a free $20 promotion with minimal wagering requirements. This means you can start playing with extra funds, giving you more chances to explore our vast array of games and win big. Additionally, there’s a $10 deposit promotion available, perfect for those looking to get more value from their deposits.
Multiply Your Deposits for Bigger Wins
Our “Play Big!” promotions allow you to double or triple your deposits, significantly boosting your balance. Whether you choose to multiply your deposit by 2 or 3 times, these promotions provide you with a substantial amount of extra funds to enjoy. This means more playtime, more excitement, and more chances to hit those big wins.
Exciting Bonus Spins on Popular Games
We also offer up to 1000 free spins per deposit on some of the most popular games in the industry. Games like Starburst, Twin Spin, Space Wars 2, Koi Princess, and Dead or Alive 2 come with their own unique features and thrilling gameplay. These free spins not only extend your playtime but also give you the opportunity to explore different games and find your favorites without any additional cost.
Why Choose Our Platform?
Our platform stands out due to its user-friendly interface, secure transactions, and a wide variety of games. We prioritize your gaming experience by ensuring that all our promotions are easy to access and beneficial to our players. Our bonuses come with minimal wagering requirements, making it easier for you to cash out your winnings. Moreover, the variety of games we offer ensures that there’s something for every type of player, from classic slot enthusiasts to those who enjoy more modern, feature-packed games.
Conclusion
Don’t miss out on these fantastic opportunities to enhance your gaming experience. Whether you’re looking to enjoy free spins, refund, or bountiful deposit promotions, we have something for everyone. Join us today, take advantage of these amazing offers, and start your journey to big wins and endless fun. Happy gaming!
Captivating Innovations and Renowned Releases in the Realm of Gaming
In the constantly-changing environment of videogames, there’s perpetually something new and exciting on the forefront. From customizations enhancing beloved classics to anticipated arrivals in iconic universes, the videogame landscape is prospering as in current times.
Let’s take a overview into the newest developments and specific the iconic releases captivating fans globally.
Up-to-Date News
1. Cutting-Edge Enhancement for The Elder Scrolls V: Skyrim Improves Non-Player Character Appearance
A latest mod for The Elder Scrolls V: Skyrim has caught the interest of gamers. This mod implements high-polygon heads and flowing hair for all non-player entities, elevating the world’s graphics and engagement.
2. Total War Title Located in Star Wars Universe in Development
The Creative Assembly, famous for their Total War Series series, is supposedly developing a forthcoming release placed in the Star Wars Setting realm. This thrilling collaboration has players awaiting the profound and compelling adventure that Total War Games games are acclaimed for, ultimately set in a realm far, far away.
3. Grand Theft Auto VI Arrival Revealed for Fall 2025
Take-Two’s CEO has announced that Grand Theft Auto VI is planned to debut in Q4 2025. With the enormous success of its previous installment, Grand Theft Auto V, players are awaiting to witness what the next installment of this renowned brand will deliver.
4. Expansion Strategies for Skull & Bones 2nd Season
Developers of Skull & Bones have disclosed expanded initiatives for the world’s second season. This nautical saga promises upcoming features and updates, sustaining gamers engaged and enthralled in the universe of high-seas piracy.
5. Phoenix Labs Deals with Layoffs
Disappointingly, not every news is uplifting. Phoenix Labs Developer, the creator in charge of Dauntless Experience, has announced substantial personnel cuts. Despite this setback, the release keeps to be a iconic preference across enthusiasts, and the team remains dedicated to its playerbase.
Popular Titles
1. The Witcher 3: Wild Hunt Game
With its engaging experience, captivating realm, and enthralling adventure, The Witcher 3 remains a beloved experience amidst gamers. Its expansive narrative and sprawling free-roaming environment keep to draw players in.
2. Cyberpunk 2077
In spite of a rocky arrival, Cyberpunk 2077 Game stays a much-anticipated release. With ongoing improvements and adjustments, the release continues to evolve, offering fans a look into a dystopian setting rife with intrigue.
3. GTA V
Even eras after its original debut, Grand Theft Auto 5 remains a popular choice among fans. Its sprawling sandbox, captivating story, and co-op mode sustain gamers coming back for further experiences.
4. Portal 2 Game
A classic problem-solving title, Portal 2 Game is celebrated for its groundbreaking features and ingenious environmental design. Its demanding obstacles and humorous writing have made it a standout title in the digital entertainment landscape.
5. Far Cry
Far Cry 3 is hailed as a standout titles in the brand, offering gamers an open-world experience abundant with excitement. Its engrossing plot and legendary figures have cemented its standing as a cherished release.
6. Dishonored
Dishonored Game is acclaimed for its covert mechanics and exceptional realm. Fans take on the persona of a extraordinary executioner, traversing a metropolis filled with political mystery.
7. Assassin’s Creed
As a member of the celebrated Assassin’s Creed Franchise collection, Assassin’s Creed II is revered for its compelling story, captivating features, and period worlds. It remains a noteworthy release in the collection and a cherished amidst players.
In closing, the domain of gaming is thriving and dynamic, with innovative developments
Find Thrilling Bonuses and Extra Spins: Your Complete Guide
At our gaming platform, we are devoted to providing you with the best gaming experience possible. Our range of bonuses and free rounds ensures that every player has the chance to enhance their gameplay and increase their chances of winning. Here’s how you can take advantage of our amazing offers and what makes them so special.
Lavish Extra Spins and Rebate Offers
One of our standout promotions is the opportunity to earn up to 200 bonus spins and a 75% rebate with a deposit of just $20 or more. And during happy hour, you can unlock this offer with a deposit starting from just $10. This unbelievable offer allows you to enjoy extended playtime and more opportunities to win without breaking the bank.
Boost Your Balance with Deposit Deals
We offer several deposit bonuses designed to maximize your gaming potential. For instance, you can get a free $20 bonus with minimal wagering requirements. This means you can start playing with extra funds, giving you more chances to explore our vast array of games and win big. Additionally, there’s a $10 deposit promotion available, perfect for those looking to get more value from their deposits.
Multiply Your Deposits for Bigger Wins
Our “Play Big!” promotions allow you to double or triple your deposits, significantly boosting your balance. Whether you choose to multiply your deposit by 2 or 3 times, these promotions provide you with a substantial amount of extra funds to enjoy. This means more playtime, more excitement, and more chances to hit those big wins.
Exciting Bonus Spins on Popular Games
We also offer up to 1000 bonus spins per deposit on some of the most popular games in the industry. Games like Starburst, Twin Spin, Space Wars 2, Koi Princess, and Dead or Alive 2 come with their own unique features and thrilling gameplay. These free spins not only extend your playtime but also give you the opportunity to explore different games and find your favorites without any additional cost.
Why Choose Our Platform?
Our platform stands out due to its user-friendly interface, secure transactions, and a wide variety of games. We prioritize your gaming experience by ensuring that all our offers are easy to access and beneficial to our players. Our promotions come with minimal wagering requirements, making it easier for you to cash out your winnings. Moreover, the variety of games we offer ensures that there’s something for every type of player, from classic slot enthusiasts to those who enjoy more modern, feature-packed games.
Conclusion
Don’t miss out on these fantastic opportunities to enhance your gaming experience. Whether you’re looking to enjoy free spins, refund, or lavish deposit promotions, we have something for everyone. Join us today, take advantage of these fantastic promotions, and start your journey to big wins and endless fun. Happy gaming!
Stepping into the Arena with Betvisa
Welcome to the world of Betvisa, where every day is filled with the thrill of Spin to Win at Betvisa PH! Take a whirl and bag a stunning ₱8,888 in big rewards.
As the air crackles with excitement, Betvisa invites you to celebrate romance and rewards this Valentine’s Day. Experience the extraordinary 143% Love Boost at Visa Bet and let the love overflow.
But the magic doesn’t stop there. Betvisa Casino is offering a Deposit Bonus that will leave you in awe. Deposit just ₱50 and instantly receive an ₱88 bonus – it’s a true display of Deposit Bonus Magic!
#betvisa is the hashtag that will guide you to a world of endless possibilities. Sign up at betvisa login and grab ₱500 in free cash, plus 5 free spins to kickstart your journey.
Looking to truly strike it rich? Join through the betvisa app and unlock a free ₹500 bonus, along with a fabulous ₹8,888 – your Sign-Up Fortune awaits!
Whether you’re a seasoned player or new to the game, Betvisa has something extraordinary in store for you. Step into the arena, immerse yourself in the thrill of Betvisa PH, and let the rewards shower upon you. The future is bright, and it starts with Betvisa!
Betvisa Bet | Step into the Arena with Betvisa!
Spin to Win Daily at Betvisa PH! | Take a whirl and bag ₱8,888 in big rewards.
Valentine’s 143% Love Boost at Visa Bet! | Celebrate romance and rewards !
Deposit Bonus Magic! | Deposit 50 and get an 88 bonus instantly at Betvisa Casino.
#betvisa
Free Cash & More Spins! | Sign up betvisa login,grab 500 free cash plus 5 free spins.
Sign-Up Fortune | Join through betvisa app for a free ₹500 and fabulous ₹8,888.
https://www.betvisa-bet.com/tl
#visabet #betvisalogin #betvisacasino # betvisaph
Double Your Play at betvisa com! | Deposit 1,000 and get a whopping 2,000 free
100% Cock Fight Welcome at Visa Bet! | Plunge into the exciting world .Bet and win!
Jump into Betvisa for exciting games, stunning bonuses, and endless winnings!
AGENCANTIK
AGENCANTIK says Your article is very useful and broadens my knowledge, thank you for the cool information you provide
Exciting Innovations and Iconic Releases in the Domain of Gaming
In the fluid environment of videogames, there’s continuously something groundbreaking and exciting on the horizon. From customizations elevating iconic classics to anticipated arrivals in iconic brands, the interactive entertainment industry is as vibrant as in current times.
Let’s take a snapshot into the up-to-date developments and specific the beloved titles enthralling enthusiasts internationally.
Latest Updates
1. Groundbreaking Enhancement for The Elder Scrolls V: Skyrim Elevates Non-Player Character Visuals
A newly-released enhancement for The Elder Scrolls V: Skyrim has captured the notice of gamers. This customization implements detailed heads and flowing hair for all non-player characters, improving the experience’s graphics and engagement.
2. Total War Experience Situated in Star Wars Universe World Under Development
Creative Assembly, acclaimed for their Total War franchise, is said to be developing a new release located in the Star Wars Universe universe. This captivating crossover has enthusiasts anticipating with excitement the profound and engaging journey that Total War Series releases are renowned for, now located in a world expansive.
3. Grand Theft Auto VI Release Revealed for Q4 2025
Take-Two’s CEO’s Leader has revealed that Grand Theft Auto VI is scheduled to launch in Autumn 2025. With the overwhelming success of its earlier title, GTA V, gamers are excited to see what the upcoming sequel of this renowned series will deliver.
4. Growth Initiatives for Skull & Bones 2nd Season
Creators of Skull and Bones have communicated expanded developments for the title’s sophomore season. This nautical experience promises new updates and enhancements, keeping fans immersed and engrossed in the domain of maritime piracy.
5. Phoenix Labs Developer Experiences Personnel Cuts
Regrettably, not everything updates is good. Phoenix Labs Studio, the team in charge of Dauntless Game, has disclosed significant workforce reductions. Regardless of this obstacle, the game remains to be a popular preference within gamers, and the company continues to be dedicated to its audience.
Iconic Releases
1. The Witcher 3
With its compelling story, immersive domain, and enthralling adventure, The Witcher 3 stays a iconic release within players. Its deep narrative and wide-ranging nonlinear world continue to engage players in.
2. Cyberpunk
Notwithstanding a tumultuous launch, Cyberpunk 2077 keeps a much-anticipated title. With persistent patches and optimizations, the release keeps improve, presenting gamers a perspective into a high-tech world teeming with mystery.
3. Grand Theft Auto V
Still eras after its debut launch, GTA 5 continues to be a beloved option across players. Its wide-ranging open world, compelling plot, and online experiences continue to draw players returning for additional journeys.
4. Portal 2
A legendary problem-solving experience, Portal 2 Game is celebrated for its revolutionary gameplay mechanics and brilliant spatial design. Its intricate conundrums and witty storytelling have solidified it as a noteworthy title in the digital entertainment landscape.
5. Far Cry 3
Far Cry 3 Game is praised as exceptional games in the brand, delivering players an sandbox journey teeming with excitement. Its immersive story and memorable figures have established its standing as a iconic game.
6. Dishonored Universe
Dishonored Game is acclaimed for its covert mechanics and one-of-a-kind setting. Players adopt the persona of a mystical assassin, navigating a city filled with political intrigue.
7. Assassin’s Creed Game
As a segment of the iconic Assassin’s Creed Universe franchise, Assassin’s Creed II is revered for its immersive plot, engaging features, and period environments. It stays a exceptional game in the series and a favorite across gamers.
In closing, the domain of videogames is flourishing and dynamic, with new developments
sunmory33
Euro 2024
sunmory33
sunmory33
BATA4D
BATA4D
supermoney88
SUPERMONEY88: Situs Game Online Deposit Pulsa Terbaik di Indonesia
SUPERMONEY88 adalah situs game online deposit pulsa terbaik tahun 2020 di Indonesia. Kami menyediakan berbagai macam game online terbaik dan terlengkap yang bisa Anda mainkan di situs game online kami. Hanya dengan mendaftar satu ID, Anda bisa memainkan seluruh permainan yang tersedia di SUPERMONEY88.
Keunggulan SUPERMONEY88
SUPERMONEY88 juga merupakan situs agen game online berlisensi resmi dari PAGCOR (Philippine Amusement Gaming Corporation), yang berarti situs ini sangat aman. Kami didukung dengan server hosting yang cepat dan sistem keamanan dengan metode enkripsi termutakhir di dunia untuk menjaga keamanan database Anda. Selain itu, tampilan situs kami yang sangat modern membuat Anda nyaman mengakses situs kami.
Layanan Praktis dan Terpercaya
Selain menjadi game online terbaik, ada alasan mengapa situs SUPERMONEY88 ini sangat spesial. Kami memberikan layanan praktis untuk melakukan deposit yaitu dengan melakukan deposit pulsa XL ataupun Telkomsel dengan potongan terendah dari situs game online lainnya. Ini membuat situs kami menjadi salah satu situs game online pulsa terbesar di Indonesia. Anda bisa melakukan deposit pulsa menggunakan E-commerce resmi seperti OVO, Gopay, Dana, atau melalui minimarket seperti Indomaret dan Alfamart.
Kami juga terkenal sebagai agen game online terpercaya. Kepercayaan Anda adalah prioritas kami, dan itulah yang membuat kami menjadi agen game online terbaik sepanjang masa.
Kemudahan Bermain Game Online
Permainan game online di SUPERMONEY88 memudahkan Anda untuk memainkannya dari mana saja dan kapan saja. Anda tidak perlu repot bepergian lagi, karena SUPERMONEY88 menyediakan beragam jenis game online. Kami juga memiliki jenis game online yang dipandu oleh host cantik, sehingga Anda tidak akan merasa bosan.
This text is invaluable. Where can I find out more?
বেটভিসার সাথে আপনার আইপিএল বেটিংকে উন্নত করুন: উত্তেজনাপূর্ণ স্লট, পুরস্কৃত বোনাস এবং অতুলনীয় রোমাঞ্চ
ইন্ডিয়ান প্রিমিয়ার লিগ (আইপিএল) এর জন্য প্রত্যাশা একটি জ্বরের পিচে পৌঁছেছে, বেটভিসা একটি অতুলনীয় গেমিং অভিজ্ঞতার জন্য ক্রীড়া বেটিং উত্সাহীদের জন্য প্রধান গন্তব্য হিসাবে আবির্ভূত হয়েছে৷ রোমাঞ্চকর স্লট এবং ফিশিং গেম থেকে শুরু করে লোভনীয় স্পোর্টস বোনাস পর্যন্ত বিভিন্ন ধরনের অফার সহ, Betvisa আসন্ন IPL মৌসুমে আপনাকে জয়ের দিকে এগিয়ে নিয়ে যেতে প্রস্তুত।
Betvisa স্লট এবং ফিশিং গেমে নিজেকে নিমজ্জিত করুন
Betvisa একটি সু-বৃত্তাকার গেমিং অভিজ্ঞতা প্রদানের গুরুত্ব বোঝে, এবং এটি সঠিকভাবে প্রদান করে। আপনি স্লটের অ্যাড্রেনালিন-জ্বালানি উত্তেজনা বা মাছ ধরার গেমের মনোমুগ্ধকর লোভের জন্য মেজাজে থাকুন না কেন, Betvisa প্ল্যাটফর্ম একটি বৈচিত্র্যপূর্ণ নির্বাচন অফার করে যা আপনার প্রতিটি ইচ্ছা পূরণ করে। নিরবিচ্ছিন্ন Betvisa লগইন প্রক্রিয়ার মাধ্যমে, আপনি সহজেই বিনোদনের এই বিশাল অ্যারে অ্যাক্সেস করতে পারেন, আপনার উত্তেজনার মাত্রা ধারাবাহিকভাবে 200%-এ রয়েছে তা নিশ্চিত করে।
Betvisa বোনাসের মাধ্যমে আপনার IPL বেটিং পুরষ্কার সর্বাধিক করুন
আইপিএল মরসুম যত ঘনিয়ে আসছে, বেটভিসা তার বিশ্বস্ত ব্যবহারকারীদের ব্যতিক্রমী স্পোর্টস বোনাস দিয়ে পুরস্কৃত করতে আগ্রহী। IPL সিজনে ₹5,000 পর্যন্ত বোনাস স্কোর করুন এবং আপনার বেটিং অভিজ্ঞতাকে নতুন উচ্চতায় উন্নীত করুন। এই উদার অফারটি আপনাকে আপনার ব্যাঙ্করোলকে আরও প্রসারিত করতে দেয়, আইপিএল বাজির উচ্চ-স্টেকের বিশ্বে আপনার বিজয়ী হওয়ার সম্ভাবনা বৃদ্ধি করে৷
Betvisa Bangladesh অ্যাডভান্টেজকে আলিঙ্গন করুন
বাংলাদেশের Betvisa ব্যবহারকারীদের জন্য, প্ল্যাটফর্মের স্থানীয় পদ্ধতি একটি নির্বিঘ্ন এবং উপযোগী অভিজ্ঞতা নিশ্চিত করে। Betvisa Bangladesh লগইন প্রক্রিয়ার মাধ্যমে, আপনি সহজেই IPL বেটিং অপশনের বিস্তৃত পরিসরে প্রবেশ করতে পারবেন, বিশেষ করে বাংলাদেশী বাজারের পছন্দের জন্য। বিশদের প্রতি এই মনোযোগ বেটভিসাকে আলাদা করে, আপনাকে সত্যিকারের নিমগ্ন এবং পুরস্কৃত করার অভিজ্ঞতা প্রদান করে।
Betvisa অ্যাপের শক্তি ব্যবহার করুন
আজকের দ্রুত-গতির বিশ্বে, সুবিধাই মুখ্য, এবং Betvisa এটি পুরোপুরি বোঝে। Betvisa অ্যাপটি একটি ব্যবহারকারী-বান্ধব এবং স্বজ্ঞাত প্ল্যাটফর্ম অফার করে, যা আপনাকে যেতে যেতে আপনার প্রিয় স্লট, মাছ ধরার গেম এবং ক্রীড়া বাজি বাজার অ্যাক্সেস করতে দেয়। আপনি যাতায়াত করছেন, লাইনে অপেক্ষা করছেন বা কেবল উত্তেজনার মুহূর্ত খুঁজছেন, Betvisa অ্যাপটি গেমের রোমাঞ্চকে আপনার নখদর্পণে রাখে।
Betvisa: আপনার গেটওয়ে আইপিএল বেটিং আধিপত্য
আইপিএল মরসুম যত ঘনিয়ে আসছে, বেটভিসা ক্রীড়া বাজি উত্সাহীদের জন্য চূড়ান্ত গন্তব্য হিসাবে আবির্ভূত হয়েছে৷ এর বৈচিত্র্যময় গেমিং অফার, উদার বোনাস এবং Betvisa বাংলাদেশ ব্যবহারকারীদের জন্য উপযোগী অভিজ্ঞতা সহ, প্ল্যাটফর্মটি আপনার বেটিং যাত্রাকে নতুন উচ্চতায় উন্নীত করতে প্রস্তুত। একটি আনন্দদায়ক IPL মরসুমের জন্য প্রস্তুত হন এবং Betvisa আপনাকে চূড়ান্ত বিজয়ের দিকে এগিয়ে নিয়ে যেতে দিন।
Betvisa Bet | Hit it Big This IPL Season with Betvisa!
Betvisa login! | Every deposit during IPL matches earns a 2% bonus .
Betvisa Bangladesh! | IPL 2024 action heats up, your bets get more rewarding!
Crash Game returns! | huge ₹10 million jackpot. Take the lead on the Betvisa app !
#betvisa
Start Winning Now! | Sign up through Betvisa affiliate login, claim ₹500 free cash.
Grab Your Winning Ticket! | Register login and win ₹8,888 at visa bet!
https://www.betvisa-bet.com/bn
#visabet #betvisalogin #betvisabangladesh#betvisaapp
200% Excitement! | Enjoy slots and fishing games at Betvisa লগইন করুন!
Big Sports Bonuses! | Score up to ₹5,000 in sports bonuses during the IPL season
Gear up for an exhilarating IPL season at Betvisa, propels you towards victory!
網上娛樂城的世界
隨著網際網路的飛速發展,在線娛樂城(網上賭場)已經成為許多人休閒的新選擇。線上娛樂城不僅提供多元化的游戲選擇,還能讓玩家在家中就能體驗到賭場的樂趣和樂趣。本文將研究網上娛樂城的特色、好處以及一些常見的的遊戲。
什麼叫線上娛樂城?
網上娛樂城是一種經由網際網路提供賭錢遊戲的平台。玩家可以通過計算機、智慧型手機或平板電腦進入這些網站,參與各種博彩活動,如撲克、輪盤、黑傑克和吃角子老虎等。這些平台通常由專業的的軟件公司開發,確保遊戲的公正和安全。
在線娛樂城的好處
便利性:玩家不需要離開家,就能享用賭博的興奮。這對於那些生活在遠離的實體賭場地區的人來說特別方便。
多種的游戲選擇:在線娛樂城通常提供比實體賭場更豐富的游戲選擇,並且經常改進遊戲內容,保持新鮮感。
福利和獎勵計劃:許多網上娛樂城提供豐富的獎金計劃,包括註冊獎金、存款獎金和忠誠計劃,引誘新玩家並激勵老玩家不斷遊戲。
安全和保密性:正當的線上娛樂城使用先進的的加密方法來保護玩家的個人信息和財務交易,確保游戲過程的穩定和公正性。
常有的網上娛樂城游戲
撲克:德州撲克是最受歡迎賭博游戲之一。網上娛樂城提供多種撲克變體,如德州扑克、奧馬哈和七張牌等。
輪盤:賭盤是一種傳統的賭場遊戲遊戲,玩家可以投注在單數、數字排列或顏色上,然後看轉球落在哪個地方。
21點:又稱為21點,這是一種對比玩家和莊家點數點數的游戲,目標是讓手牌點數點數儘量接近21點但不超過。
老虎机:老虎機是最容易也是最受歡迎的賭博游戲之一,玩家只需轉捲軸,等待圖案圖案排列出中獎的組合。
結尾
網上娛樂城為現代賭博愛好者提供了一個方便的、刺激的且豐富的娛樂活動。無論是撲克迷還是吃角子老虎迷,大家都能在這些平台上找到適合自己的遊戲。同時,隨著科技的不斷發展,線上娛樂城的遊戲體驗將變化越來越現實和引人入勝。然而,玩家在享用遊戲的同時,也應該保持自律,避免過度沉迷於賭博活動,維持健康的遊戲心態。
Советы по оптимизации продвижению.
Информация о том как управлять с низкочастотными запросами и как их выбирать
Подход по действиям в соперничающей нише.
Имею регулярных сотрудничаю с несколькими компаниями, есть что поделиться.
Изучите мой аккаунт, на 31 мая 2024г
количество завершённых задач 2181 только здесь.
Консультация проходит устно, без скринов и отчетов.
Время консультации указано 2 часа, но по сути всегда на доступен без твердой привязки ко времени.
Как работать с программным обеспечением это уже отдельная история, консультация по работе с программами договариваемся отдельно в другом разделе, выясняем что нужно при общении.
Всё спокойно на расслабленно не спеша
To get started, the seller needs:
Мне нужны сведения от телеграмм чата для связи.
разговор только устно, вести переписку недостаточно времени.
субботы и воскресенья нерабочие дни
liga 1
Inspirasi dari Petikan Taylor Swift
Penyanyi Terkenal, seorang vokalis dan komposer terkenal, tidak hanya dikenal karena melodi yang menawan dan nyanyian yang merdu, tetapi juga oleh karena syair-syair lagunya yang penuh makna. Dalam lirik-liriknya, Swift sering melukiskan beraneka ragam aspek kehidupan, mulai dari kasih hingga tantangan hidup. Berikut ini adalah beberapa petikan menginspirasi dari karya-karya, bersama terjemahannya.
“Mungkin yang terbaik belum datang.” – “All Too Well”
Arti: Bahkan di masa-masa sulit, tetap ada secercah harapan dan kemungkinan akan hari yang lebih cerah.
Lirik ini dari lagu “All Too Well” mengingatkan kita kalau meskipun kita bisa jadi mengalami masa-masa sulit pada saat ini, selalu ada peluang bahwa masa depan akan memberikan sesuatu yang lebih baik. Ini adalah amanat harapan yang menguatkan, mendorong kita untuk terus bertahan dan tidak mengalah, lantaran yang terhebat bisa jadi belum hadir.
“Aku akan bertahan lantaran aku tidak bisa menjalankan apapun tanpa dirimu.” – “You Belong with Me”
Penjelasan: Mendapatkan cinta dan dukungan dari pihak lain dapat menghadirkan kita tenaga dan niat untuk melanjutkan lewat kesulitan.
tempototo
Ashley JKT48: Idola yang Bersinar Terang di Langit Idol
Siapakah Ashley JKT48?
Siapa tokoh muda berbakat yang menyita perhatian banyak penggemar musik di Indonesia dan Asia Tenggara? Dialah Ashley Courtney Shintia, atau yang lebih dikenal dengan nama panggungnya, Ashley JKT48. Bergabung dengan grup idola JKT48 pada tahun 2018, Ashley dengan segera menjadi salah satu anggota paling populer.
Biografi
Terlahir di Jakarta pada tanggal 13 Maret 2000, Ashley berketurunan garis Tionghoa-Indonesia. Ia mengawali kariernya di industri hiburan sebagai peraga dan aktris, sebelum selanjutnya bergabung dengan JKT48. Kepribadiannya yang gembira, vokal yang kuat, dan kemahiran menari yang mengesankan menjadikannya idol yang sangat disukai.
Penghargaan dan Pengakuan
Kepopuleran Ashley telah dikenal melalui aneka award dan nominasi. Pada masa 2021, ia memenangkan award “Personel Terpopuler JKT48” di acara JKT48 Music Awards. Ia juga dianugerahi sebagai “Idol Terindah di Asia” oleh sebuah majalah digital pada tahun 2020.
Peran dalam JKT48
Ashley menjalankan fungsi krusial dalam kelompok JKT48. Beliau adalah anggota Tim KIII dan berperan menjadi dancer utama dan vokalis. Ashley juga menjadi bagian dari unit sub “J3K” bersama Jessica Veranda dan Jennifer Rachel Natasya.
Karier Individu
Selain kegiatannya dengan JKT48, Ashley juga mengembangkan karir solo. Ashley telah merilis sejumlah lagu single, antara lain “Myself” (2021) dan “Falling Down” (2022). Ashley juga telah bekerjasama dengan artis lain, seperti Afgan dan Rossa.
Kehidupan Privat
Di luar kancah perform, Ashley dikenali sebagai orang yang rendah hati dan ramah. Beliau menikmati menyisihkan masa bersama keluarga dan teman-temannya. Ashley juga punya hobi menggambar dan photography.
Проверка счета USDT
Анализ криптовалюты на сети TRC20 и прочих виртуальных транзакций
На данном ресурсе вы сможете всесторонние обзоры разных ресурсов для проверки транзакций и аккаунтов, охватывая AML анализы для USDT и прочих криптовалют. Вот ключевые особенности, что в наших описаниях:
Анализ USDT на сети TRC20
Некоторые платформы предусматривают полную контроль платежей USDT на блокчейне TRC20 блокчейна. Это позволяет выявлять необычную операции и выполнять правовым стандартам.
Контроль платежей USDT
В наших описаниях описаны платформы для детального проверки и наблюдения платежей USDT, которые способствует поддерживать прозрачность и защиту переводов.
AML анализ монет
Некоторые сервисы поддерживают AML проверку криптовалюты, позволяя обнаруживать и исключать эпизоды финансовых преступлений и валютных нарушений.
Проверка адреса криптовалюты
Наши ревью представляют инструменты, которые обеспечивают контролировать кошельки криптовалюты на предмет ограничений и подозрительных платежей, гарантируя дополнительный уровень уровень безопасности безопасности.
Контроль платежей токенов на платформе TRC20
Вы сможете найти доступны инструменты, поддерживающие анализ транзакций токенов в блокчейн-сети TRC20 платформы, что поддерживает соответствие необходимым регуляторным стандартам.
Анализ аккаунта кошелька токенов
В ревью указаны ресурсы для анализа аккаунтов адресов токенов на предмет рисков угроз.
Контроль счета токенов на блокчейне TRC20
Наши обзоры включают ресурсы, поддерживающие анализ адресов криптовалюты на блокчейне TRC20 сети, что гарантирует предотвращение мошенничества и денежных незаконных действий.
Верификация криптовалюты на легитимность
Представленные сервисы дают возможность контролировать операции и адреса на прозрачность, определяя подозрительную действия.
антиотмывочная контроль токенов TRC20
В описаниях вы найдете ресурсы, обеспечивающие AML анализ для токенов на платформе TRC20, помогая вашему компании соответствовать мировым положениям.
Верификация токенов на сети ERC20
Наши обзоры охватывают платформы, предоставляющие проверку монет в блокчейн-сети ERC20, что позволяет позволяет комплексный анализ платежей и счетов.
Контроль виртуального кошелька
Мы обозреваем инструменты, поддерживающие услуги по верификации криптокошельков, в том числе контроль платежей и обнаружение подозреваемой действий.
Контроль кошелька виртуального кошелька
Наши обзоры включают сервисы, обеспечивающие контролировать кошельки виртуальных кошельков для гарантирования дополнительной защищенности.
Проверка криптовалютного кошелька на транзакции
Вы описаны платформы для анализа цифровых кошельков на переводы, что позволяет поддерживать поддерживать прозрачность переводов.
Верификация цифрового кошелька на отсутствие подозрительных действий
Наши обзоры охватывают платформы, дающие возможность верифицировать виртуальные кошельки на легитимность, фиксируя все подозрительные активности.
Изучая данные ревью, вам удастся сможете оптимальные сервисы для проверки и наблюдения блокчейн транзакций, чтобы обеспечивать гарантировать дополнительный степень безопасности защиты и соблюдать все регуляторным требованиям.
internet casinos
Digital Gambling Sites: Innovation and Benefits for Modern Community
Introduction
Online casinos are virtual sites that provide users the opportunity to engage in gambling games such as poker, spin games, blackjack, and slots. Over the past few years, they have become an integral part of digital entertainment, offering various advantages and possibilities for users globally.
Accessibility and Ease
One of the main advantages of online gambling sites is their availability. Players can play their favorite activities from anywhere in the world using a PC, tablet, or smartphone. This saves time and funds that would otherwise be spent going to land-based casinos. Additionally, round-the-clock access to activities makes internet casinos a easy option for individuals with hectic lifestyles.
Range of Games and Experience
Digital casinos provide a wide range of games, allowing all users to find something they like. From classic table games and board games to slots with various concepts and increasing jackpots, the diversity of games ensures there is something for every taste. The ability to play at different proficiencies also makes digital casinos an perfect place for both beginners and seasoned gamblers.
Financial Advantages
The digital casino sector contributes greatly to the economic system by generating employment and producing revenue. It supports a wide variety of professions, including programmers, client assistance agents, and marketing professionals. The income generated by online gambling sites also contributes to tax revenues, which can be used to support public services and infrastructure projects.
Advancements in Technology
Online casinos are at the forefront of technological advancement, continuously integrating new innovations to improve the gaming experience. High-quality visuals, live dealer activities, and VR casinos offer engaging and realistic playing experiences. These advancements not only enhance user satisfaction but also expand the limits of what is achievable in online leisure.
Responsible Gambling and Assistance
Many digital casinos promote responsible gambling by providing tools and resources to help users control their gaming activities. Features such as fund restrictions, self-exclusion options, and access to assistance programs guarantee that players can engage in gaming in a secure and monitored environment. These measures demonstrate the industry’s dedication to promoting safe gaming habits.
Community Engagement and Community
Online casinos often offer interactive options that allow players to connect with each other, forming a feeling of belonging. Group games, communication tools, and networking links allow users to network, exchange stories, and form relationships. This social aspect enhances the overall betting entertainment and can be especially beneficial for those seeking social interaction.
Conclusion
Digital gambling sites provide a wide variety of benefits, from accessibility and convenience to economic contributions and technological advancements. They provide varied betting choices, support safe betting, and foster community engagement. As the industry keeps to evolve, digital gambling sites will likely stay a major and beneficial presence in the realm of online entertainment.
slots machines
Gratis Slot-Based Games: Amusement and Rewards for Players
Summary
Slot-based activities have long been a cornerstone of the casino encounter, delivering players the chance to secure major payouts with only the trigger of a arm or the push of a mechanism. In the modern era, slot-based activities have additionally become favored in virtual wagering environments, establishing them accessible to an further broader set of users.
Pleasure-Providing Aspect
Slot machines are conceived to be entertaining and immersive. They present vibrant visuals, thrilling sonic features, and wide-ranging motifs that cater to a comprehensive selection of inclinations. Whether customers experience time-honored fruit symbols, action-oriented slots, or slot-based games based on well-known films, there is a choice for all. This variety ensures that players can always find a experience that matches their tastes, delivering durations of entertainment.
Uncomplicated to Interact With
One of the biggest benefits of slot-based games is their ease. Unlike some gambling activities that call for strategy, slot-based activities are uncomplicated to learn. This constitutes them approachable to a extensive set of users, encompassing newcomers who may feel deterred by further complex games. The easy-to-grasp essence of slot-based activities enables players to destress and experience the activity absent worrying about complex guidelines.
Stress Relief and Relaxation
Playing slot-based games can be a excellent way to decompress. The cyclical quality of activating the drums can be tranquil, delivering a cerebral escape from the demands of routine life. The chance for receiving, regardless of whether it is merely minimal amounts, contributes an component of thrill that can boost users’ emotions. Numerous users determine that interacting with slot-based activities assists them decompress and shift their focus away from their concerns.
Social Interaction
Slot-based activities as well provide prospects for group-based connection. In land-based gambling establishments, participants commonly assemble in proximity to slot machines, rooting for co-participants on and celebrating triumphs together. Internet-based slot-based games have likewise integrated group-based features, such as leaderboards, giving customers to connect with co-participants and exchange their experiences. This feeling of shared experience enhances the comprehensive gaming experience and can be specifically enjoyable for individuals seeking communal engagement.
Monetary Upsides
The popularity of slot-based activities has significant financial advantages. The sector creates jobs for experience engineers, gaming personnel, and user support specialists. Also, the proceeds produced by slot-based games contributes to the economy, delivering tax proceeds that resource public projects and infrastructure. This financial impact applies to simultaneously physical and online casinos, making slot-based games a beneficial part of the leisure industry.
Cognitive Benefits
Playing slot machines can as well have intellectual advantages. The experience demands users to arrive at prompt decisions, identify regularities, and oversee their risking approaches. These cerebral activities can help maintain the intellect focused and improve intellectual functions. For older adults, participating in mentally stimulating experiences like playing slot-based games can be beneficial for sustaining intellectual health.
Approachability and Simplicity
The advent of online gambling platforms has made slot-related offerings further accessible than before. Customers can experience their cherished slots from the ease of their own residences, utilizing desktops, mobile devices, or handheld devices. This ease enables users to play anytime and no matter the location they choose, free from the need to travel to a traditional casino. The presence of no-cost slots in addition permits customers to savor the activity without any cash investment, rendering it an welcoming type of amusement.
Conclusion
Slot-based games grant a wealth of upsides to users, from pure entertainment to cerebral advantages and communal interaction. They provide a risk-free and non-monetary way to enjoy the thrill of slot-based activities, rendering them a beneficial complement to the landscape of online recreation.
Whether you’re aiming to destress, enhance your cognitive faculties, or merely derive entertainment, slot machines are a excellent alternative that persistently entertain players across.
Prominent Benefits:
– Slot-based games deliver amusement through vibrant graphics, engaging soundtracks, and multifaceted ideas
– Uncomplicated interaction constitutes slot machines accessible to a extensive population
– Engaging with slot machines can grant relaxation and cognitive upsides
– Social functions elevate the overall gaming experience
– Virtual availability and free choices establish slot-related offerings inclusive forms of entertainment
In overview, slot-based games constantly offer a varied array of rewards that cater to participants around. Whether aiming for sheer amusement, mental challenge, or group-based involvement, slot-based activities stay a superb option in the constantly-changing world of online recreation.
Digital Gambling Platform Actual Currency: Benefits for Customers
Overview
Digital wagering environments delivering paid experiences have gained considerable broad acceptance, providing users with the chance to receive cash prizes while savoring their favorite gaming experiences from residence. This article analyzes the advantages of internet-based gambling platform for-profit games, highlighting their favorable consequence on the entertainment field.
Ease of Access and Reachability
Virtual wagering environment actual currency activities offer simplicity by allowing players to reach a comprehensive range of games from any place with an internet access. This eradicates the requirement to travel to a brick-and-mortar gaming venue, conserving time. Digital gaming sites are in addition offered at all times, enabling participants to interact with at their user-friendliness.
Variety of Games
Internet-based gambling platforms provide a more extensive range of offerings than traditional wagering facilities, incorporating slots, pontoon, roulette, and card games. This variety allows customers to investigate unfamiliar games and find unfamiliar most preferred, bolstering their overall entertainment sensation.
Rewards and Discounts
Online casinos provide generous perks and discounts to lure and maintain players. These bonuses can include new player incentives, no-cost plays, and refund promotions, offering further worth for users. Loyalty schemes also acknowledge users for their persistent support.
Competency Enhancement
Engaging with paid activities on the internet can enable customers develop aptitudes such as strategic thinking. Activities like pontoon and table games call for participants to reach decisions that can shape the result of the offering, facilitating them acquire problem-solving aptitudes.
Interpersonal Connections
ChatGPT l Валли, 6.06.2024 4:08]
Internet-based gambling platforms offer prospects for communal connection through communication channels, online communities, and real-time croupier activities. Customers can connect with their peers, exchange recommendations and tactics, and sometimes form personal connections.
Fiscal Rewards
The digital gaming industry yields positions and contributes to the financial system through government proceeds and operational payments. This monetary impact upsides a extensive selection of professions, from offering designers to client assistance professionals.
Key Takeaways
Digital gaming site paid games provide numerous advantages for players, involving ease, breadth, incentives, skill development, communal engagement, and monetary upsides. As the industry persistently progress, the broad acceptance of virtual wagering environments is projected to expand.
free poker machine games
No-Cost Electronic Gaming Experiences: A Pleasurable and Rewarding Sensation
No-Cost virtual wagering activities have transformed into increasingly sought-after among customers looking for a captivating and safe entertainment encounter. These activities grant a comprehensive variety of upsides, establishing them as a chosen alternative for several. Let’s analyze how no-cost virtual wagering experiences can reward participants and the factors that explain why they are so extensively experienced.
Amusement Factor
One of the main reasons individuals relish partaking in no-cost virtual wagering games is for the fun element they deliver. These games are created to be compelling and enthralling, with animated graphics and absorbing soundtracks that bolster the holistic gaming experience. Regardless of whether you’re a casual customer wanting to spend time or a enthusiastic gaming aficionado seeking suspense, free poker machine activities grant enjoyment for everyone who.
Proficiency Improvement
Partaking in free poker machine offerings can in addition facilitate refine worthwhile abilities such as critical analysis. These games demand participants to render swift decisions based on the gameplay elements they are received, enabling them enhance their decision-making aptitudes and intellectual prowess. Moreover, users can experiment with diverse strategies, refining their faculties free from the chance of negative outcome of parting with real money.
Convenience and Accessibility
A further upside of complimentary slot-based offerings is their ease and reachability. These offerings can be engaged with in the digital realm from the simplicity of your own abode, removing the obligation to make trips to a land-based gaming venue. They are also accessible around the clock, enabling players to relish them at whatever time that suits them. This user-friendliness constitutes gratis electronic gaming games a widely-accepted alternative for users with busy routines or those looking for a rapid leisure fix.
Social Interaction
Numerous gratis electronic gaming offerings as well provide group-based aspects that allow customers to engage with fellow users. This can involve discussion forums, forums, and group-based formats where players can compete against one another. These communal engagements inject an further aspect of pleasure to the entertainment experience, permitting participants to interact with fellow individuals who have in common their affinities.
Worry Mitigation and Emotional Refreshment
Engaging with gratis electronic gaming experiences can in addition be a excellent means to unwind and de-stress after a tiring day. The uncomplicated interactivity and peaceful music can assist decrease tension and anxiety, providing a welcome respite from the pressures of everyday experience. Additionally, the suspense of earning virtual rewards can elevate your emotional state and render you rejuvenated.
Recap
Gratis electronic gaming experiences present a wide selection of rewards for customers, involving pleasure, skill development, ease, communal engagement, and anxiety reduction and decompression. Whether you’re aiming to hone your leisure skills or solely derive entertainment, gratis electronic gaming games grant a advantageous and enjoyable encounter for customers of every degrees.
hcs777
Download Program 888 dan Menangkan Bonus: Petunjuk Pendek
**App 888 adalah opsi terbaik untuk Pengguna yang mengharapkan keseruan main daring yang menggembirakan dan menguntungkan. Bersama imbalan harian dan kemampuan memikat, aplikasi ini menawarkan menghadirkan keseruan main optimal. Disini manual singkat untuk memanfaatkan pemanfaatan Perangkat Lunak 888.
Instal dan Mulailah Raih
Sistem Tersedia:
App 888 memungkinkan di-download di Android, HP iOS, dan Windows. Mulai main dengan cepat di perangkat apa saja.
Imbalan Setiap Hari dan Keuntungan
Keuntungan Masuk Sehari-hari:
Mendaftar pada hari untuk meraih bonus sebesar 100K pada hari ketujuh.
Rampungkan Misi:
Dapatkan peluang lotere dengan menyelesaikan tugas terkait. Tiap aktivitas menawarkan Kamu sebuah opsi undi untuk mengklaim bonus mencapai 888K.
Pengklaiman Langsung:
Imbalan harus diterima sendiri di dalam perangkat lunak. Jangan lupa untuk mengambil hadiah tiap periode agar tidak habis masa berlakunya.
Mekanisme Pengeretan
Opsi Undian:
Setiap periode, Kamu bisa mengklaim satu kesempatan undian dengan menyelesaikan pekerjaan.
Jika peluang undi habis, rampungkan lebih banyak pekerjaan untuk mengambil extra peluang.
Tingkat Imbalan:
Ambil hadiah jika keseluruhan undian Pengguna melebihi 100K dalam sehari.
Peraturan Utama
Penerimaan Imbalan:
Bonus harus diambil manual dari aplikasi. Jika tidak, imbalan akan secara otomatis diambil ke akun pengguna Anda setelah satu waktu.
Peraturan Taruhan:
Keuntungan membutuhkan setidaknya satu bertaruh berlaku untuk dimanfaatkan.
Kesimpulan
Program 888 menyediakan keseruan berjudi yang mengasyikkan dengan hadiah tinggi. Download perangkat lunak hari ini dan rasakan kemenangan besar setiap periode!
Untuk detail lebih lanjut tentang promosi, deposit, dan program referensi, lihat page beranda program.
mantul88
rajaspin
Ashley JKT48: Idola yang Bercahaya Terang di Langit Idol
Siapa Ashley JKT48?
Siapakah tokoh muda berbakat yang mencuri perhatian sejumlah besar penyuka musik di Indonesia dan Asia Tenggara? Dialah Ashley Courtney Shintia, atau yang dikenal dengan nama panggungnya, Ashley JKT48. Bergabung dengan grup idola JKT48 pada masa 2018, Ashley dengan lekas menjadi salah satu anggota paling populer.
Biografi
Lahir di Jakarta pada tanggal 13 Maret 2000, Ashley memiliki darah Tionghoa-Indonesia. Beliau memulai perjalanannya di industri hiburan sebagai model dan pemeran, hingga akhirnya kemudian menjadi anggota dengan JKT48. Personanya yang periang, vokal yang bertenaga, dan kemahiran menari yang mengesankan menjadikannya idol yang sangat dicintai.
Penghargaan dan Pengakuan
Ketenaran Ashley telah diakui melalui aneka apresiasi dan pencalonan. Pada tahun 2021, ia meraih pengakuan “Anggota Paling Populer JKT48” di event JKT48 Music Awards. Ia juga diberi gelar sebagai “Idol Tercantik di Asia” oleh sebuah media daring pada masa 2020.
Fungsi dalam JKT48
Ashley memainkan peran krusial dalam kelompok JKT48. Beliau adalah member Tim KIII dan berfungsi sebagai penari utama dan penyanyi utama. Ashley juga terlibat sebagai bagian dari sub-unit “J3K” dengan Jessica Veranda dan Jennifer Rachel Natasya.
Karier Solo
Selain aktivitasnya di JKT48, Ashley juga mengembangkan perjalanan mandiri. Beliau telah merilis beberapa lagu single, termasuk “Myself” (2021) dan “Falling Down” (2022). Ashley juga telah bekerja sama dengan penyanyi lain, seperti Afgan dan Rossa.
Aktivitas Privat
Selain dunia pertunjukan, Ashley dikenal sebagai sosok yang rendah hati dan ramah. Ia suka menghabiskan jam dengan family dan sahabat-sahabatnya. Ashley juga memiliki kegemaran mewarnai dan memotret.
jonitogel
Instal Aplikasi 888 dan Dapatkan Bonus: Petunjuk Pendek
**App 888 adalah opsi unggulan untuk Pengguna yang membutuhkan permainan main online yang menggembirakan dan berjaya. Bersama bonus setiap hari dan fasilitas menarik, program ini siap menghadirkan aktivitas bermain paling baik. Disini instruksi pendek untuk memaksimalkan penggunaan Perangkat Lunak 888.
Download dan Segera Dapatkan
Layanan Tersedia:
Aplikasi 888 bisa diambil di HP Android, iOS, dan Laptop. Mulai bermain dengan praktis di media manapun.
Bonus Tiap Hari dan Bonus
Keuntungan Login Harian:
Login pada hari untuk meraih hadiah sampai 100K pada waktu ketujuh.
Tuntaskan Misi:
Peroleh opsi lotere dengan merampungkan pekerjaan terkait. Masing-masing tugas menyediakan Kamu satu kesempatan undian untuk mendapatkan hadiah sampai 888K.
Pengambilan Sendiri:
Bonus harus dikumpulkan manual di dalam program. Jangan lupa untuk mengklaim keuntungan pada hari agar tidak batal.
Sistem Pengeretan
Kesempatan Undi:
Masing-masing waktu, Para Pengguna bisa mendapatkan sebuah kesempatan undian dengan menyelesaikan pekerjaan.
Jika opsi lotere habis, rampungkan lebih banyak tugas untuk mendapatkan extra kesempatan.
Batas Keuntungan:
Ambil hadiah jika akumulasi lotere Para Pengguna lebih dari 100K dalam satu hari.
Aturan Pokok
Pengklaiman Imbalan:
Hadiah harus diklaim langsung dari program. Jika tidak, keuntungan akan otomatis diserahkan ke akun pengguna Anda setelah satu waktu.
Persyaratan Taruhan:
Imbalan memerlukan paling tidak satu betting valid untuk digunakan.
Kesimpulan
Program 888 menghadirkan aktivitas bermain yang menyenangkan dengan keuntungan besar. Instal perangkat lunak sekarang juga dan alamilah keberhasilan besar-besaran pada periode!
Untuk informasi lebih rinci tentang promo, top up, dan sistem rekomendasi, kunjungi laman utama perangkat lunak.
kangtoto
Inspirasi dari Ucapan Taylor Swift
Taylor Swift, seorang penyanyi dan komposer terkenal, tidak hanya dikenal karena nada yang indah dan vokal yang merdu, tetapi juga karena syair-syair karyanya yang bermakna. Dalam lirik-liriknya, Swift sering menggambarkan beraneka ragam aspek kehidupan, mulai dari cinta hingga tantangan hidup. Berikut ini adalah beberapa kutipan menginspirasi dari lagu-lagunya, beserta maknanya.
“Mungkin yang paling baik belum tiba.” – “All Too Well”
Arti: Bahkan di saat-saat sulit, senantiasa ada secercah harapan dan kemungkinan untuk hari yang lebih baik.
Lirik ini dari lagu “All Too Well” menyadarkan kita kalau biarpun kita barangkali mengalami masa sulit saat ini, senantiasa ada potensi bahwa hari esok akan memberikan perubahan yang lebih baik. Ini adalah pesan harapan yang menguatkan, merangsang kita untuk bertahan dan tidak menyerah, lantaran yang terbaik mungkin belum datang.
“Aku akan tetap bertahan karena aku tak bisa mengerjakan apa pun tanpa dirimu.” – “You Belong with Me”
Makna: Menemukan kasih dan dukungan dari orang lain dapat menyediakan kita kekuatan dan kemauan keras untuk melanjutkan melewati kesulitan.
Online gambling sites are steadily more widespread, providing various incentives to entice new users. One of the most enticing offers is the no upfront deposit bonus, a promotion that enables users to try their hand without any financial risk. This write-up explores the upsides of no upfront deposit bonuses and highlights how they can improve their effectiveness.
What is a No Deposit Bonus?
A no upfront deposit bonus is a kind of casino promotion where gamblers are given bonus credits or free plays without the need to submit any of their own cash. This permits casino enthusiasts to explore the online casino, test out different game options and have a chance to win real funds, all without any initial expenditure.
Advantages of No Deposit Bonuses
Risk-Free Exploration
No upfront deposit bonuses offer a safe way to try out internet casinos. Players can evaluate multiple games, get to know the gaming environment, and assess the overall gaming experience without investing their own funds. This is notably helpful for newcomers who may not be aware of virtual casinos.
Chance to Win Real Money
One of the most attractive elements of no upfront deposit bonuses is the opportunity to earn real cash. Although the amounts may be small, any earnings earned from the bonus can generally be withdrawn after meeting the casino’s staking criteria. This introduces an element of thrill and gives a possible financial return without any upfront investment.
Learning Opportunity
No upfront deposit bonuses offer a wonderful opportunity to grasp how various games are played. Gamblers can experiment with methods, understand the guidelines of the casino games, and become more confident without worrying about forfeiting their own funds. This can be notably helpful for difficult gaming activities like blackjack.
Conclusion
Free bonuses provide numerous advantages for players, like risk-free investigation, the potential to get real rewards, and valuable educational chances. As the industry keeps to grow, the appeal of no-deposit bonuses is likely to increase.
sweepstakes casino
Investigating Lottery Casinos: An Exciting and Convenient Gambling Option
Prelude
Promotion gambling platforms are transforming into a preferred choice for participants searching for an exciting and legitimate approach to partake in online betting. Differing from standard internet-based betting sites, lottery gaming hubs work under alternative authorized frameworks, allowing them to present events and awards without coming under the identical regulations. This piece explores the principle of lottery gambling platforms, their benefits, and why they are drawing a increasing figure of players.
Understanding Sweepstakes Casinos
A contest casino runs by offering users with internet money, which can be used to experience competitions. Gamers can achieve more online funds or tangible awards, including cash. The key disparity from classic betting sites is that players do not acquire funds instantly but receive it through advertising campaigns, such as get a service or taking part in a no-cost entry lottery. This framework facilitates sweepstakes gaming hubs to operate legitimately in many jurisdictions where classic online gaming is regulated.
Pro88
Its like you read my mind! You seem to know so much approximately this, like you wrote the guide in it or something. I feel that you could do with some % to drive the message house a bit, however other than that, this is fantastic blog. An excellent read. I’ll definitely be back.
https://codemobile.ca/rupiahtoto
It’s remarkable for me to have a website, which is valuable in favor of my experience. thanks admin
娛樂城評價
10 大線上娛樂城評價實測|線上賭場推薦排名一次看!
在台灣,各式線上娛樂城如同雨後春筍般湧現,競爭激烈。對於一般的玩家來說,選擇一家可靠的線上賭場可說是至關重要的。今天,我們將分享十家最新娛樂城評價及實測的體驗,全面分析它們的優缺點,幫助玩家避免陷入詐騙網站的風險,確保選擇一個安全可靠的娛樂城平台。
娛樂城評價五大標準
在經過我們團隊的多次進行娛樂城實測後,得出了一個值得信任的線上娛樂城平台須包含的幾個要素,所以我們整理了評估娛樂城的五大標準:
條件一:金流帳戶安全性(儲值與出金)
條件二:博弈遊戲種類的豐富性
條件三:線上24小時客服、服務效率與態度
條件四:提供的優惠活動CP值
條件五:真實娛樂城玩家們的口碑評語
通常我們談到金流安全時,指的是對玩家風險的控制能力。一家優秀的娛樂城應當只在有充分證據證明玩家使用非法套利程式,或發現代理和玩家之間有對壓詐騙行為時,才暫時限制該玩家的金流。若無正當理由,則不應隨意限制玩家的金流,以防給玩家造成被詐騙的錯覺。
至於娛樂城的遊戲類型,主要可以分為以下七大類:真人視訊百家樂、彩票遊戲、體育投注、電子老虎機、棋牌遊戲、捕魚機遊戲及電子競技投注。這些豐富多樣的遊戲類型提供了廣泛的娛樂選擇。
十大娛樂城實測評價排名
基於上述五項標準,我們對以下十家現金版娛樂城進行了的實測分析,並對此給出了以下的排名結果:
RG富遊娛樂城
bet365娛樂城
DG娛樂城
yabo亞博娛樂城
PM娛樂城
1XBET娛樂城
九州娛樂城
LEO娛樂城
王者娛樂城
THA娛樂城
https://avpkw.ca/maxwin138
娛樂城
富遊娛樂城評價:2024年最新評價
推薦指數 : ★★★★★ ( 5.0/5 )
富遊娛樂城作為目前最受歡迎的博弈網站之一,在台灣擁有最高的註冊人數。
RG富遊以安全、公正、真實和順暢的品牌保證,贏得了廣大玩家的信賴。富遊線上賭場不僅提供了豐富多樣的遊戲種類,還有眾多吸引人的優惠活動。在出金速度方面,獲得無數網紅和網友的高度評價,確保玩家能享有無憂的博弈體驗。
推薦要點
新手首選: 富遊娛樂城,2024年評選首選,提供專為新手打造的豐富教學和獨家優惠。
一存雙收: 首存1000元,立獲1000元獎金,僅需1倍流水,新手友好。
免費體驗: 新玩家享免費體驗金,暢遊各式遊戲,開啟無限可能。
優惠多元: 活動豐富,流水要求低,適合各類型玩家。
玩家首選: 遊戲多樣,服務優質,是新手與老手的最佳賭場選擇。
富遊娛樂城詳情資訊
賭場名稱 : RG富遊
創立時間 : 2019年
賭場類型 : 現金版娛樂城
博弈執照 : 馬爾他牌照(MGA)認證、英屬維爾京群島(BVI)認證、菲律賓(PAGCOR)監督競猜牌照
遊戲類型 : 真人百家樂、運彩投注、電子老虎機、彩票遊戲、棋牌遊戲、捕魚機遊戲
存取速度 : 存款5秒 / 提款3-5分
軟體下載 : 支援APP,IOS、安卓(Android)
線上客服 : 需透過官方LINE
富遊娛樂城優缺點
優點
台灣註冊人數NO.1線上賭場
首儲1000贈1000只需一倍流水
擁有體驗金免費體驗賭場
網紅部落客推薦保證出金線上娛樂城
缺點
需透過客服申請體驗金
富遊娛樂城存取款方式
存款方式
提供四大超商(全家、7-11、萊爾富、ok超商)
虛擬貨幣ustd存款
銀行轉帳(各大銀行皆可)
取款方式
網站內申請提款及可匯款至綁定帳戶
現金1:1出金
富遊娛樂城平台系統
真人百家 — RG真人、DG真人、歐博真人、DB真人(原亞博/PM)、SA真人、OG真人、WM真人
體育投注 — SUPER體育、鑫寶體育、熊貓體育(原亞博/PM)
彩票遊戲 — 富遊彩票、WIN 539
電子遊戲 —RG電子、ZG電子、BNG電子、BWIN電子、RSG電子、GR電子(好路)
棋牌遊戲 —ZG棋牌、亞博棋牌、好路棋牌、博亞棋牌
電競遊戲 — 熊貓體育
捕魚遊戲 —ZG捕魚、RSG捕魚、好路GR捕魚、DB捕魚
娛樂城推薦
bocor88
bocor88
2024娛樂城推薦,經過玩家實測結果出爐Top5!
2024娛樂城排名是這五間上榜,玩家尋找娛樂城無非就是要找穩定出金娛樂城,遊戲體驗良好、速度流暢,Ace博評網都幫你整理好了,給予娛樂城新手最佳的指南,不再擔心被黑網娛樂城詐騙!
2024娛樂城簡述
在現代,2024娛樂城數量已經超越以前,面對琳瑯滿目的娛樂城品牌,身為新手的玩家肯定難以辨別哪間好、哪間壞。
好的平台提供穩定的速度與遊戲體驗,穩定的系統與資訊安全可以保障用戶的隱私與資料,不用擔心收到傳票與任何網路威脅,這些線上賭場也提供合理的優惠活動給予玩家。
壞的娛樂城除了會騙取你的金錢之外,也會打著不實的廣告、優惠滿滿,想領卻是一場空!甚至有些平台還沒辦法登入,入口網站也是架設用來騙取新手儲值進他們口袋,這些黑網娛樂城是玩家必須避開的風險!
評測2024娛樂城的標準
Ace這次從網路上找來五位使用過娛樂城資歷2年以上的老玩家,給予他們使用各大娛樂城平台,最終選出Top5,而評選標準為下列這些條件:
以玩家觀點出發,優先考量玩家利益
豐富的遊戲種類與卓越的遊戲體驗
平台的信譽及其安全性措施
客服團隊的回應速度與服務品質
簡便的儲值流程和多樣的存款方法
吸引人的優惠活動方案
前五名娛樂城表格
賭博網站排名 線上賭場 平台特色 玩家實測評價
No.1 富遊娛樂城 遊戲選擇豐富,老玩家優惠多 正面好評
No.2 bet365娛樂城 知名大廠牌,運彩盤口選擇多 介面流暢
No.3 亞博娛樂城 多語言支持,介面簡潔順暢 賽事豐富
No.4 PM娛樂城 撲克牌遊戲豐富,選擇多元 直播順暢
No.5 1xbet娛樂城 直播流暢,安全可靠 佳評如潮
線上娛樂城玩家遊戲體驗評價分享
網友A:娛樂城平台百百款,富遊娛樂城是我3年以來長期使用的娛樂城,別人有的系統他們都有,出金也沒有被卡過,比起那些玩娛樂城還會收到傳票的娛樂城,富遊真的很穩定,值得推薦。
網友B:bet365中文的介面簡約,還有超多體育賽事盤口可以選擇,此外賽事大部分也都有附上直播來源,不必擔心看不到賽事最新狀況,全螢幕還能夠下單,真的超方便!
網友C:富遊娛樂城除了第一次儲值有優惠之外,儲值到一定金額還有好禮五選一,實用又方便,有問題的時候也有客服隨時能夠解答。
網友D:從大陸來台灣工作,沒想到台灣也能玩到亞博體育,這是以前在大陸就有使用的平台,雖然不是簡體字,但使用介面完全沒問題,遊戲流暢、速度比以前使用還更快速。
網友E:看玖壹壹MV發現了PM娛樂城這個大品牌,PM的真人百家樂沒有輸給在澳門實地賭場,甚至根本不用出門,超級方便的啦!
https://tennissherbrooke.ca/jadwal-piala-dunia-u-17
在现代,在线赌场提供了多种便捷的存款和取款方式。对于较大金额的存款,您可以选择中国信托、台中银行、合作金库、台新银行、国泰银行或中华邮政。这些银行提供的服务覆盖金额范围从$1000到$10万,确保您的资金可以安全高效地转入赌场账户。
如果您需要进行较小金额的存款,可以选择通过便利店充值。7-11、全家、莱尔富和OK超商都提供这种服务,适用于金额范围在$1000到$2万之间的充值。通过这些便利店,您可以轻松快捷地完成资金转账,无需担心银行的营业时间或复杂的操作流程。
在进行娱乐场提款时,您可以选择通过各大银行转账或ATM转账。这些方法不仅安全可靠,而且非常方便,适合各种提款需求。最低提款金额为$1000,而上限则没有限制,确保您可以灵活地管理您的资金。
在选择在线赌场时,玩家评价和推荐也是非常重要的。许多IG网红和部落客,如丽莎、穎柔、猫少女日记-Kitty等,都对一些知名的娱乐场给予了高度评价。这些推荐不仅帮助您找到可靠的娱乐场所,还能确保您在游戏中享受到最佳的用户体验。
总体来说,在线赌场通过提供多样化的存款和取款方式,以及得到广泛认可的服务质量,正在不断吸引更多的玩家。无论您选择通过银行还是便利店进行充值,都能体验到快速便捷的操作。同时,通过查看玩家的真实评价和推荐,您也能更有信心地选择合适的娱乐场,享受安全、公正的游戏环境。
娛樂城
在现代,在线赌场提供了多种便捷的存款和取款方式。对于较大金额的存款,您可以选择中国信托、台中银行、合作金库、台新银行、国泰银行或中华邮政。这些银行提供的服务覆盖金额范围从$1000到$10万,确保您的资金可以安全高效地转入赌场账户。
如果您需要进行较小金额的存款,可以选择通过便利店充值。7-11、全家、莱尔富和OK超商都提供这种服务,适用于金额范围在$1000到$2万之间的充值。通过这些便利店,您可以轻松快捷地完成资金转账,无需担心银行的营业时间或复杂的操作流程。
在进行娱乐场提款时,您可以选择通过各大银行转账或ATM转账。这些方法不仅安全可靠,而且非常方便,适合各种提款需求。最低提款金额为$1000,而上限则没有限制,确保您可以灵活地管理您的资金。
在选择在线赌场时,玩家评价和推荐也是非常重要的。许多IG网红和部落客,如丽莎、穎柔、猫少女日记-Kitty等,都对一些知名的娱乐场给予了高度评价。这些推荐不仅帮助您找到可靠的娱乐场所,还能确保您在游戏中享受到最佳的用户体验。
总体来说,在线赌场通过提供多样化的存款和取款方式,以及得到广泛认可的服务质量,正在不断吸引更多的玩家。无论您选择通过银行还是便利店进行充值,都能体验到快速便捷的操作。同时,通过查看玩家的真实评价和推荐,您也能更有信心地选择合适的娱乐场,享受安全、公正的游戏环境。
在现代,在线赌场提供了多种便捷的存款和取款方式。对于较大金额的存款,您可以选择中国信托、台中银行、合作金库、台新银行、国泰银行或中华邮政。这些银行提供的服务覆盖金额范围从$1000到$10万,确保您的资金可以安全高效地转入赌场账户。
如果您需要进行较小金额的存款,可以选择通过便利店充值。7-11、全家、莱尔富和OK超商都提供这种服务,适用于金额范围在$1000到$2万之间的充值。通过这些便利店,您可以轻松快捷地完成资金转账,无需担心银行的营业时间或复杂的操作流程。
在进行娱乐场提款时,您可以选择通过各大银行转账或ATM转账。这些方法不仅安全可靠,而且非常方便,适合各种提款需求。最低提款金额为$1000,而上限则没有限制,确保您可以灵活地管理您的资金。
在选择在线赌场时,玩家评价和推荐也是非常重要的。许多IG网红和部落客,如丽莎、穎柔、猫少女日记-Kitty等,都对一些知名的娱乐场给予了高度评价。这些推荐不仅帮助您找到可靠的娱乐场所,还能确保您在游戏中享受到最佳的用户体验。
总体来说,在线赌场通过提供多样化的存款和取款方式,以及得到广泛认可的服务质量,正在不断吸引更多的玩家。无论您选择通过银行还是便利店进行充值,都能体验到快速便捷的操作。同时,通过查看玩家的真实评价和推荐,您也能更有信心地选择合适的娱乐场,享受安全、公正的游戏环境。
Player台灣線上娛樂城遊戲指南與評測
台灣最佳線上娛樂城遊戲的終極指南!我們提供專業評測,分析熱門老虎機、百家樂、棋牌及其他賭博遊戲。從遊戲規則、策略到選擇最佳娛樂城,我們全方位覆蓋,協助您更安全的遊玩。
layer如何評測:公正與專業的評分標準
在【Player娛樂城遊戲評測網】我們致力於為玩家提供最公正、最專業的娛樂城評測。我們的評測過程涵蓋多個關鍵領域,旨在確保玩家獲得可靠且全面的信息。以下是我們評測娛樂城的主要步驟:
安全與公平性
安全永遠是我們評測的首要標準。我們審查每家娛樂城的執照資訊、監管機構以及使用的隨機數生成器,以確保其遊戲結果的公平性和隨機性。
02.
遊戲品質與多樣性
遊戲的品質和多樣性對於玩家體驗至關重要。我們評估遊戲的圖形、音效、用戶介面和創新性。同時,我們也考量娛樂城提供的遊戲種類,包括老虎機、桌遊、即時遊戲等。
03.
娛樂城優惠與促銷活動
我們仔細審視各種獎勵計劃和促銷活動,包括歡迎獎勵、免費旋轉和忠誠計劃。重要的是,我們也檢查這些優惠的賭注要求和條款條件,以確保它們公平且實用。
04.
客戶支持
優質的客戶支持是娛樂城質量的重要指標。我們評估支持團隊的可用性、響應速度和專業程度。一個好的娛樂城應該提供多種聯繫方式,包括即時聊天、電子郵件和電話支持。
05.
銀行與支付選項
我們檢查娛樂城提供的存款和提款選項,以及相關的處理時間和手續費。多樣化且安全的支付方式對於玩家來說非常重要。
06.
網站易用性、娛樂城APP體驗
一個直觀且易於導航的網站可以顯著提升玩家體驗。我們評估網站的設計、可訪問性和移動兼容性。
07.
玩家評價與反饋
我們考慮真實玩家的評價和反饋。這些資料幫助我們了解娛樂城在實際玩家中的表現。
娛樂城常見問題
娛樂城是什麼?
娛樂城是什麼?娛樂城是台灣對於線上賭場的特別稱呼,線上賭場分為幾種:現金版、信用版、手機娛樂城(娛樂城APP),一般來說,台灣人在稱娛樂城時,是指現金版線上賭場。
線上賭場在別的國家也有別的名稱,美國 – Casino, Gambling、中國 – 线上赌场,娱乐城、日本 – オンラインカジノ、越南 – Nhà cái。
娛樂城會被抓嗎?
在台灣,根據刑法第266條,不論是實體或線上賭博,參與賭博的行為可處最高5萬元罰金。而根據刑法第268條,為賭博提供場所並意圖營利的行為,可能面臨3年以下有期徒刑及最高9萬元罰金。一般賭客若被抓到,通常被視為輕微罪行,原則上不會被判處監禁。
信用版娛樂城是什麼?
信用版娛樂城是一種線上賭博平台,其中的賭博活動不是直接以現金進行交易,而是基於信用系統。在這種模式下,玩家在進行賭博時使用虛擬的信用點數或籌碼,這些點數或籌碼代表了一定的貨幣價值,但實際的金錢交易會在賭博活動結束後進行結算。
現金版娛樂城是什麼?
現金版娛樂城是一種線上博弈平台,其中玩家使用實際的金錢進行賭博活動。玩家需要先存入真實貨幣,這些資金轉化為平台上的遊戲籌碼或信用,用於參與各種賭場遊戲。當玩家贏得賭局時,他們可以將這些籌碼或信用兌換回現金。
娛樂城體驗金是什麼?
娛樂城體驗金是娛樂場所為新客戶提供的一種免費遊玩資金,允許玩家在不需要自己投入任何資金的情況下,可以進行各類遊戲的娛樂城試玩。這種體驗金的數額一般介於100元到1,000元之間,且對於如何使用這些體驗金以達到提款條件,各家娛樂城設有不同的規則。
สล็อต
สล็อตแมชชีนเว็บตรง: ความสนุกสนานที่ผู้เล่นไม่ควรพลาด
การเล่นสล็อตในยุคนี้เป็นที่นิยมเพิ่มมากขึ้น เนื่องจากความสะดวกสบายที่ผู้ใช้สามารถเข้าถึงได้จากทุกหนทุกแห่งได้ตลอดเวลา โดยไม่ต้องใช้เวลาการเดินทางถึงคาสิโนจริง ๆ ในเนื้อหานี้ เราจะกล่าวถึง “สล็อตแมชชีน” และความเพลิดเพลินที่คุณจะได้พบในเกมสล็อตออนไลน์เว็บตรง
ความสะดวกในการเล่นสล็อตออนไลน์
หนึ่งในเหตุผลสล็อตที่เว็บตรงเป็นที่ยอดนิยมอย่างยิ่ง คือความสะดวกที่นักเดิมพันมี คุณสามารถเล่นได้ทุกหนทุกแห่งทุกเวลา ไม่ว่าจะเป็นที่บ้านของคุณ ที่ทำงาน หรือแม้กระทั่งขณะเดินทางอยู่ สิ่งที่คุณควรมีคือเครื่องมือที่ต่ออินเทอร์เน็ตได้ ไม่ว่าจะเป็นสมาร์ทโฟน แท็บเล็ต หรือแล็ปท็อป
นวัตกรรมกับสล็อตเว็บตรง
การเล่นเกมสล็อตในยุคนี้ไม่เพียงแต่สะดวก แต่ยังมาพร้อมกับเทคโนโลยีใหม่ล่าสุดอีกด้วย สล็อตเว็บตรงใช้เทคโนโลยี HTML5 ซึ่งทำให้ท่านไม่ต้องกังวลใจเกี่ยวกับการลงซอฟต์แวร์หรือแอปพลิเคชันเพิ่มเติม แค่ใช้เบราว์เซอร์บนอุปกรณ์ที่คุณมีและเข้าไปที่เว็บไซต์ของเรา คุณก็สามารถเริ่มเล่นเกมสล็อตได้ทันที
ความหลากหลายของเกมของสล็อต
สล็อตที่เว็บตรงมาพร้อมกับตัวเลือกหลากหลายของเกมให้เลือกที่ท่านสามารถเลือกเล่นได้ ไม่ว่าจะเป็นเกมสล็อตแบบคลาสสิกหรือเกมที่มีฟีเจอร์พิเศษและโบนัสมากมาย ท่านจะพบเจอมีเกมที่ให้เล่นมากมาย ซึ่งทำให้ไม่เบื่อกับการเล่นสล็อต
รองรับทุกอุปกรณ์ที่ใช้
ไม่ว่าท่านจะใช้สมาร์ทโฟนระบบ Androidหรือ iOS ผู้เล่นก็สามารถเล่นเกมสล็อตออนไลน์ได้ไม่มีสะดุด เว็บไซต์ของเราสนับสนุนระบบและทุกเครื่องมือ ไม่ว่าจะเป็นโทรศัพท์มือถือใหม่ล่าสุดหรือรุ่นเก่าแก่ หรือถึงแม้จะเป็นแท็บเล็ทและโน้ตบุ๊ก ท่านก็สามารถเพลิดเพลินกับเกมสล็อตได้ได้อย่างครบถ้วน
สล็อตทดลองฟรี
สำหรับผู้ที่ยังใหม่กับการเล่นสล็อต หรือยังไม่มั่นใจเกี่ยวกับเกมที่อยากเล่น PG Slot ยังมีระบบทดลองเล่นเกมสล็อต ท่านสามารถทดลองเล่นได้ทันทีโดยไม่ต้องลงทะเบียนหรือฝากเงินก่อน การทดลองเล่นเกมสล็อตนี้จะช่วยให้ท่านเรียนรู้วิธีการเล่นและเข้าใจเกมได้โดยไม่ต้องเสียเงิน
โบนัสและโปรโมชั่น
ข้อดีอีกอย่างหนึ่งของการเล่นเกมสล็อตกับ PG Slot คือมีโปรโมชันและโบนัสมากมายสำหรับผู้เล่น ไม่ว่าผู้เล่นจะเป็นสมาชิกใหม่หรือสมาชิกเก่า คุณสามารถได้รับโบนัสและโปรโมชันต่าง ๆ ได้อย่างต่อเนื่อง ซึ่งจะเพิ่มโอกาสชนะและเพิ่มความบันเทิงในเกม
สรุป
การเล่นสล็อตออนไลน์ที่ PG Slot เป็นการลงทุนที่คุ้มค่า ท่านจะได้รับความเพลิดเพลินและความสะดวกสบายจากการเล่นเกม นอกจากนี้ยังมีโอกาสชนะรางวัลและโบนัสเพียบ ไม่ว่าท่านจะใช้มือถือ แท็บเล็ทหรือคอมพิวเตอร์รุ่นใด ก็สามารถร่วมสนุกกับเราได้ทันที อย่ารอช้า สมัครสมาชิกและเริ่มเล่น PG Slot ทันที
เมื่อเทียบ ไซต์ PG Slots ในขณะที่ มี ประโยชน์ หลายประการ เมื่อเทียบกับ คาสิโนแบบ ดั้งเดิม, โดยมาก ใน ปัจจุบัน. ข้อดีสำคัญ เหล่านี้ ประกอบด้วย:
ความสะดวก: คุณ สามารถใช้งาน สล็อตออนไลน์ได้ ตลอด 24 ชั่วโมง จาก ทุกอย่าง, ให้ ผู้เล่นสามารถ ทดลอง ได้ ทุกสถานที่ โดยไม่ต้อง เสียเวลาไป ไปคาสิโนแบบ เดิม ๆ
เกมหลากประเภท: สล็อตออนไลน์ นำเสนอ เกม ที่ หลากหลายรูปแบบ, เช่น สล็อตคลาสสิค หรือ ตัวเกม ที่มี ฟีเจอร์ และรางวัล พิเศษ, ไม่ส่งผลให้ ความเบื่อหน่าย ในเกม
โปรโมชั่น และประโยชน์: สล็อตออนไลน์ ส่วนใหญ่ มี โปรโมชั่น และโบนัส เพื่อยกระดับ โอกาส ในการ ชนะ และ ปรับปรุง ความผ่อนคลาย ให้กับเกม
ความเชื่อมั่น และ ความไว้วางใจ: สล็อตออนไลน์ โดยทั่วไป มี มาตรการรักษาความปลอดภัย ที่ ดี, และ พึ่งพาได้ ว่า ข้อมูลลับ และ การชำระเงิน จะได้รับความ คุ้มครอง
การสนับสนุนลูกค้า: PG Slots ใช้ ทีมงาน มืออาชีพ ที่มุ่งมั่น ดูแล ตลอดเวลาไม่หยุด
การเล่นบนอุปกรณ์เคลื่อนที่: สล็อต PG รองรับ การเล่นบนมือถือ, ทำให้ ผู้เล่นสามารถเล่น ในทุกที่
เล่นฟรี: ของ ผู้เล่นรายใหม่, PG ยังให้บริการ ทดลองเล่นโดยไม่เสียค่าใช้จ่าย อีกด้วย, เพื่อให้ คุณ ทำความเข้าใจ วิธีใช้ และเรียนรู้ เกมก่อน เล่นด้วยเงินจริง
สล็อต PG มีคุณสมบัติ คุณสมบัติที่ดี มากก ที่ ส่งผล ให้ได้รับความนิยม ในวันนี้, ส่งเสริม ระดับ ความสนุกสนาน ให้กับเกมด้วย.
Thank you for your tireless pursuit of excellence in your writing.
ทดลองเล่นสล็อต pg เว็บ ตรง
ความรู้สึกการทดลองเล่นเกมสล็อตแมชชีน PG บนพอร์ทัลพนันโดยตรง: เริ่มการเดินทางแห่งความสุขที่ไม่มีที่สิ้นสุด
ในกรณีของนักพนันที่กำลังมองหาการพบเจอเกมที่ไม่ซ้ำใคร และหวังหาแหล่งพนันที่มีความน่าเชื่อถือ, การลองเล่นสล็อต PG บนแพลตฟอร์มตรงนับว่าเป็นตัวเลือกที่น่าดึงดูดอย่างมาก. อันเนื่องมาจากความหลากหลายของเกมสล็อตแมชชีนที่มีให้เลือกเล่นมากมาย, ผู้เล่นจะได้สัมผัสกับโลกแห่งความเร้าใจและความเพลิดเพลินที่ไม่มีที่สิ้นสุด.
เว็บไซต์การเดิมพันตรงนี้ มอบการเล่นเกมการเล่นที่น่าเชื่อถือ น่าเชื่อถือ และรองรับความต้องการของนักเสี่ยงโชคได้เป็นอย่างดี. ไม่ว่าท่านจะคุณจะโปรดปรานสล็อตแมชชีนแบบคลาสสิคที่คุ้นเคย หรืออยากทดลองสัมผัสเกมแปลกใหม่ที่มีคุณสมบัติพิเศษและรางวัลล้นหลาม, เว็บตรงนี้นี้ก็มีให้เลือกอย่างหลากหลายชนิด.
อันเนื่องมาจากระบบการทดลองเล่นสล็อต PG โดยไม่เสียค่าใช้จ่าย, ผู้เล่นจะได้จังหวะเรียนรู้วิธีการเล่นเดิมพันและทดลองกลยุทธ์ต่างๆนาๆ ก่อนเริ่มใช้เงินลงทุนด้วยเงินจริง. นี่นับว่าโอกาสอันยอดเยี่ยมที่จะเสริมความพร้อมสมบูรณ์และเสริมโอกาสในการได้รับรางวัลใหญ่ใหญ่.
ไม่ว่าคุณจะคุณจะอยากได้ความสนุกสนานที่เคยชิน หรือการพิชิตแปลกใหม่, เกมสล็อตแมชชีน PG บนแพลตฟอร์มเดิมพันโดยตรงก็มีให้เลือกอย่างหลากหลาย. ท่านจะได้ประสบกับการสัมผัสการเล่นเกมที่น่าตื่นเต้นเร้าใจ น่ารื่นเริง และสนุกเพลิดเพลินไปกับโอกาสที่ดีในการชนะโบนัสมหาศาล.
อย่ารอ, ร่วมสนุกทดลองเล่นสล็อต PG บนเว็บเดิมพันตรงนี้ตอนนี้ และเจอโลกแห่งความบันเทิงแห่งความบันเทิงที่ปลอดภัย น่าติดตามต่อ และพร้อมด้วยความเพลิดเพลินรอคอยท่าน. ประสบความรื่นเริง, ความสุข และโอกาสในการได้รางวัลใหญ่มหาศาล. เริ่มเข้าสู่การประสบความสำเร็จในวงการเกมออนไลน์เดี๋ยวนี้!
บาคาร่า
הימורי ספורטיביים – הימורים באינטרנט
הימור ספורטיביים נהיו לאחד התחומים הצומחים ביותר בהימור באינטרנט. שחקנים מסוגלים להמר על תוצאותיהם של אירועים ספורט מוכרים כמו כדורגל, כדורסל, טניס ועוד. האפשרויות להימור הן מרובות, כולל תוצאתו המשחק, כמות הגולים, כמות הפעמים ועוד. להלן דוגמאות של למשחקים נפוצים שעליהם ניתן להתערב:
כדורגל: ליגת אלופות, מונדיאל, ליגות מקומיות
כדור סל: ליגת NBA, ליגת יורוליג, תחרויות בינלאומיות
טניס: טורניר ווימבלדון, אליפות ארה”ב הפתוחה, אליפות צרפת הפתוחה
פוקר ברשת – הימור ברשת
משחק הפוקר באינטרנט הוא אחד ממשחקי ההימור הנפוצים ביותר בימינו. שחקנים מסוגלים להתחרות מול יריבים מכל רחבי העולם במגוון גרסאות של המשחק , לדוגמה טקסס הולדם, Omaha, Stud ועוד. ניתן לגלות תחרויות ומשחקי במגוון דרגות ואפשרויות מגוונות. אתרי פוקר המובילים מציעים:
מבחר רב של גרסאות פוקר
טורנירים שבועיות וחודשיים עם פרסים כספיים גבוהים
שולחנות המשחק למשחק מהיר ולטווח הארוך
תוכניות נאמנות ללקוחות ומועדוני עם הטבות בלעדיות
בטיחות והגינות
בעת הבחירה בפלטפורמה להימורים ברשת, חשוב לבחור גם אתרים מורשים ומפוקחים המציעים גם סביבה למשחק בטוחה והגיונית. אתרים אלה משתמשים בטכנולוגיית הצפנה מתקדמת להבטחה על נתונים אישיים ופיננסי, וכן בתוכנות גנרטור מספרים רנדומליים (RNG) כדי לוודא הגינות במשחקי ההימורים.
מעבר לכך, חשוב לשחק באופן אחראי תוך קביעת מגבלות הימור אישיות של השחקן. מרבית אתרי ההימורים מאפשרים למשתתפים להגדיר מגבלות להפסדים ופעילויות, וגם לנצל כלים נגד התמכרויות. שחקו בתבונה ואל תרדפו אחר הפסדים.
המדריך השלם לקזינו באינטרנט, משחקי ספורט ופוקר ברשת
ההימורים באינטרנט מציעים עולם שלם של הזדמנויות מרתקות לשחקנים, החל מקזינו באינטרנט וכל משחקי ספורט ופוקר באינטרנט. בעת בחירת פלטפורמת הימורים, חשוב לבחור גם אתרי הימורים המפוקחים המציעים גם סביבה משחק מאובטחת והוגנת. זכרו לשחק באופן אחראי תמיד – ההימורים ברשת נועדו להיות מבדרים ולא לגרום לבעיות פיננסיות או חברתיות.
pro88
Exploring Pro88: A Comprehensive Look at a Leading Online Gaming Platform
In the world of online gaming, Pro88 stands out as a premier platform known for its extensive offerings and user-friendly interface. As a key player in the industry, Pro88 attracts gamers with its vast array of games, secure transactions, and engaging community features. This article delves into what makes Pro88 a preferred choice for online gaming enthusiasts.
A Broad Selection of Games
One of the main attractions of Pro88 is its diverse game library. Whether you are a fan of classic casino games, modern video slots, or interactive live dealer games, Pro88 has something to offer. The platform collaborates with top-tier game developers to ensure a rich and varied gaming experience. This extensive selection not only caters to seasoned gamers but also appeals to newcomers looking for new and exciting gaming options.
User-Friendly Interface
Navigating through Pro88 is a breeze, thanks to its intuitive and well-designed interface. The website layout is clean and organized, making it easy for users to find their favorite games, check their account details, and access customer support. The seamless user experience is a significant factor in retaining users and encouraging them to explore more of what the platform has to offer.
Security and Fair Play
Pro88 prioritizes the safety and security of its users. The platform employs advanced encryption technologies to protect personal and financial information. Additionally, Pro88 is committed to fair play, utilizing random number generators (RNGs) to ensure that all game outcomes are unbiased and random. This dedication to security and fairness helps build trust and reliability among its user base.
Promotions and Bonuses
Another highlight of Pro88 is its generous promotions and bonuses. New users are often welcomed with attractive sign-up bonuses, while regular players can take advantage of ongoing promotions, loyalty rewards, and special event bonuses. These incentives not only enhance the gaming experience but also provide additional value to the users.
Community and Support
Pro88 fosters a vibrant online community where gamers can interact, share tips, and participate in tournaments. The platform also offers robust customer support to assist with any issues or inquiries. Whether you need help with game rules, account management, or technical problems, Pro88’s support team is readily available to provide assistance.
Mobile Compatibility
In today’s fast-paced world, mobile compatibility is crucial. Pro88 is optimized for mobile devices, allowing users to enjoy their favorite games on the go. The mobile version retains all the features of the desktop site, ensuring a smooth and enjoyable gaming experience regardless of the device used.
Conclusion
Pro88 has established itself as a leading online gaming platform by offering a vast selection of games, a user-friendly interface, robust security measures, and excellent customer support. Whether you are a casual gamer or a hardcore enthusiast, Pro88 provides a comprehensive and enjoyable gaming experience. Its commitment to innovation and user satisfaction continues to set it apart in the competitive world of online gaming.
Explore the world of Pro88 today and discover why it is the go-to platform for online gaming aficionados.
슬롯 게임 무료
Fang Jifan은 매우 직접적으로 말했습니다. “닥쳐, 당신이 무엇인지 말하십시오.”
bocor88
bocor88
娛樂城
台灣線上娛樂城是指通過互聯網提供賭博和娛樂服務的平台。這些平台主要針對台灣用戶,但實際上可能在境外運營。以下是一些關於台灣線上娛樂城的重要信息:
1. 服務內容:
– 線上賭場遊戲(如老虎機、撲克、輪盤等)
– 體育博彩
– 彩票遊戲
– 真人荷官遊戲
2. 特點:
– 全天候24小時提供服務
– 可通過電腦或移動設備訪問
– 常提供優惠活動和獎金來吸引玩家
3. 支付方式:
– 常見支付方式包括銀行轉賬、電子錢包等
– 部分平台可能接受加密貨幣
4. 法律狀況:
– 在台灣,線上賭博通常是非法的
– 許多線上娛樂城實際上是在國外註冊運營
5. 風險:
– 由於缺乏有效監管,玩家可能面臨財務風險
– 存在詐騙和不公平遊戲的可能性
– 可能導致賭博成癮問題
6. 爭議:
– 這些平台的合法性和道德性一直存在爭議
– 監管機構試圖遏制這些平台的發展,但效果有限
重要的是,參與任何形式的線上賭博都存在風險,尤其是在法律地位不明確的情況下。建議公眾謹慎對待,並了解相關法律和潛在風險。
如果您想了解更多具體方面,例如如何識別和避免相關風險,我可以提供更多信息。
https://politicsoc.com/
AGENCANTIK
AGENCANTIK it really can’t be trusted
bocor88
Проституция в городе Москве является проблемой как сложной и многоаспектной вопросом. Несмотря на она запрещается законодательством, этот бизнес существует как существенным нелегальным сектором.
Контекст в прошлом
В советские годы интимные услуги имела место нелегально. По окончании СССР, в ситуации экономической нестабильности, секс-работа оказалась более заметной.
Современная состояние
Сейчас секс-работа в Москве принимает различные формы, включая престижных услуг эскорта и заканчивая уличного уровня секс-работы. Высококлассные услуги часто предоставляются через онлайн, а уличная секс-работа сосредоточена в определённых областях городской территории.
Общественно-экономические аспекты
Многие девушки вступают в этот бизнес по причине финансовых затруднений. Секс-работа может оказаться интересной из-за перспективы немедленного дохода, но это сопряжена с рисками для здоровья и охраны здоровья.
Законодательные вопросы
Секс-работа в РФ нелегальна, и за ее организацию занятие существуют жесткие штрафы. Проституток постоянно задерживают к дисциплинарной наказанию.
Таким образом, не обращая внимания на запреты, интимные услуги является элементом экономики в тени столицы с серьёзными социальными и законодательными последствиями.
эромассаж в москве
娛樂城警示帳戶
I am in fact glad to read this website posts which includes lots of useful data, thanks for providing these information.
https://cameradb.review/wiki/Crystal_Clear_The_Ultimate_Guide_to_Auto_Glass_Replacement
https://www.google.com.co/url?q=https://telegra.ph/Shattered-No-More-A-Guide-to-Auto-Glass-Replacement-06-02
https://win-line.net/מכונות-מזל-על-כסף-אמיתי/
להעביר, נתונים לדבריך.
ההתמודדות באינטרנט הפכה לתחום נחשק מאוד בעת האחרונה, המכיל אפשרויות שונות של אפשרויות משחק, כמו משחקי פוקר.
בסיכום זה נבחן את תעשיית ההתמודדות המקוונת ונעניק לכם הערות חשובות שיסייע לכם להבין בתחום מרתק זה.
הימורי ספורט – קזינו באינטרנט
קזינו אונליין כולל מגוון רחב של אפשרויות מסורתיים כגון חריצים. הפעילות באינטרנט מעניקים למבקרים ליהנות מחוויית משחק אותנטית מכל מקום.
סוג המשחק תיאור מקוצר
מכונות פירות משחקי מזל
רולטה הימור על תוצאות על גלגל מסתובב
משחק קלפים להגעה ל-21 משחק קלפים בו המטרה להגיע לסכום של 21
משחק קלפים פוקר משחק קלפים אסטרטגי
התמודדות בבאקרה משחק קלפים מהיר וקצר
הימורי ספורט – קזינו באינטרנט
הימורי ספורט מהווים חלק מ אחד האזורים המתרחבים ביותר בפעילות באינטרנט. מבקרים מסוגלים לסחור על תוצאים של משחקי ספורט פופולריים כגון ועוד.
ההימורים יכולים להיות על תוצאת התחרות, מספר העופרות ועוד.
סוג הפעילות פירוט משחקי ספורט מרכזיים
ניחוש התפוקה ניחוש התוצאה הסופית של התחרות כדורגל, כדורסל, טניס
הפרש סקורים ניחוש ההפרש בסקורים בין הקבוצות כדורגל, כדורסל, הוקי
כמות התוצאות ניחוש כמות הסקורים בתחרות כל ענפי הספורט
המנצח בתחרות ניחוש מי יסיים ראשון (ללא קשר לניקוד) מרבית ענפי הספורט
התמודדות דינמית הימורים במהלך האירוע בזמן אמת כדורגל, טניס, הוקי
התמודדות מורכבת שילוב של מספר אופני התמודדות מגוון ענפי ספורט
התמודדות בפוקר מקוון – התמודדות באינטרנט
משחקי קלפים אונליין מהווה אחד מתחומי התמודדות המובילים ביותר בתקופה הנוכחית. מתמודדים מסוגלים להשתלב מול שחקנים אחרים מרחבי העולם במגוון
http://bbs.sdhuifa.com/home.php?mod=space&uid=554088
virtual assistant
How Could A Outsourcing Firm Achieve At A Minimum Of One Deal From Ten Sessions?
Outsourcing organizations could boost their sales success rates by focusing on a number of crucial approaches:
Comprehending Customer Demands
Prior to appointments, conducting comprehensive investigation on prospective clients’ companies, pain points, and particular requirements is vital. This readiness permits outsourcing organizations to customize their solutions, making them more attractive and applicable to the client.
Lucid Value Proposition
Providing a coherent, persuasive value statement is crucial. Outsourcing organizations should emphasize the ways in which their offerings offer economic benefits, improved efficiency, and expert knowledge. Explicitly illustrating these pros assists clients understand the concrete value they would receive.
Establishing Trust
Reliability is a key element of effective transactions. BPO companies might build trust by highlighting their history with case histories, reviews, and market credentials. Verified success stories and endorsements from satisfied customers can significantly strengthen credibility.
Efficient Follow Through
Steady follow-up after meetings is key to maintaining engagement. Tailored follow-up messages that repeat important subjects and answer any questions help keep the client interested. Employing CRM tools makes sure that no prospect is overlooked.
Unconventional Lead Generation Strategy
Innovative methods like content strategies can place outsourcing firms as thought leaders, pulling in potential clients. Interacting at industry events and utilizing online platforms like business social media could increase reach and establish significant connections.
Pros of Delegating Technical Support
Delegating IT support to a outsourcing organization might cut expenses and offer entry to a experienced labor force. This enables enterprises to concentrate on primary tasks while ensuring top-notch assistance for their clients.
Optimal Methods for App Development
Embracing agile methods in app creation provides for quicker deployment and progressive improvement. Multidisciplinary teams enhance cooperation, and constant feedback aids identify and address issues early.
Importance of Individual Employee Brands
The individual brands of workers boost a outsourcing organization’s reputation. Recognized market experts within the company draw customer confidence and contribute to a positive standing, helping with both customer acquisition and keeping talent.
Global Impact
These tactics help outsourcing companies by pushing productivity, boosting client relationships, and encouraging How Could A BPO Company Achieve At Least One Transaction From Ten Appointments?
BPO companies might improve their deal conversion rates by prioritizing a few key tactics:
Comprehending Customer Needs
Prior to sessions, carrying out detailed research on possible clients’ enterprises, challenges, and specific requirements is essential. This preparation allows BPO companies to adapt their offerings, rendering them more attractive and pertinent to the client.
Lucid Value Proposition
Providing a clear, persuasive value proposition is crucial. BPO firms should underline the ways in which their services offer cost savings, enhanced efficiency, and expert knowledge. Evidently showcasing these pros enables clients grasp the measurable benefit they would receive.
Establishing Confidence
Trust is a key element of fruitful deals. Outsourcing firms might establish reliability by showcasing their track record with case examples, reviews, and sector certifications. Demonstrated success stories and reviews from happy customers could significantly bolster reputation.
Effective Follow-Up
Regular post-meeting communication subsequent to sessions is essential to retaining engagement. Customized post-meeting communication messages that repeat key subjects and respond to any questions help maintain client interest. Using CRM systems guarantees that no lead is neglected.
Non-Standard Lead Generation Approach
Original methods like content marketing can establish outsourcing firms as thought leaders, pulling in potential customers. Connecting at market events and leveraging social media platforms like LinkedIn can extend reach and build significant connections.
Advantages of Contracting Out IT Support
Contracting Out technical support to a outsourcing organization could reduce spending and offer availability of a skilled labor force. This permits companies to concentrate on primary tasks while ensuring top-notch service for their clients.
Optimal Methods for App Development
Implementing agile methodologies in app creation ensures faster completion and step-by-step advancement. Cross-functional units enhance collaboration, and ongoing feedback assists detect and address issues at an early stage.
Significance of Personal Branding for Employees
The personal brands of workers enhance a BPO firm’s reputation. Famous sector experts within the firm pull in client credibility and contribute to a positive reputation, helping with both client acquisition and keeping talent.
Global Impact
These tactics aid BPO organizations by promoting productivity, enhancing customer relations, and encouraging
http://forums.indexrise.com/user-316302.html
I am in fact thankful to the owner of this website who has shared this impressive post at here.
https://0.gp/aLaaq
https://win-line.net/ווינר-ליין-ווינר-אונליין/
לבצע, אסמכתא לדבריך.
ההמרה באינטרנט הפכה לנישה מושך מאוד בעת האחרונה, המציע אפשרויות שונות של חלופות פעילות, לדוגמה מכונות מזל.
בסקירה זה נסקור את תחום הפעילות המקוונת ונמסור לכם נתונים חשובים שיתרום לכם לחקור באזור מעניין זה.
קזינו אונליין – הימורים באינטרנט
משחקי פוקר מכיל מבחר מגוון של אפשרויות קלאסיים כגון פוקר. הקזינו באינטרנט נותנים למתמודדים ליהנות מחווית הימורים מקצועית בכל עת ומקום.
האירוע סיכום קצר
משחקי מזל משחקי מזל עם גלגלים
גלגל הרולטה הימור על מספרים וצבעים על גלגל מסתובב
משחק קלפים להגעה ל-21 משחק קלפים בו המטרה להגיע לסכום של 21
משחק קלפים פוקר התמודדות אסטרטגית בקלפים
משחק הבאקרה משחק קלפים מהיר וקצר
התמרמרות ספורטיבית – פעילות באינטרנט
הימורים בתחום הספורט מהווים אחד התחומים הצומחים הגדולים ביותר בהימורים באינטרנט. משתתפים רשאים להתמודד על פרמטרים של אירועי ספורט פופולריים כגון כדורסל.
השקעות מתאפשרות על תוצאת האירוע, מספר העופרות ועוד.
סוג הפעילות הסבר תחרויות ספורט מקובלות
ניחוש הביצועים ניחוש התוצאה הסופית של התחרות כדורגל, כדורסל, הוקי
הפרש ביצועים ניחוש ההפרש בתוצאות בין הקבוצות כל ענפי הספורט
מספר שערים/נקודות ניחוש כמות הביצועים בתחרות כדורגל, כדורסל, קריקט
מנצח המשחק ניחוש איזו קבוצה תנצח (ללא קשר לתוצאה) מספר ענפי ספורט
הימורי חי התמודדות במהלך האירוע בזמן אמת כדורגל, טניס, קריקט
התמרמרות מגוונת שילוב של מספר הימורים שונים מספר ענפי ספורט
משחקי קלפים אונליין – הימורים באינטרנט
התמודדות בפוקר מקוון מייצג אחד מתחומי הפעילות המובילים המשפיעים ביותר בזמן האחרון. משתתפים מסוגלים להתמודד מול יריבים מכל רחבי הגלובליזציה בסוגים ש
blackpanther77 login
borju89 slot
네라 벳
정말 이 사람들의 뇌가 좀 이상하다는 생각이 듭니다.
bocor88 login
Быстрое строительство автомойки – это наша специализация. Мы обеспечиваем высокое качество и готовность к открытию в кратчайшие сроки.
Основание да пазарувате при нашия магазин?
Огромен избор
Ние осигуряваме внушителен избор от компоненти и принадлежности за смартфони.
Конкурентни тарифи
Ценовите предложения са изключително конкурентоспособни на пазарната среда. Ние работим да предоставяме висококачествени продукти на най-добрите тарифи, за да придобиете най-добра възвръщаемост за вложените средства.
Бърза куриерска услуга
Всички поръчки подадени до 16:00 часа се изпращат и изпращат светкавично. Така осигуряваме, че ще придобиете желаните резервни части възможно скоростно.
Удобно търсене
Нашият онлайн магазин е конфигуриран да бъде интуитивен за ползване. Вие сте в състояние да избирате стоки по модел, което прецизира намирането на необходимия артикул за вашата нужда.
Обслужване на превъзходно професионализъм
Екипът ни с висока квалификация постоянно на разположение, за да отговорят на Ваши запитвания и да ви помогнат да идентифицирате подходящите артикули според вашите изисквания. Ние положуваме грижи да гарантираме изключително обслужване, за да се радвате от партньорството си с нас.
Основна номенклатура:
Оригинални резервни части за телефони: Надеждни дисплеи, които осигуряват перфектно визуализация.
Допълнителни артикули за таблети: От източници на енергия до други компоненти – всички изискуеми за възстановяването на вашия таблет.
GSM сервиз: Професионални сервизни услуги за обслужване на вашите устройства.
Странични устройства за телефони: Богата гама от калъфи.
Компоненти за електронни комуникации: Необходимите компоненти за ремонт на Мобилни системи.
Насочете се към нашата компания за Необходимите нужди от аксесоари за мобилни телефони, и се радвайте на качествени услуги, привлекателни ценови условия и изключително съдействие.
Строительство автомойки под ключ – это наш профиль! Обещаем качество, соблюдение сроков и построение устойчивого бизнеса от идеи до открытия.
Предварително заявете отличен отель незакъснително незабавно
Идеальное дестинация для отдыха по выгодной стойност
Заявете водещи оферти настаняване и жилища прямо сейчас със сигурност на наша обслужване резервиране. Откройте за ваше удоволствие неповторими предложения и специални намаления за резервиране отелей във всички глобус. Независимо дали планирате организирате туризъм на пляже, деловую пътуване или любовен уикенд, при нас ще откриете отлично място за престой.
Реални кадри, отзиви и коментари
Разглеждайте автентични кадри, цялостни отзиви и обективни отзывы за хотелите. Мы предлагаем разнообразен асортимент вариантов отсядане, за да можете подберете тот, който най-пълно покрива вашите финансов ресурс и предпочитания туризъм. Наш сервис предоставя открито и увереност, правейки Ви достъпна изискваната данни за вземане на най-добро решение.
Лекота и безопасность
Отминете за продължителните разглеждания – резервирайте веднага удобно и гарантирано в нашата компания, с алтернатива плащане на място. Наш процесс бронирования прост и безопасен, что позволяет вам да се фокусирате за планиране вашего путешествия, а не по детайли.
Водещи обекти мира за туристически интерес
Открийте отличното обект за престой: места за подслон, гостевые дома, хостелы – все под рукой. Около 2 миллионов възможности на ваш выбор. Започнете Вашето пътуване: забронируйте отели и откривайте водещите места из цял земята! Нашата платформа представя качествените оферти за настаняване и богат асортимент дестинации за всякакъв уровня бюджет.
Разгледайте для себя Европу
Разглеждайте города Европейската география за откриване на варианти за престой. Откройте подробно опции за престой на Европейския континент, от курортов в средиземноморския регион до алпийски скривалища в Алпийските планини. Наши указания ще ви доведат към водещите опции престой в стария регион. Просто кликнете линковете отдолу, за находяне на хотел във Вашата избрана европейской стране и инициирайте свое европейское изследване
Резюме
Заявете отлично дестинация для отдыха при изгодна ставка безотлагателно
Международное бронирование гостиниц
Зарезервируйте превъзходен мотел незабавно днес
Перфектно дестинация за почивка с атрактивна такса
Оформете най-добри варианти подслон и престой в момента със сигурност на наша система резервиране. Разгледайте за ваша полза неповторими оферти и специални намаления на бронирование настаняване във всички свят. Независимо от желаете ли вы пътуване на пляже, служебна командировка или приятелски уикенд, в нашия магазин можете да откриете превъзходно локация для проживания.
Подлинные кадри, оценки и коментари
Наблюдавайте реални кадри, подробные оценки и правдиви препоръки об отелях. Имаме голям набор възможности размещения, за да имате възможност намерите съответния, същия наилучшим образом покрива вашему бюджет и тип дейност. Нашето обслужване гарантира надеждно и увереност, правейки Ви достъпна всю необходимую сведения для принятия правилен избор.
Удобство и надеждност
Забудьте за отнемащите идентификации – оформете веднага просто и надеждно при нас, с опция заплащане на място. Нашата процедура резервиране прост и надежден, даващ Ви възможност сосредоточиться в планирането на вашето пътуване, а не по детайли.
Главные достопримечательности земното кълбо за туристически интерес
Найдите най-подходящото место за престой: места за подслон, гостевые дома, хостелы – всичко на едно място. Над 2 000 000 опции за Ваше решение. Започнете Вашето пътуване: резервирайте места за настаняване и откривайте топ дестинации във всички земното кълбо! Нашата платформа представя водещите предложения за подслон и разнообразный асортимент объектов за различни степен средства.
Откройте задълбочено Европейския континент
Разглеждайте города Европейската география за намиране на варианти за престой. Откройте подробно възможности за подслон на Европейския континент, от курортни на Средиземном море до планински убежищ в Альпах. Нашите насоки ще ви ориентират к лучшим оферти размещения в континентален континенте. Незабавно посетете на ссылки под това, за да откриете дестинация във Вашата предпочитана европейской стране и начать свое европейское опознаване
В заключение
Резервирайте идеальное место для отдыха с атрактивна такса безотлагателно
tuan88 slot
kantorbola
Heya i’m for the primary time here. I came across this board and I in finding It truly useful & it helped me out a lot. I am hoping to provide something back and help others like you helped me.
外送茶是什麼?禁忌、價格、茶妹等級、術語等..老司機告訴你!
外送茶是什麼?
外送茶、外約、叫小姐是一樣的東西。簡單來說就是在通訊軟體與茶莊聯絡,選好自己喜歡的妹子後,茶莊會像送飲料這樣把妹子派送到您指定的汽車旅館、酒店、飯店等交易地點。您只需要在您指定的地點等待,妹妹到達後,就可以開心的開始一場美麗的約會。
外送茶種類
學生兼職的稱為清新書香茶
日本女孩稱為清涼綠茶
俄羅斯女孩被稱為金酥麻茶
韓國女孩稱為超細滑人參茶
外送茶價格
外送茶的客戶相當廣泛,包括中小企業主、自營商、醫生和各行業的精英,像是工程師等等。在台北和新北地區,他們的消費指數大約在 7000 到 10000 元之間,而在中南部則通常在 4000 到 8000 元之間。
對於一般上班族和藍領階層的客人來說,建議可以考慮稍微低消一點,比如在北部約 6000 元左右,中南部約 4000 元左右。這個價位的茶妹大多是新手兼職,但有潛力。
不同地區的客人可以根據自己的經濟能力和喜好選擇適合自己的價位範圍,以免感到不滿意。物價上漲是一個普遍現象,受到地區和經濟情況等因素的影響,茶莊的成本也在上升,因此價格調整是合理的。
外送茶外約流程
加入LINE:加入外送茶官方LINE,客服隨時為你服務。茶莊一般在中午 12 點到凌晨 3 點營業。
告知所在地區:聯絡客服後,告訴他們約會地點,他們會幫你快速找到附近的茶妹。
溝通閒聊:有任何約妹問題或需要查看妹妹資訊,都能得到詳盡的幫助。
提供預算:告訴客服你的預算,他們會找到最適合你的茶妹。
提早預約:提早預約比較好配合你的空檔時間,也不用怕到時候約不到你想要的茶妹。
外送茶術語
喝茶術語就像是進入茶道的第一步,就像是蓋房子打地基一樣。在這裡,我們將這些外送茶入門術語分類,讓大家能夠清楚地理解,讓喝茶變得更加容易上手。
魚:指的自行接客的小姐,不屬於任何茶莊。
茶:就是指「小姐」的意思,由茶莊安排接客。
定點茶:指由茶莊提供地點,客人再前往指定地點與小姐交易。
外送茶:指的是到小姐到客人指定地點接客。
個工:指的是有專屬工作室自己接客的小姐。
GTO:指雞頭也就是飯店大姊三七茶莊的意思。
摳客妹:只負責找客人請茶莊或代調找美眉。
內機:盤商應召站提供茶園的人。
經紀人:幫內機找美眉的人。
馬伕:外送茶司機又稱教練。
代調:收取固定代調費用的人(只針對同業)。
阿六茶:中國籍女子,賣春的大陸妹。
熱茶、熟茶:年齡比較大、年長、熟女級賣春者(或稱阿姨)。
燙口 / 高溫茶:賣春者年齡過高。
台茶:從事此職業的台灣小姐。
本妹:從事此職業的日本籍小姐。
金絲貓:西方國家的小姐(歐美的、金髮碧眼的那種)。
青茶、青魚:20 歲以下的賣春者。
乳牛:胸部很大的小姐(D 罩杯以上)。
龍、小叮噹、小叮鈴:體型比較肥、胖、臃腫、大隻的小姐。
AGENCANTIK
AGENCANTIK a site that can make you happy
CAYK Marketing
TORONTO — Googlle is wading into Canada’s employment market place with a new search
feature and a $1 million investment into a forthcoming jobs
platform.
Also visit my site … 스웨이드
coindarwin web3 academy
The Story About Solana’s Architect Toly Yakovenko’s Achievement
After A Pair of Servings of Coffees plus a Beer
Yakovenko, the visionary the innovator behind Solana, commenced his path with a routine practice – two coffees and a brew. Little did he know, these occasions would spark the machinery of his future. Nowadays, Solana is as a formidable competitor in the crypto sphere, with a market cap in the billions.
Initial Ethereum ETF Sales
The new Ethereum ETF newly was introduced with a staggering trading volume. This historic event saw numerous spot Ethereum ETFs from multiple issuers start trading on American exchanges, introducing unseen activity into the generally calm ETF trading market.
Ethereum ETF Approval by SEC
The SEC has formally approved the Ethereum ETF to be listed. As a cryptographic asset with smart contracts, it is expected that Ethereum to have a profound impact the blockchain sector following this approval.
Trump’s Bitcoin Tactics
As the election approaches, Trump positions himself as the “Crypto President,” repeatedly showing his advocacy for the cryptocurrency industry to garner votes. His method differs from Biden’s tactic, targeting the interest of the crypto community.
Musk’s Influence on Crypto
Elon, a famous figure in the crypto community and a supporter of the Trump camp, created a buzz yet again, driving a meme coin linked to his antics. His involvement keeps shaping the market landscape.
Recent Binance News
The subsidiary of Binance, BAM, has been allowed to invest customer funds into U.S. Treasuries. In addition, Binance observed its seventh anniversary, emphasizing its progress and obtaining multiple compliance licenses. At the same time, the firm also revealed plans to take off several notable cryptocurrency trading pairs, altering the market landscape.
AI’s Impact on the Economy
A top stock analyst from Goldman Sachs recently observed that AI is unlikely to cause an economic transformation
RGBET trang chủ
RGBET trang chủ với hệ thống game nhà cái đỉnh cao – Nhà cái uy tín số 1 Việt Nam trong lĩnh vực cờ bạc online
RG trang chủ, RG RICH GAME, Nhà Cái RG
RGBET Trang Chủ Và Câu Chuyện Thương Hiệu
Ra đời vào năm 2010 tại Đài Loan, RGBET nhanh chóng trở thành một trang cá cược chất lượng hàng đầu khu vực Châu Á. Nhà cái được cấp phép hoạt động hợp pháp bởi công ty giải trí trực tuyến hợp pháp được ủy quyền và giám sát theo giấy phép Malta của Châu Âu – MGA. Và chịu sự giám sát chặt chẽ của tổ chức PAGCOR và BIV.
RGBET trang chủ cung cấp cho người chơi đa dạng các thể loại cược đặc sắc như: thể thao, đá gà, xổ số, nổ hũ, casino trực tuyến. Dịch vụ CSKH luôn hoạt động 24/7. Với chứng chỉ công nghệ GEOTRUST, nhà cái đảm bảo an toàn cho mọi giao dịch của khách hàng. APP RG thiết kế tối ưu giải quyết mọi vấn đề của người dùng IOS và Android.
Là một nhà cái đến từ đất nước công nghệ, nhà cái luôn không ngừng xây dựng và nâng cấp hệ thống game và dịch vụ hoàn hảo. Mọi giao dịch nạp rút được tự động hoá cho phép người chơi hoàn tất giao dịch chỉ với 2 phút vô cùng nhanh chóng
RGBET Lớn Nhất Uy Tín Nhất – Giá Trị Cốt Lõi
Nhà Cái RG Và Mục Tiêu Thương Hiệu
Giá trị cốt lõi mà RGBET mong muốn hướng đến đó chính là không ngừng hoàn thiện để đem đến một hệ thống chất lượng, công bằng và an toàn. Nâng cao sự hài lòng của người chơi, đẩy mạnh hoạt động chống gian lận và lừa đảo. RG luôn cung cấp hệ thống kèo nhà cái đặc sắc, cùng các sự kiện – giải đấu hàng đầu và tỷ lệ cược cạnh tranh đáp ứng mọi nhu cầu khách hàng.
Thương hiệu cá cược RGBET cam kết đem lại cho người chơi môi trường cá cược công bằng, văn minh và lành mạnh. Đây là nguồn động lực to lớn giúp nhà cái thực tế hóa các hoạt động của mình.
RGBET Có Tầm Nhìn Và Sứ Mệnh
Đổi mới và sáng tạo là yếu tố cốt lõi giúp đạt được mục tiêu dưới sự chuyển mình mạnh mẽ của công nghệ. Tầm nhìn và sứ mệnh của RGBET là luôn tìm tòi những điều mới lạ, đột phá mạnh mẽ, vượt khỏi giới hạn bản thân, đương đầu với thử thách để đem đến cho khách hàng sản phẩm hoàn thiện nhất.
Chúng tôi luôn sẵn sàng tiếp thu ý kiến và nâng cao bản thân mỗi ngày để tạo ra sân chơi bổ ích, uy tín và chuyên nghiệp cho người chơi. Để có thể trở thành nhà cái phù hợp với mọi khách hàng.
Khái Niệm Giá Trị Cốt Lõi Nhà Cái RGBET
Giá trị cốt lõi của nhà cái RG luôn gắn kết chặt chẽ với nhau giữa 5 khái niệm: Chính trực, chuyên nghiệp, an toàn, đổi mới, công nghệ.
Chính Trực
Mọi quy luật, cách thức của trò chơi đều được nhà cái cung cấp công khai, minh bạch và chi tiết. Mỗi tựa game hoạt động đều phải chịu sự giám sát kỹ lưỡng bởi các cơ quan tổ chức có tiếng về sự an toàn và minh bạch của nó.
Chuyên Nghiệp
Các hoạt động tại RGBET trang chủ luôn đề cao sự chuyên nghiệp lên hàng đầu. Từ giao diện đến chất lượng sản phẩm luôn được trau chuốt tỉ mỉ từng chi tiết. Thế giới giải trí được xây dựng theo văn hóa Châu Á, phù hợp với đại đa số thị phần khách Việt.
An Toàn
RG lớn nhất uy tín nhất luôn ưu tiên sử dụng công nghệ mã hóa hiện đại nhất để đảm bảo an toàn, riêng tư cho toàn bộ thông tin của người chơi. Đơn vị cam kết nói không với hành vi gian lận và mua bán, trao đổi thông tin cá nhân bất hợp pháp.
Đổi Mới
Nhà cái luôn theo dõi và bắt kịp xu hướng thời đại, liên tục bổ sung các sản phẩm mới, phương thức cá cược mới và các ưu đãi độc lạ, mang đến những trải nghiệm thú vị cho người chơi.
Công Nghệ
RGBET trang chủ tập trung xây dựng một giao diện game sắc nét, sống động cùng tốc độ tải nhanh chóng. Ứng dụng RGBET giải nén ít dung lượng phù hợp với mọi hệ điều hành và cấu hình, tăng khả năng sử dụng của khách hàng.
RGBET Khẳng Định Giá Trị Thương Hiệu
Hoạt động hợp pháp với đầy đủ giấy phép, chứng chỉ an toàn đạt tiêu chuẩn quốc tế
Hệ thống game đa màu sắc, đáp ứng được mọi nhu cầu người chơi
Chính sách bảo mật RG hiện đại và đảm bảo an toàn cho người chơi cá cược
Bắt tay hợp tác với nhiều đơn vị phát hành game uy tín, chất lượng thế giới
Giao dịch nạp rút RG cấp tốc, nhanh gọn, bảo mật an toàn
Kèo nhà cái đa dạng với bảng tỷ lệ kèo cao, hấp dẫn
Dịch Vụ RGBET Casino Online
Dịch vụ khách hàng
Đội ngũ CSKH RGBET luôn hoạt động thường trực 24/7. Nhân viên được đào tạo chuyên sâu luôn giải đáp tất cả các khó khăn của người chơi về các vấn đề tài khoản, khuyến mãi, giao dịch một cách nhanh chóng và chuẩn xác. Hạn chế tối đa làm ảnh hưởng đến quá trình trải nghiệm của khách hàng.
Đa dạng trò chơi
Với sự nhạy bén trong cập nhật xu thế, nhà cái RGBET đã dành nhiều thời gian phân tích nhu cầu khách hàng, đem đến một kho tàng game chất lượng với đa dạng thể loại từ RG casino online, thể thao, nổ hũ, game bài, đá gà, xổ số.
Khuyến mãi hấp dẫn
RGBET trang chủ liên tục cập nhật và thay đổi các sự kiện ưu đãi đầy hấp dẫn và độc đáo. Mọi thành viên bất kể là người chơi mới, người chơi cũ hay hội viên VIP đều có cơ hội được hưởng ưu đãi đặc biệt từ nhà cái.
Giao dịch linh hoạt, tốc độ
Thương hiệu RGBET luôn chú tâm đến hệ thống giao dịch. Nhà cái cung cấp dịch vụ nạp rút nhanh chóng với đa dạng phương thức như thẻ cào, ví điện tử, ngân hàng điện tử, ngân hàng trực tiếp. Mọi hoạt động đều được bảo mật tuyệt đối bởi công nghệ mã hóa tiên tiến.
App cá độ RGBET
App cá độ RGBET là một ứng dụng cho phép người chơi đăng nhập RG nhanh chóng, đồng thời các thao tác đăng ký RG trên app cũng được tối ưu và trở nên đơn giản hơn. Tham gia cá cược RG bằng app cá độ, người chơi sẽ có 1 trải nghiệm cá cược tuyệt vời và thú vị.
RGBET Có Chứng Nhận Cá Cược Quốc Tế
Nhà cái RGBET hoạt động hợp pháp dưới sự cấp phép của hai tổ chức thế giới là PAGCOR và MGA, tính minh bạch và công bằng luôn được giám sát gắt gao bởi BIV. Khi tham gia cược tại đây, người chơi sẽ được đảm bảo quyền và lợi ích hợp pháp của mình.
Việc sở hữu các chứng nhận quốc tế còn cho thấy nguồn tài chính ổn định, dồi dào của RGBET. Điều này cho thấy việc một nhà cái được công nhận bởi các cơ quan quốc tế không phải là một chuyện dễ.
Theo quy định nhà cái RGBET, chỉ người chơi từ đủ 18 tuổi trở lên mới có thể tham gia cá cược tại RGBET
MGA (Malta Gaming Authority)
Tổ chức MGA đảm bảo tính vẹn toàn và ổn định của các trò chơi. Có các chính sách bảo vệ nguồn tài chính và quyền lợi của người chơi. Chứng nhận một nhà cái hoạt động có đầy đủ pháp lý, tuân thủ nghiêm chỉnh luật cờ bạc.
Chứng nhận Quần đảo Virgin Vương quốc Anh (BIV)
Tổ chứng chứng nhận nhà cái có đầy đủ tài chính để hoạt động kinh doanh cá cược. Với nguồn ngân sách dồi dào, ổn định nhà cái bảo đảm tính thanh khoản cho người chơi, mọi quyền lợi sẽ không bị xâm phạm.
Giấy Phép PAGCOR
Tổ chức cấp giấy phép cho nhà cái hoạt động đạt chuẩn theo tiêu chuẩn quốc tế. Cho phép nhà cái tổ chức cá cược một cách hợp pháp, không bị rào cản. Có chính sách ngăn chặn mọi trò chơi có dấu hiệu lừa đảo, duy trì sự minh bạch, công bằng.
Nhà Cái RGBET Phát Triển Công Nghệ
Nhà cái RGBET hỗ trợ trên nhiều thiết bị : IOS, Android, APP, WEB, Html5
RG và Trách Nhiệm Xã Hội
RGBET RichGame không đơn thuần là một trang cá cược giải trí mà nhà cái còn thể hiện rõ tính trách nhiệm xã hội của mình. Đơn vị luôn mong muốn người chơi tham gia cá cược phải có trách nhiệm với bản thân, gia đình và cả xã hội. Mọi hoạt động diễn ra tại RGBET trang chủ nói riêng hay bất kỳ trang web khác, người chơi phải thật sự bình tĩnh và lý trí, đừng để bản thân rơi vào “cạm bẫy của cờ bạc”.
RGBET RichGame với chính sách nghiêm cấm mọi hành vi xâm phạm thông tin cá nhân và gian lận nhằm tạo ra một môi trường cá cược công bằng, lành mạnh. Nhà cái khuyến cáo mọi cá nhân chưa đủ 18 tuổi không nên đăng ký RG và tham gia vào bất kỳ hoạt động cá cược nào.
rgbet 1840914